- Mailing Lists
- in
- A Crash Course in P2P
Archives
- By thread 5201
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 12
[Online workshop] Level up your Kubernetes observability with New Relic
Panama Canal restrictions are expected to shake up global supply chains
A Crash Course in P2P
A Crash Course in P2P
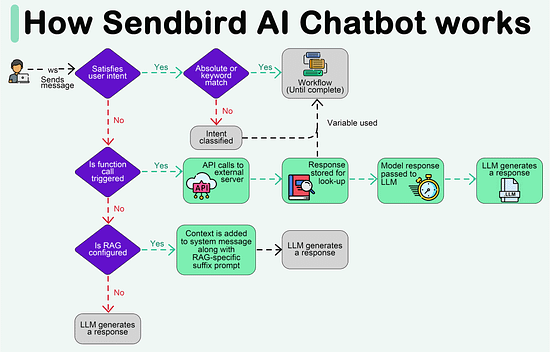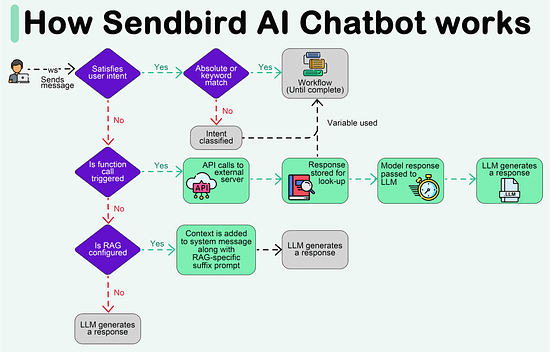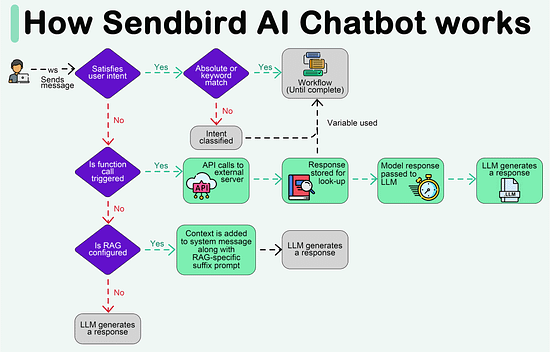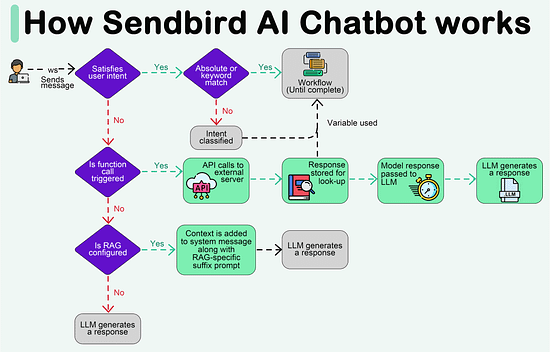
Create your free AI chatbot (Sponsored)Meet Sendbird SmartAssistant, a customizable chatbot powered by OpenAI’s GPT engine. The only chatbot that can be presented in your brand, trained with your own content, and deployed via low-to-no code. In this interactive Demo you will see how Sendbird offers:
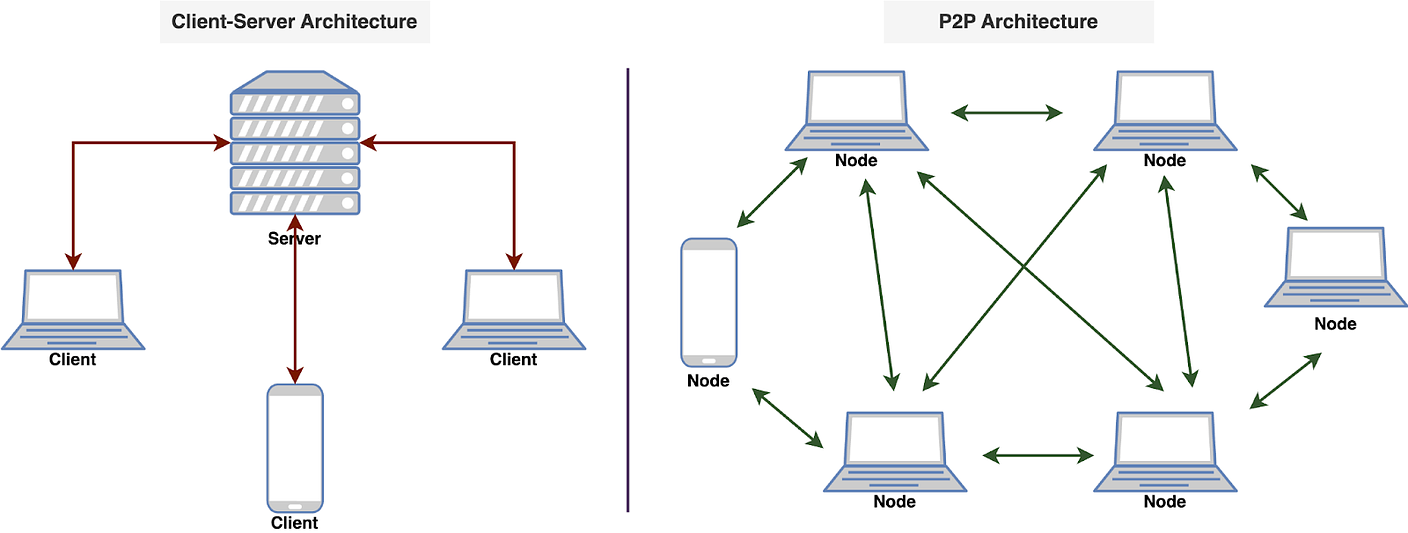
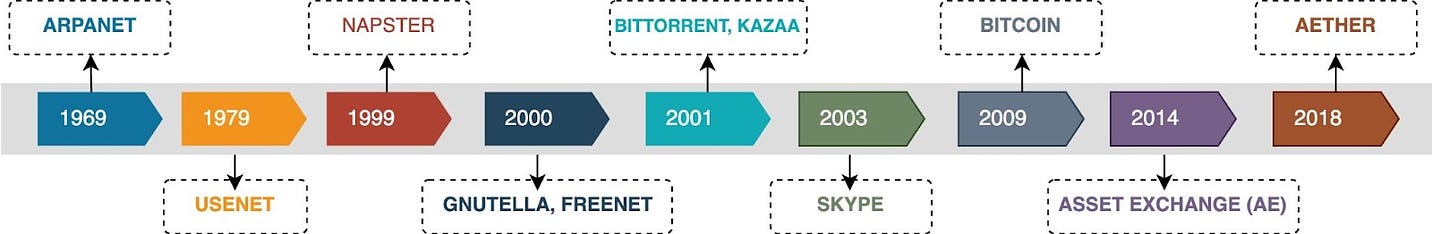
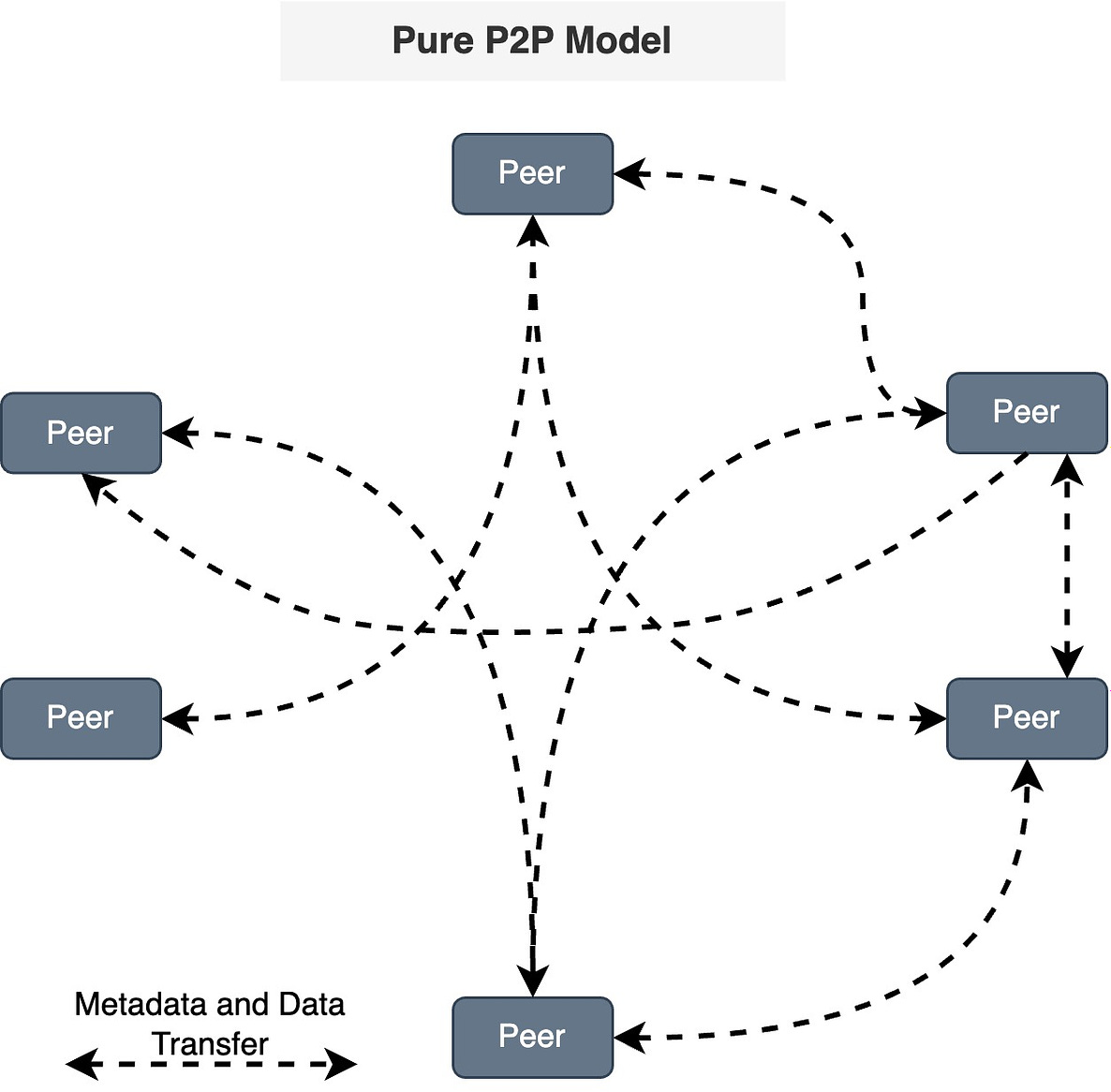
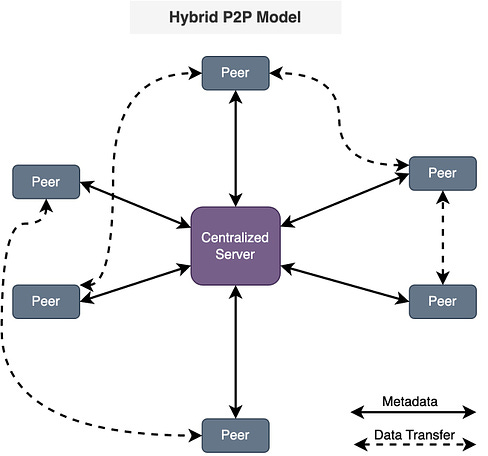
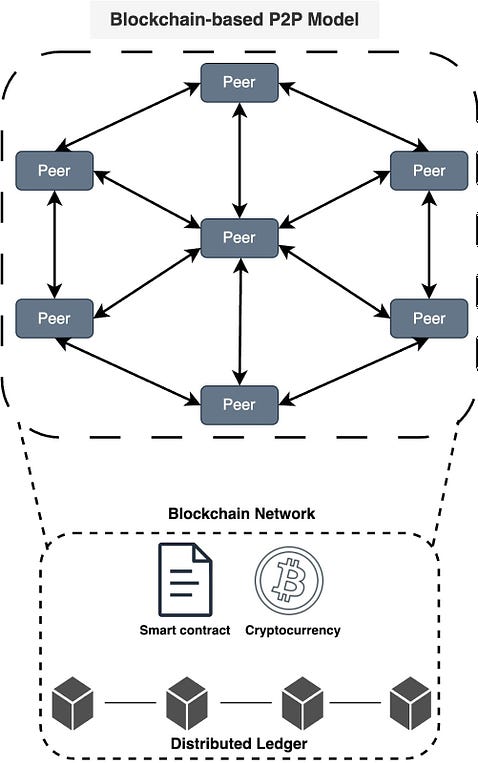
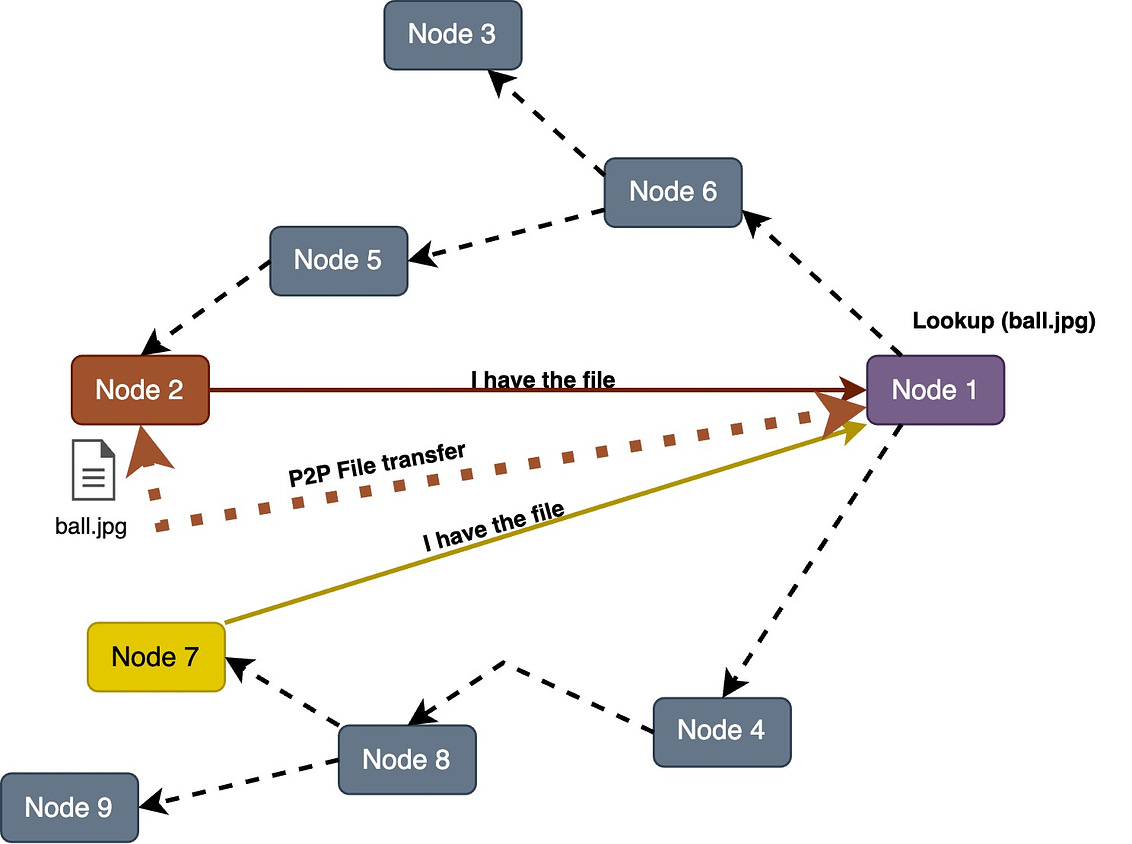
Try SmartAssistant, part of Sendbird's AI-embedded communications platform across chat, messaging, voice, and video APIs, to enable faster, deeper engagement with your customers. A Crash Course in P2PIn this issue, we are diving deep into the world of P2P (peer-to-peer) networks. It's all about computers talking directly to each other. We will take you on a cool journey, checking out how P2P networks evolved, the different P2P models, and the nitty-gritty details of how they work. We will talk about the challenges faced by P2P networks and a sneak peek into the future where blockchain and DeFi make things even more interesting. A P2P network is a type of network in which different computers communicate with each other directly without the need for a central server. The peer in the term indicates that all participating computers/systems are equal. These computers are also called nodes. In a traditional network architecture (known as the client-server architecture), there is usually one server and multiple clients. If two clients want to communicate with each other, the message has to first reach the server and then the server sends the message to the second client. History of P2P networksWe start our discussion of P2P with the history of such networks, as it is not a recent concept. The evolution of P2P networks is a fascinating journey spanning several decades, marked by groundbreaking developments and innovations. Here is a timeline of key P2P applications and transformative moments in the history of P2P. Types of P2P modelsWe would like to discuss how the P2P networks operate, but before we do that, it is important to understand the different ways in which peer-to-peer networks can be structured or categorized based on their functionalities. So, here are some common types of P2P models. Pure P2P modelIn this model, there is no central server or authority, and each node can act both as a client and a server. Hybrid P2P modelThis model makes use of centralized servers for facilitating initial connection and peer discovery. Further communication between peers is carried out in a decentralized manner. This approach balances the benefits of a decentralized network with the efficiency of centralized coordination. Blockchain-based P2P modelA blockchain-based Peer-to-Peer model refers to a decentralized network architecture where the principles of P2P interaction are combined with blockchain technology. In this model, blockchain serves as the underlying distributed ledger or database that records and verifies transactions, creating a secure and transparent environment for peer-to-peer interactions. This model is often associated with decentralized applications (DApps) and platforms that leverage the capabilities of blockchain for various purposes. Latest articlesIf you’re not a paid subscriber, here’s what you missed this month. To receive all the full articles and support ByteByteGo, consider subscribing: How the P2P network operatesNow, we are all set to discuss how a typical P2P network operates. As discussed earlier, the P2P network is an example of a decentralized architecture where each node has equal status and is capable of both requesting and providing resources or services. P2P networks can be used for various applications, including file sharing, communication, distributed computing, and more. Here is a general overview of how a P2P network operates. Node InitializationWhen a new node in a P2P network boots up, it doesn’t know anything about the network, because there is no central server. Usually, developers provide a list of trusted nodes written directly into the code of the P2P client application that can be used for initial peer discovery. These trusted nodes could be centralized servers or peers depending upon the P2P application. A node is usually identified by the following node triple: IP address, Port number, and node ID. The node ID should be unique with no collisions between peers. There are several methods to achieve this:
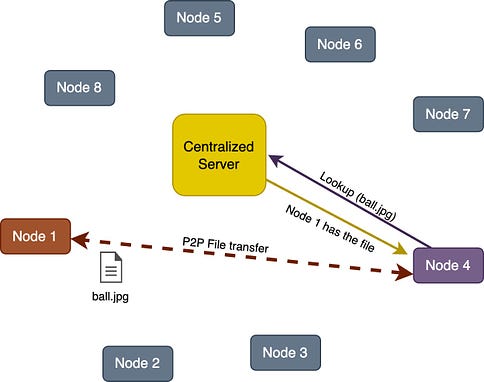
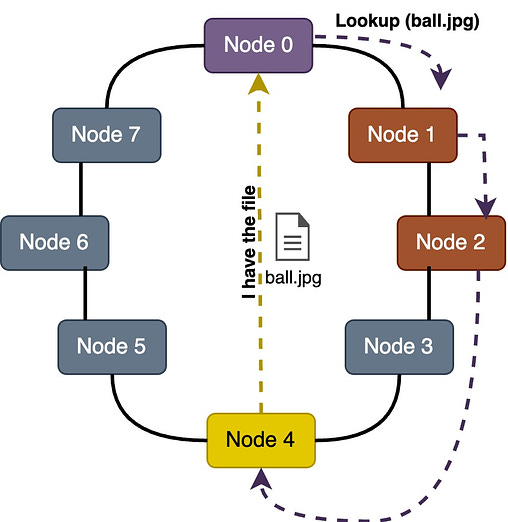
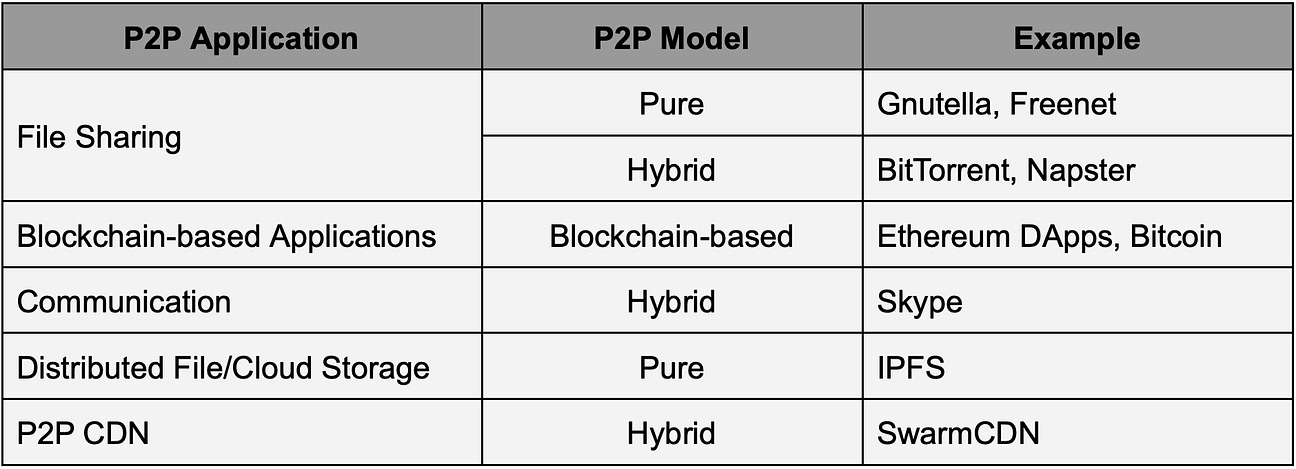
Take the example of Bitcoin, when a Bitcoin client starts, it checks its database for a list of reliable peers, if no such list is found it will use the default list hard coded into the software by the developers. Once the client has found a peer it will periodically look for new peers. The hard-coded list is just a bootstrap, once the client has a few nodes connected it doesn't need the original list anymore. The Bitcoin P2P system is designed to be very fault-tolerant and decentralized. Discovery and ConnectionAfter the node initialization, it needs a way to discover and connect with other nodes in the network. There are different methods for peer discovery in a P2P network. Some of the methods are discussed below. Centralized Server / Tracker Server: In this method, there is a central server that has information about all nodes in the network. When a new node wants to join the P2P network, it first contacts the central server which provides the new node the information about other peers. The new node can then communicate directly with other nodes. This method may seem like client-server architecture. However, the server is only used for peer discovery and not for actual communication since after peer discovery, the communication among peers occurs directly. The central server is also called a tracker in some P2P applications that maintains a list of active peers in the network. All existing peers periodically communicate with the tracker to confirm their availability and get a fresh list of all available peers. The hybrid P2P model utilizes this approach. Distributed Hash Tables (DHTs): It is a decentralized method for peer discovery commonly used in P2P networks. Nodes are assigned a unique identifier, and a distributed hash table is used to map these identifiers to IP addresses. When a node wants to discover another peer, it can perform a lookup in the DHT to find the corresponding IP address. The pure P2P model utilizes this approach. Broadcasting and Multicasting: Nodes may broadcast their presence or send multicast messages to the network. Other nodes can listen to these broadcasts or messages to discover peers. This method is more common in smaller, local P2P networks. For example, when a node sends a broadcast file request to the network, all peers who can provide the file send the message to the requester node. The node then chooses the specific peer to get the file from. Distributed Data StoragePeers in a P2P network share resources directly with each other. Resources can include files, computational power, or other services. So, the question is, how these resources are being stored in a P2P network? We can understand this with the help of an example. In a file-sharing P2P network, each peer contributes a portion of its storage to host parts of files. This results in a distributed storage system where the complete file is reconstructed by combining contributions from multiple peers in the network. Routing and LookupEvery node maintains a lookup table (also called a routing table) where it stores the node information (IP, Port, and ID) of the closest peers it knows of. The implementation for lookup tables varies based on the topology, but all share a common principle - they enable nodes to identify the peer closest to any given node ID. If the peer has the data it will route it back to the query originator, if not, it will route the query to the closest node it has on its lookup table, this process continues recursively until the node that has the data is found. Depending on the P2P protocol, there exist different metrics to define the distance between the node ID of two peers. For example, the very popular peer-to-peer protocol Kademlia uses the XOR-metric. Real-life applications of P2P networkP2P networks have some cool real-life applications. Here are some common P2P applications along with the respective models they often fall into: Advantages of P2P networkDecentralizationP2P networks are designed to operate in a decentralized manner, meaning there is no central server or authority controlling the network. Redundancy and reliabilityThe data is not placed in just one peer’s storage. Multiple peers have a copy of the same data which prevents a single point of failure - unlike the traditional client-server architecture where the central server has the data and can be lost if the server fails. Since data is distributed across multiple nodes, P2P networks are inherently redundant. If one node fails or leaves the network, the data can still be retrieved from other nodes, enhancing reliability. ScalabilityA P2P network is more scalable than a traditional client-server architecture. In a traditional client-server architecture, a single server has to handle all requests. If there are too many client requests, the server may not be able to handle all of the requests. However, in the case of P2P, each request is not necessarily handled by a single node, thus providing scalability. Distributed computingP2P networks can be used for distributed computing tasks where processing is distributed among multiple nodes. This is beneficial for tasks that require significant computational power. File Sharing and content distributionP2P networks, especially those using protocols like BitTorrent, excel in distributing large files efficiently. Users can download and upload simultaneously, reducing the load on individual servers. Privacy and anonymityIn P2P systems, users may enjoy increased privacy and anonymity as they communicate directly with peers without relying on a central server. This can be advantageous in applications where privacy is a concern. Challenges in P2P networkLet’s now discuss, some of the challenges in P2P networks. Security concernsP2P networks can be more vulnerable to security threats, including unauthorized access, malware distribution, etc. Dependency on peer availabilityThe availability of data in a P2P network depends on the willingness and availability of peers to share that data. If certain nodes leave the network or become unresponsive, it can affect the availability of resources. Legal and copyright issuesP2P networks are known to share and spread copyrighted material. Sharing copyrighted material can lead users to legal issues. For example, Metallica (a music band) filed a lawsuit against Napster in 2000. Napster was shut down in 2001. In another incident, the alleged owner of one of the biggest torrent sites, i.e., kickasstorrents, was arrested by the US authorities from Poland back in 2016. Similarly, another famous torrent site for movies YIFY Torrents or YTS also went down in 2015 after facing a lawsuit from Motion Picture Association of America. Regulatory frameworks for P2P networksP2P networks are playing a significant role in shaping the Internet's future. Nevertheless, it's crucial to address specific legal and ethical considerations. For instance:
What lies ahead for the P2P networks?P2P networks have gained traction in recent years when it comes to file sharing and cryptocurrency. With the advent of DeFi (decentralized finance) on blockchain, the future of P2P networks looks greener than ever. DeFi platforms allow people to lend or borrow funds from others without relying on any financial institute or brokerage. The most prominent blockchain that supports DeFi is the Ethereum blockchain. Furthermore, P2P could play a role in how our smart devices communicate. Imagine your smart fridge and coffee maker having a direct chit-chat without involving a server. They might even plan your breakfast together. Sounds fun! isn’t it? RecapHere is what we have covered in this newsletter:
© 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:38 - 6 Feb 2024