- Mailing Lists
- in
- EP117: What makes HTTP2 faster than HTTP1?
Archives
- By thread 5363
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 176
EP117: What makes HTTP2 faster than HTTP1?
EP117: What makes HTTP2 faster than HTTP1?
This week’s system design refresher:
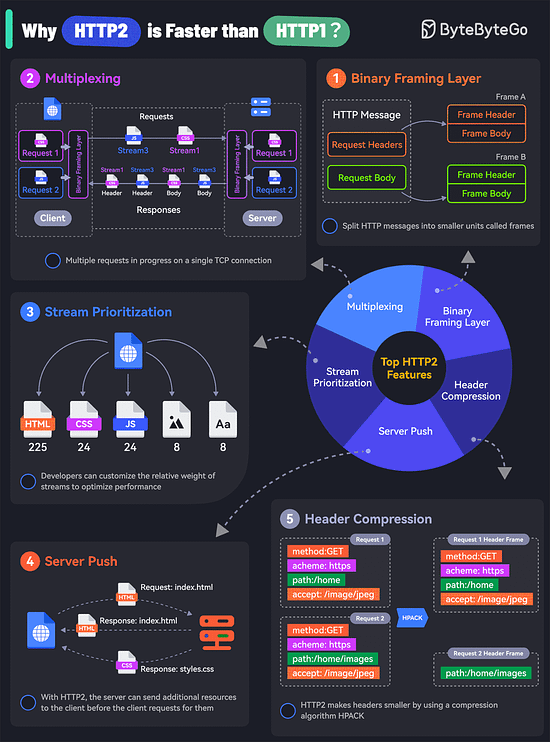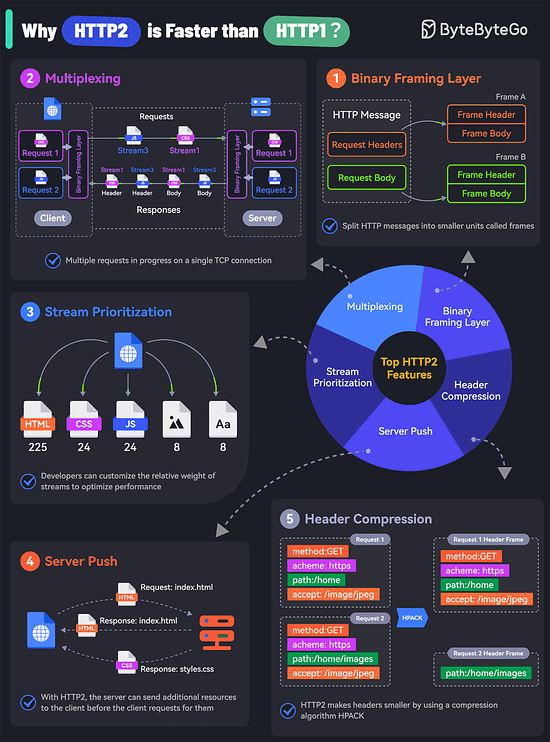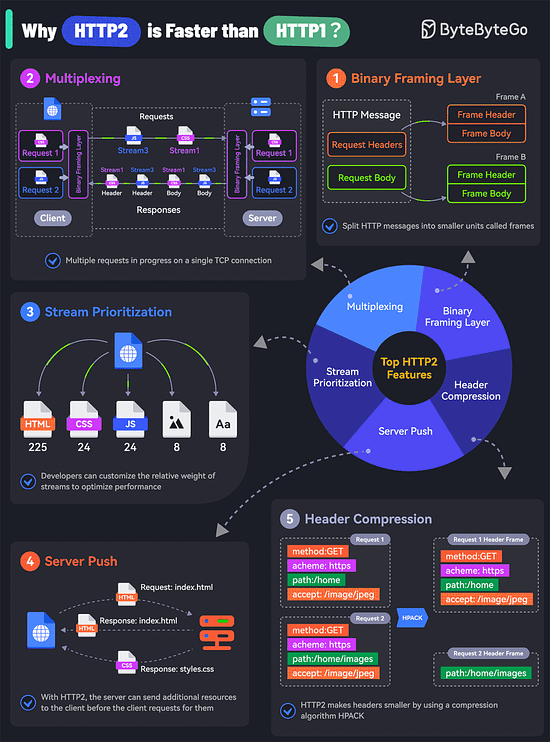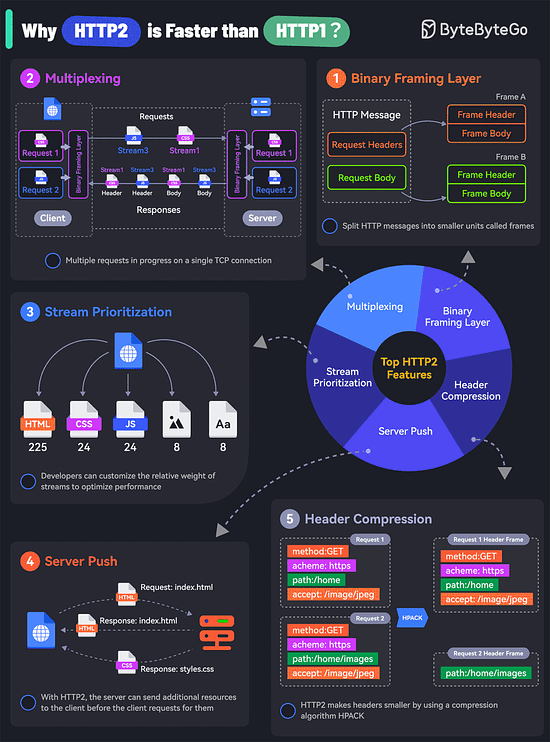
Collaborating on APIs Is Easier with Postman (Sponsored)API Collaboration improves developer productivity by empowering producers and consumers to share, discover, and reuse high-quality API assets. Postman revolutionizes the experience of collaborative API development with Postman Collections and Workspaces. Used together, they enable API design, testing, and documentation, while providing a shared canvas for collaborating on API assets. Learn how companies like Cvent, Visma, Built Technologies, and Amadeus use Postman to collaborate more easily and deliver better APIs faster. Kafka vs. RabbitMQ vs. Messaging Middleware vs. Pulsar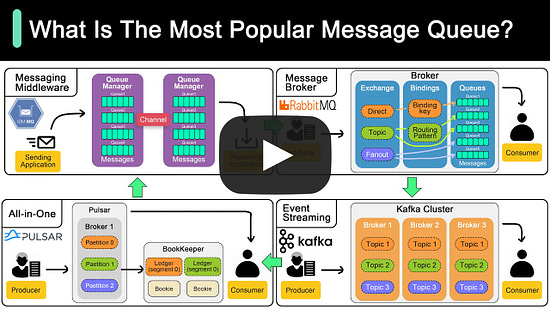 What makes HTTP2 faster than HTTP1?The key features of HTTP2 play a big role in this. Let’s look at them:
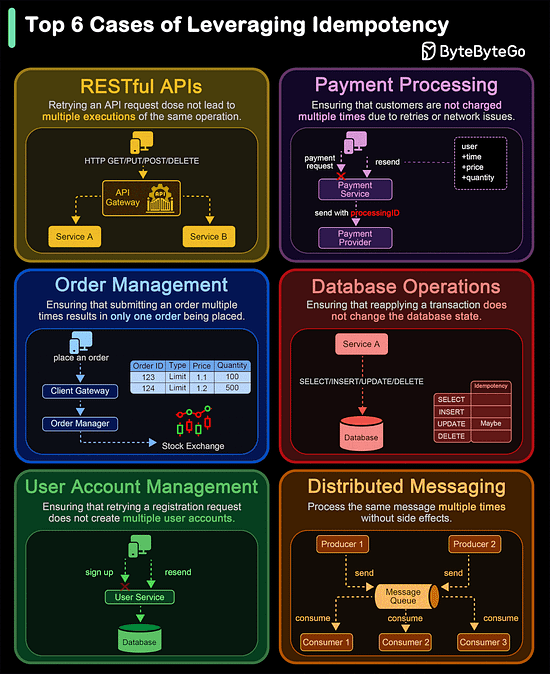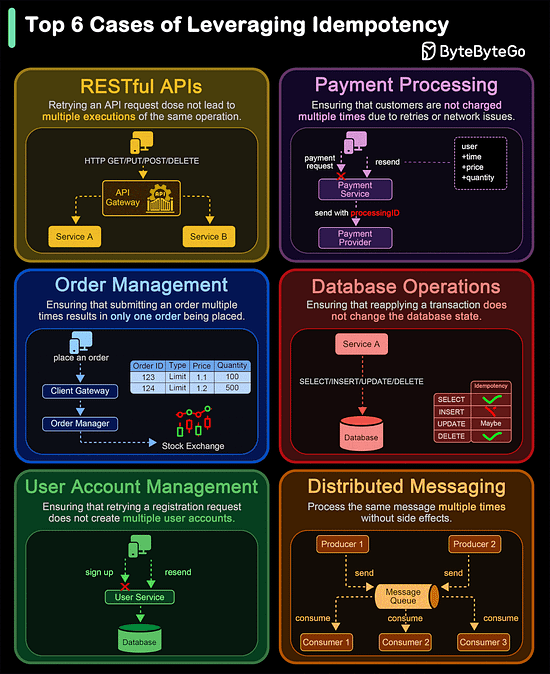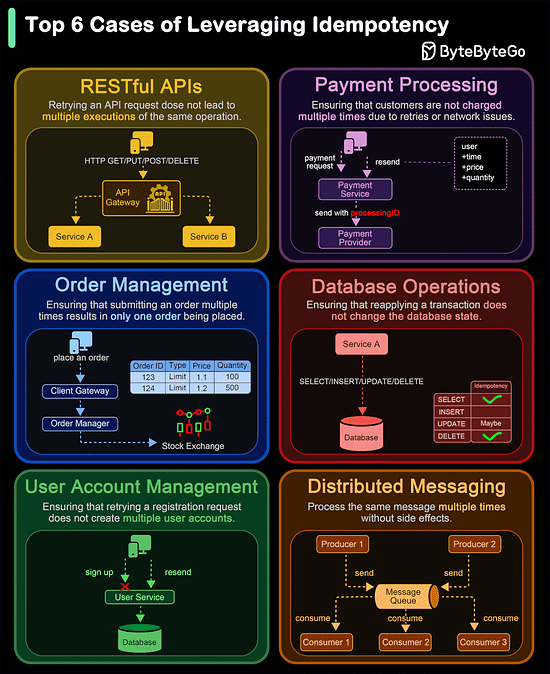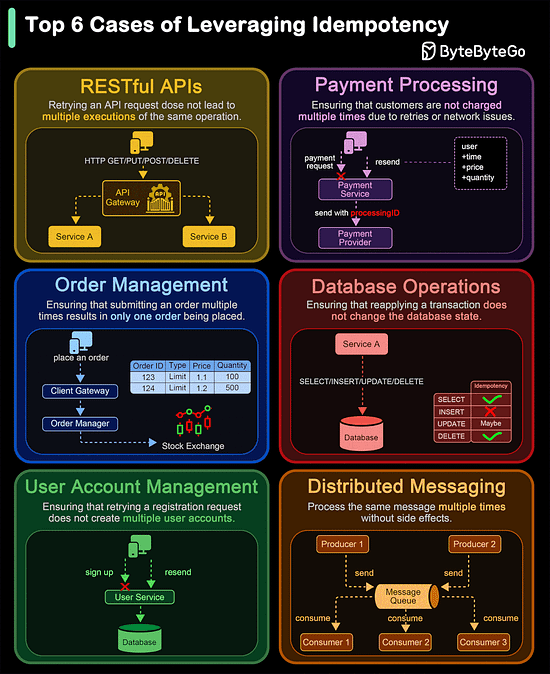
Of course, despite these features, HTTP2 can also be slow depending on the exact technical scenario. Therefore, developers need to test and optimize things to maximize the benefits of HTTP2. Latest articlesIf you’re not a paid subscriber, here’s what you missed. To receive all the full articles and support ByteByteGo, consider subscribing: Top 6 Cases to Apply IdempotencyIdempotency is essential in various scenarios, particularly where operations might be retried or executed multiple times. Here are the top 6 use cases where idempotency is crucial:
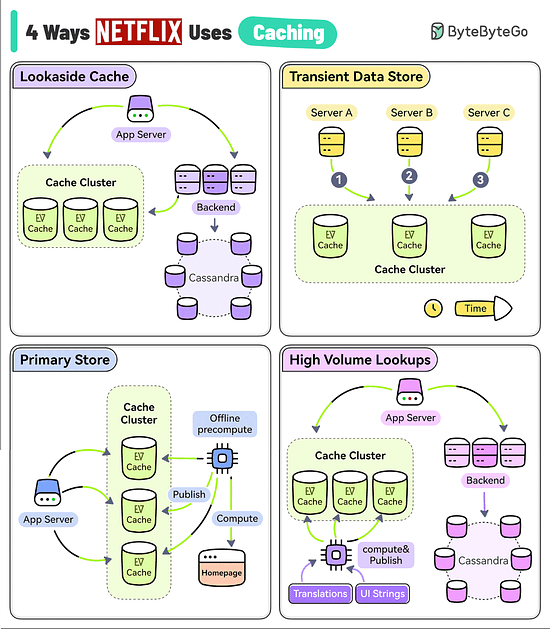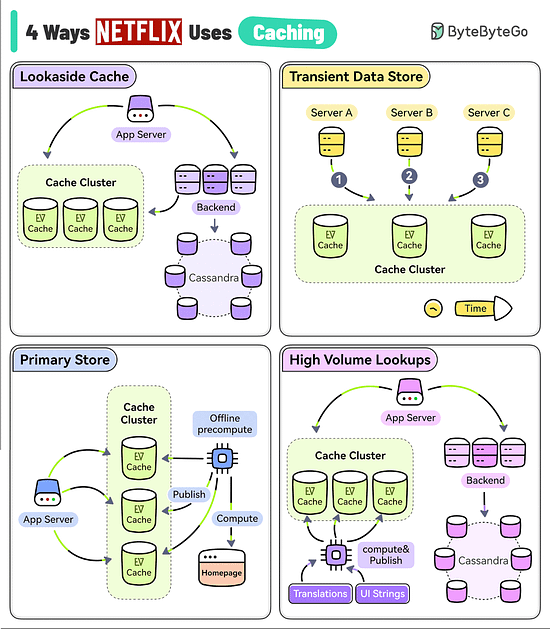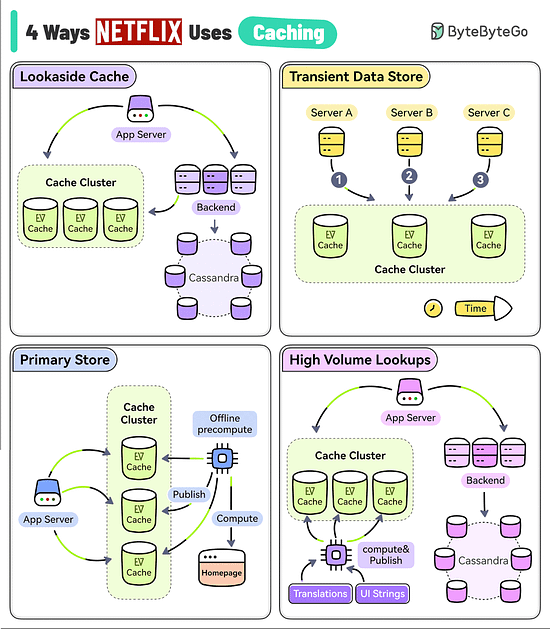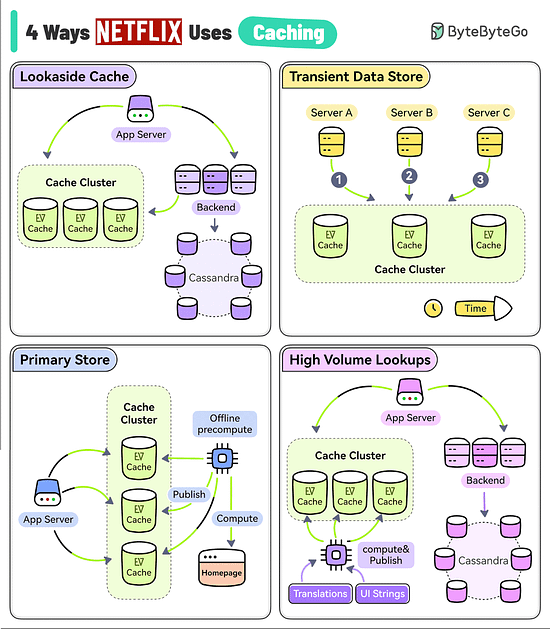
4 Ways Netflix Uses Caching to Hold User AttentionThe goal of Netflix is to keep you streaming for as long as possible. But a user’s typical attention span is just 90 seconds. They use EVCache (a distributed key-value store) to reduce latency so that the users don’t lose interest.
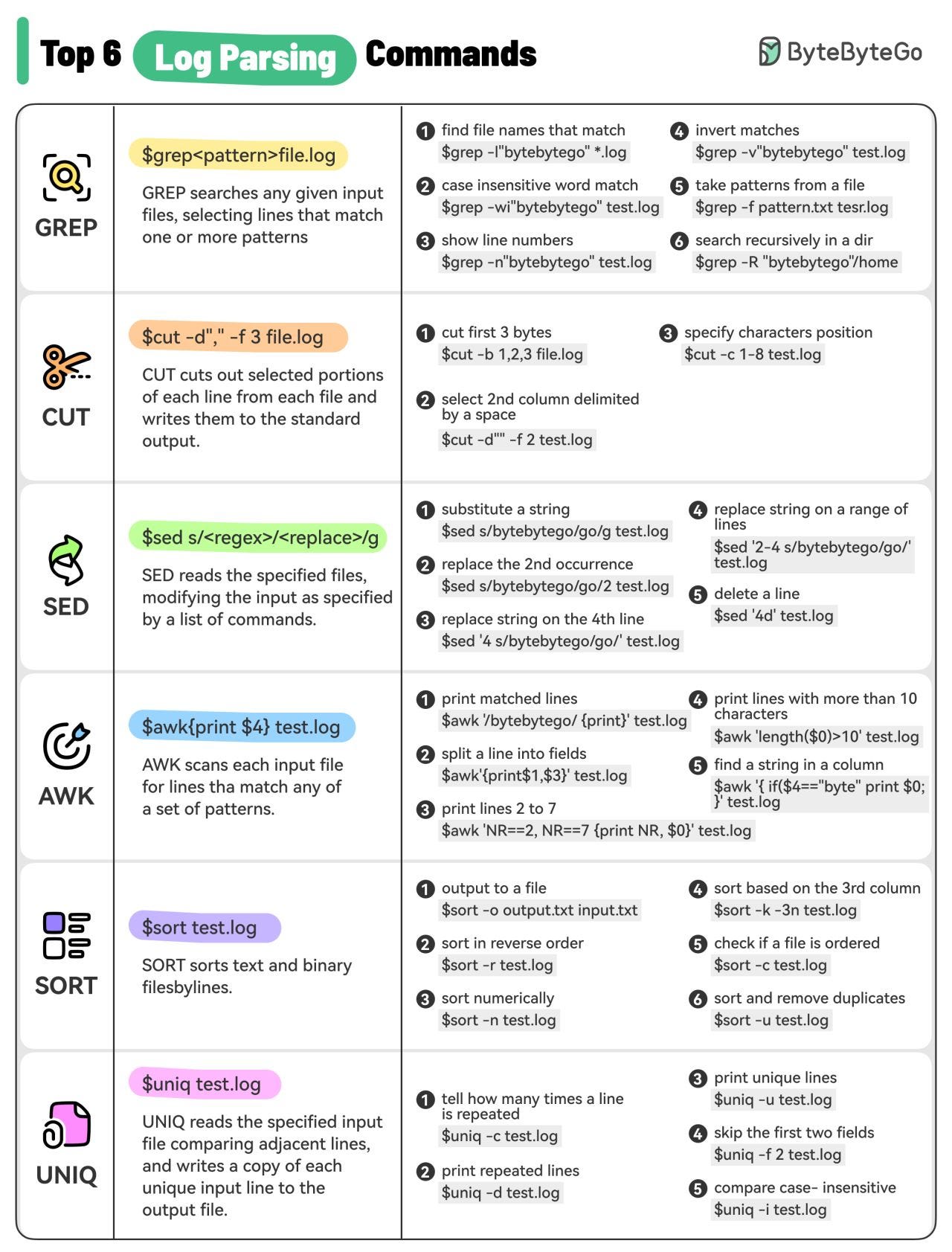
Reference: "Caching at Netflix: The Hidden Microservice" by Scott Mansfield Log Parsing Cheat SheetThe diagram below lists the top 6 log parsing commands.
These commands are often used in combination to quickly find useful information from the log files. For example, the below commands list the timestamps (column 2) when there is an exception happening for xxService. SPONSOR USGet your product in front of more than 500,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com © 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:36 - 22 Jun 2024