- Mailing Lists
- in
- EP102: Encoding vs Encryption vs Tokenization
Archives
- By thread 4453
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 27
EP102: Encoding vs Encryption vs Tokenization
EP102: Encoding vs Encryption vs Tokenization
This week’s system design refresher:
Register for POST/CON 24 | April 30 - May 1 (Sponsored)Postman’s annual user conference will be one of 2024’s top developer events and an unforgettable experience! Join the wider API community in San Francisco and be the first to learn about the latest Postman product advancements, elevate your skills in hands-on workshops with Postman experts, and hear from industry leaders, including:
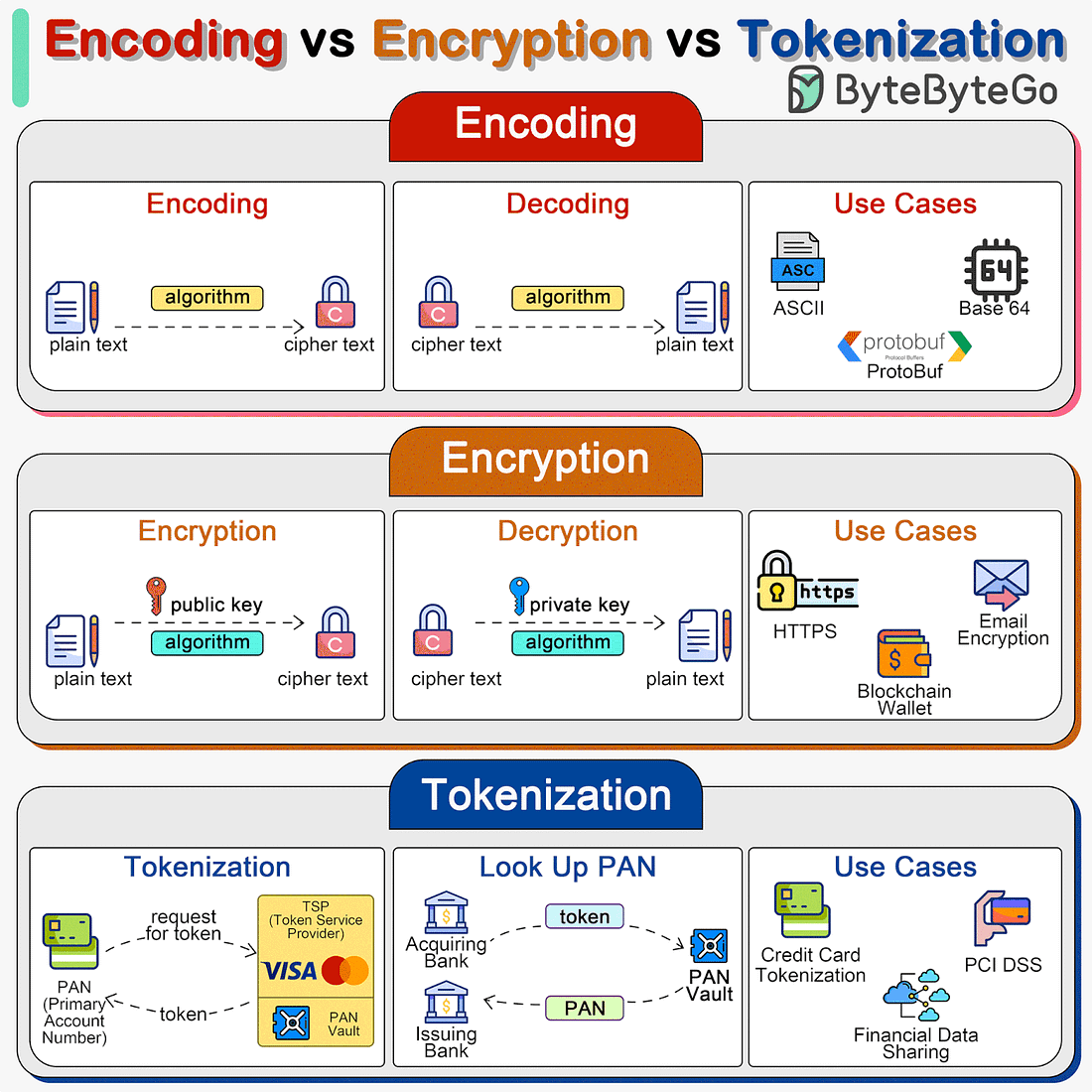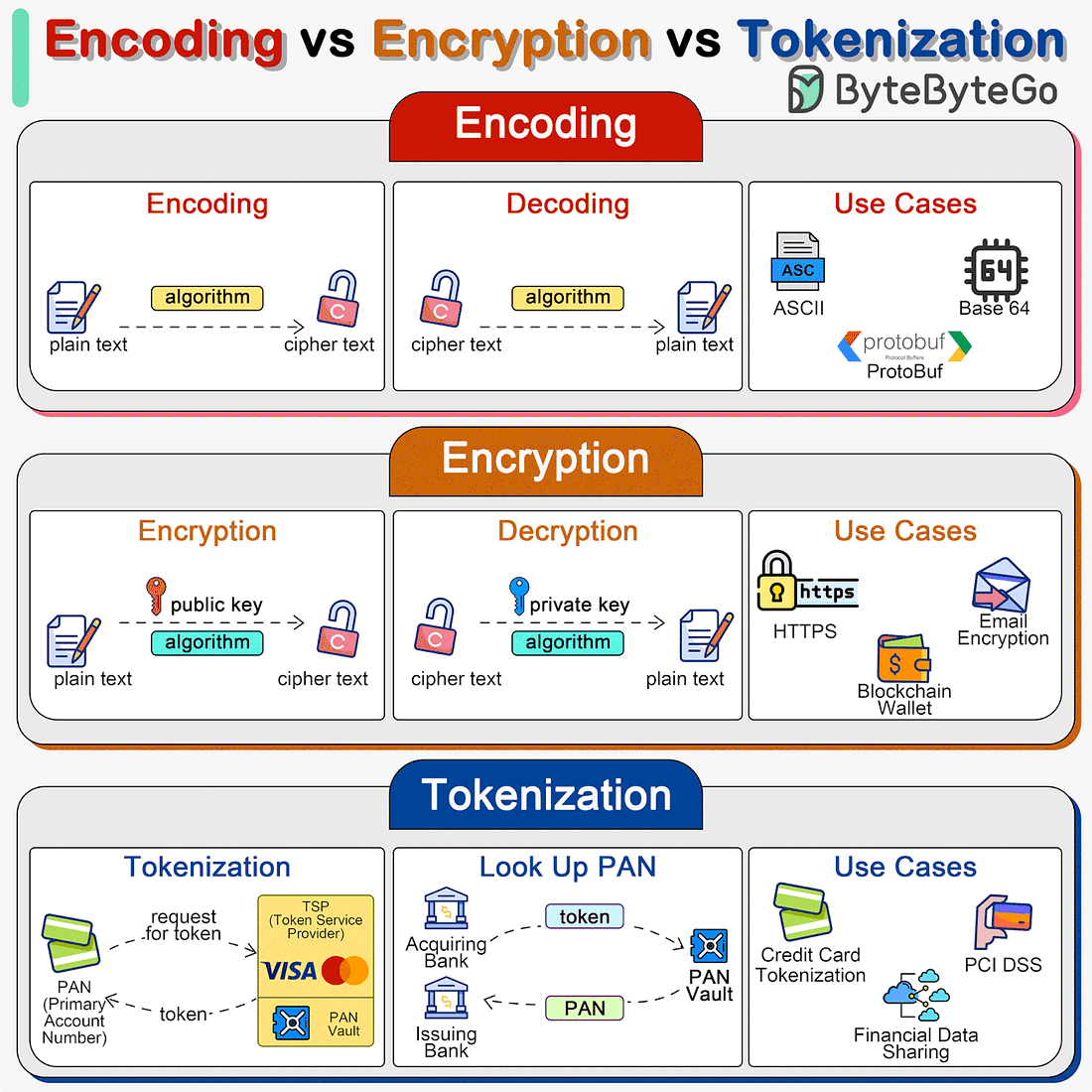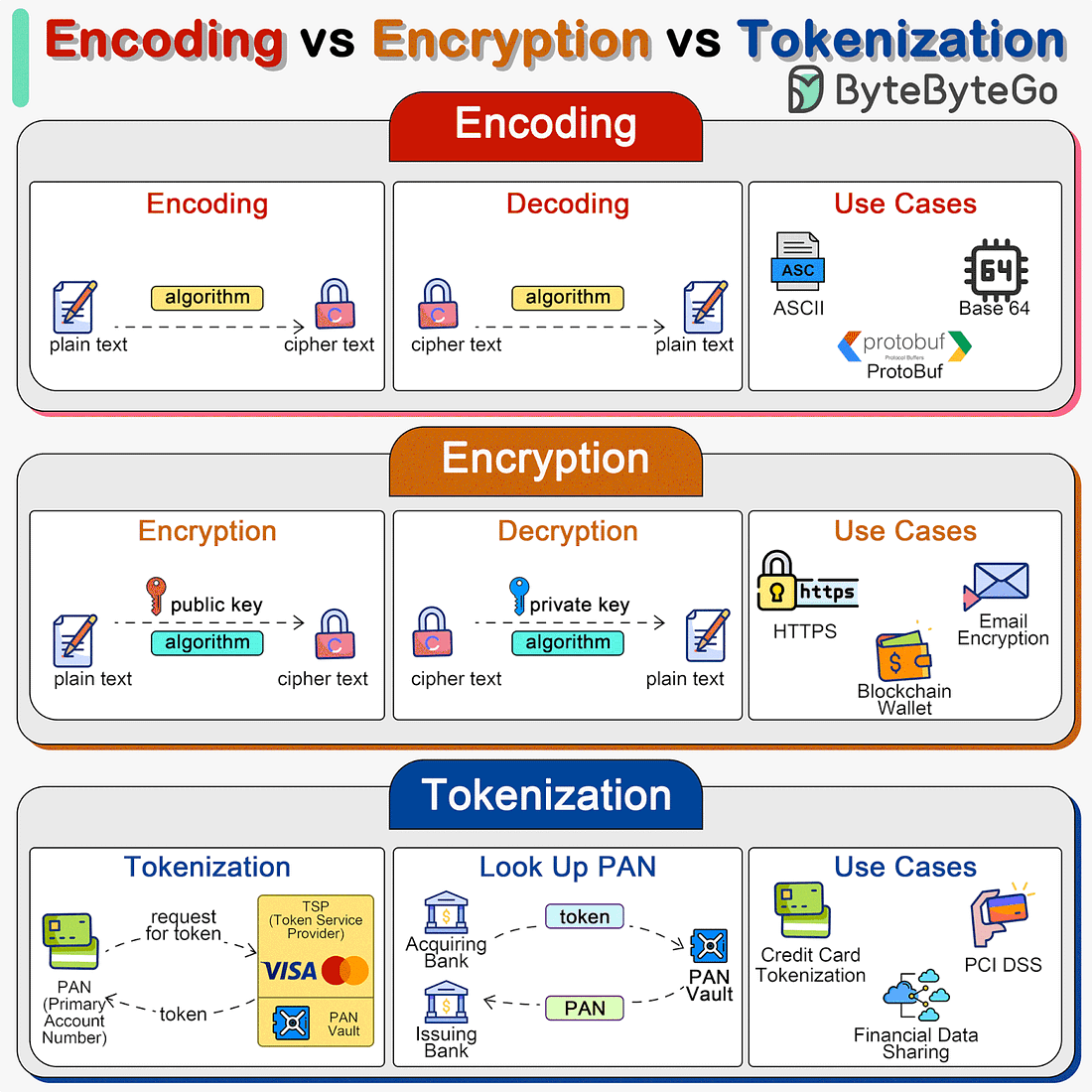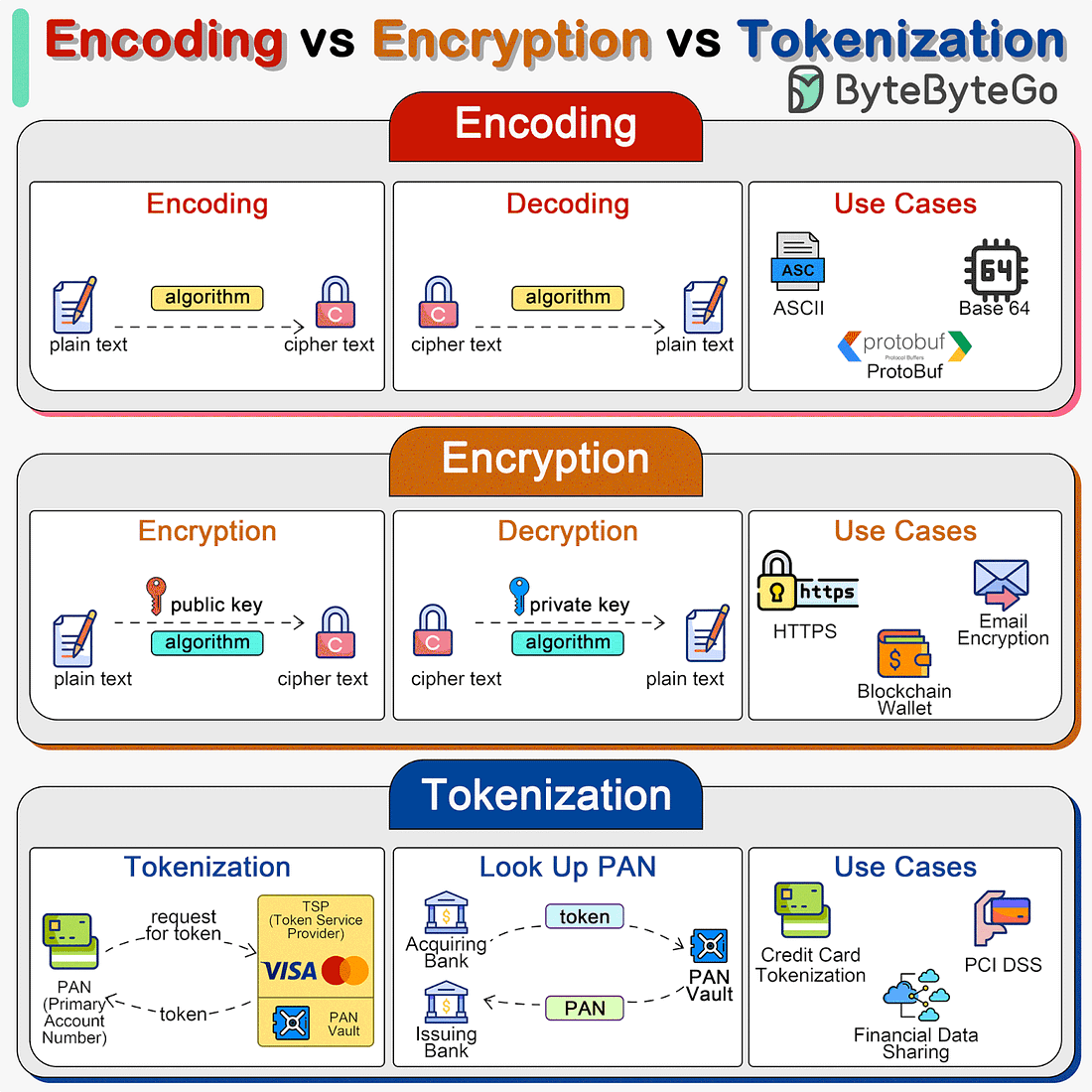
See the full agenda and register now to get a 30% Early Adopter discount! Bonus: Did we mention there's an awesome after-party with a special celebrity guest? Caching Pitfalls Every Developer Should Know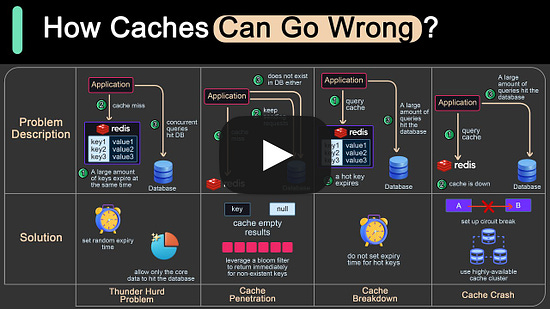 Encoding vs Encryption vs TokenizationEncoding, encryption, and tokenization are three distinct processes that handle data in different ways for various purposes, including data transmission, security, and compliance. In system designs, we need to select the right approach for handling sensitive information.
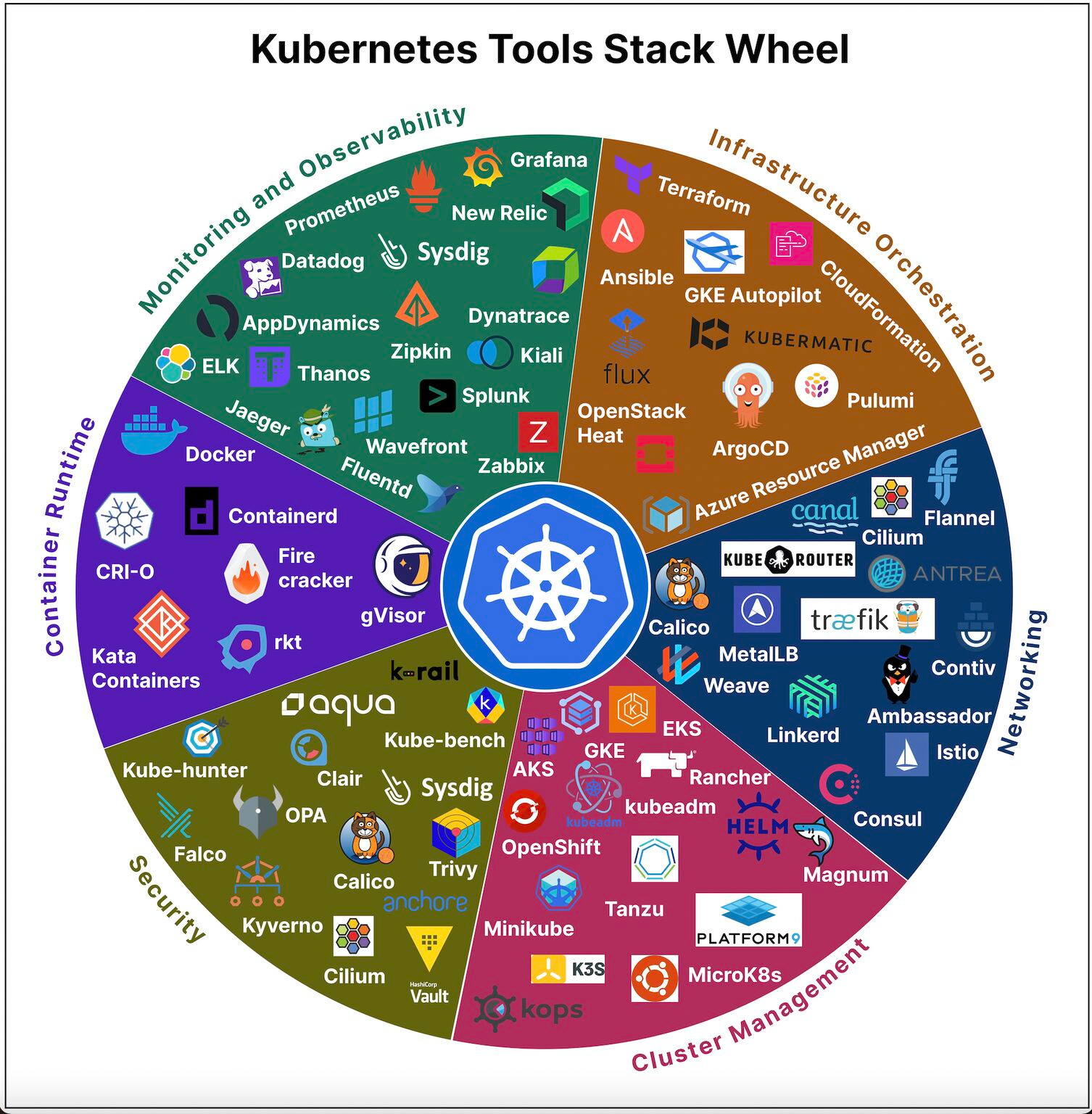
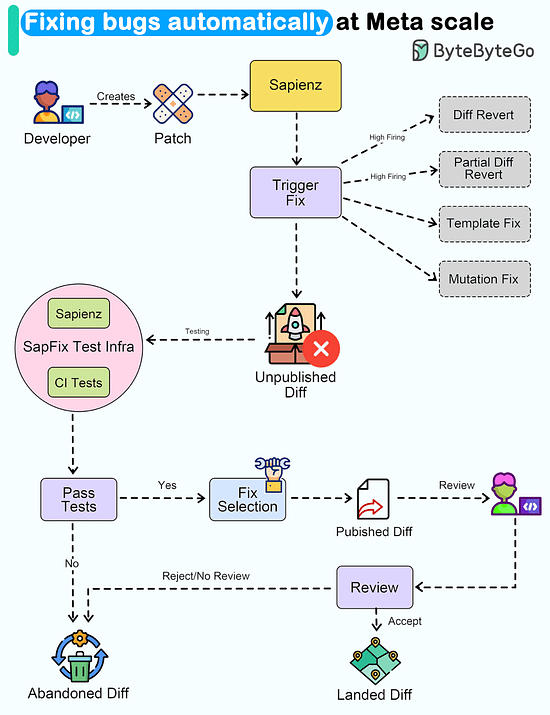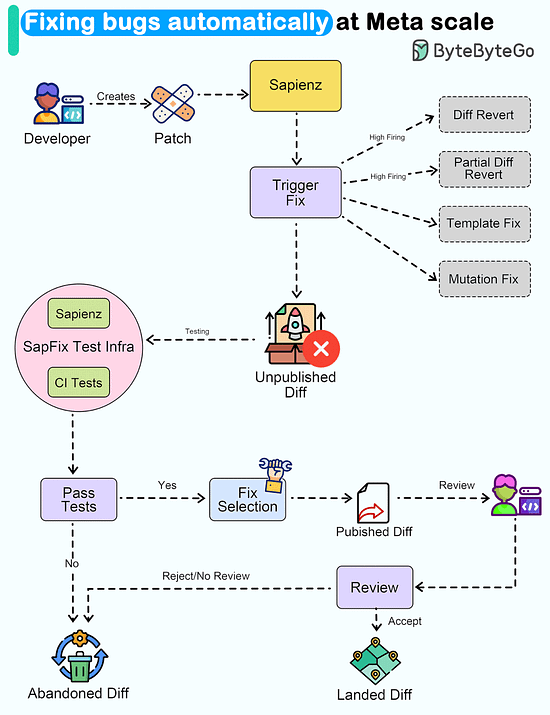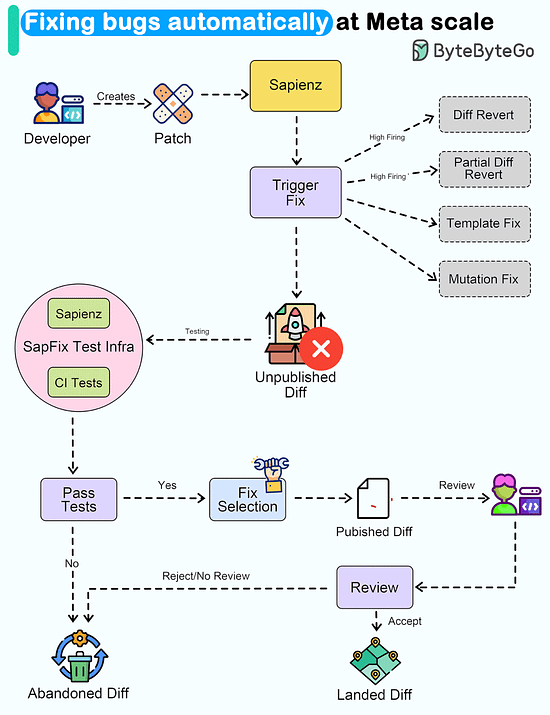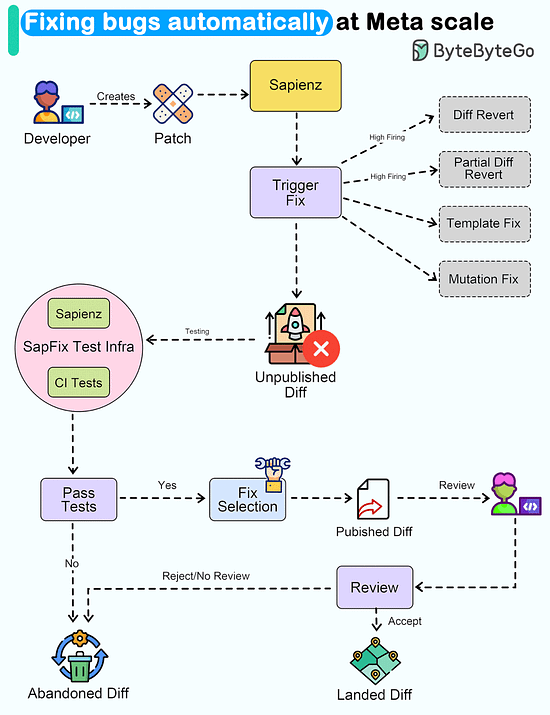
Latest articlesIf you’re not a paid subscriber, here’s what you missed this month. To receive all the full articles and support ByteByteGo, consider subscribing: Kubernetes Tools Stack WheelKubernetes tools continually evolve, offering enhanced capabilities and simplifying container orchestration. The innumerable choice of tools speaks about the vastness and the scope of this dynamic ecosystem, catering to diverse needs in the world of containerization. In fact, getting to know about the existing tools themselves can be a significant endeavor. With new tools and updates being introduced regularly, staying informed about their features, compatibility, and best practices becomes essential for Kubernetes practitioners, ensuring they can make informed decisions and adapt to the ever-changing landscape effectively. Fixing bugs automatically at Meta ScaleWouldn't it be nice if a system could automatically detect and fix bugs for us Meta released a paper about how they automated end-to-end repair at the Facebook scale. Let's take a closer look. The goal of a tool called SapFix is to simplify debugging by automatically generating fixes for specific issues. How successful has SapFix been? Here are some details that have been made available:
Here’s how SapFix actually works:
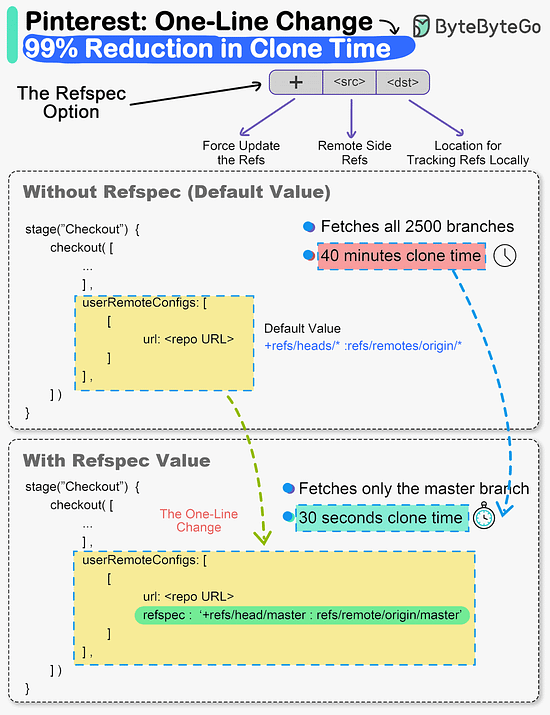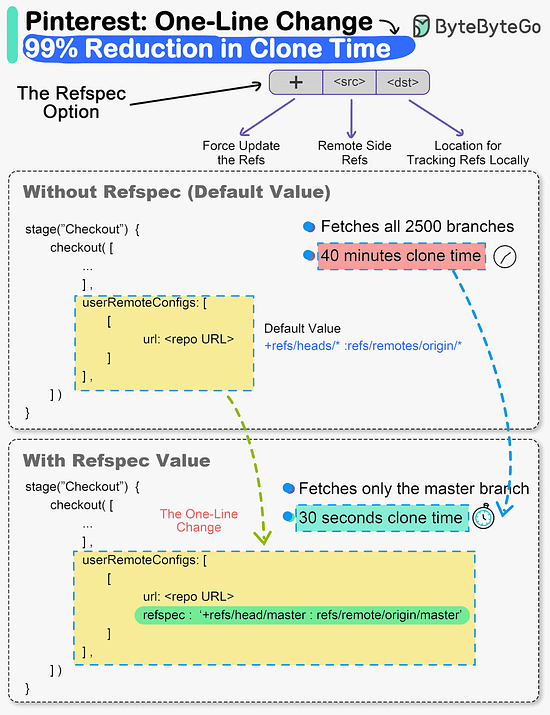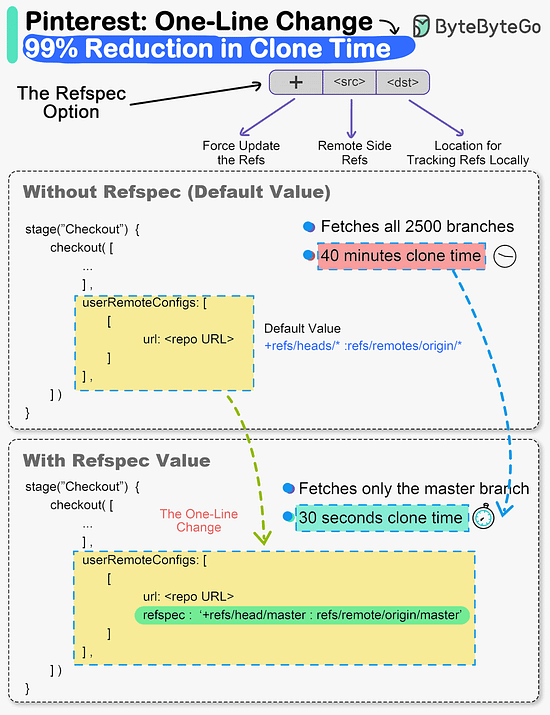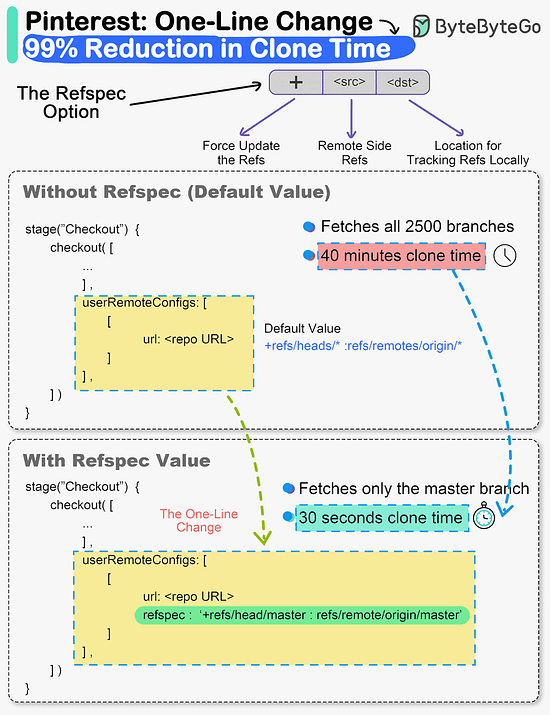
Reference: The one-line change that reduced clone times by a whopping 99%, says Pinterest.While it may sound cliché, small changes can definitely create a big impact. The Engineering Productivity team at Pinterest witnessed this first-hand. They made a small change in the Jenkins build pipeline of their monorepo codebase called Pinboard. And it brought down clone times from 40 minutes to a staggering 30 seconds. For reference, Pinboard is the oldest and largest monorepo at Pinterest. Some facts about it:
Cloning monorepos having a lot of code and history is time consuming. This was exactly what was happening with Pinboard. The build pipeline (written in Groovy) started with a “Checkout” stage where the repository was cloned for the build and test steps. The clone options were set to shallow clone, no fetching of tags and only fetching the last 50 commits. But it missed a vital piece of optimization. The Checkout step didn’t use the Git refspec option. This meant that Git was effectively fetching all refspecs for every build. For the Pinboard monorepo, it meant fetching more than 2500 branches. 𝐒𝐨 - 𝐰𝐡𝐚𝐭 𝐰𝐚𝐬 𝐭𝐡𝐞 𝐟𝐢𝐱? The team simply added the refspec option and specified which ref they cared about. It was the “master” branch in this case. This single change allowed Git clone to deal with only one branch and significantly reduced the overall build time of the monorepo. Reference: SPONSOR USGet your product in front of more than 500,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com. © 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:36 - 9 Mar 2024