- Mailing Lists
- in
- EP164: JWT Simply Explained
Archives
- By thread 4908
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 19
EP164: JWT Simply Explained
EP164: JWT Simply Explained
AWS Guide to Cloud Architecture Diagrams (Sponsored)Enhance visibility into your cloud architecture with expert insights from AWS + Datadog. In this ebook, AWS Solutions Architects Jason Mimick and James Wenzel guide you through best practices for creating professional and impactful diagrams. This week’s system design refresher:
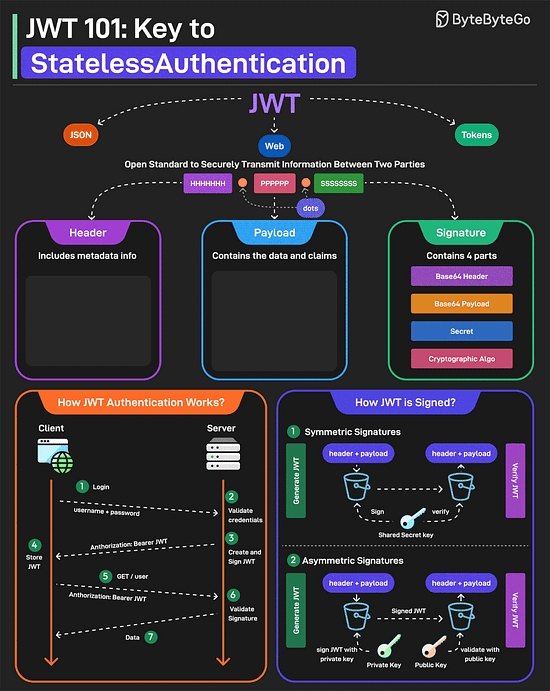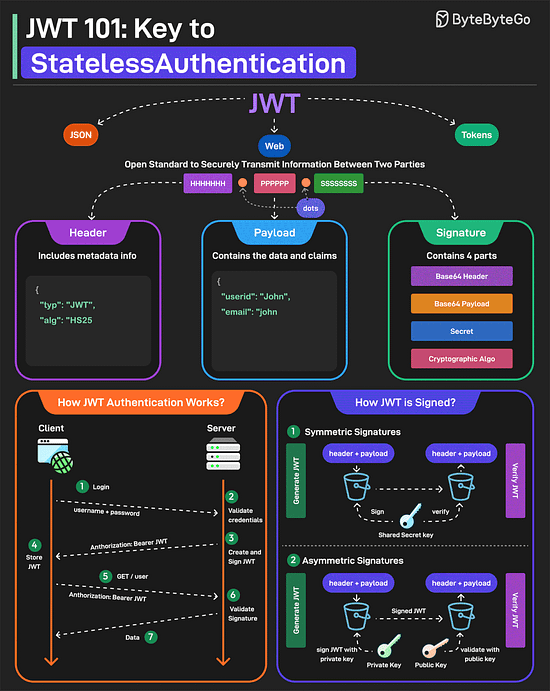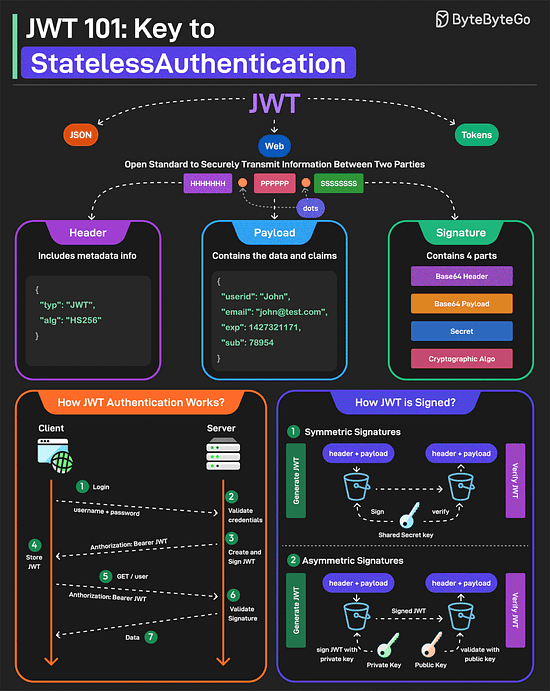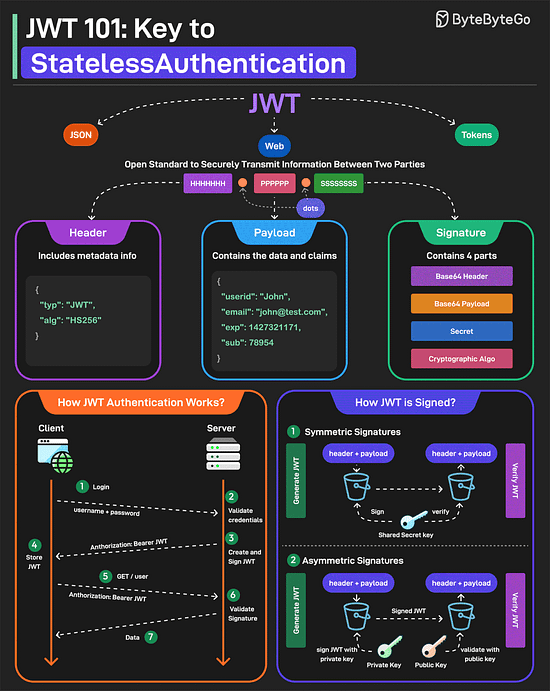
JWT Simply ExplainedJWT or JSON Web Tokens is an open standard for securely transmitting information between two parties. They are widely used for authentication and authorization. A JWT consists of three main components:
JWTs can be signed in two different ways:
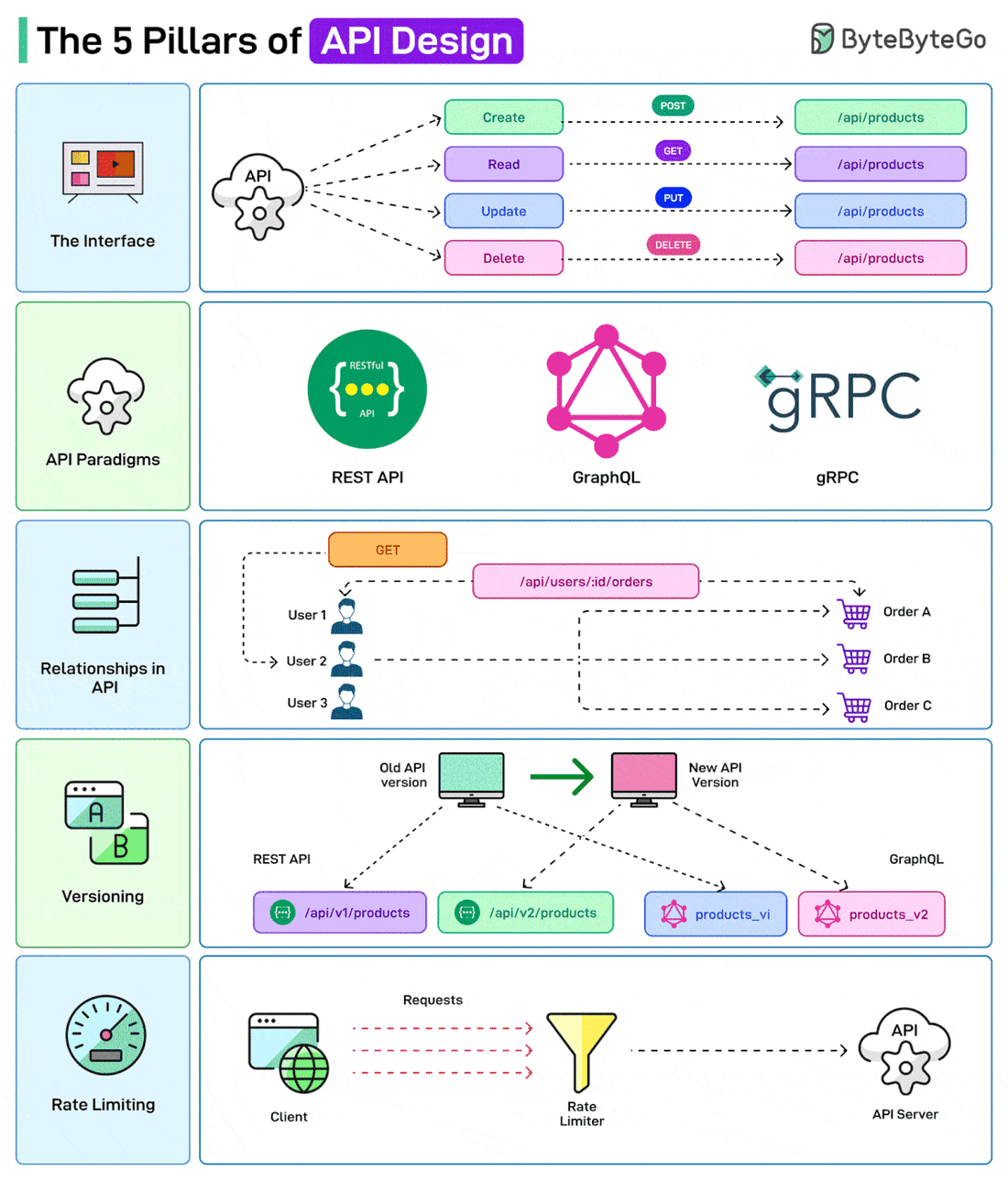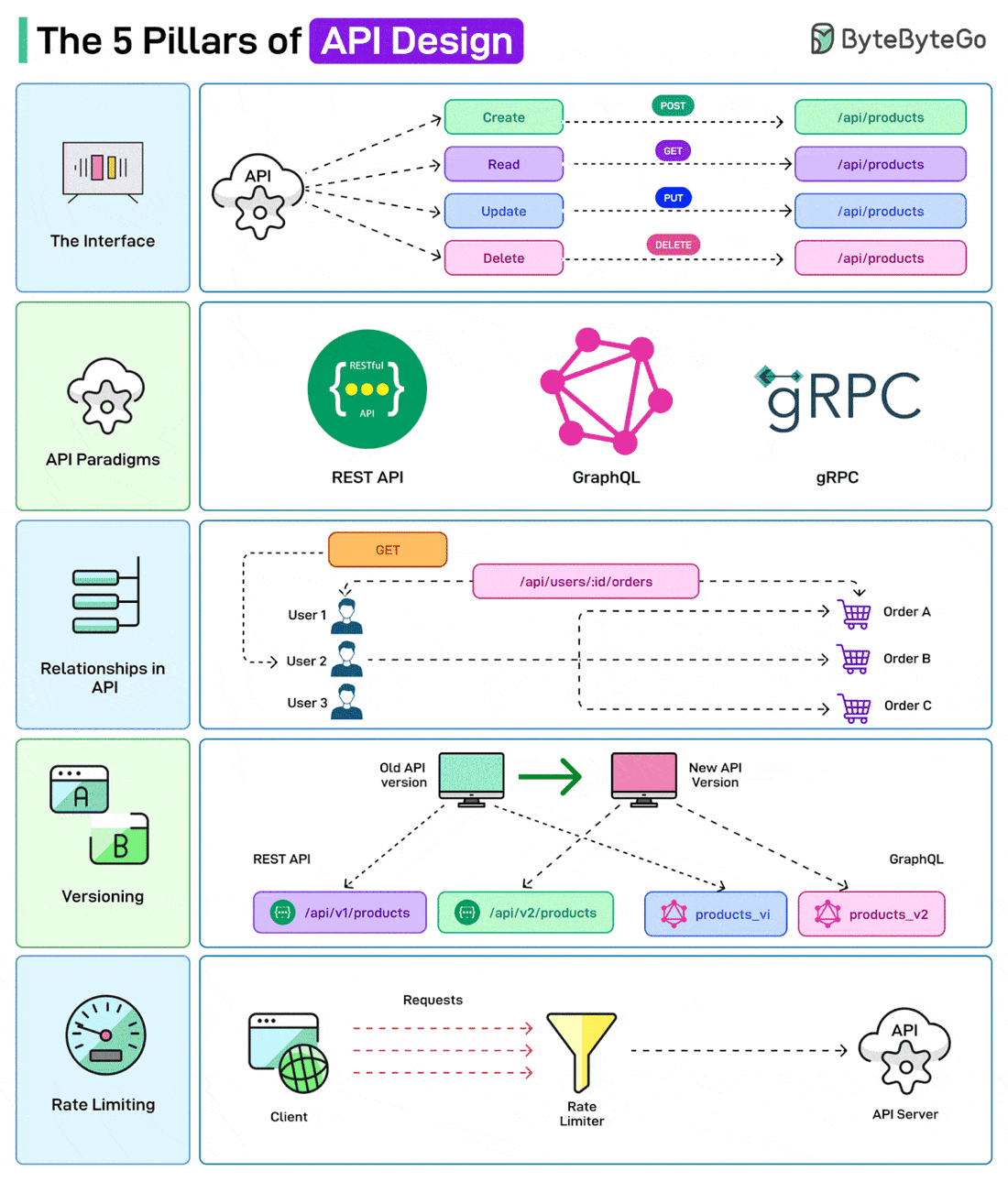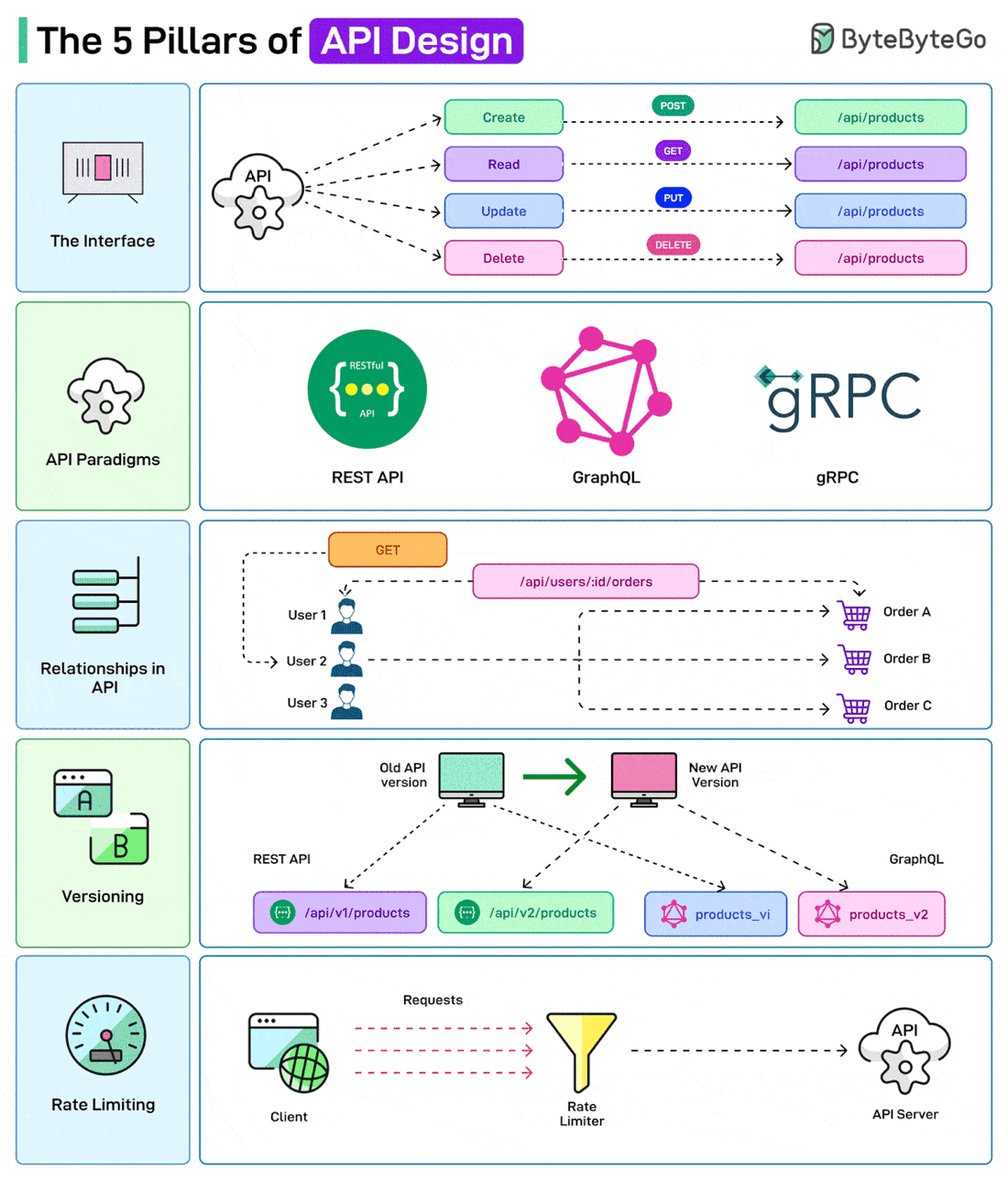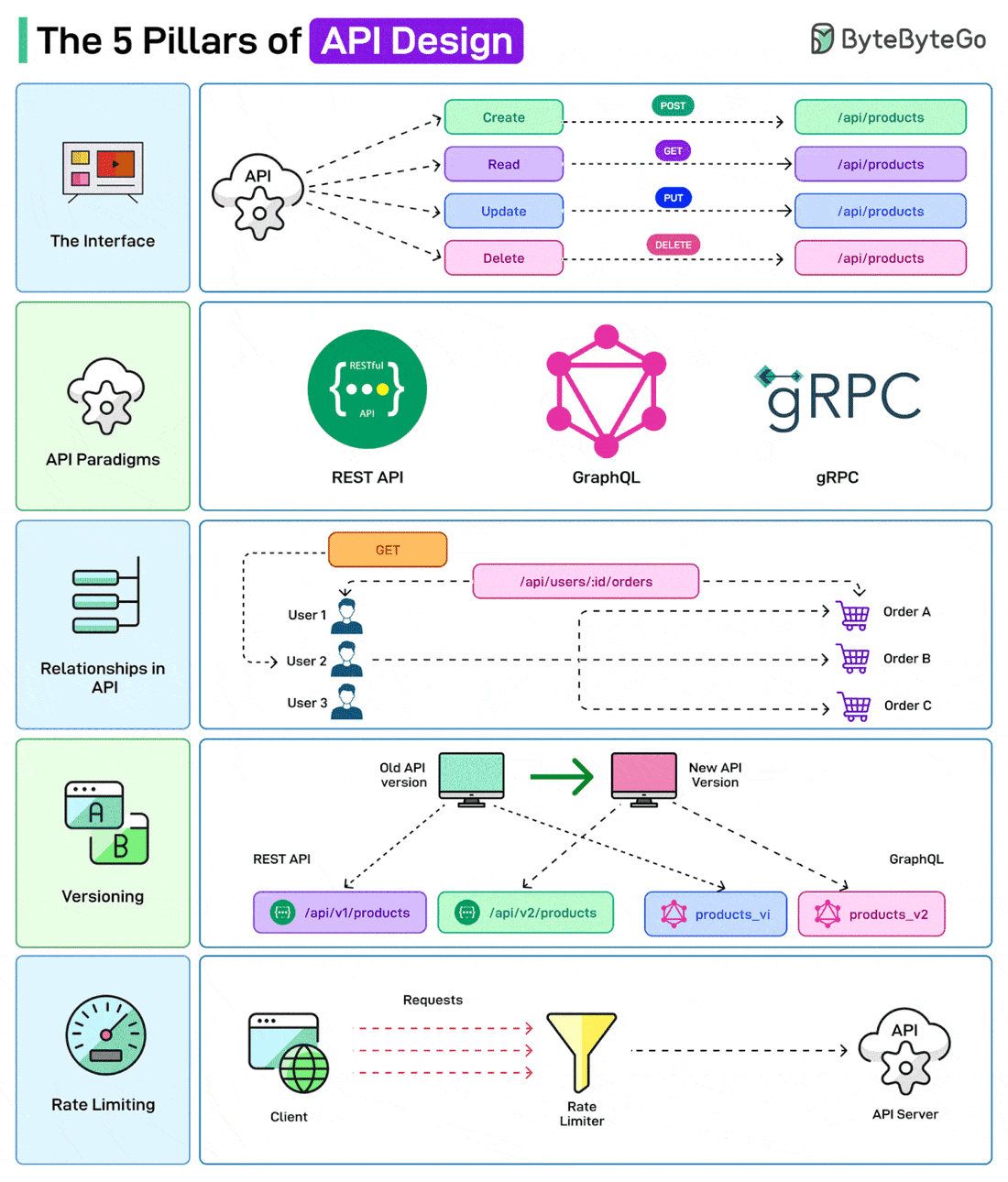
Over to you: Do you use JWTs for authentication? The 5 Pillars of API DesignAPIs are the backbone of modern systems. But it is also important to design them in the right way. Here are a few things that a developer should consider while designing APIs
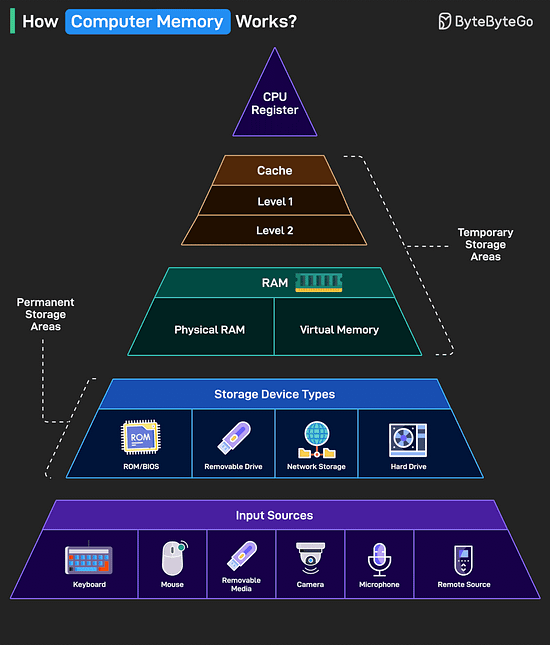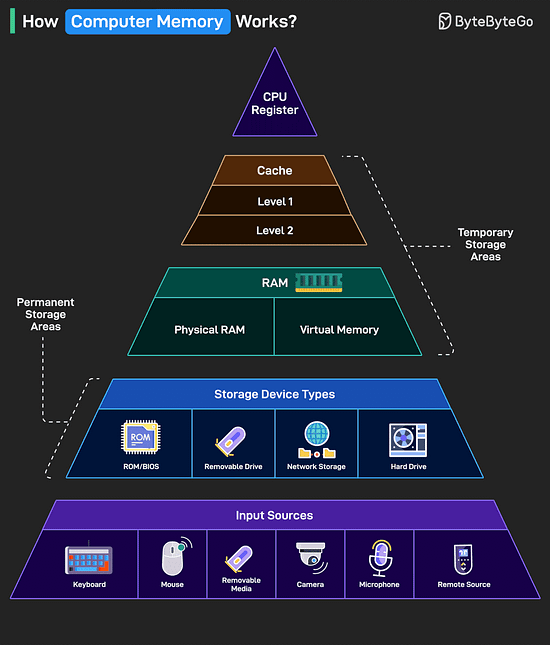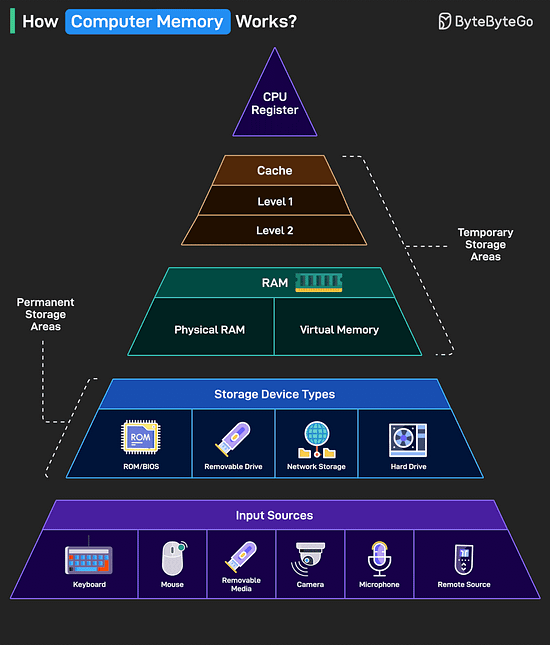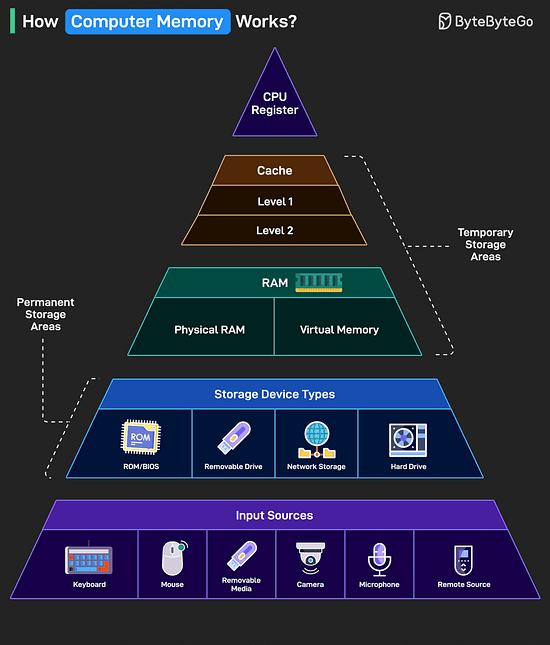
Over to you: Which other API Design principle will you add to the list? How Computer Memory Works?Here’s a simple breakdown that shows how data moves through a system from input to processing to storage.
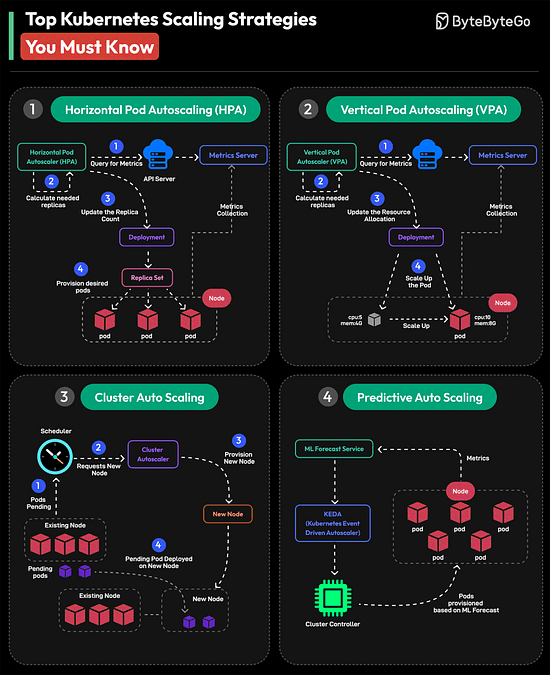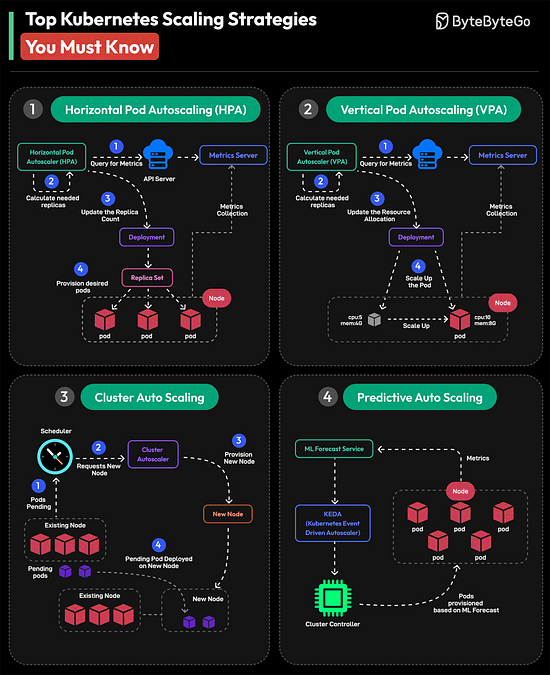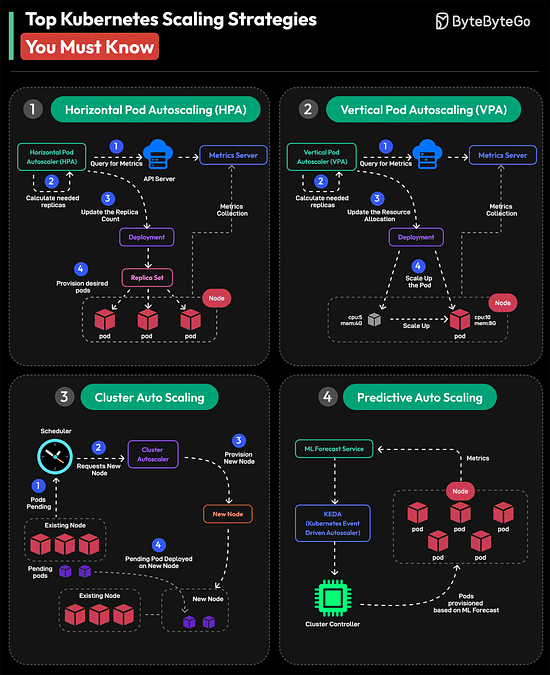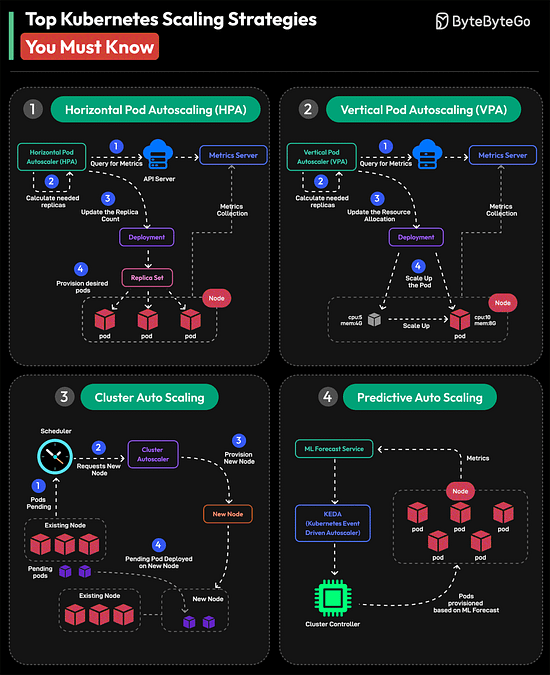
The higher you go in the memory pyramid, the faster and smaller the storage. Over to you: What else will you add to improve the understanding of a computer memory’s working? Top Kubernetes Scaling Strategies You Must Know
Over to you: Which other Kubernetes Scaling Strategy will you add to the list? Hiring Now: Tech RolesTop ML Roles Opened in the Last 12 Hours
High Impact Roles at High Growth AI Startups this week
High Salary General SWE Roles this week
SPONSOR USGet your product in front of more than 1,000,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com. © 2025 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 12:03 - 24 May 2025