- Mailing Lists
- in
- EP135: Big Data Pipeline Cheatsheet for AWS, Azure, and Google Cloud
Archives
- By thread 4937
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 48
EP135: Big Data Pipeline Cheatsheet for AWS, Azure, and Google Cloud
EP135: Big Data Pipeline Cheatsheet for AWS, Azure, and Google Cloud
The Enterprise Ready Conference for engineering leaders (Sponsored)The Enterprise Ready Conference is a one-day event in SF, bringing together product and engineering leaders shaping the future of enterprise SaaS. This week’s system design interview:
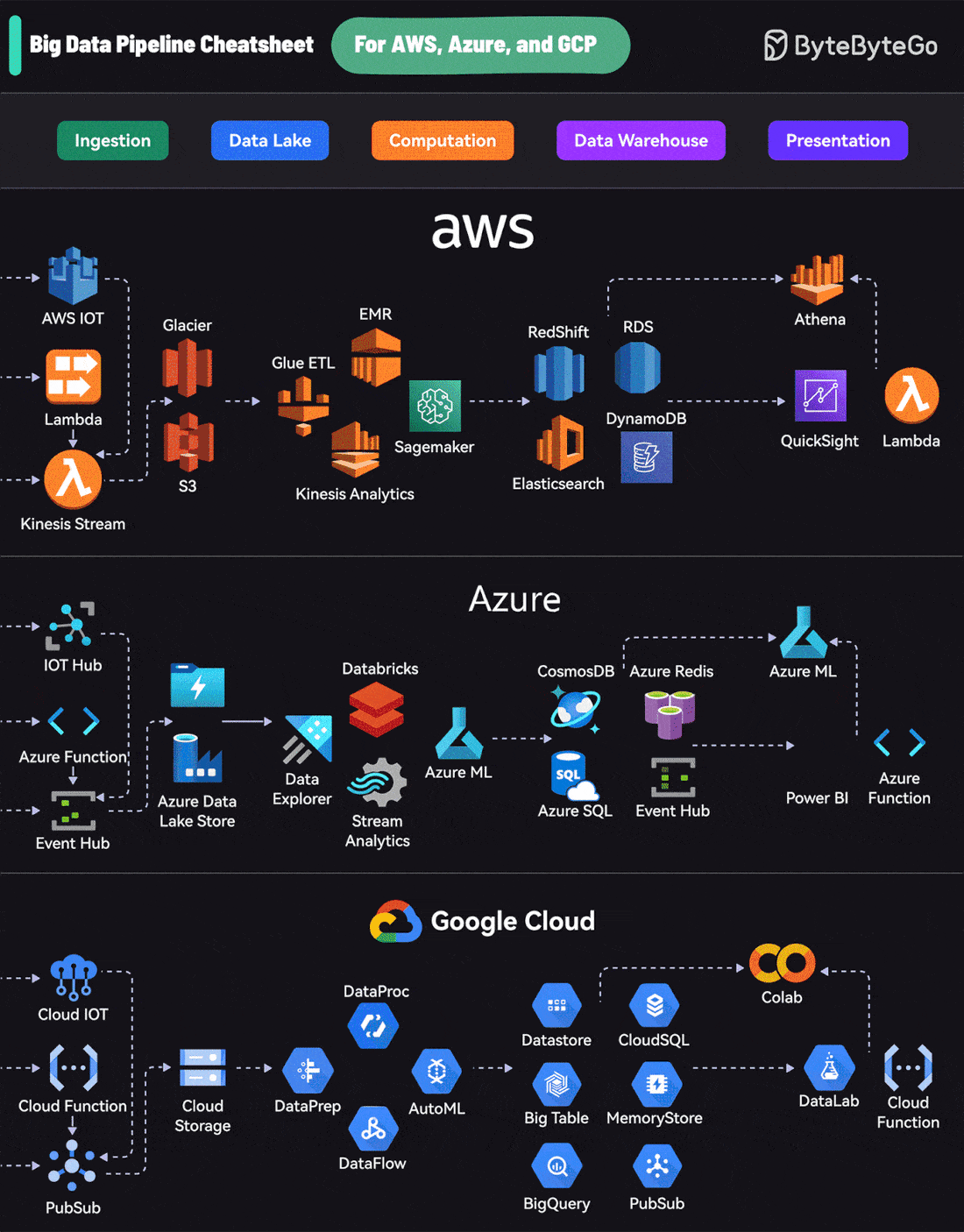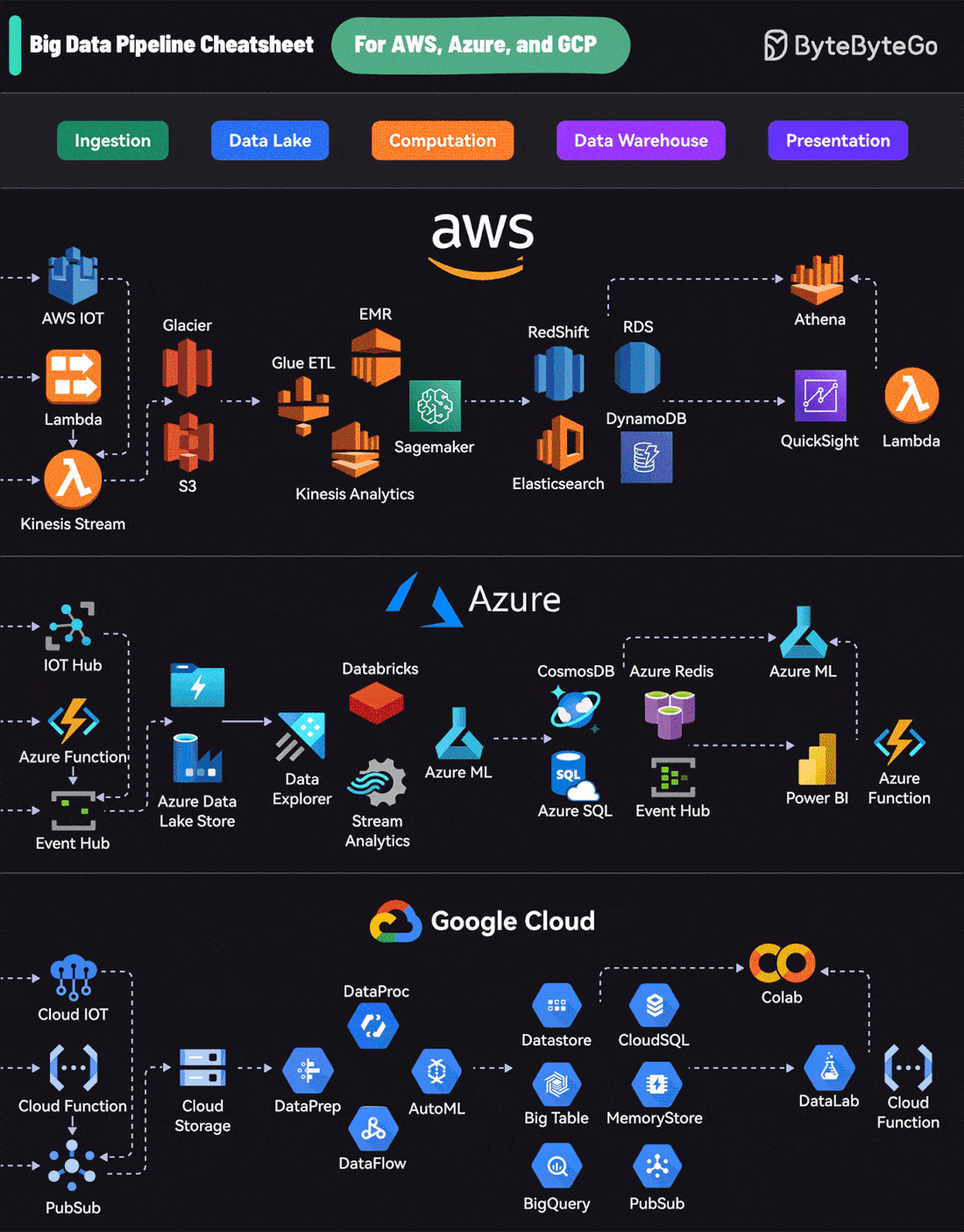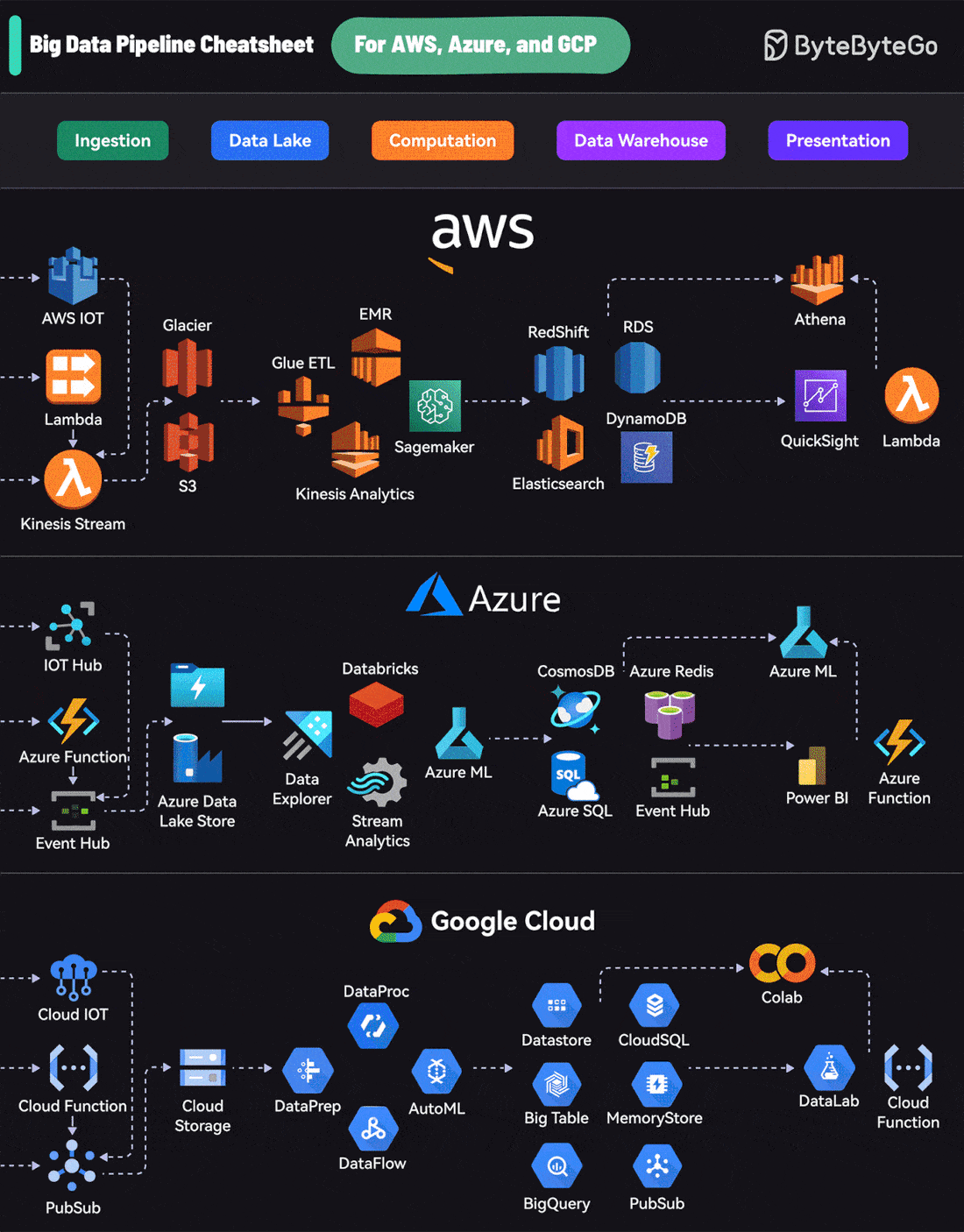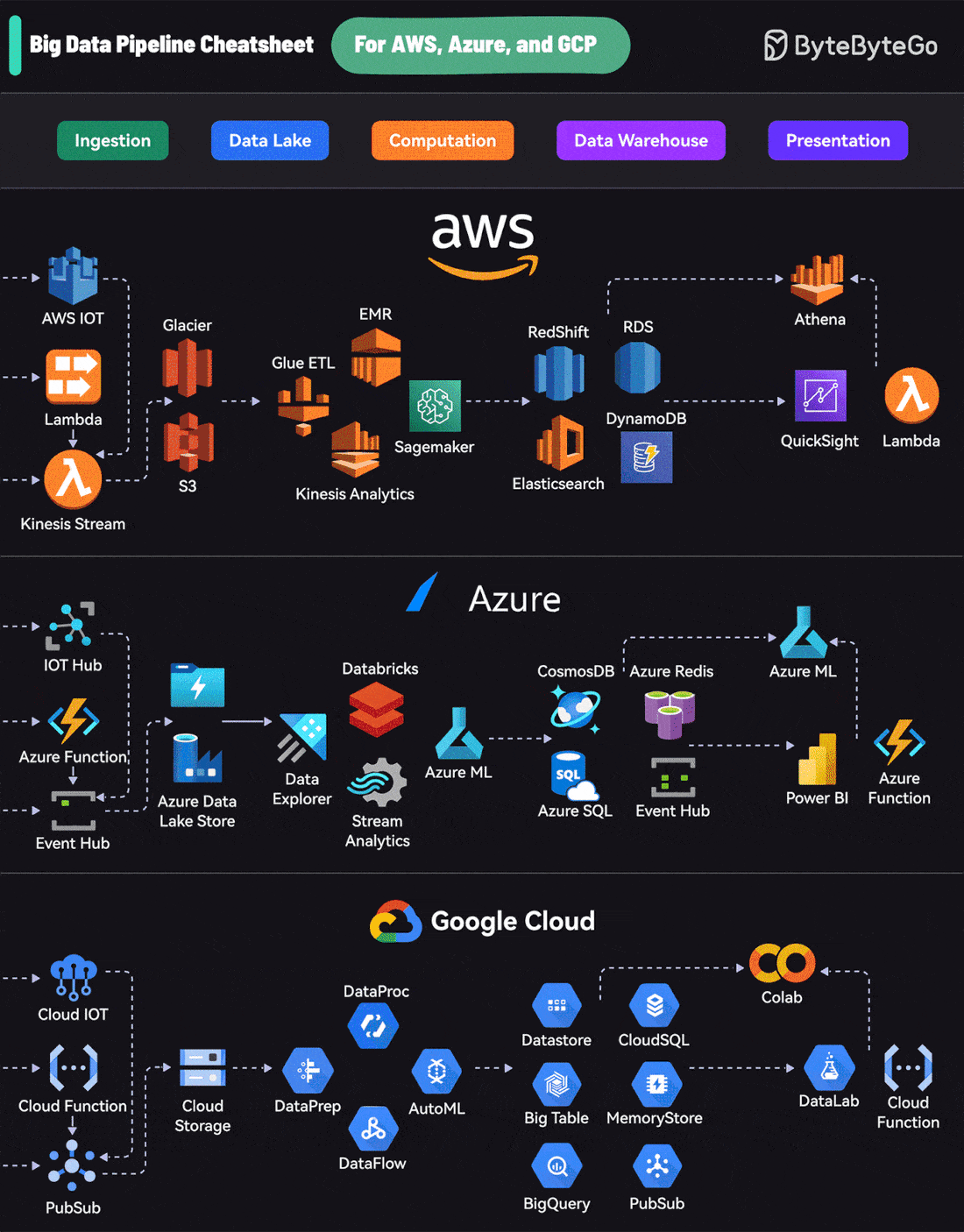
Big Data Pipeline Cheatsheet for AWS, Azure, and Google CloudEach platform offers a comprehensive suite of services that cover the entire lifecycle:
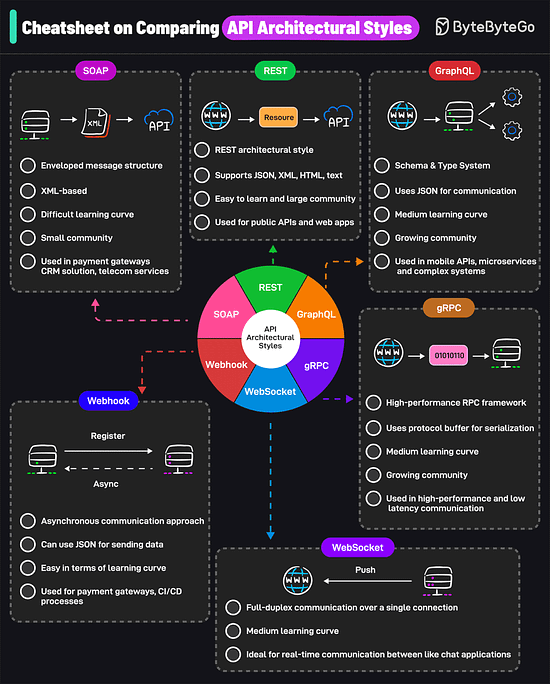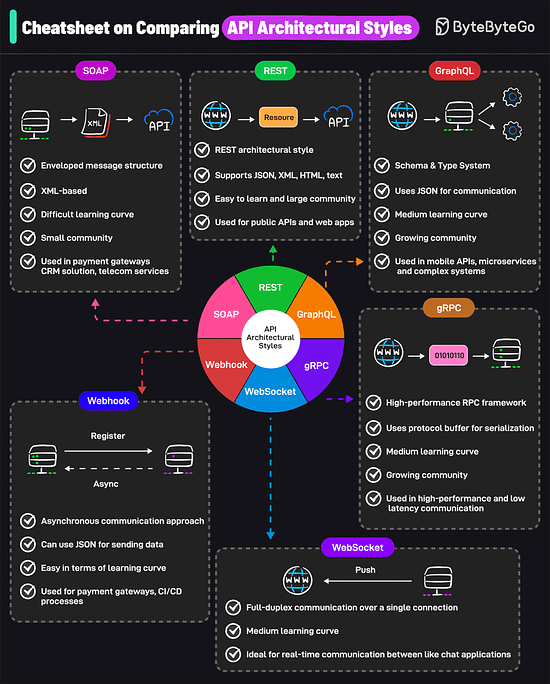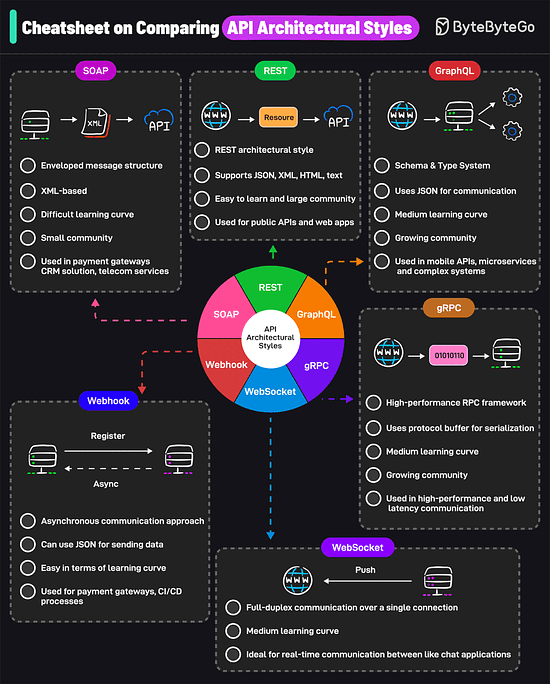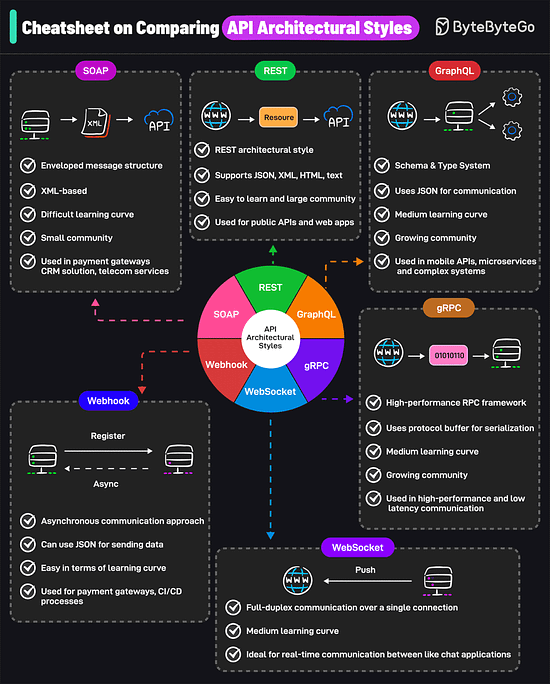
AWS uses services like Kinesis for data streaming, S3 for storage, EMR for processing, RedShift for warehousing, and QuickSight for visualization. A Cheatsheet on Comparing API Architectural StylesIt covers the 6 most popular API architectural styles:
Over to you: Which other architectural style have you used? 200+ hours of research on Advanced AI Tools for Technical Leaders & Professionals (Sponsored)Imagine cutting hours of manual work, solving complex issues instantly, and having AI optimise your entire workflow—making you 10x more productive. This FREE 3 hour Mini Crash Course on AI will help you save 16+ hours every week & put your 50% of your work on autopilot. Save your seat now (usually $399 but free for first 100 readers) You will learn 20+ AI tools & use AI to:
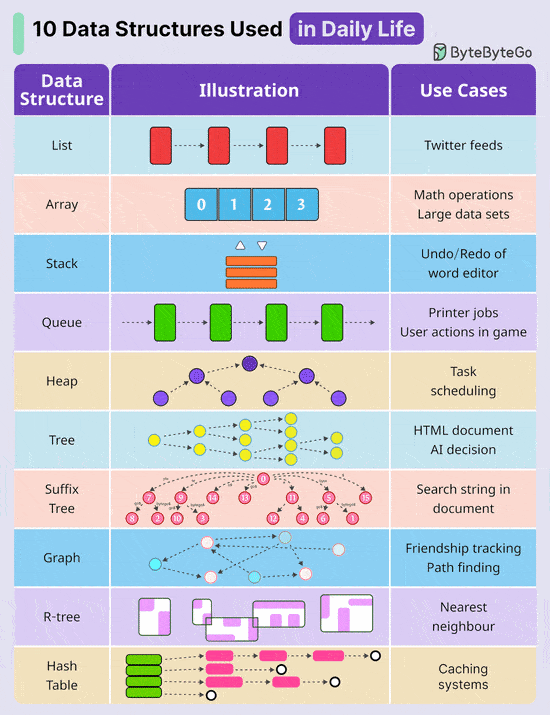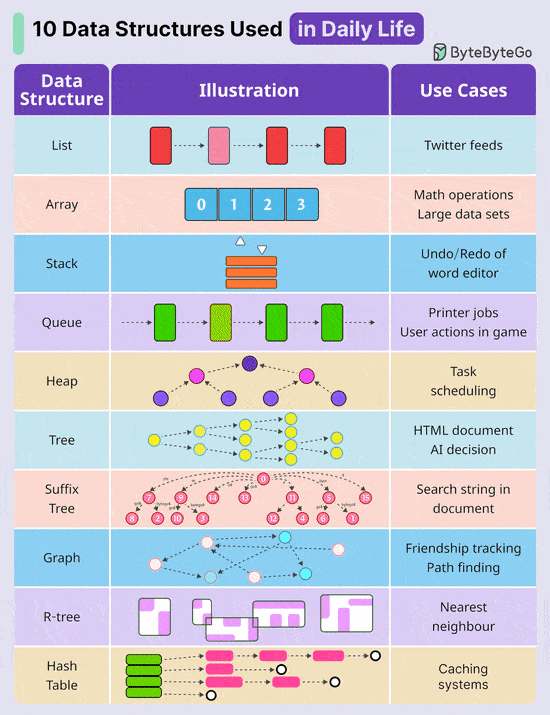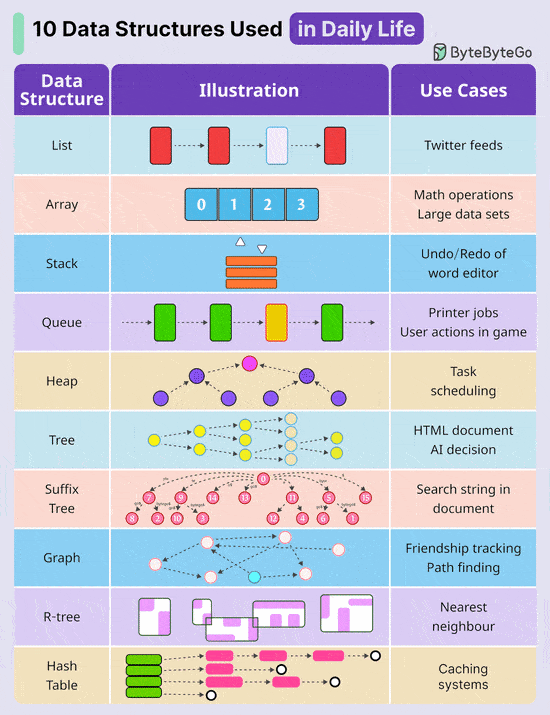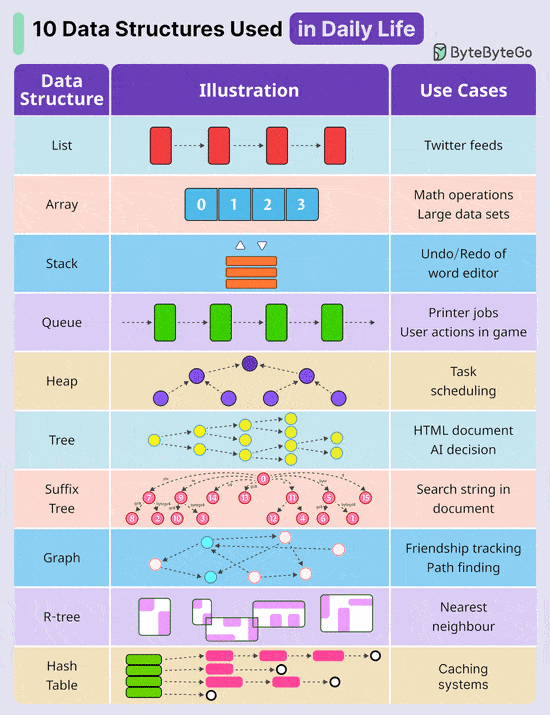
By letting AI handle these critical tasks, you’ll save hours each week, unlock more time for strategic thinking & innovation and spend more time with family. Register for the Crash Course Now 10 Key Data Structures We Use Every Day
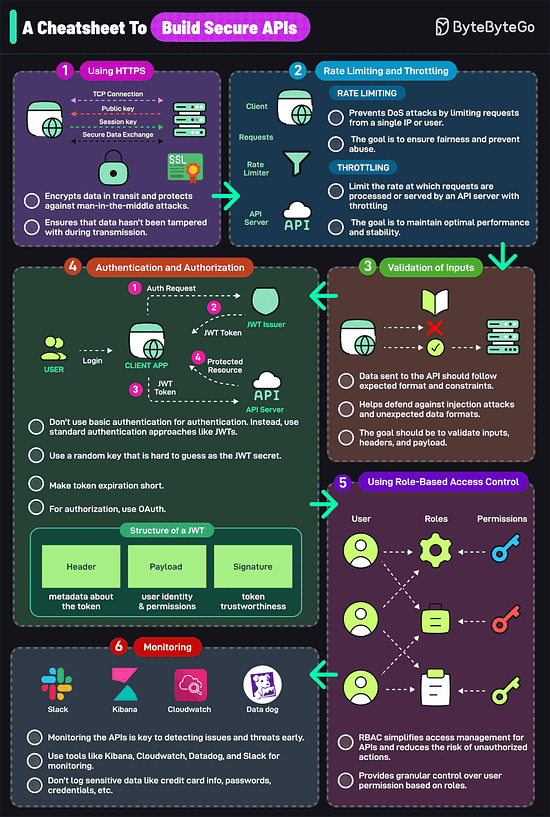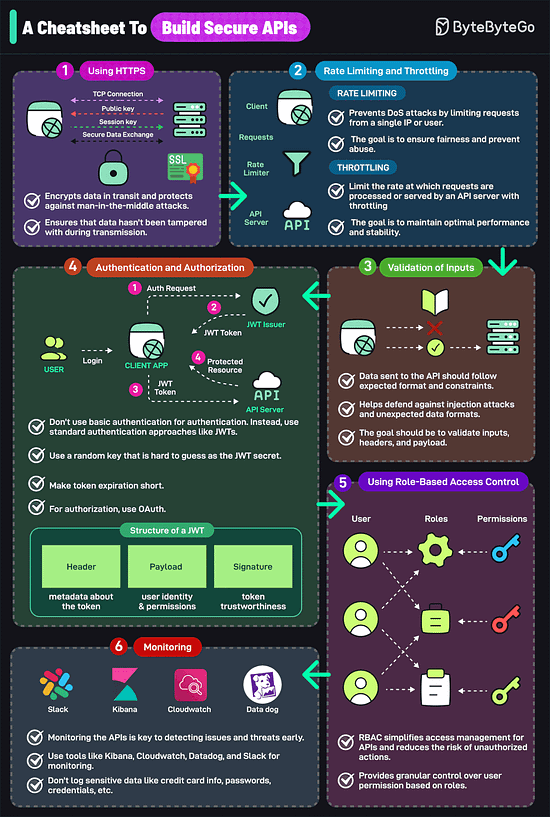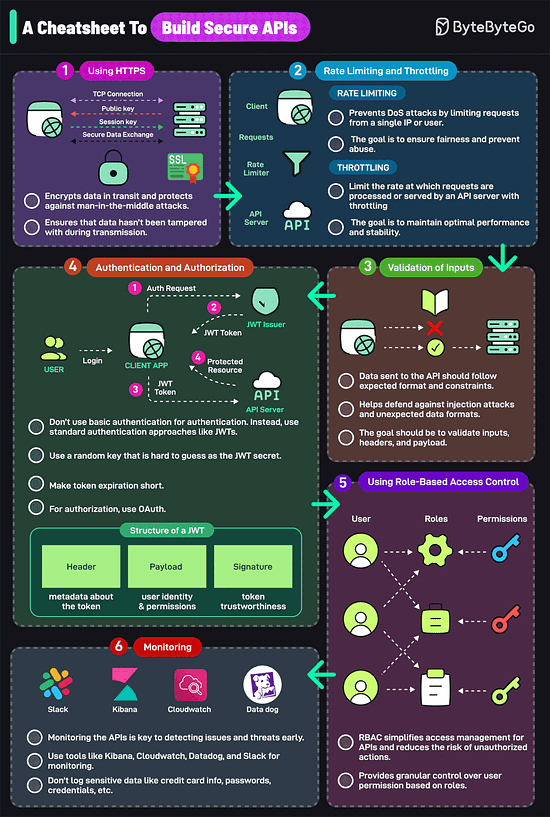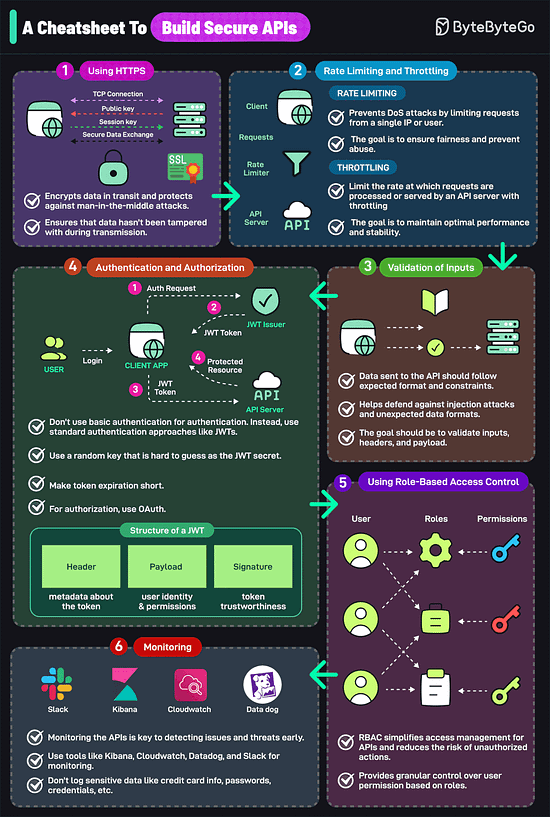
Over to you: Which additional data structures have we overlooked? A Cheatsheet to Build Secure APIsAn insecure API can compromise your entire application. Follow these strategies to mitigate the risk:
Over to you: What else would you do to build a secure API? SPONSOR USGet your product in front of more than 1,000,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com © 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:36 - 26 Oct 2024