- Mailing Lists
- in
- EP165: AI Agent versus MCP
Archives
- By thread 4924
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 35
EP165: AI Agent versus MCP
EP165: AI Agent versus MCP
✂️Cut your QA cycles down to minutes with QA Wolf (Sponsored)If slow QA processes bottleneck you or your software engineering team and you’re releasing slower because of it — you need to check out QA Wolf. QA Wolf’s AI-native service supports web and mobile apps, delivering 80% automated test coverage in weeks and helping teams ship 5x faster by reducing QA cycles to minutes. QA Wolf takes testing off your plate. They can get you:
The benefit? No more manual E2E testing. No more slow QA cycles. No more bugs reaching production. With QA Wolf, Drata’s team of 80+ engineers achieved 4x more test cases and 86% faster QA cycles. This week’s system design refresher:
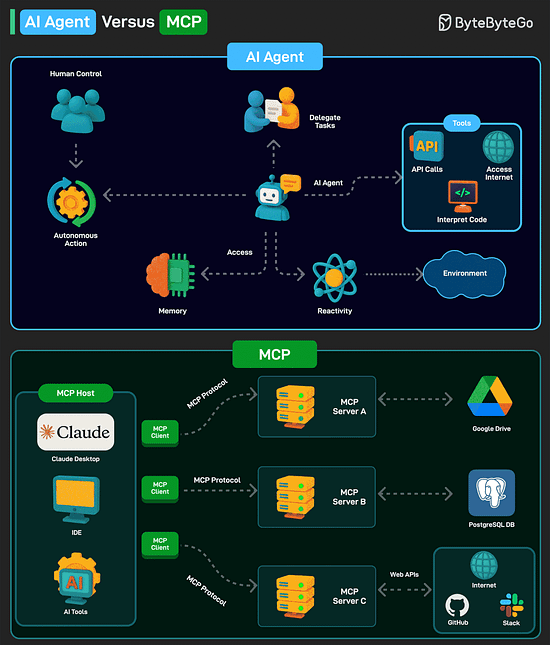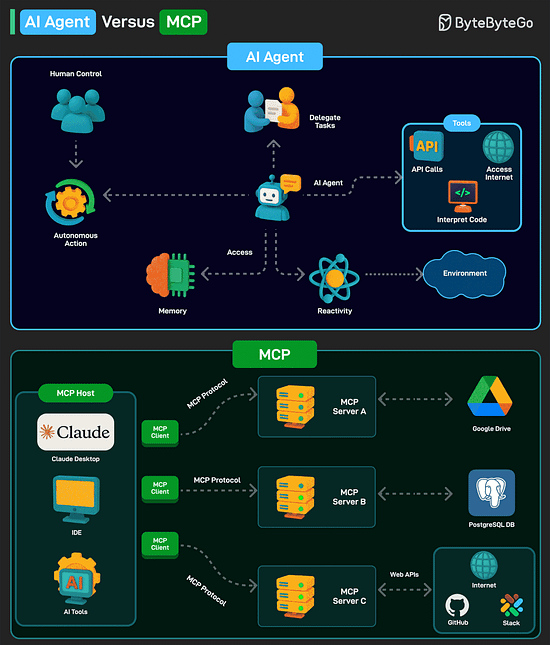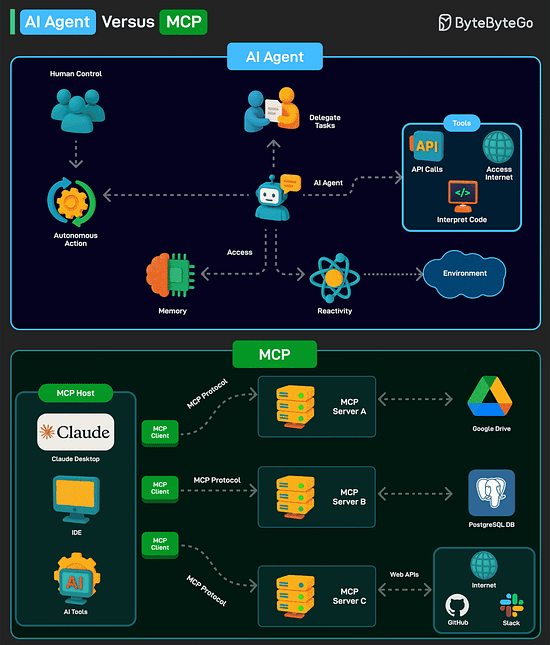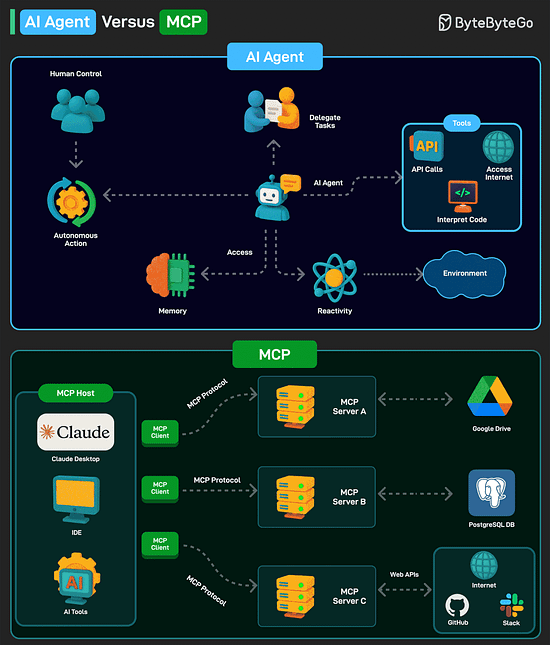
AI Agent versus MCPAn AI agent is a software program that can interact with its environment, gather data, and use that data to achieve predetermined goals. AI agents can choose the best actions to perform to meet those goals. Key characteristics of AI agents are as follows:
Model Context Protocol (MCP) is a new system introduced by Anthropic to make AI models more powerful. It is an open standard that allows AI models (like Claude) to connect to databases, APIs, file systems, and other tools without needing custom code for each new integration. MCP follows a client-server model with 3 key components:
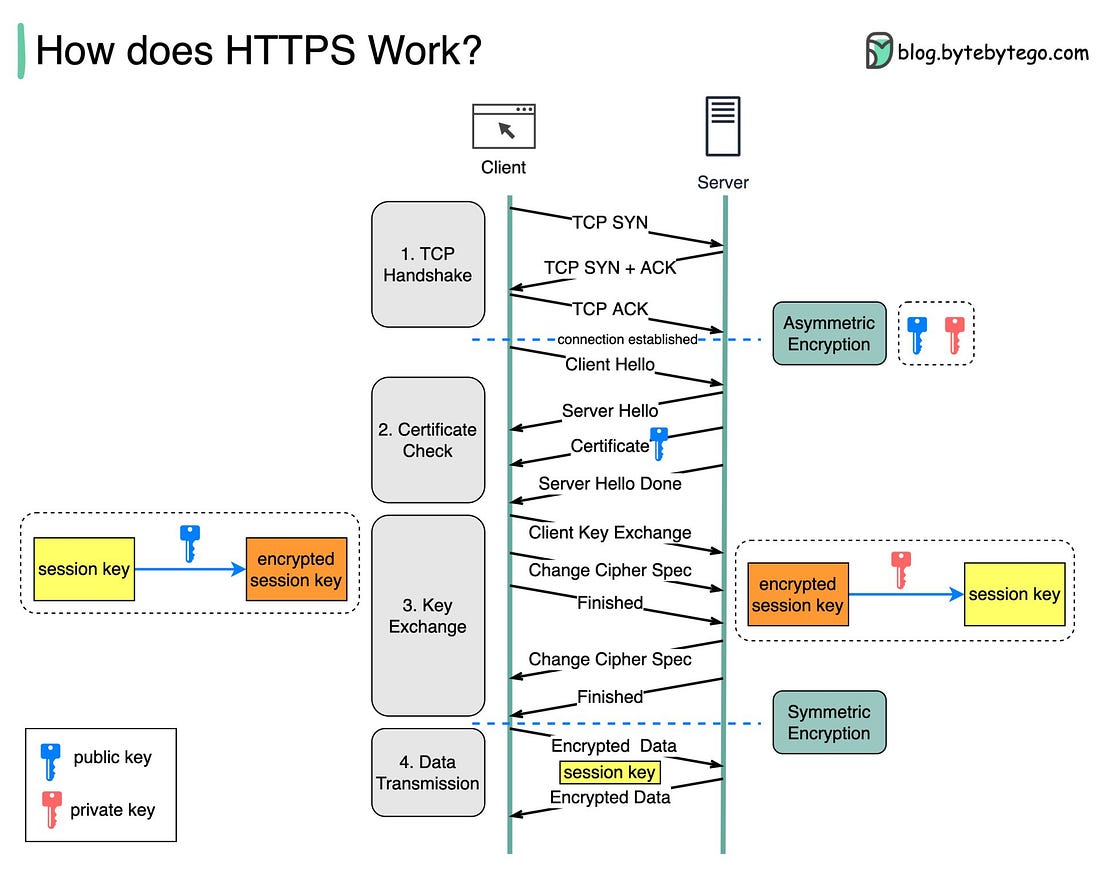
Over to you: Have you used AI Agents or MCP? Stop Software Erosion with Smarter Static Code Analysis (Sponsored)This webinar, "Using Static Code Analysis Correctly", explores how static code analysis can be a powerful ally in maintaining code quality, preventing software erosion, and ensuring long-term maintainability. Whether you're working in automotive, medical, embedded systems, or other safety-critical industries, you'll gain practical insights into spotting design drift, managing architectural consistency, and avoiding common pitfalls in C and C++ codebases. In this 40-minute webinar, we break down real-world challenges and demonstrate how thoughtful use of static analysis can help you build more robust, reliable systems from the inside out. How does HTTPS work?Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP.) HTTPS transmits encrypted data using Transport Layer Security (TLS.) If the data is hijacked online, all the hijacker gets is binary code. How is the data encrypted and decrypted? Step 1 - The client (browser) and the server establish a TCP connection. Step 2 - The client sends a “client hello” to the server. The message contains a set of necessary encryption algorithms (cipher suites) and the latest TLS version it can support. The server responds with a “server hello” so the browser knows whether it can support the algorithms and TLS version. The server then sends the SSL certificate to the client. The certificate contains the public key, host name, expiry dates, etc. The client validates the certificate. Step 3 - After validating the SSL certificate, the client generates a session key and encrypts it using the public key. The server receives the encrypted session key and decrypts it with the private key. Step 4 - Now that both the client and the server hold the same session key (symmetric encryption), the encrypted data is transmitted in a secure bi-directional channel. Why does HTTPS switch to symmetric encryption during data transmission? There are two main reasons:
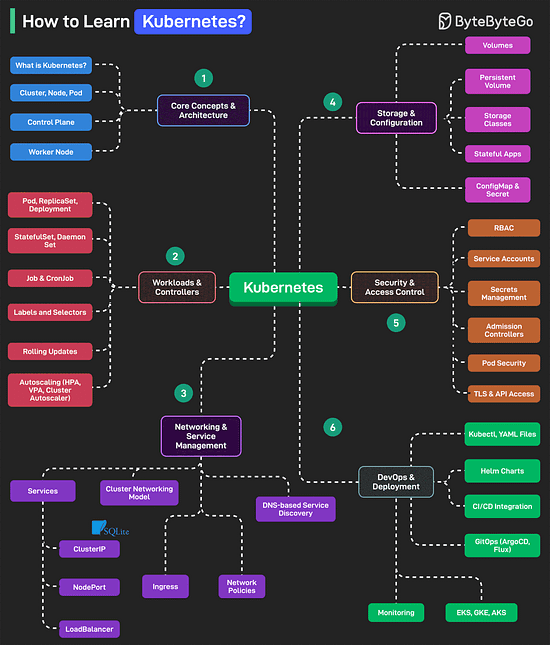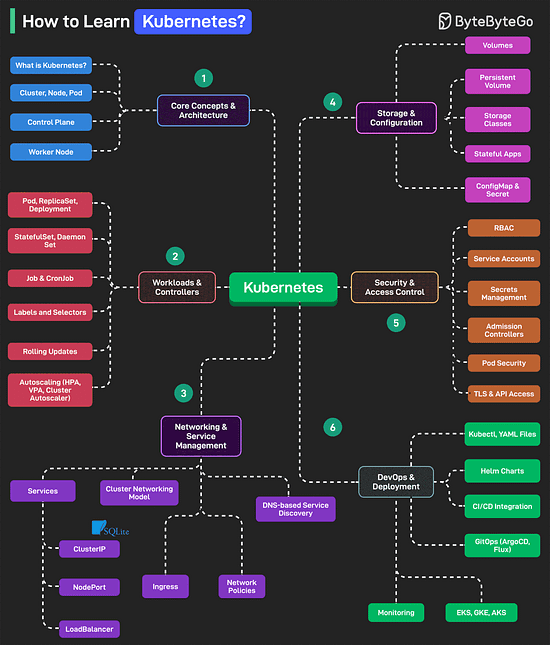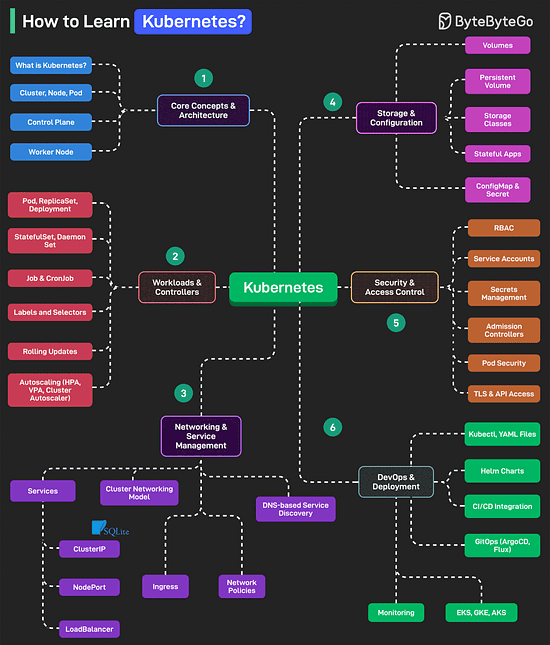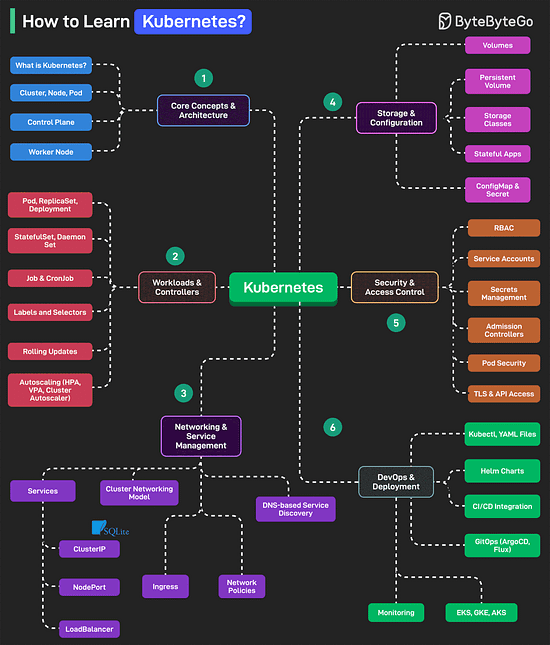
Over to you: how much performance overhead does HTTPS add, compared to HTTP? How to Learn Kubernetes?Kubernetes is an open-source container orchestration platform that automates the deployment, scaling, and management of containerized applications.
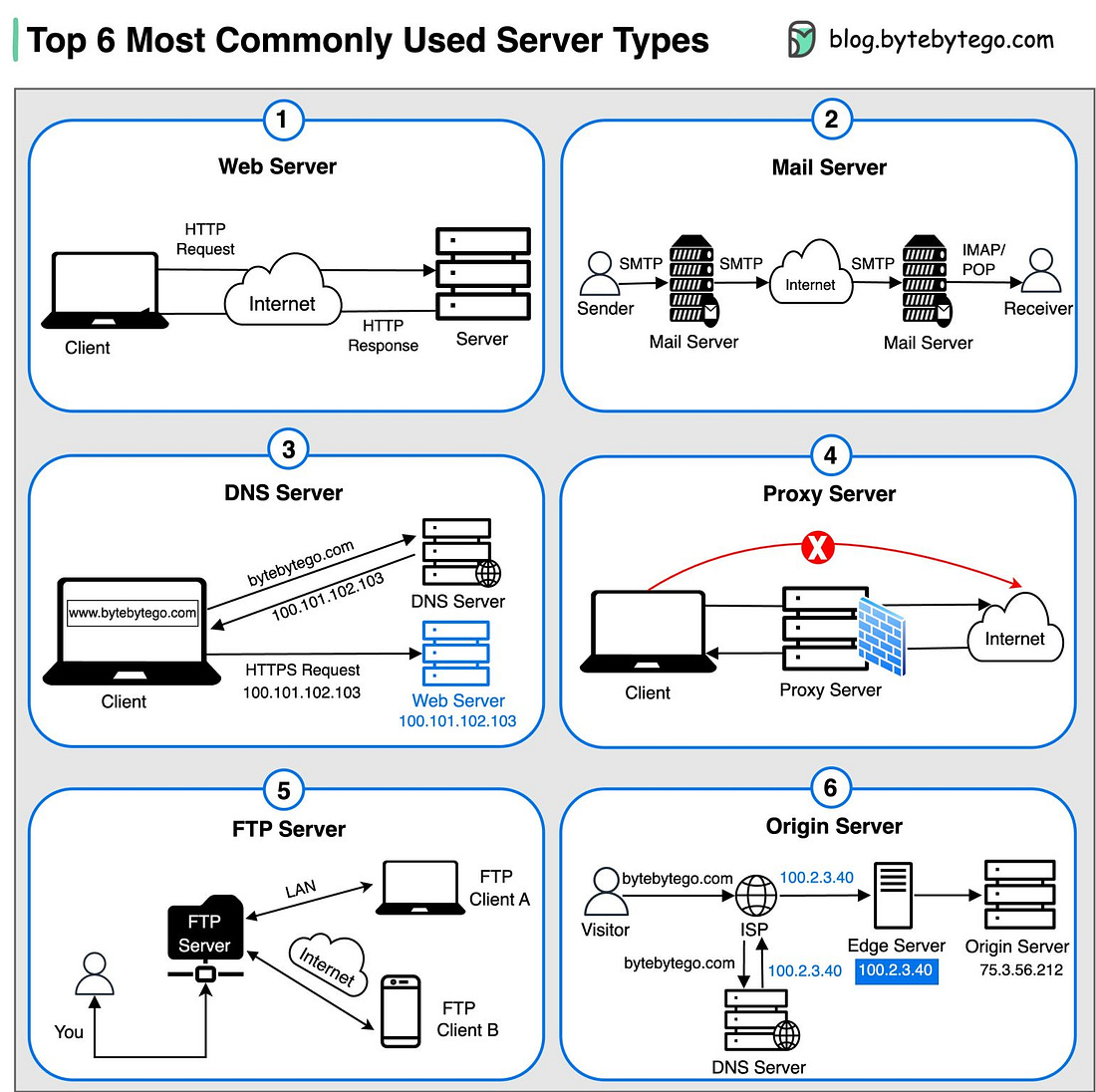
Over to you: What else will you add to the list for learning Kubernetes? Top 6 most commonly used Server Types
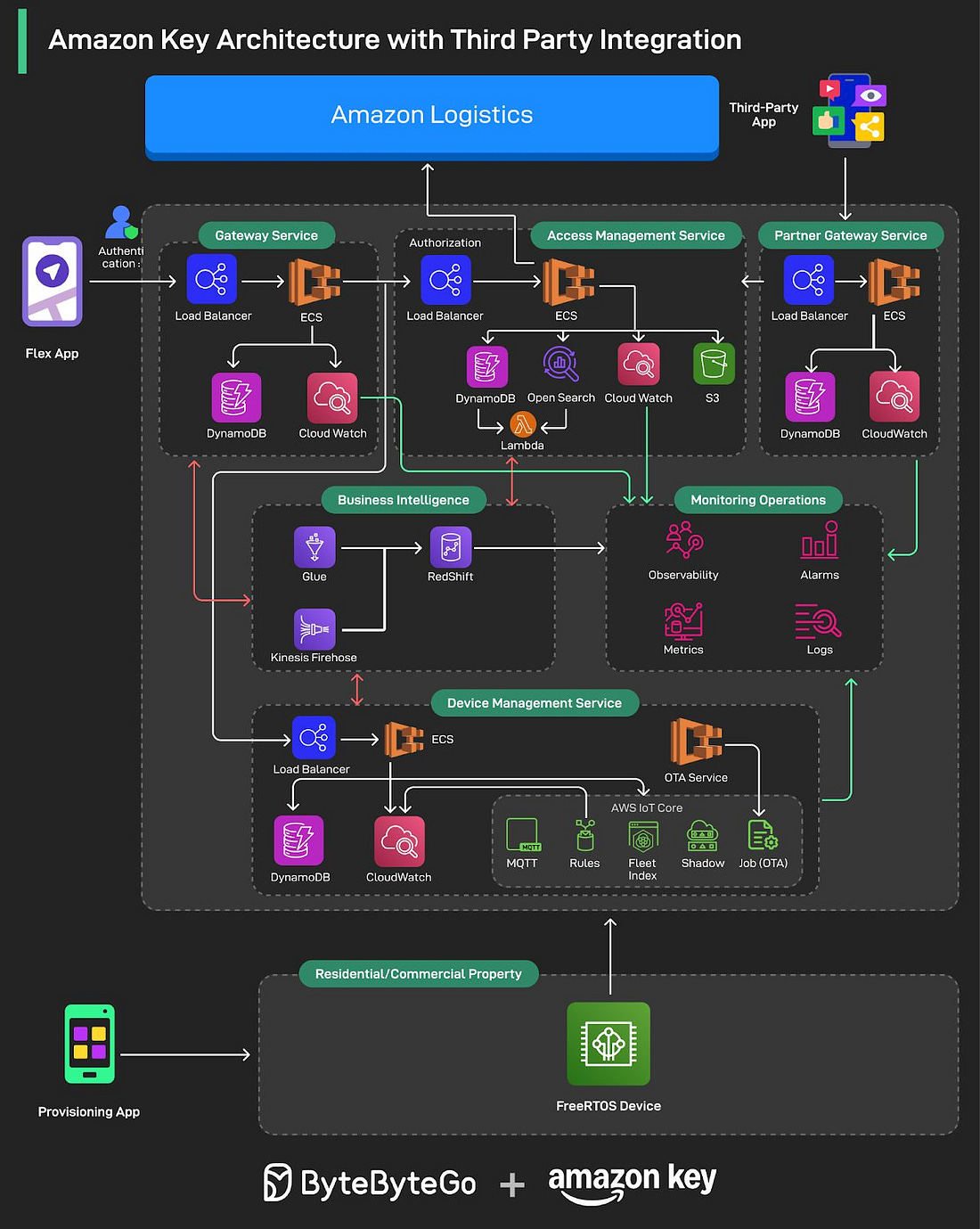
Over to you: Which type of server do you find most crucial in your online experience? Amazon Key Architecture with Third Party IntegrationAmazon Key is a REALLY convenient way to have your packages securely delivered right inside your garage or multifamily property. This story is packed with valuable lessons on:
Dive into the full newsletter here. Hiring Now: Top AI Startups and AI RolesThis Week’s High-Impact Roles at Fast-Growing AI Startups
High Salary SWE Roles this week
Today’s latest ML positions - hiring now!
SPONSOR USGet your product in front of more than 1,000,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com. © 2025 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:37 - 31 May 2025