- Mailing Lists
- in
- EP109: Top 6 Tools to Turn Code into Beautiful Diagrams
Archives
- By thread 5200
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 11
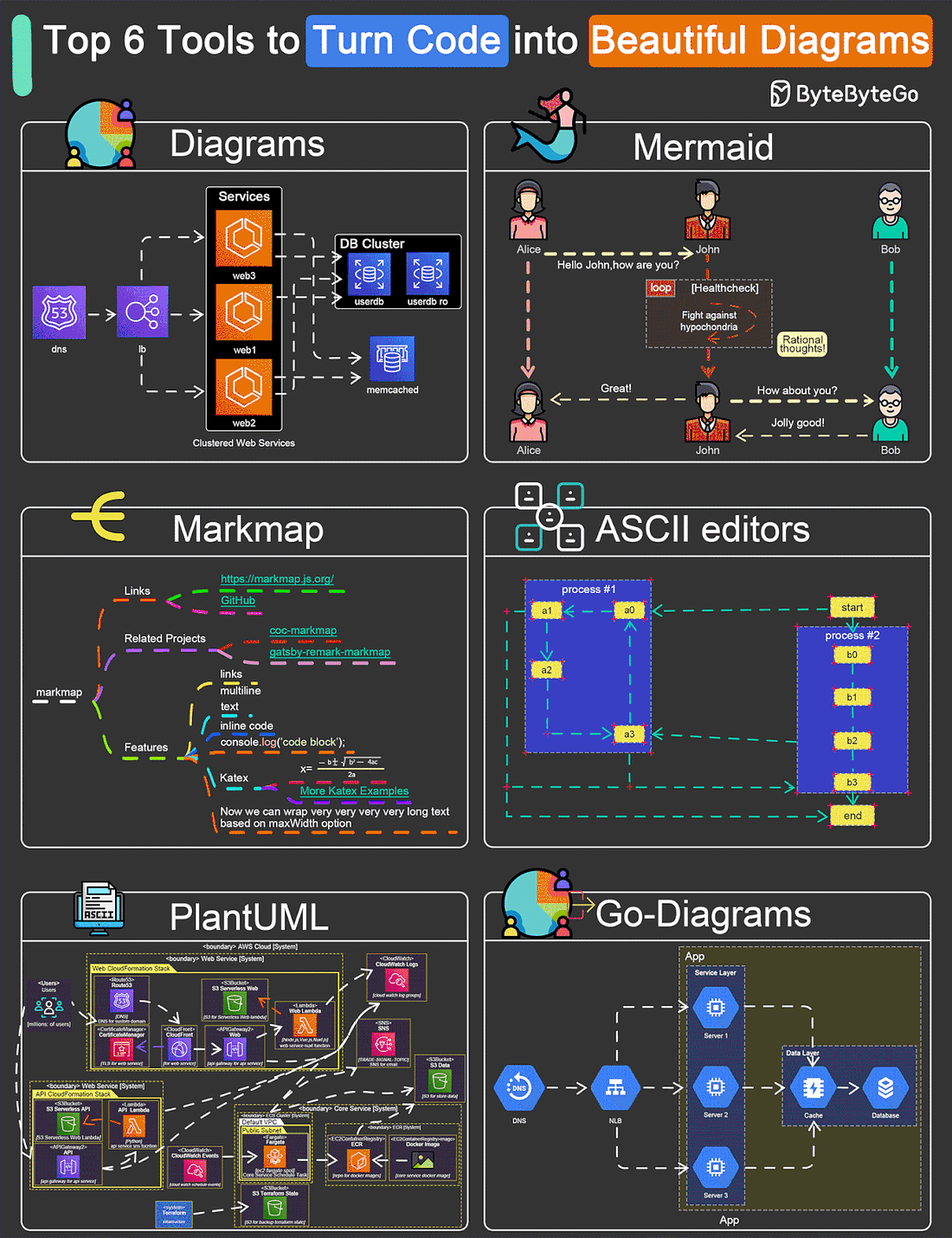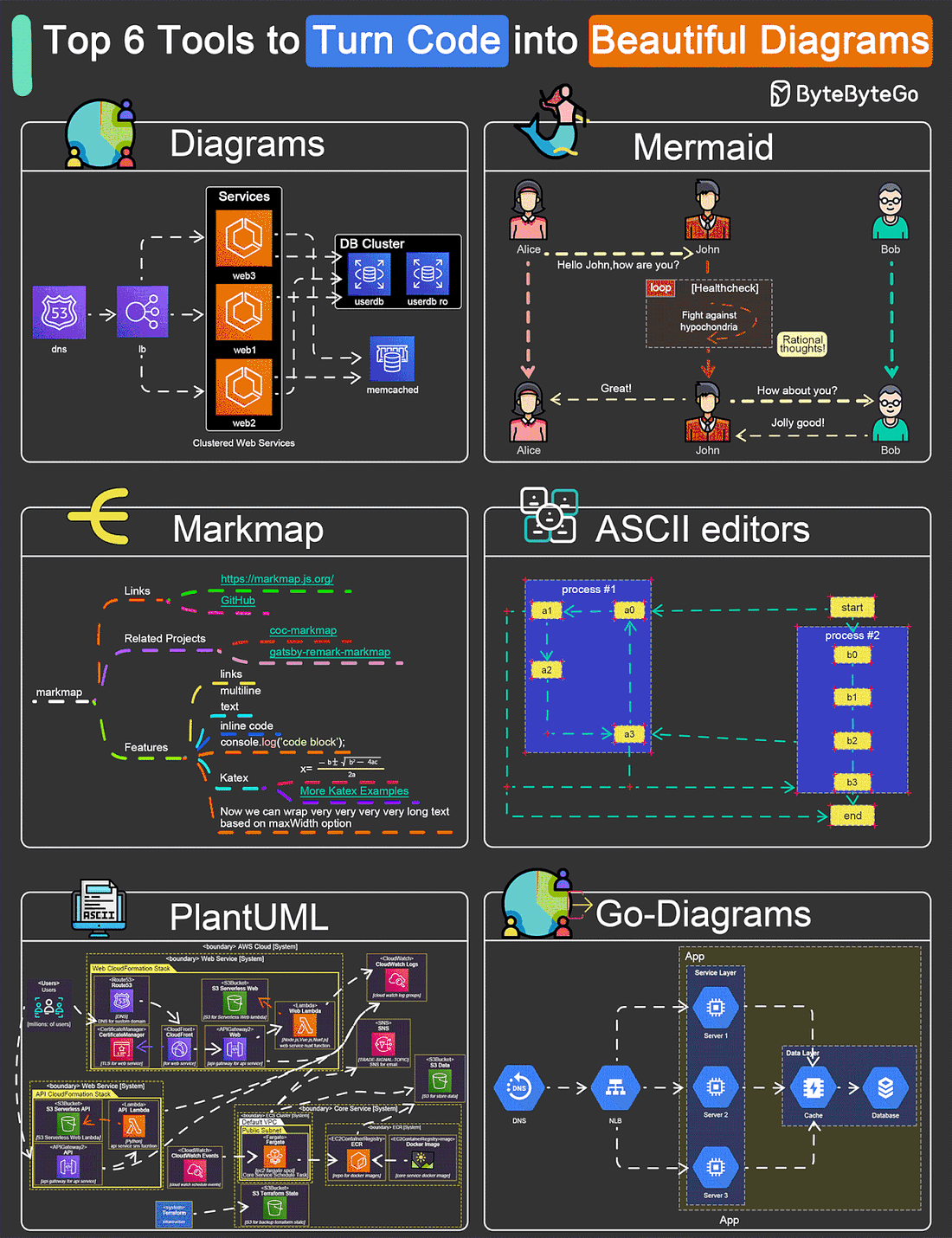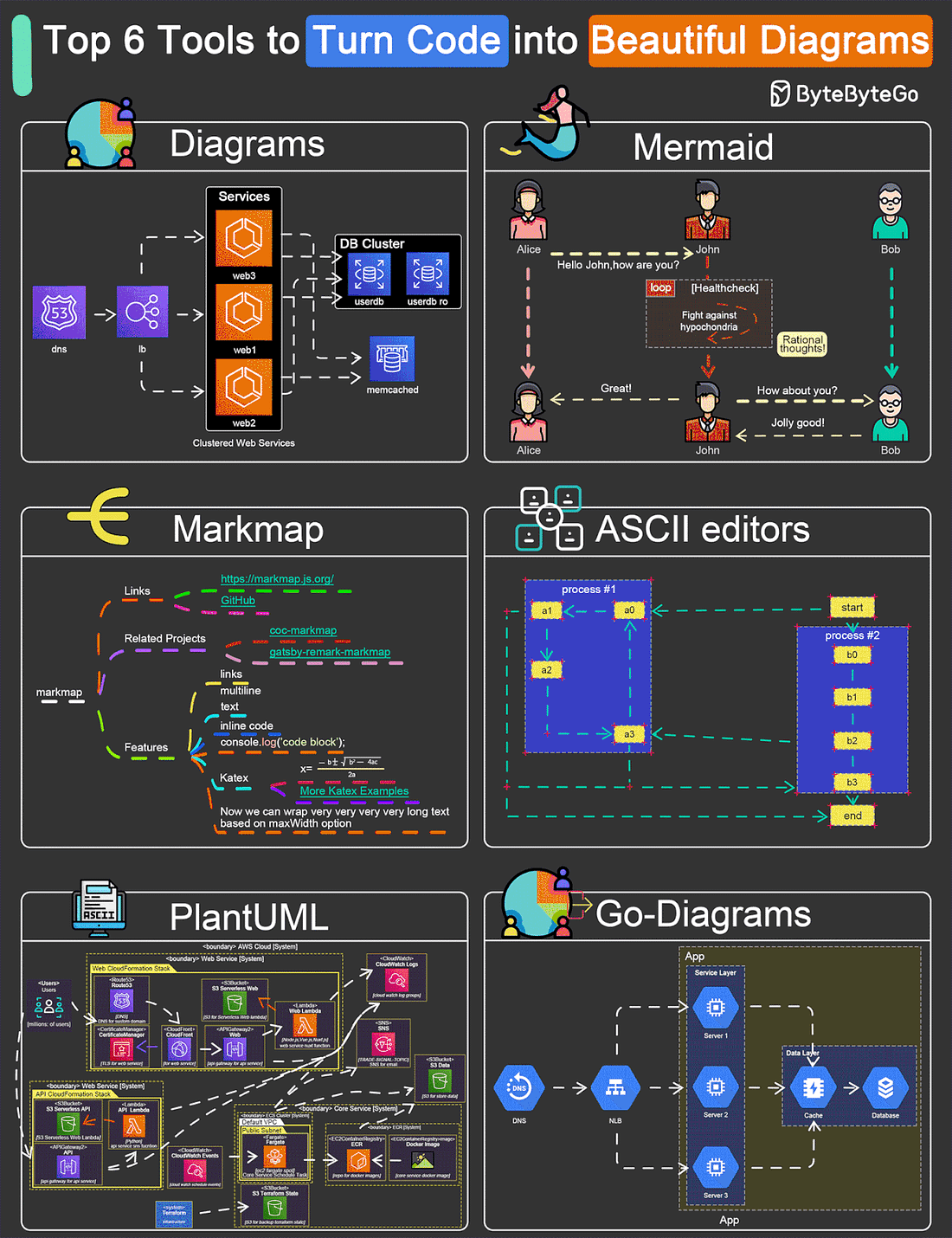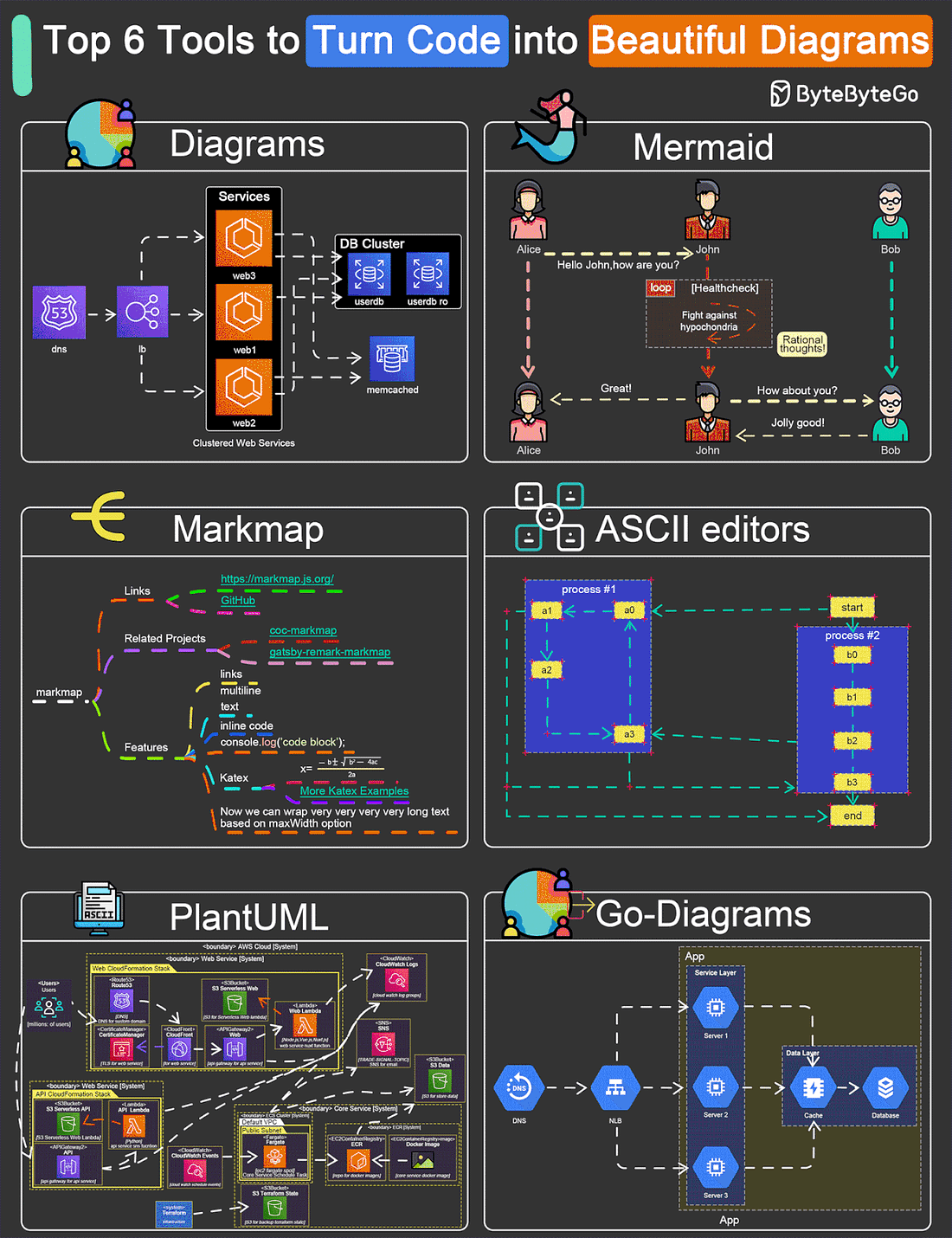
EP109: Top 6 Tools to Turn Code into Beautiful Diagrams
EP109: Top 6 Tools to Turn Code into Beautiful Diagrams
This week’s system design refresher:
POST/CON 24 | April 30 - May 1 (Sold Out)(Sponsored)POST/CON 24 is sold out, but you can still join the waitlist here for a complimentary ticket and be the first to know if tickets become available! You’ll hear keynote speakers, see demos of new Postman features, watch an incredible panel discussion on AI—and so much more. If you can’t join us in person, mark your calendar and save this link to check out the livestream of it all on May 1, from 9 am - 11:30 am PDT. Top 9 Must-Read Blogs for Engineers Top 6 Tools to Turn Code into Beautiful Diagrams
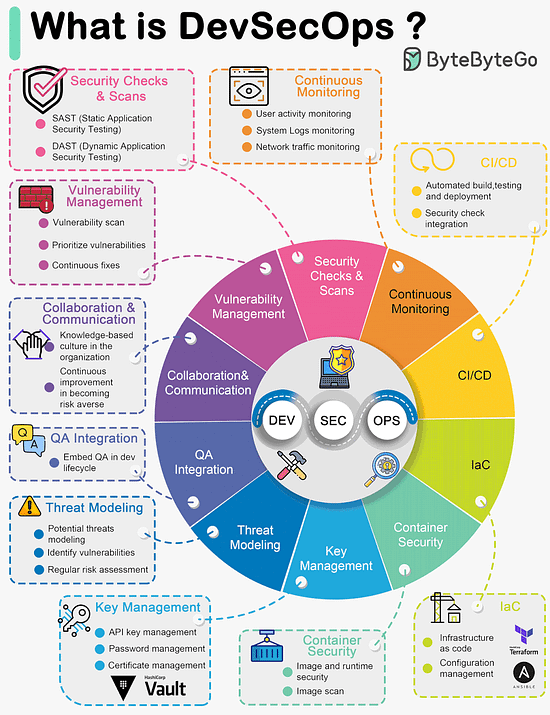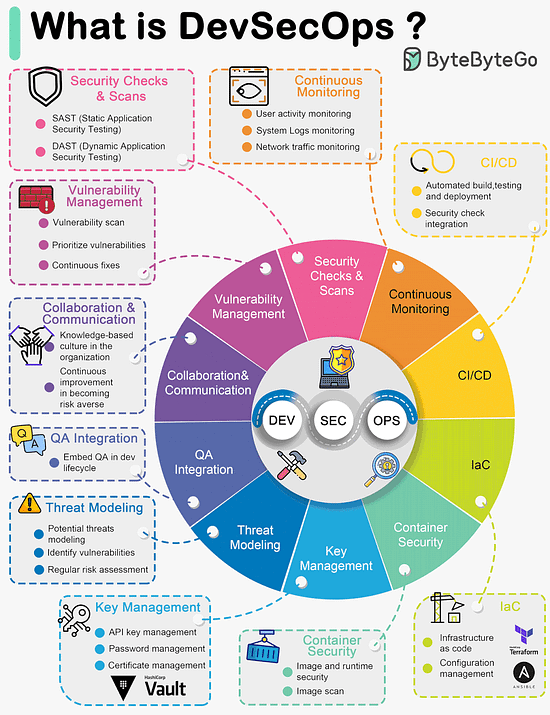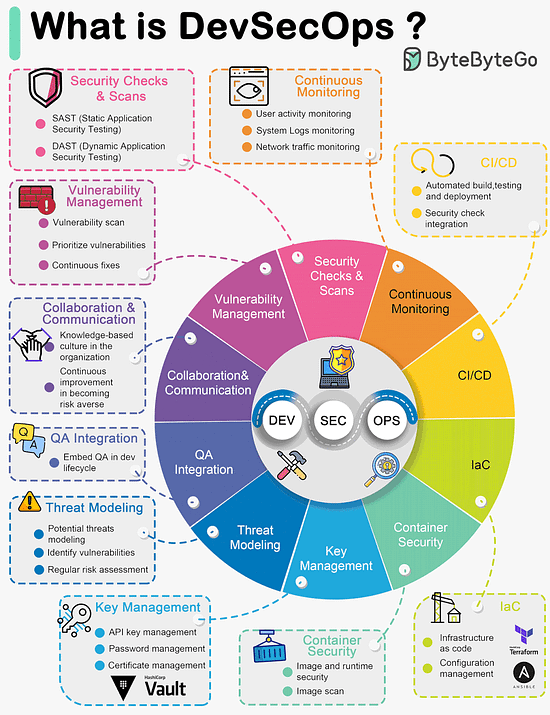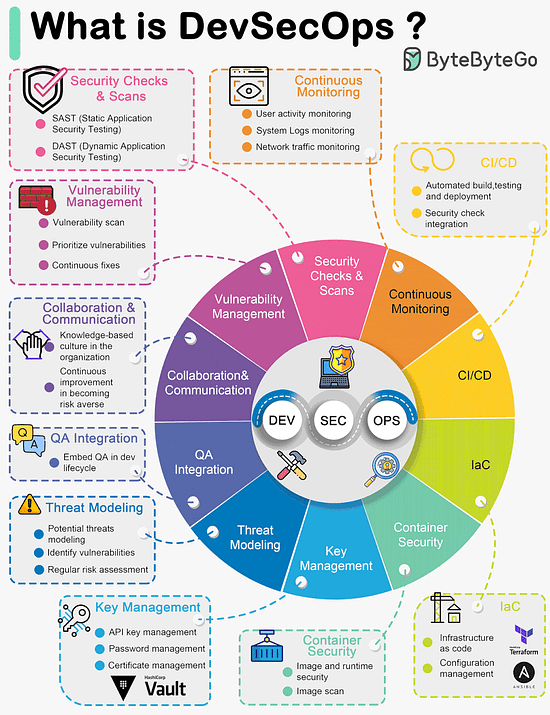
Over to you: Did we miss anything? What's your favorite? Latest articlesIf you’re not a paid subscriber, here’s what you missed. To receive all the full articles and support ByteByteGo, consider subscribing: What is DevSecOps?DevSecOps emerged as a natural evolution of DevOps practices with a focus on integrating security into the software development and deployment process. The term "DevSecOps" represents the convergence of Development (Dev), Security (Sec), and Operations (Ops) practices, emphasizing the importance of security throughout the software development lifecycle.
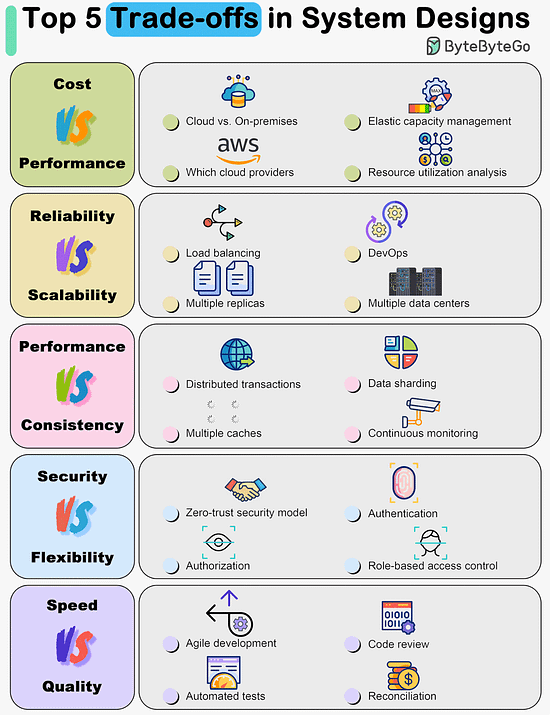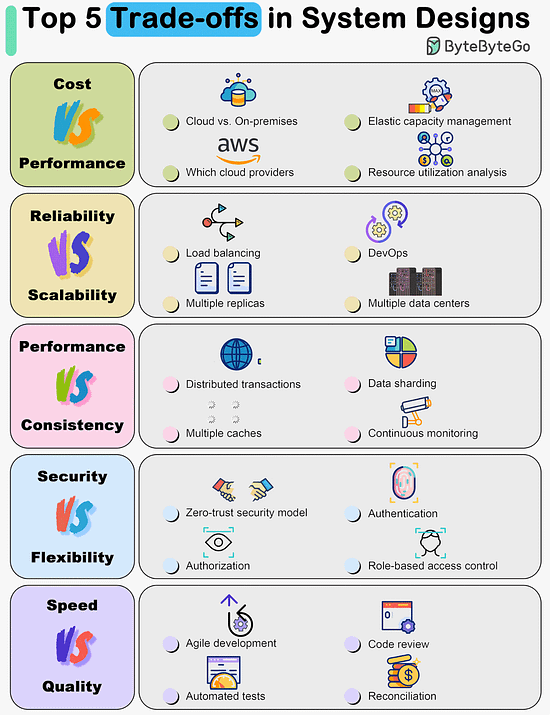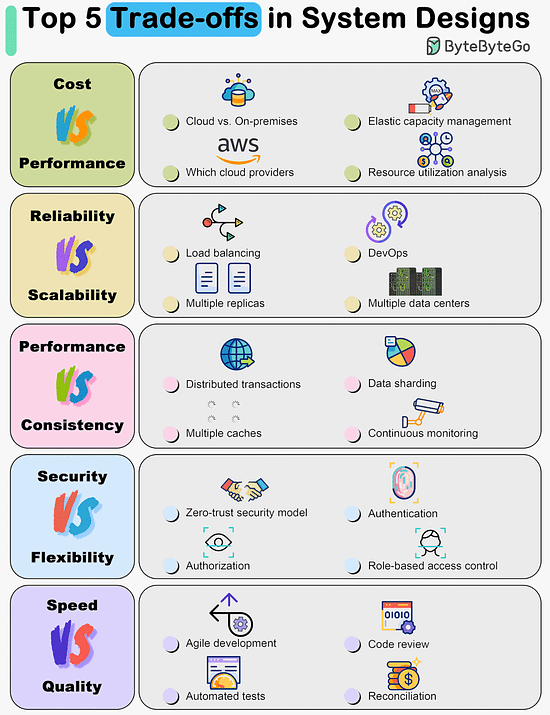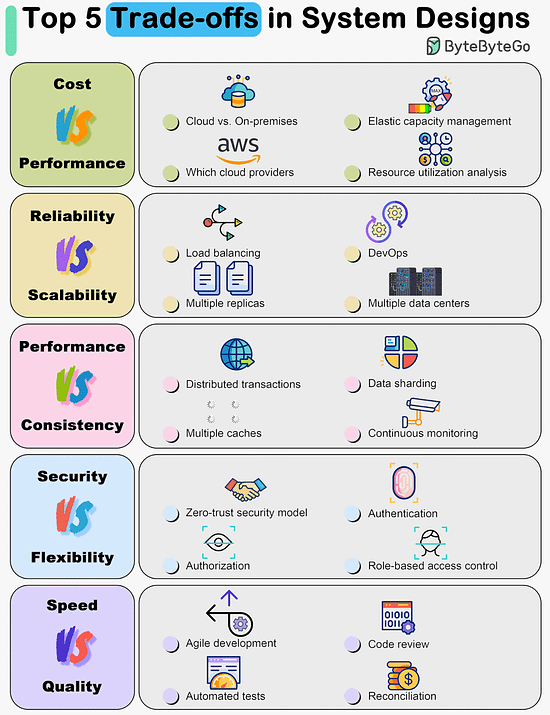
Top 5 Trade-offs in System DesignsEverything is a trade-off.
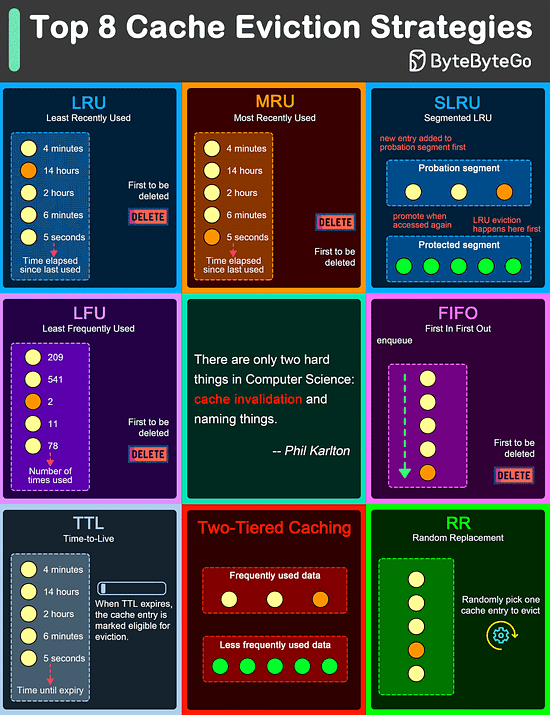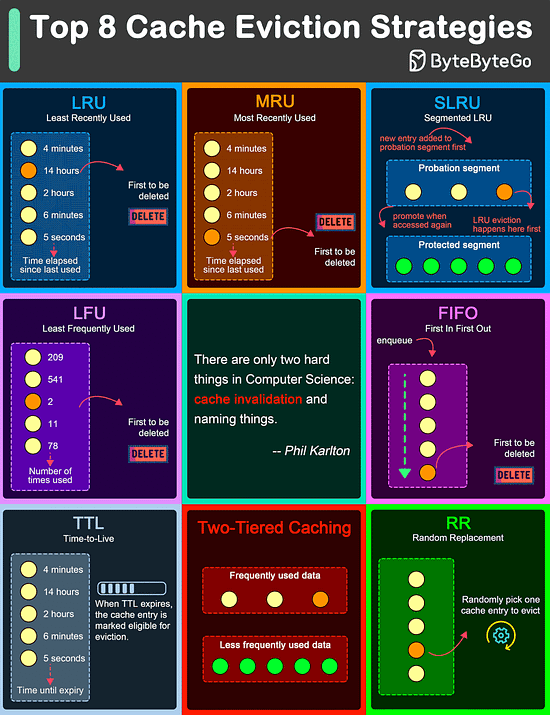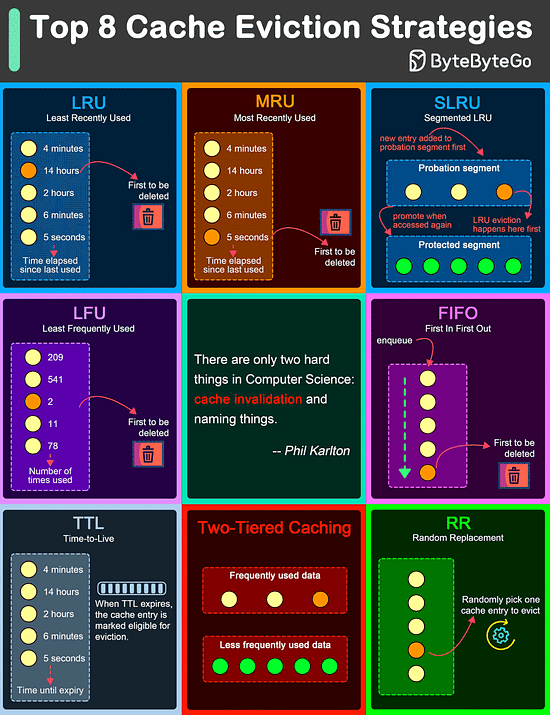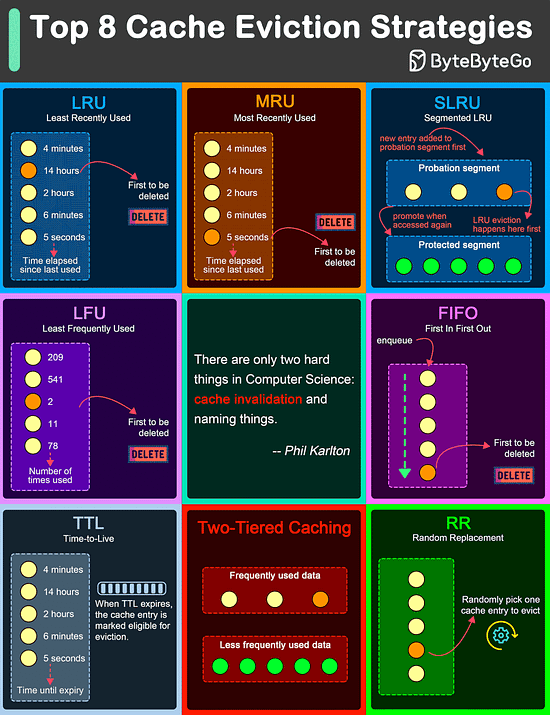
Over to you: What trade-offs have you made in the past? Top 8 Cache Eviction Strategies
SPONSOR USGet your product in front of more than 500,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com. © 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:46 - 27 Apr 2024