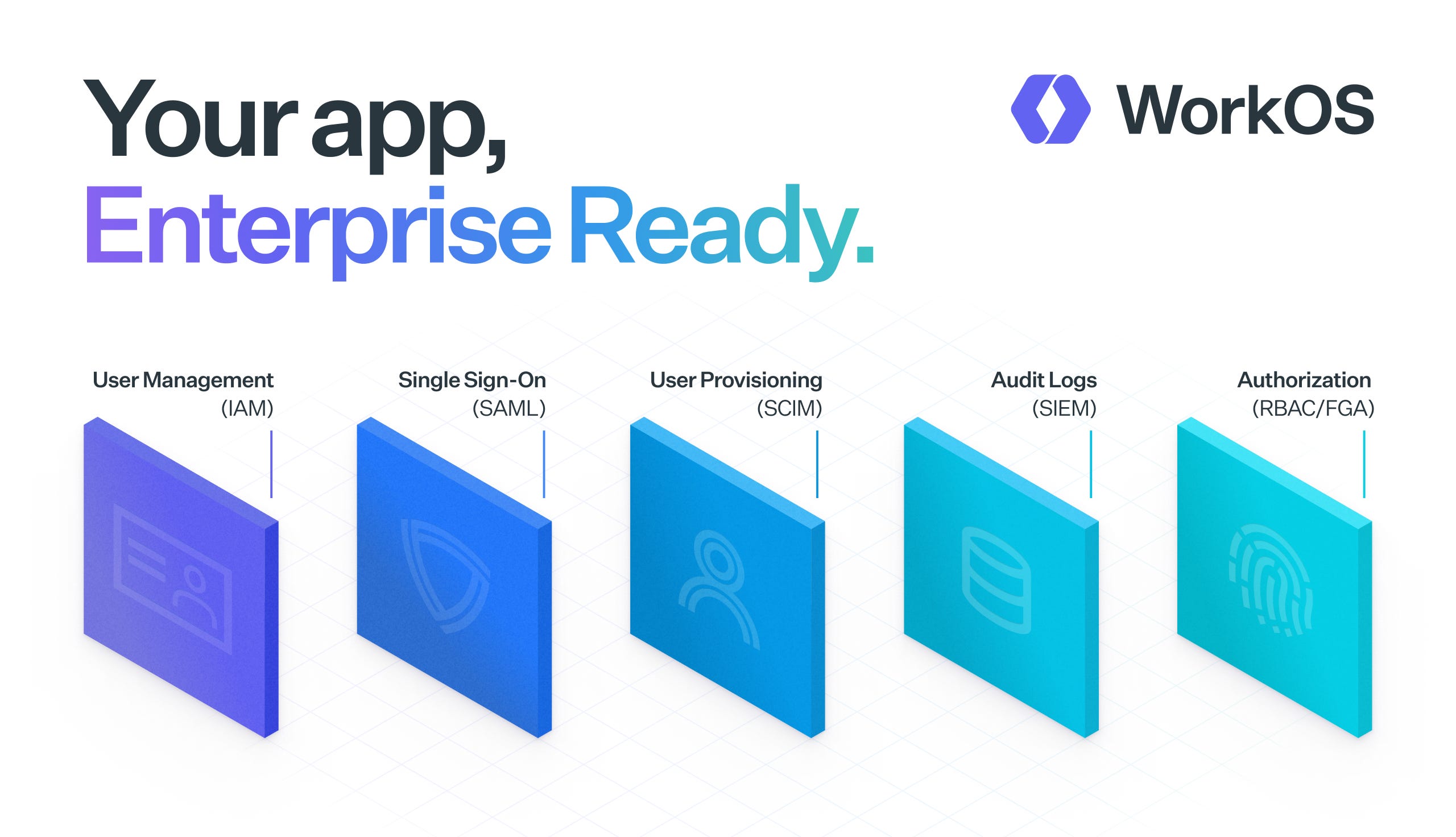
WorkOS is a modern identity platform for B2B SaaS.
→ A complete user management solution that is free up to 1 million MAUs. Includes MFA, RBAC, bot protection, and user impersonation.
→ Enterprise SSO that supports any identity provider that uses SAML or OIDC protocols.
→ Directory Sync that powers user provisioning and deprovisioning for any SCIM-compliant directory.
→ Fine-Grained Authorization (FGA) that can support complex authorization schemes like Google Docs-style permissions.
→ The Admin Portal, a self-serve UI that streamlines SSO and SCIM onboarding for your customers' IT admins.
WorkOS is used by hundreds of high-growth companies including Cursor, Perplexity, and Vercel.
Start deploying enterprise plans today
This week’s system design refresher:
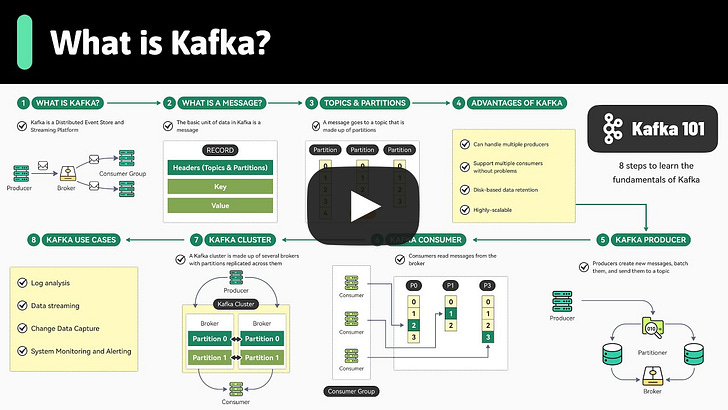
Apache Kafka Fundamentals You Should Know (Youtube video)
The Fundamental Pillars of Object-Oriented Programming
Top 6 Multithreading Design Patterns You Must Know
How Do C++, Java, Python Work?
Explaining 9 types of API testing
REST API Vs. GraphQL
SPONSOR US
Apache Kafka Fundamentals You Should Know
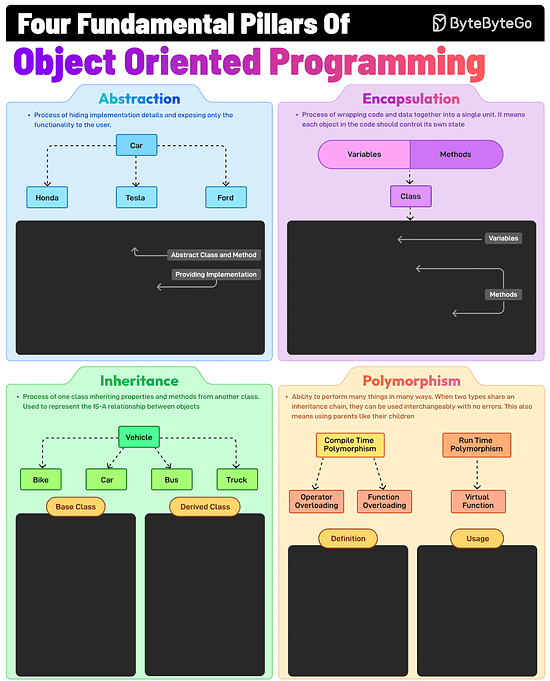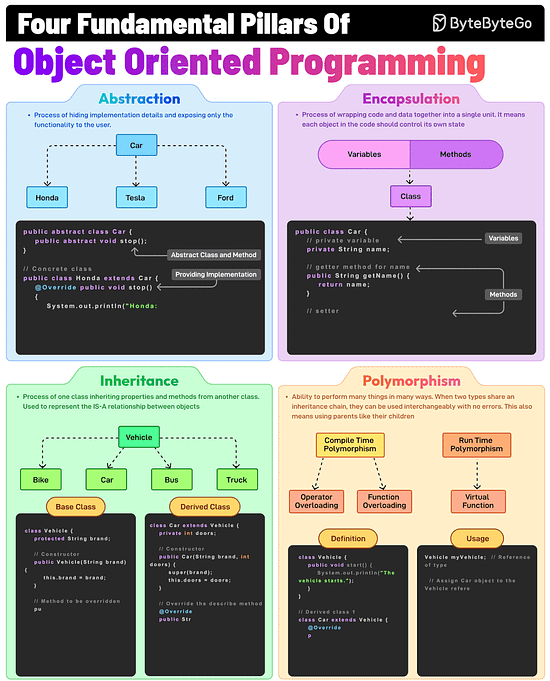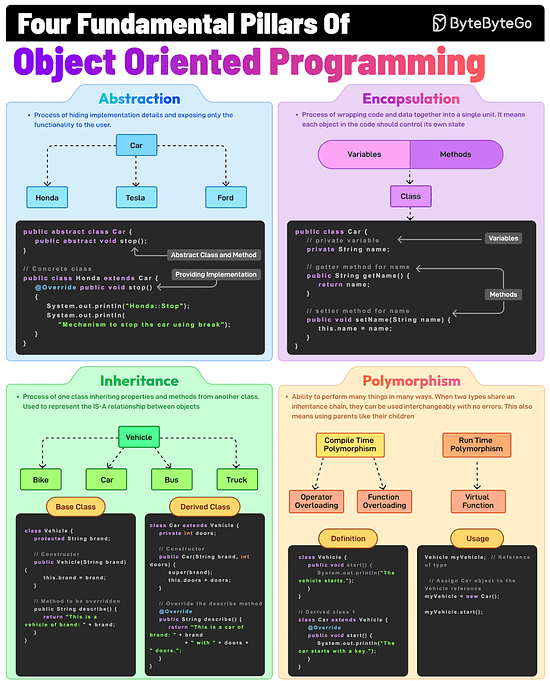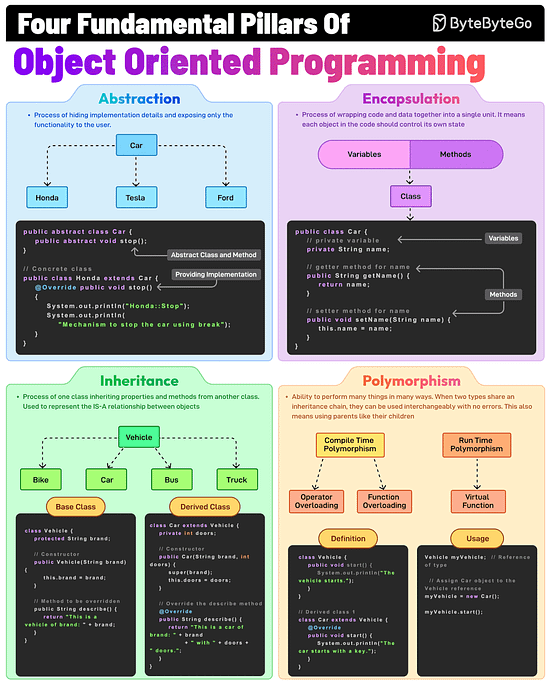
The Fundamental Pillars of Object-Oriented Programming
Abstraction, Encapsulation, Inheritance, and Polymorphism are the four pillars of object-oriented programming. What do they mean?
Abstraction
This is the process of hiding implementation details and showing only the essential features of an object. For example, a Vehicle class with an abstract stop method.
Encapsulation
It involves wrapping data (fields) and methods in a single unit (class) and restricting direct access using access modifiers. For example, private fields with public getters and setters.
Inheritance
The process of creating a new class (child) that inherits attributes and methods from an existing class (parent), thereby promoting code reuse. For example, a Car class inherits from a Vehicle class.
Polymorphism
It allows methods to perform differently based on the object they are invoked on. When two types share an inheritance chain, they can be used interchangeably with no errors.
Over to you: Do you use object-oriented programming?
Simplify your architecture with Confluent Cloud, the fully managed Apache Kafka solution. Designed for developers and architects, it offers effortless scalability, enterprise-grade security, and seamless integration with 120+ pre-built connectors. Say goodbye to managing infrastructure and focus on building real-time, scalable systems that focus on building critical real-time applications.
Try Confluent Cloud for free PLUS $400 credits on us!
Try Free
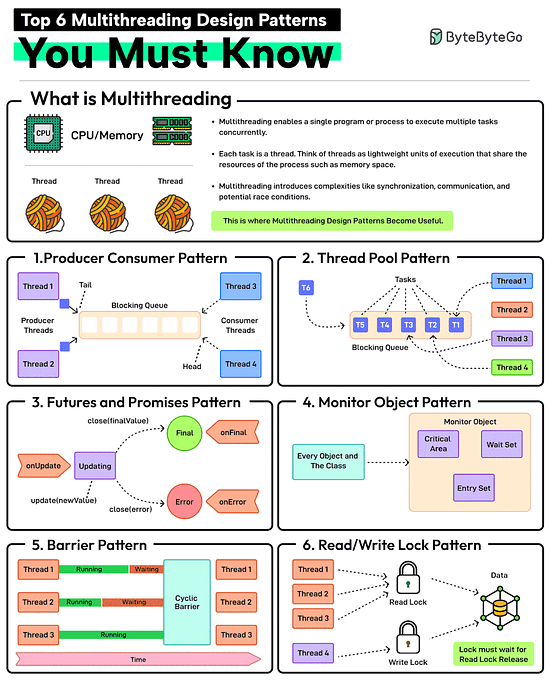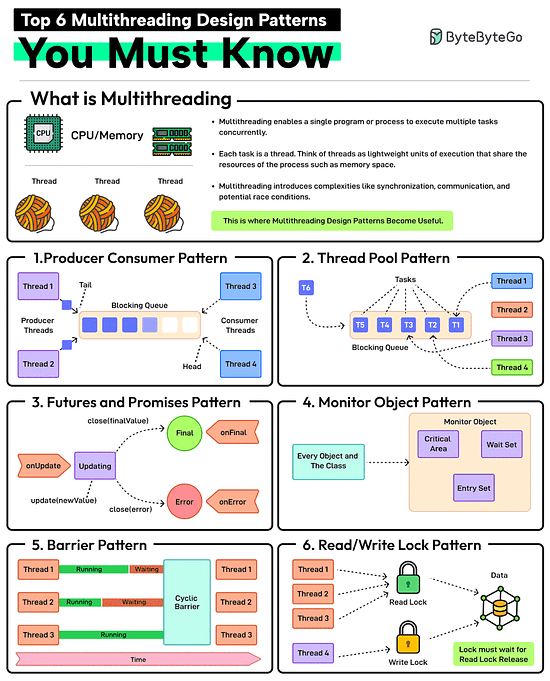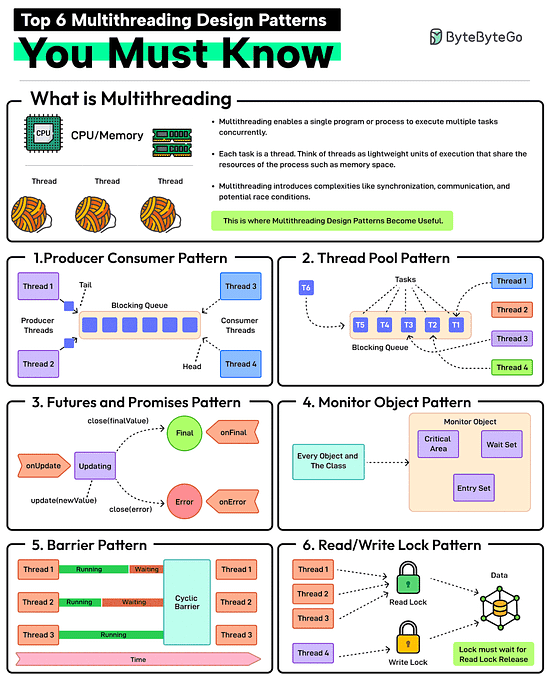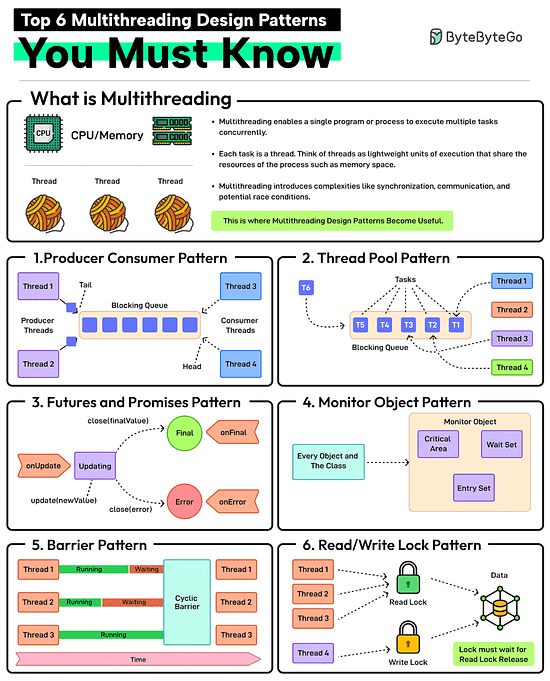
Top 6 Multithreading Design Patterns You Must Know
Multithreading enables a single program or process to execute multiple tasks concurrently. Each task is a thread. Think of threads as lightweight units of execution that share the resources of the process such as memory space.
However, multithreading also introduces complexities like synchronization, communication, and potential race conditions. This is where patterns help.
Producer-Consumer Pattern
This pattern involves two types of threads: producers generating data and consumers processing that data. A blocking queue acts as a buffer between the two.
Thread Pool Pattern
In this pattern, there is a pool of worker threads that can be reused for executing tasks. Using a pool removes the overhead of creating and destroying threads. Great for executing a large number of short-lived tasks.
Futures and Promises Pattern
In this pattern, the promise is an object that holds the eventual results and the future provides a way to access the result. This is great for executing long-running operations concurrently without blocking the main thread.
Monitor Object Pattern
Ensures that only one thread can access or modify a shared resource within an object at a time. This helps prevent race conditions. The pattern is required when you need to protect shared data or resources from concurrent access.
Barrier Pattern
Synchronizes a group of threads. Each thread executes until it reaches a barrier point in the code and blocks until all threads have reached the same barrier. Ideal for parallel tasks that need to reach a specific stage before starting the next stage.
Read-Write Lock Pattern
It allows multiple threads to read from a shared resource but only allows one thread to write to it at a time. Ideal for managing shared resources where reads are more frequent than writes.
Over to you: Which other multithreading design pattern will you add to the list?
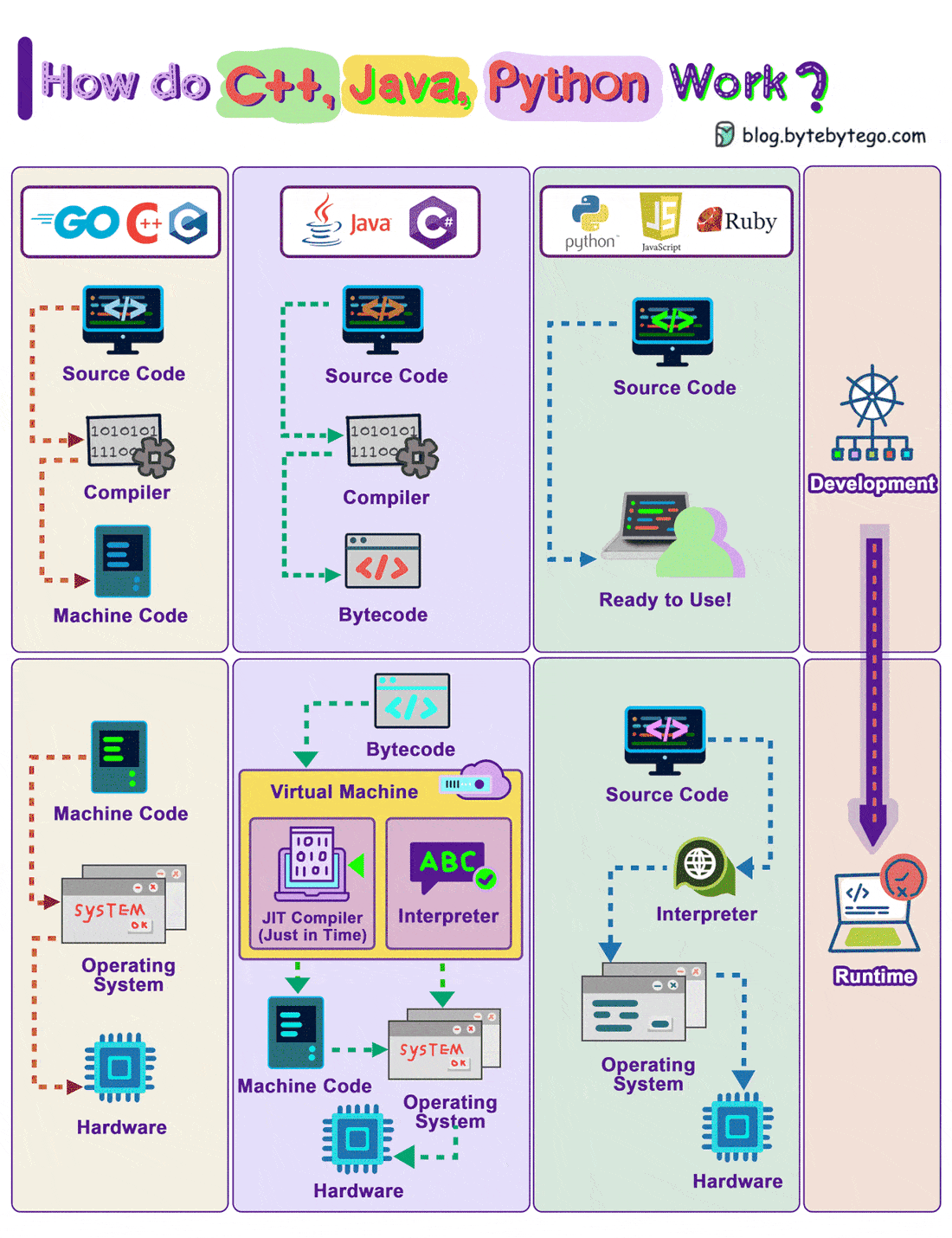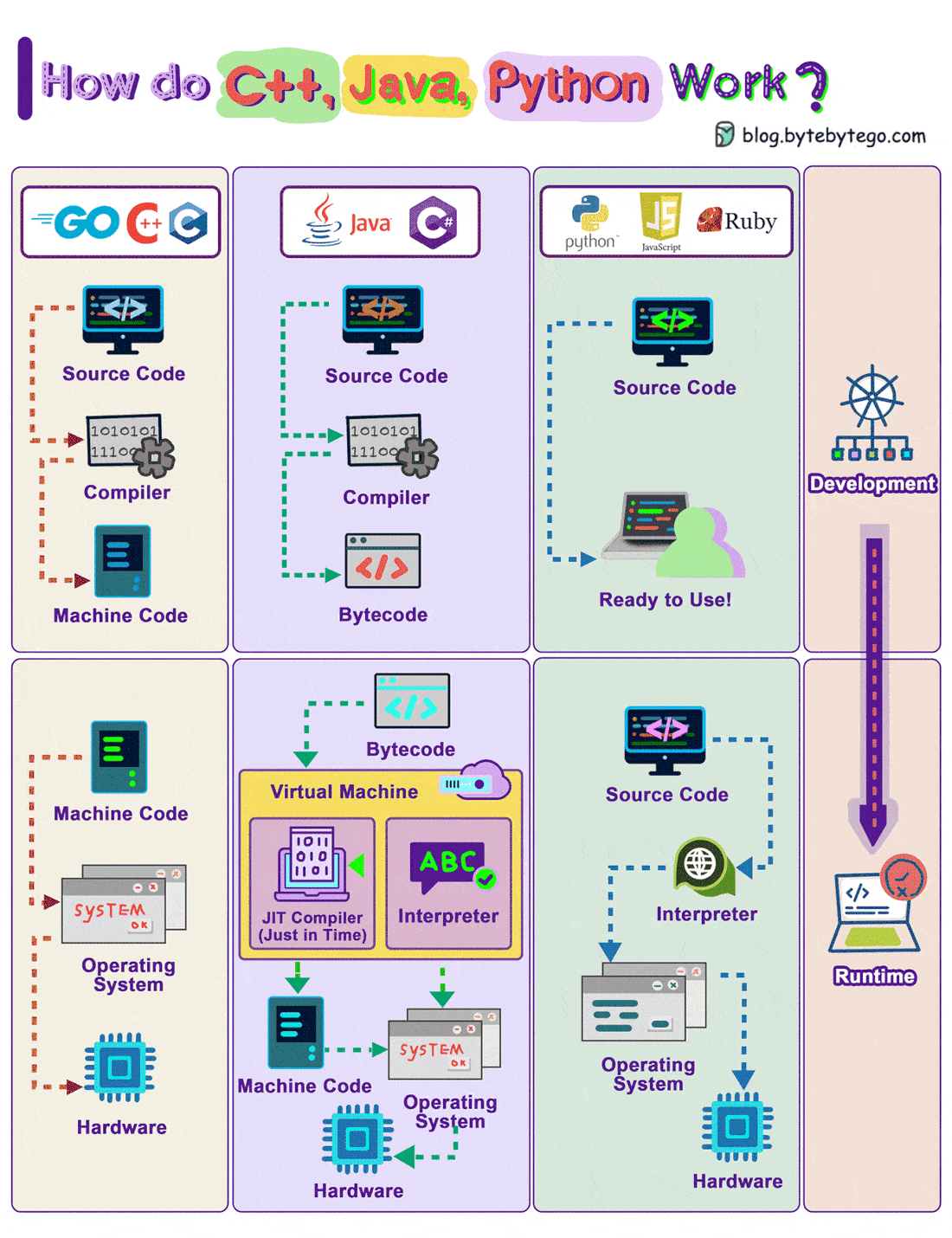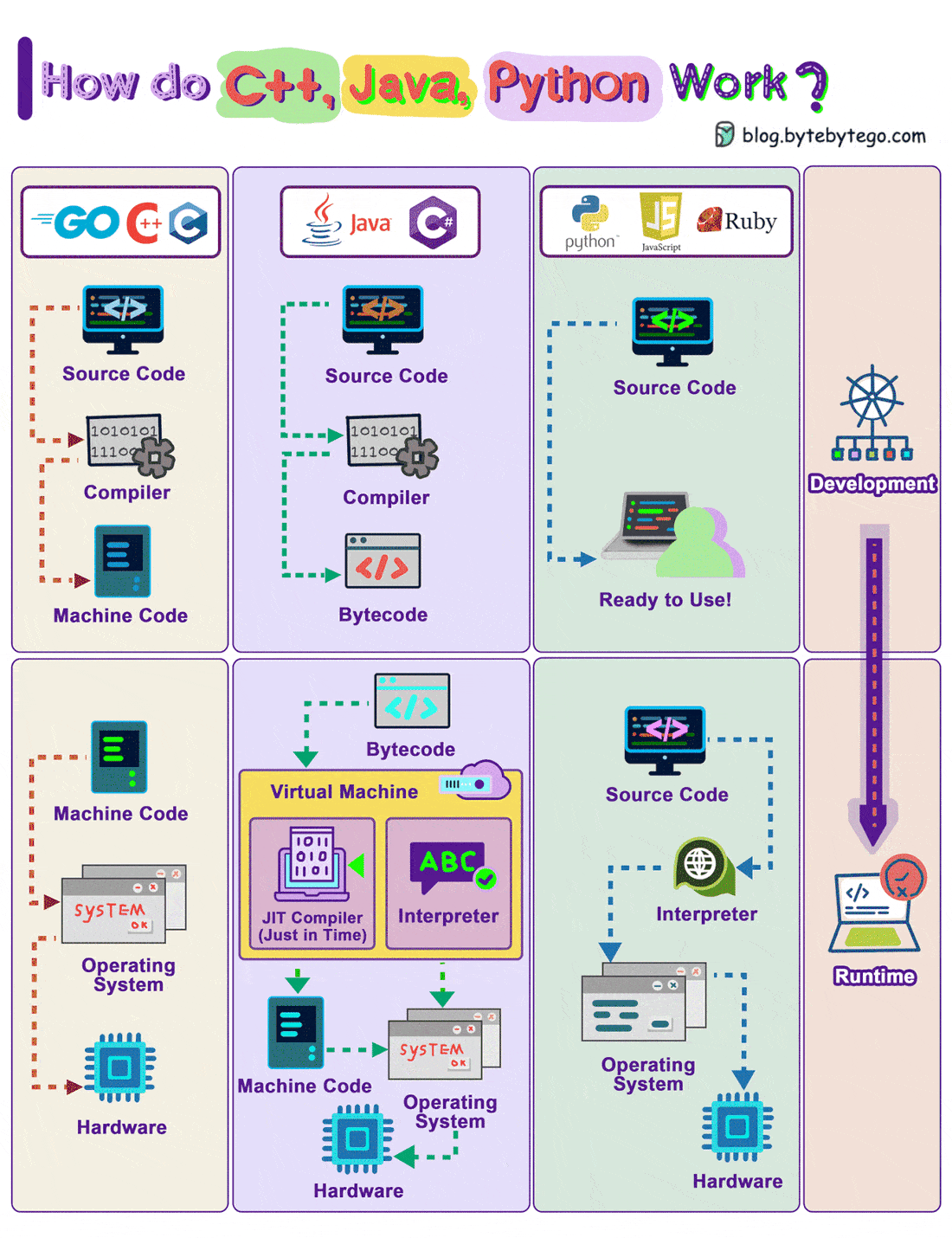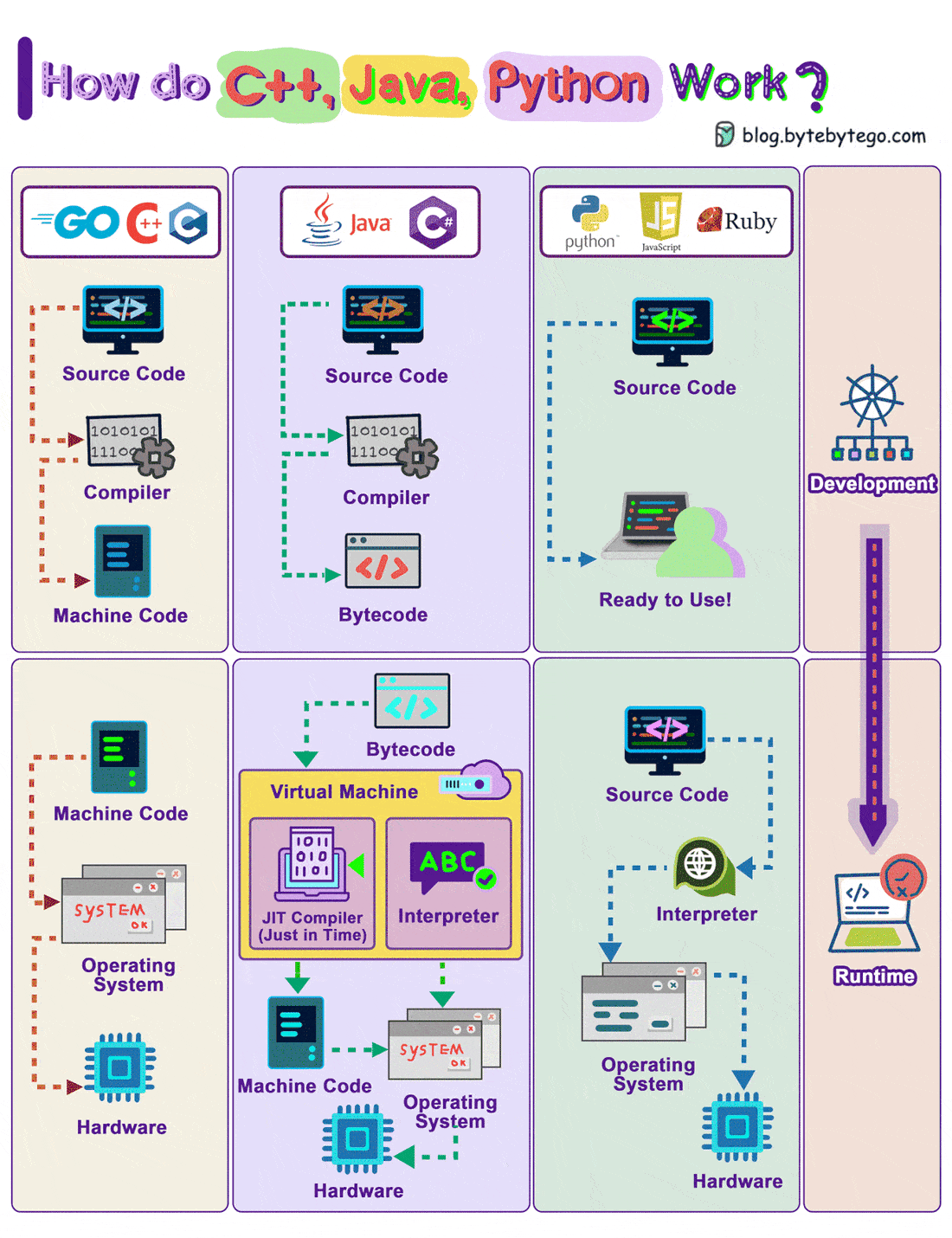
How Do C++, Java, Python Work?
The diagram shows how the compilation and execution work.
Compiled languages are compiled into machine code by the compiler. The machine code can later be executed directly by the CPU. Examples: C, C++, Go.
A bytecode language like Java, compiles the source code into bytecode first, then the JVM executes the program. Sometimes JIT (Just-In-Time) compiler compiles the source code into machine code to speed up the execution. Examples: Java, C#
Interpreted languages are not compiled. They are interpreted by the interpreter during runtime. Examples: Python, Javascript, Ruby
Compiled languages in general run faster than interpreted languages.
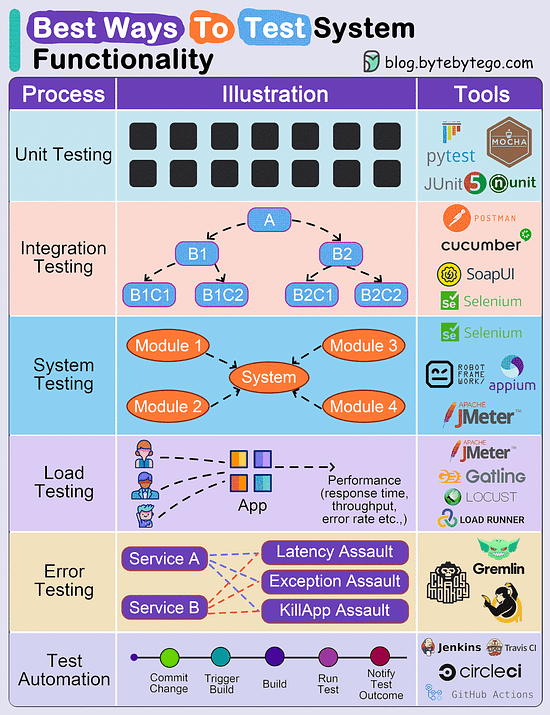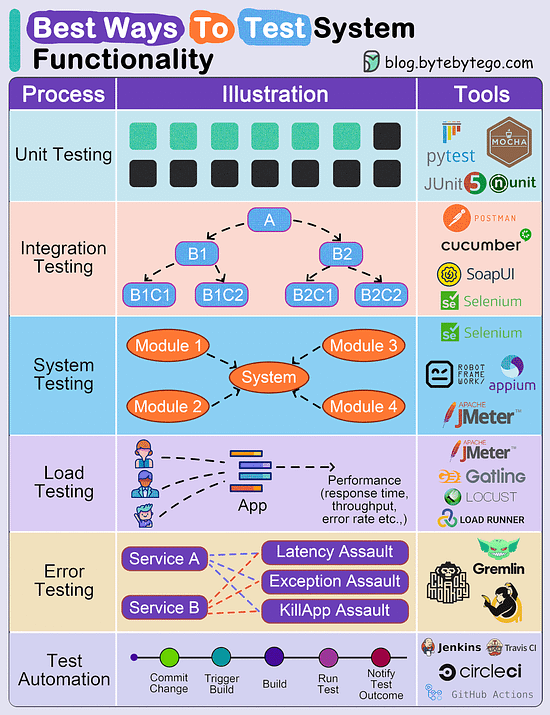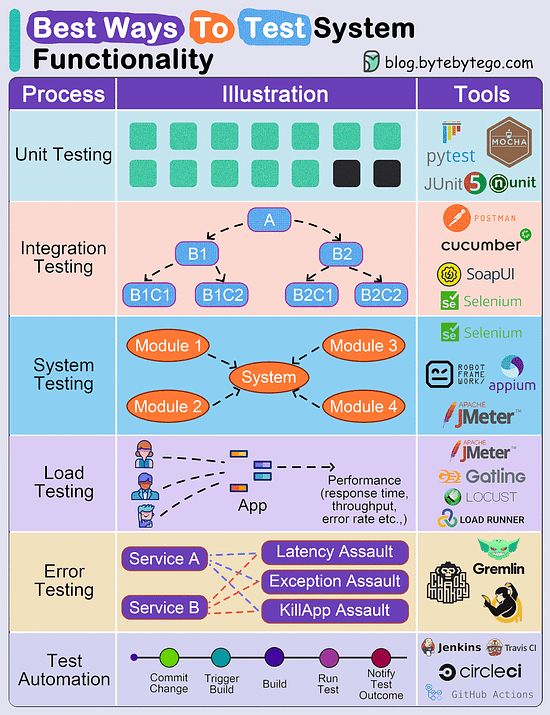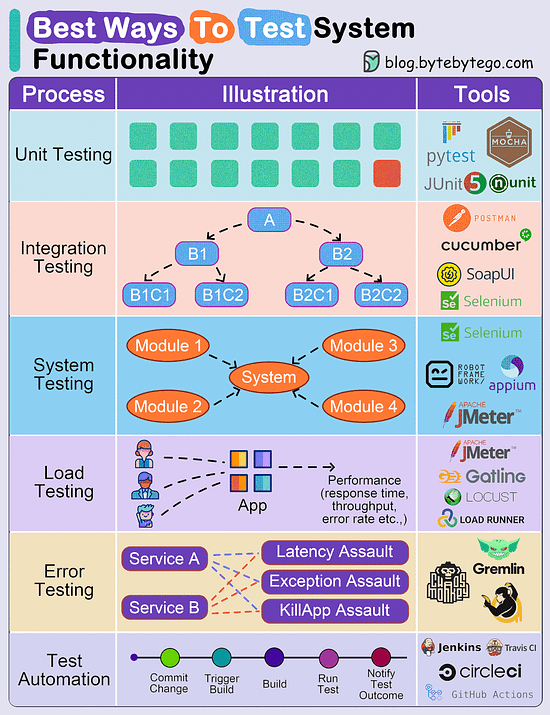
Explaining 9 types of API testing
Smoke Testing
This is done after API development is complete. Simply validate if the APIs are working and nothing breaks.
Functional Testing
This creates a test plan based on the functional requirements and compares the results with the expected results.
Integration Testing
This test combines several API calls to perform end-to-end tests. The intra-service communications and data transmissions are tested.
Regression Testing
This test ensures that bug fixes or new features shouldn’t break the existing behaviors of APIs.
Load Testing
This tests applications’ performance by simulating different loads. Then we can calculate the capacity of the application.
Stress Testing
We deliberately create high loads to the APIs and test if the APIs are able to function normally.
Security Testing
This tests the APIs against all possible external threats.
UI Testing
This tests the UI interactions with the APIs to make sure the data can be displayed properly.
Fuzz Testing
This injects invalid or unexpected input data into the API and tries to crash the API. In this way, it identifies the API vulnerabilities.
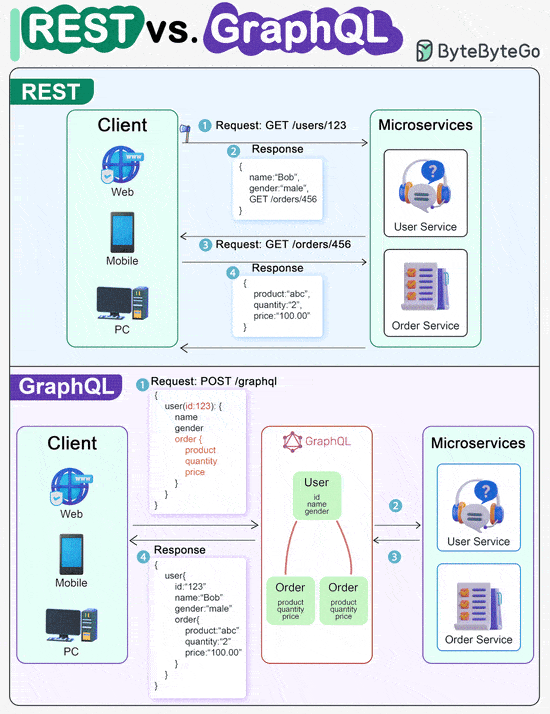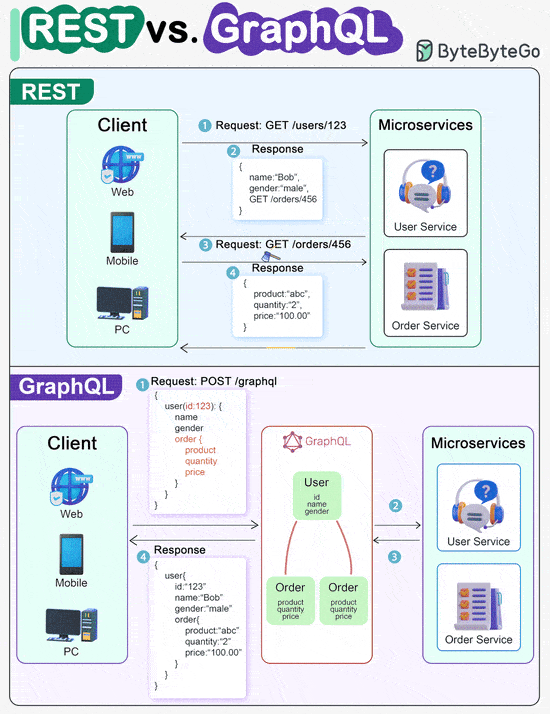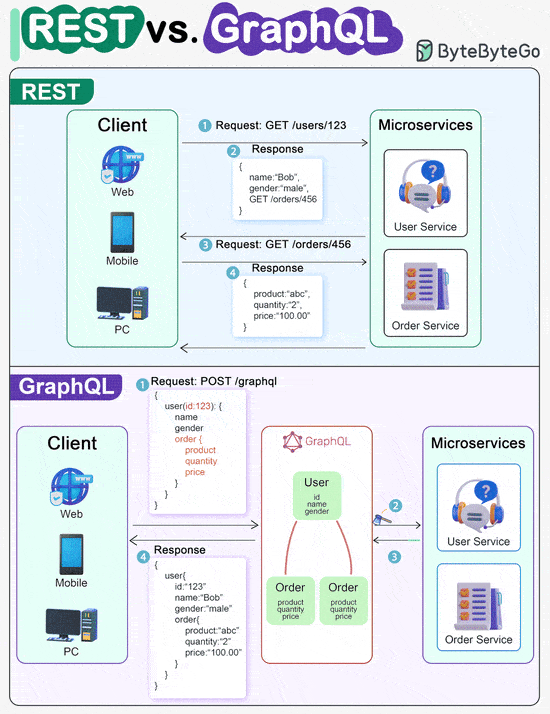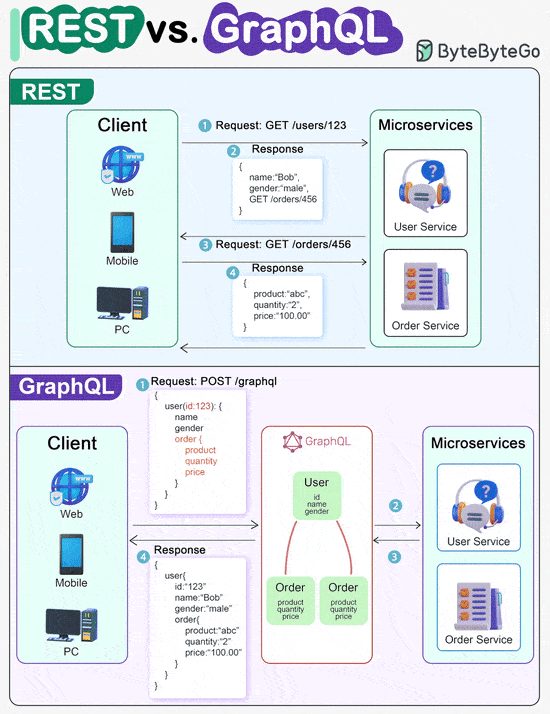
REST API Vs. GraphQL
When it comes to API design, REST and GraphQL each have their own strengths and weaknesses.
REST
Uses standard HTTP methods like GET, POST, PUT, DELETE for CRUD operations.
Works well when you need simple, uniform interfaces between separate services/applications.
Caching strategies are straightforward to implement.
The downside is it may require multiple roundtrips to assemble related data from separate endpoints.
GraphQL
Provides a single endpoint for clients to query for precisely the data they need.
Clients specify the exact fields required in nested queries, and the server returns optimized payloads containing just those fields.
Supports Mutations for modifying data and Subscriptions for real-time notifications.
Great for aggregating data from multiple sources and works well with rapidly evolving frontend requirements.
However, it shifts complexity to the client side and can allow abusive queries if not properly safeguarded
Caching strategies can be more complicated than REST.
The best choice between REST and GraphQL depends on the specific requirements of the application and development team. GraphQL is a good fit for complex or frequently changing frontend needs, while REST suits applications where simple and consistent contracts are preferred.
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com.