- Mailing Lists
- in
- EP144: The 9 Algorithms That Dominate Our World
Archives
- By thread 5425
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 239
EP144: The 9 Algorithms That Dominate Our World
EP144: The 9 Algorithms That Dominate Our World
WorkOS: Your app, Enterprise Ready. (Sponsored)WorkOS is a modern identity platform for B2B SaaS. → A complete user management solution that is free up to 1 million MAUs. Includes MFA, RBAC, bot protection, and user impersonation. WorkOS is used by hundreds of high-growth companies including Cursor, Perplexity, and Vercel. This week’s system design refresher:
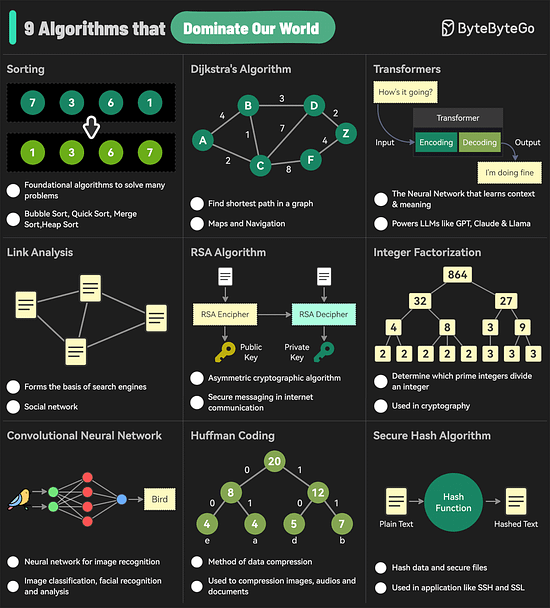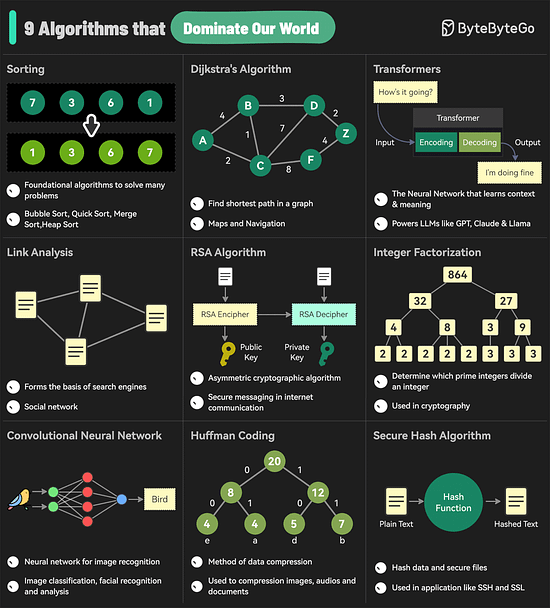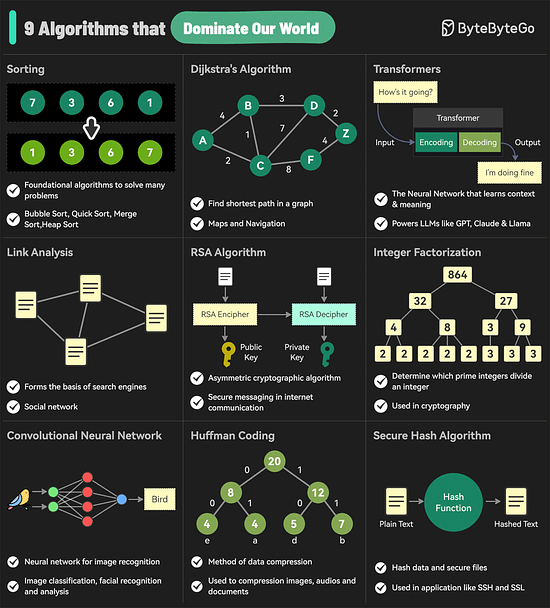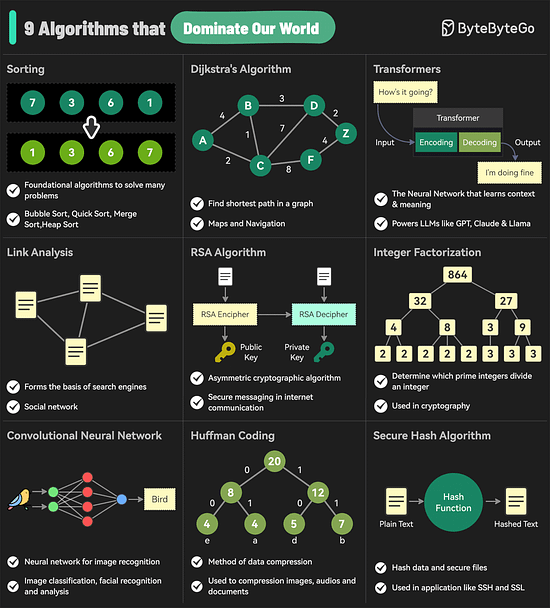
The 9 Algorithms That Dominate Our WorldThe diagram below shows the most commonly used algorithms in our daily lives. They are used in internet search engines, social networks, WiFi, cell phones, and even satellites.
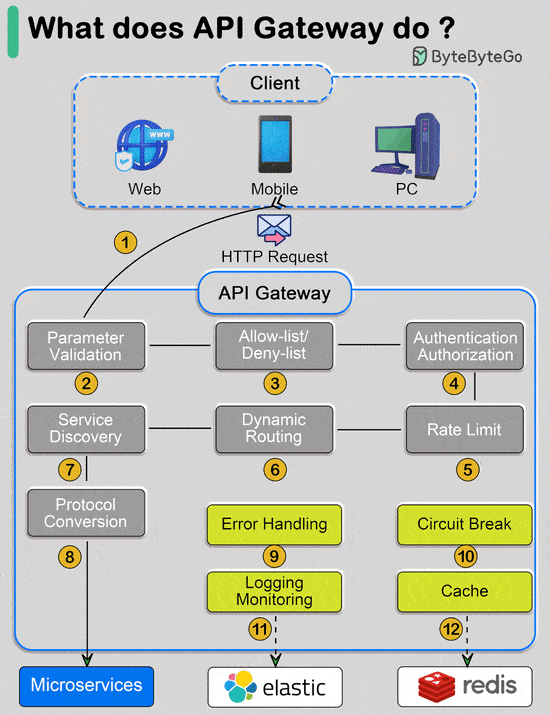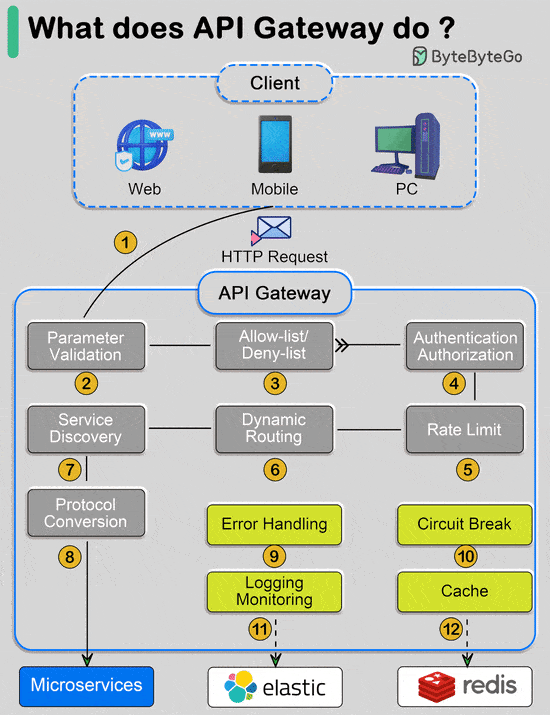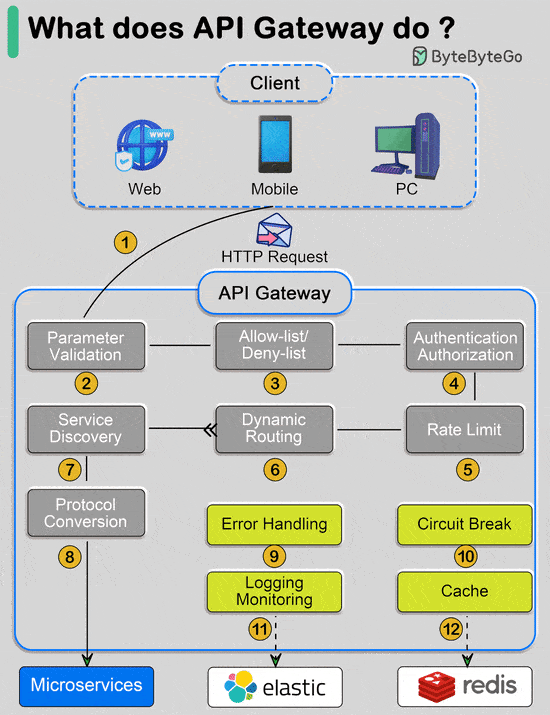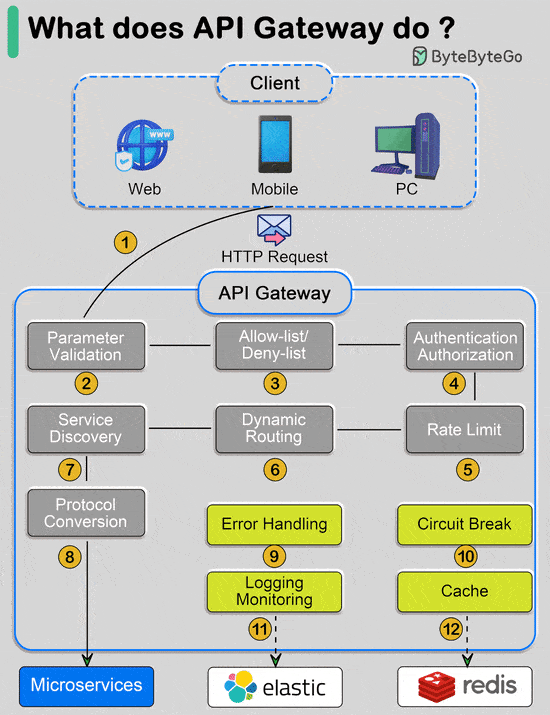
Over to you: Are there any other commonly used algorithms we missed? What does API gateway do?The diagram below shows the detail. Step 1 - The client sends an HTTP request to the API gateway.
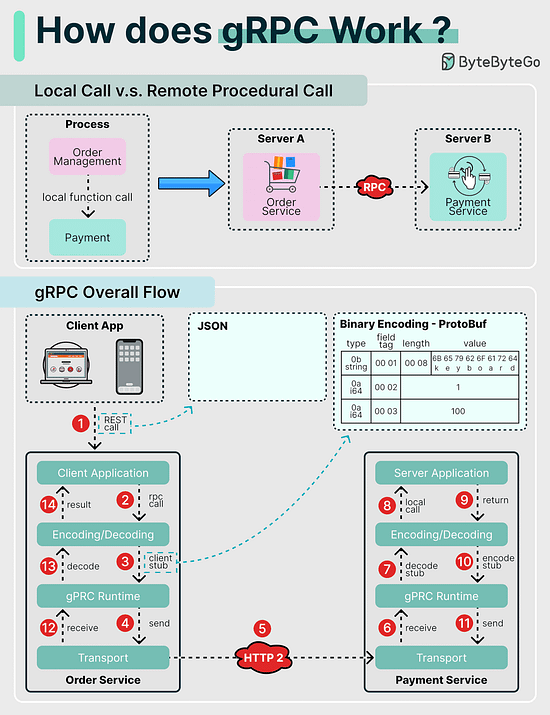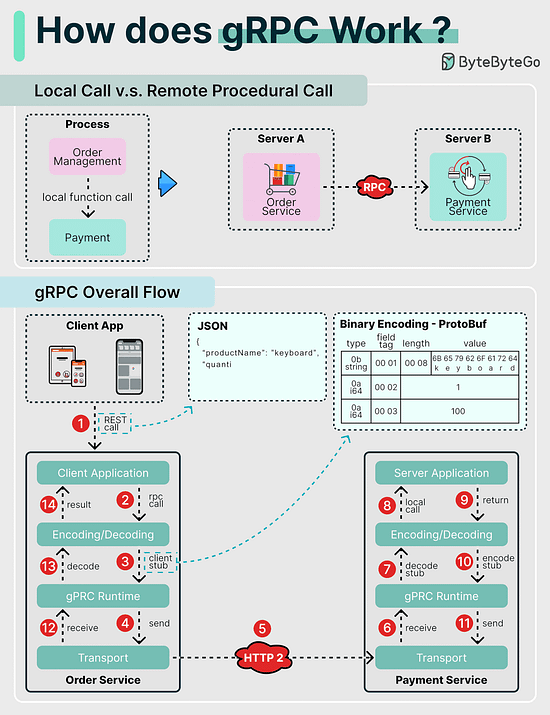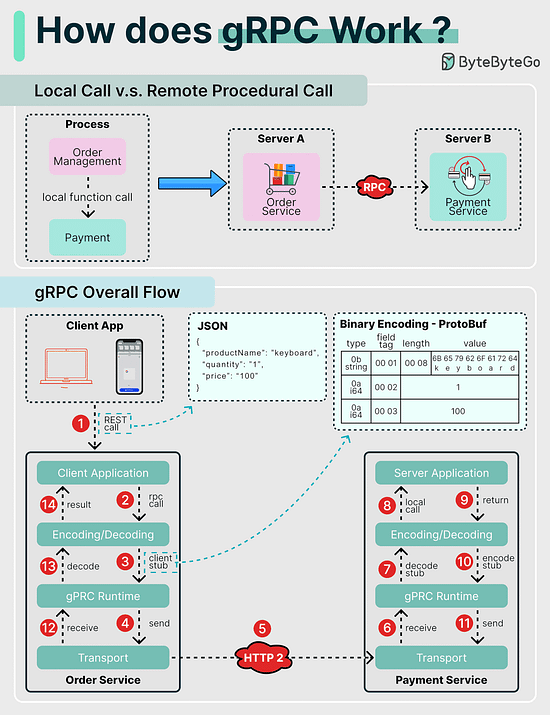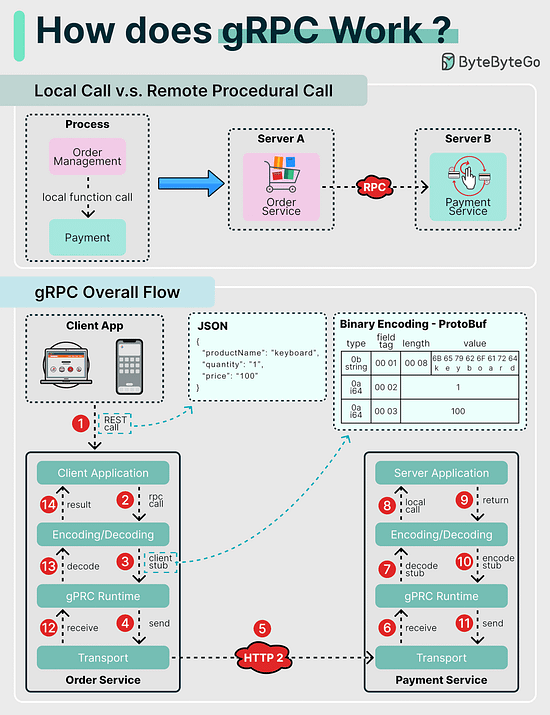
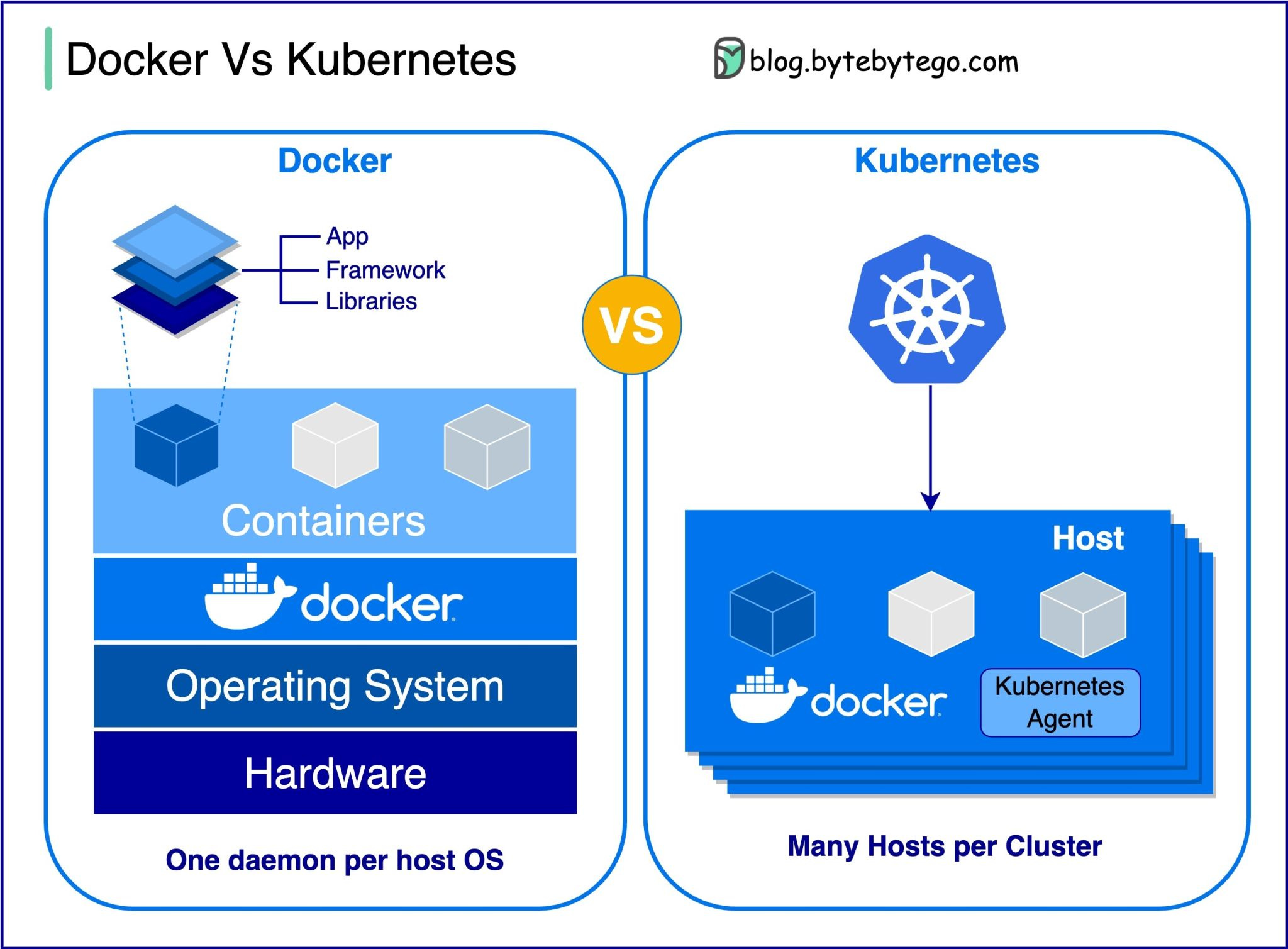
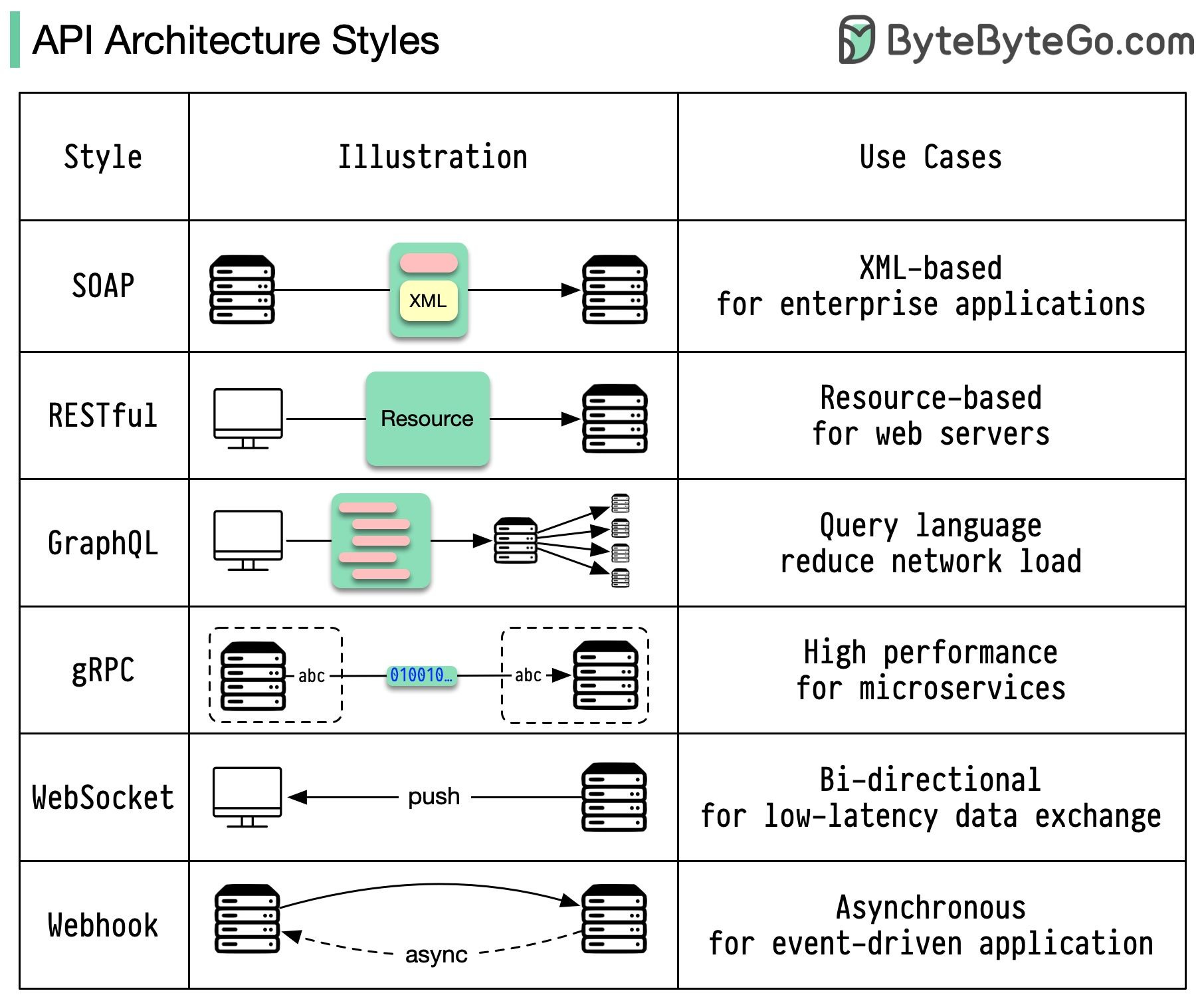
How does gRPC work?RPC (Remote Procedure Call) is called “remote” because it enables communications between remote services when services are deployed to different servers under microservice architecture. From the user’s point of view, it acts like a local function call. Step 1: A REST call is made from the client. The request body is usually in JSON format. Docker vs. Kubernetes. Which one should we use?What is Docker ? How many API architecture styles do you know?Architecture styles define how different components of an application programming interface (API) interact with one another. As a result, they ensure efficiency, reliability, and ease of integration with other systems by providing a standard approach to designing and building APIs. Here are the most used styles:
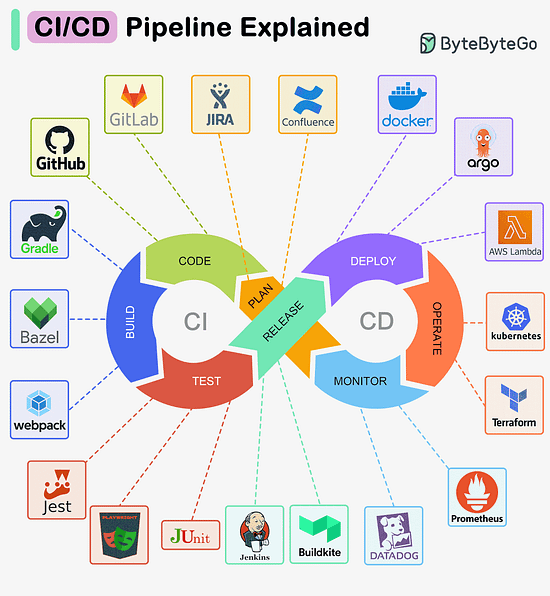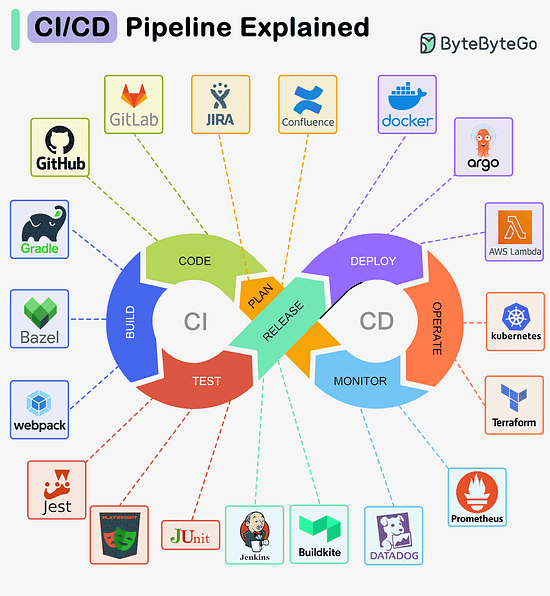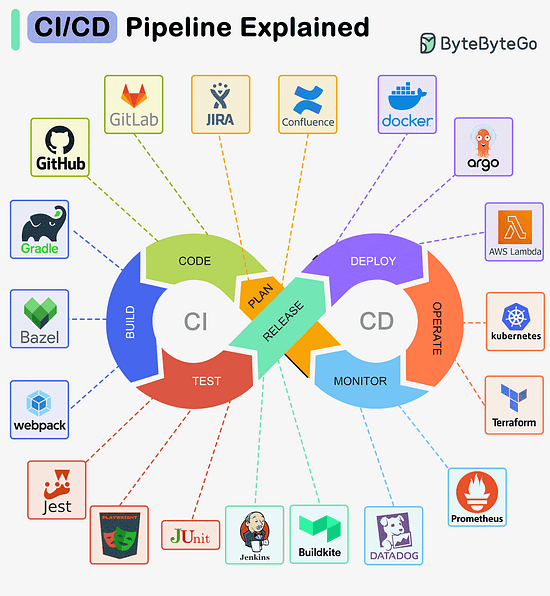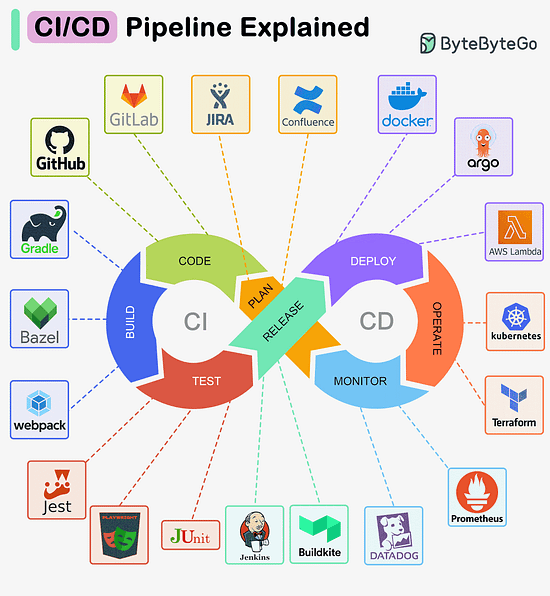
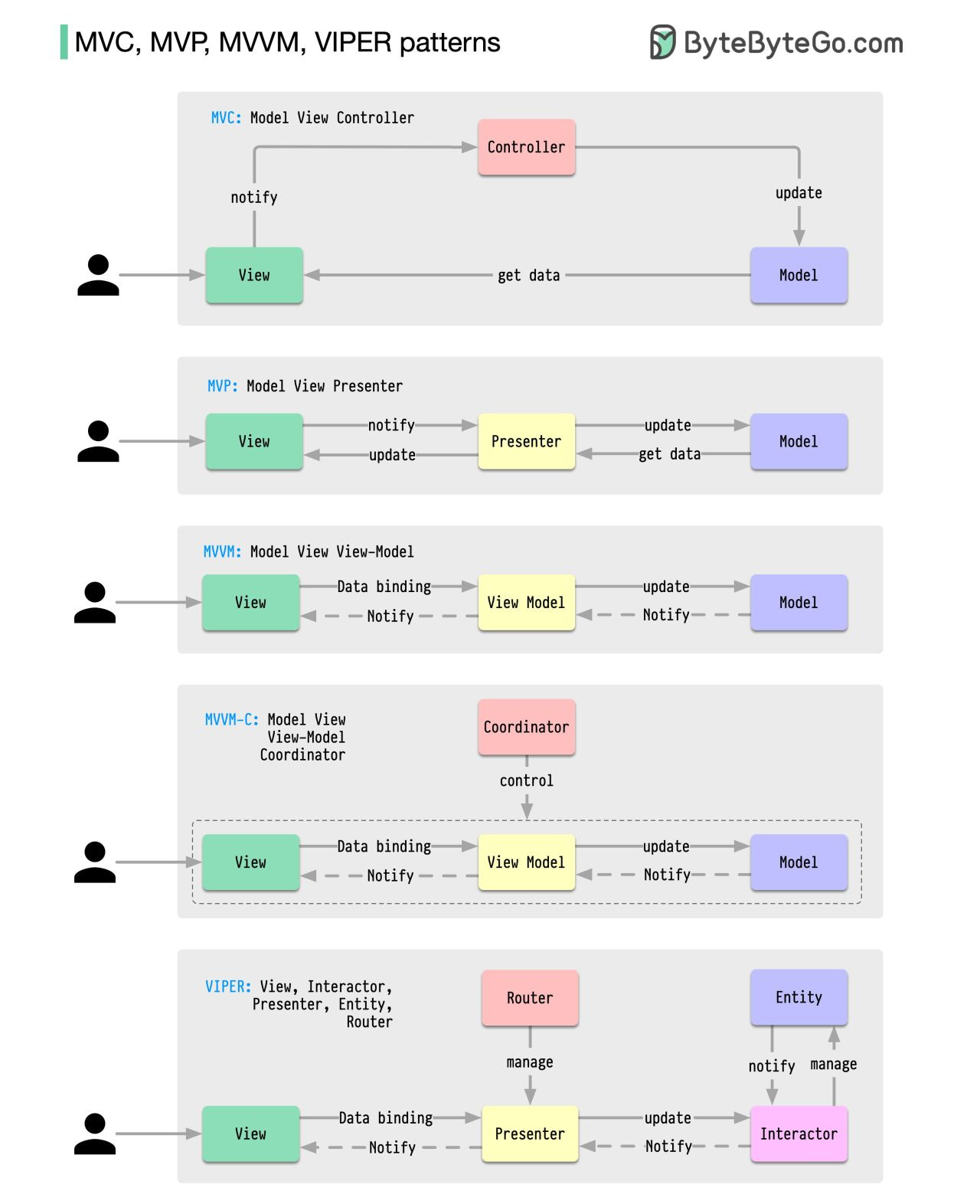
Over to you: Are there any other famous styles we missed? CI/CD Pipeline ExplainedA CI/CD pipeline is a tool that automates the process of building, testing, and deploying software. MVC, MVP, MVVM, VIPER PatternsWhat distinguishes MVC, MVP, MVVM, MVVM-C, and VIPER architecture patterns from each other? These architecture patterns are among the most commonly used in app development, whether on iOS or Android platforms. Developers have introduced them to overcome the limitations of earlier patterns. So, how do they differ?
SPONSOR USGet your product in front of more than 1,000,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com. © 2025 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:35 - 4 Jan 2025