- Mailing Lists
- in
- EP69: Explaining JSON Web Token (JWT) To a 10 Year Old Kid
Archives
- By thread 5193
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 4
EP69: Explaining JSON Web Token (JWT) To a 10 Year Old Kid
EP69: Explaining JSON Web Token (JWT) To a 10 Year Old Kid
This is a sneak peek of today’s paid newsletter for our premium subscribers. Get access to this issue and all future issues - by subscribing today. Latest articlesIf you’re not a subscriber, here’s what you missed this mont To receive all the full articles and support ByteByteGo, consider subscribing: This week’s system design refresher:
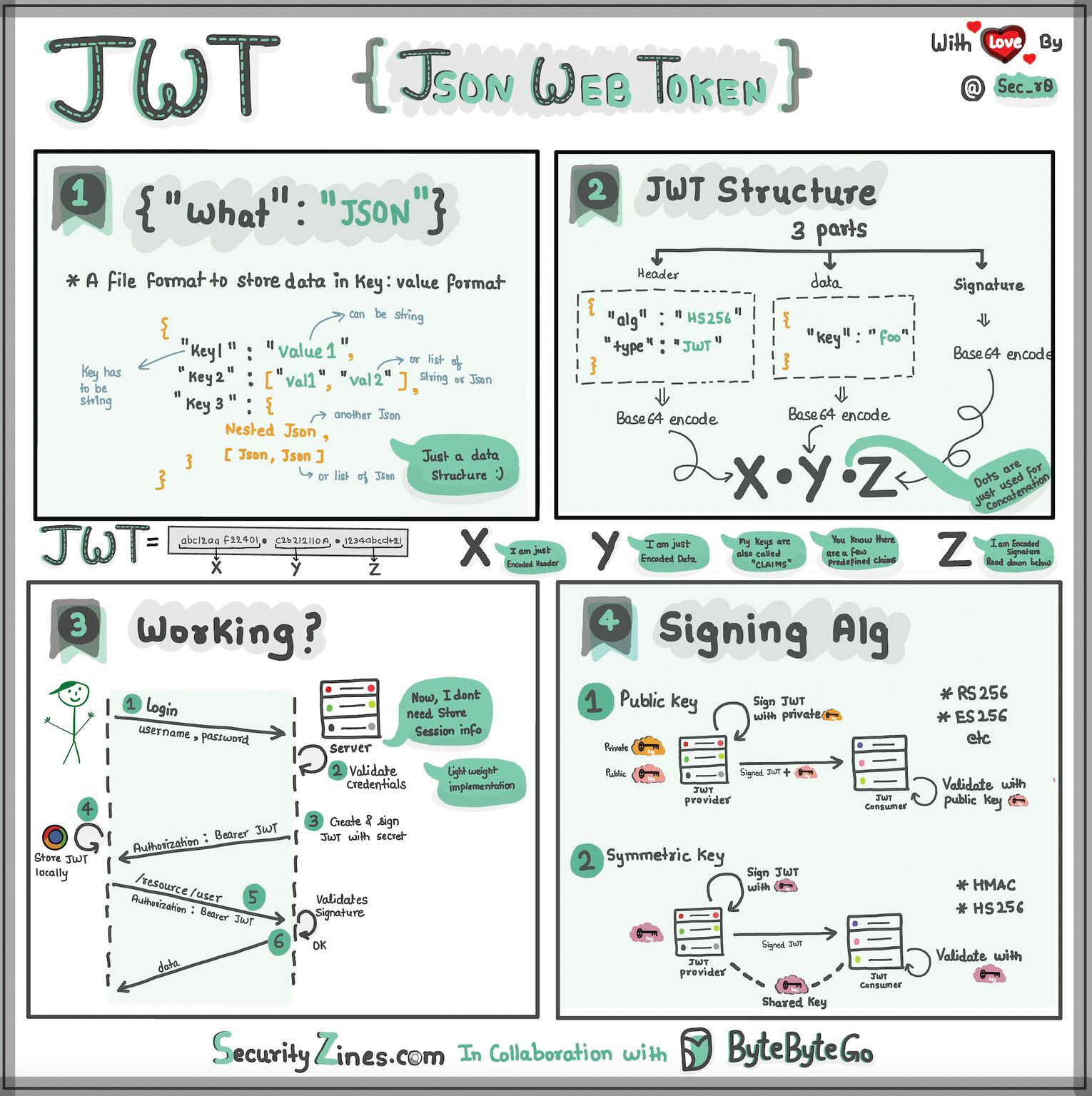
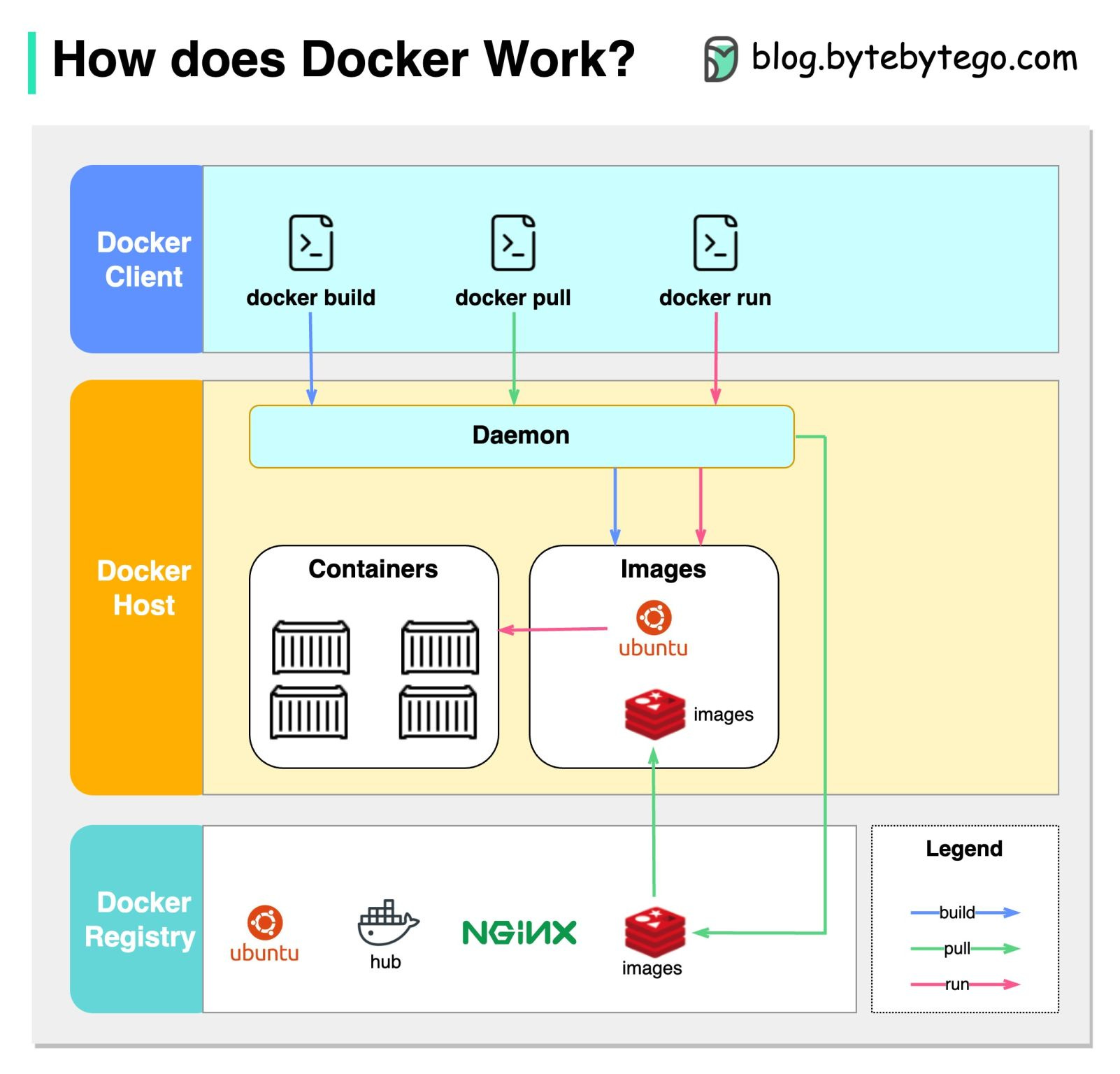
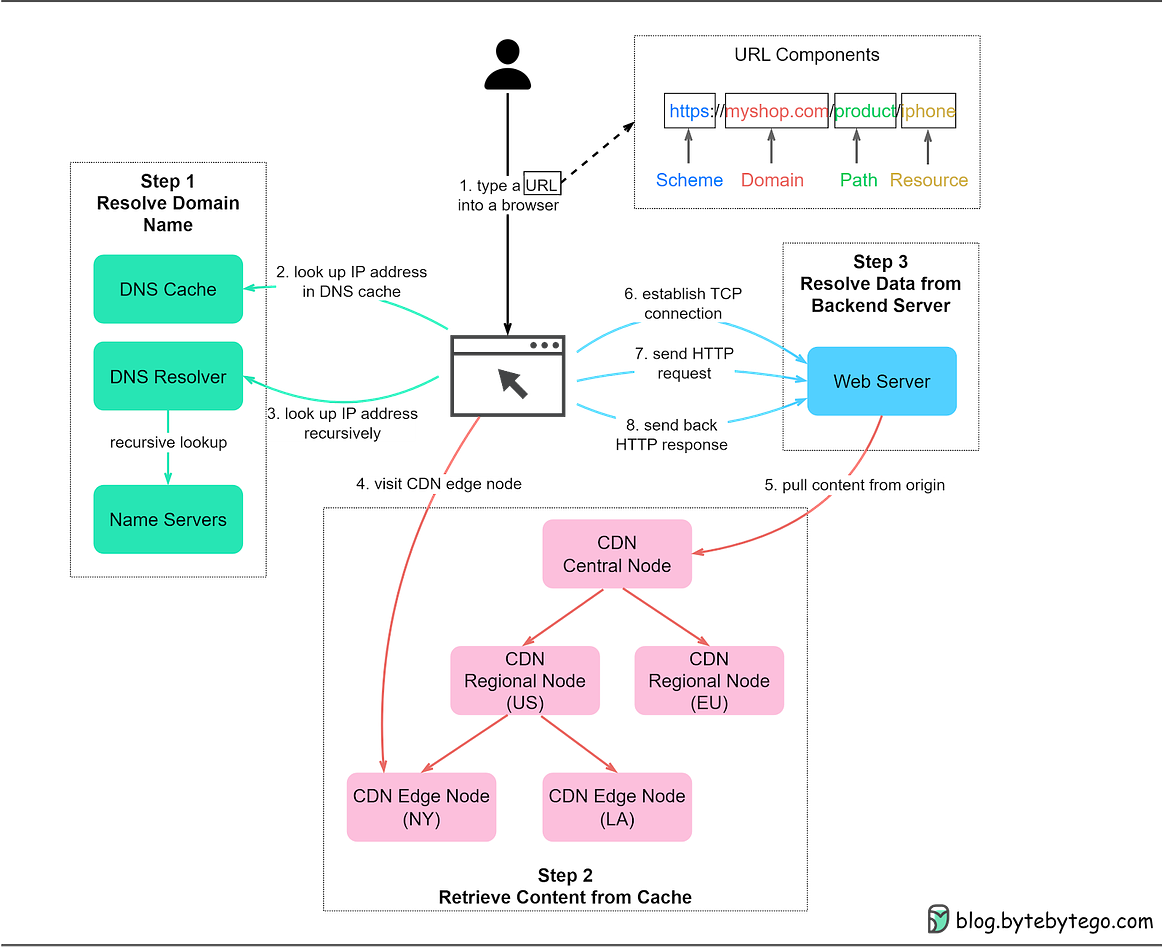
DevOps vs. SRE vs. Platform Engineering Explaining JSON Web Token (JWT) to a 10 year old KidImagine you have a special box called a JWT. Inside this box, there are three parts: a header, a payload, and a signature. The header is like the label on the outside of the box. It tells us what type of box it is and how it's secured. It's usually written in a format called JSON, which is just a way to organize information using curly braces { } and colons : The payload is like the actual message or information you want to send. It could be your name, age, or any other data you want to share. It's also written in JSON format, so it's easy to understand and work with. Now, the signature is what makes the JWT secure. It's like a special seal that only the sender knows how to create. The signature is created using a secret code, kind of like a password. This signature ensures that nobody can tamper with the contents of the JWT without the sender knowing about it. When you want to send the JWT to a server, you put the header, payload, and signature inside the box. Then you send it over to the server. The server can easily read the header and payload to understand who you are and what you want to do. Over to you: When should we use JWT for authentication? What are some other authentication methods? Guest post by Rohit Sehgal. How does Docker work?The diagram below shows the architecture of Docker and how it works when we run “docker build”, “docker pull” and “docker run”. There are 3 components in Docker architecture:
Let’s take the “docker run” command as an example.
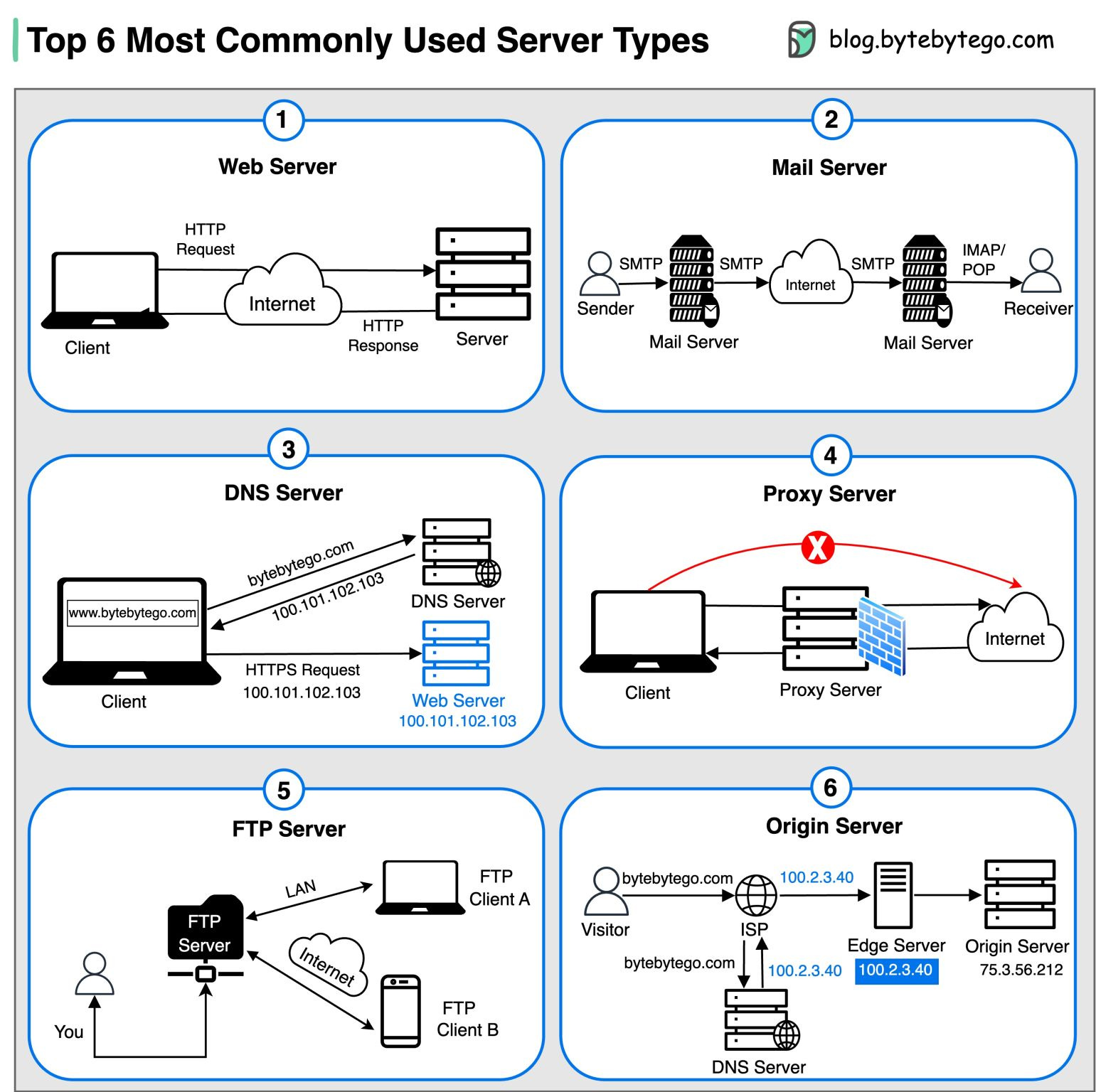
Top 6 most commonly used Server Types
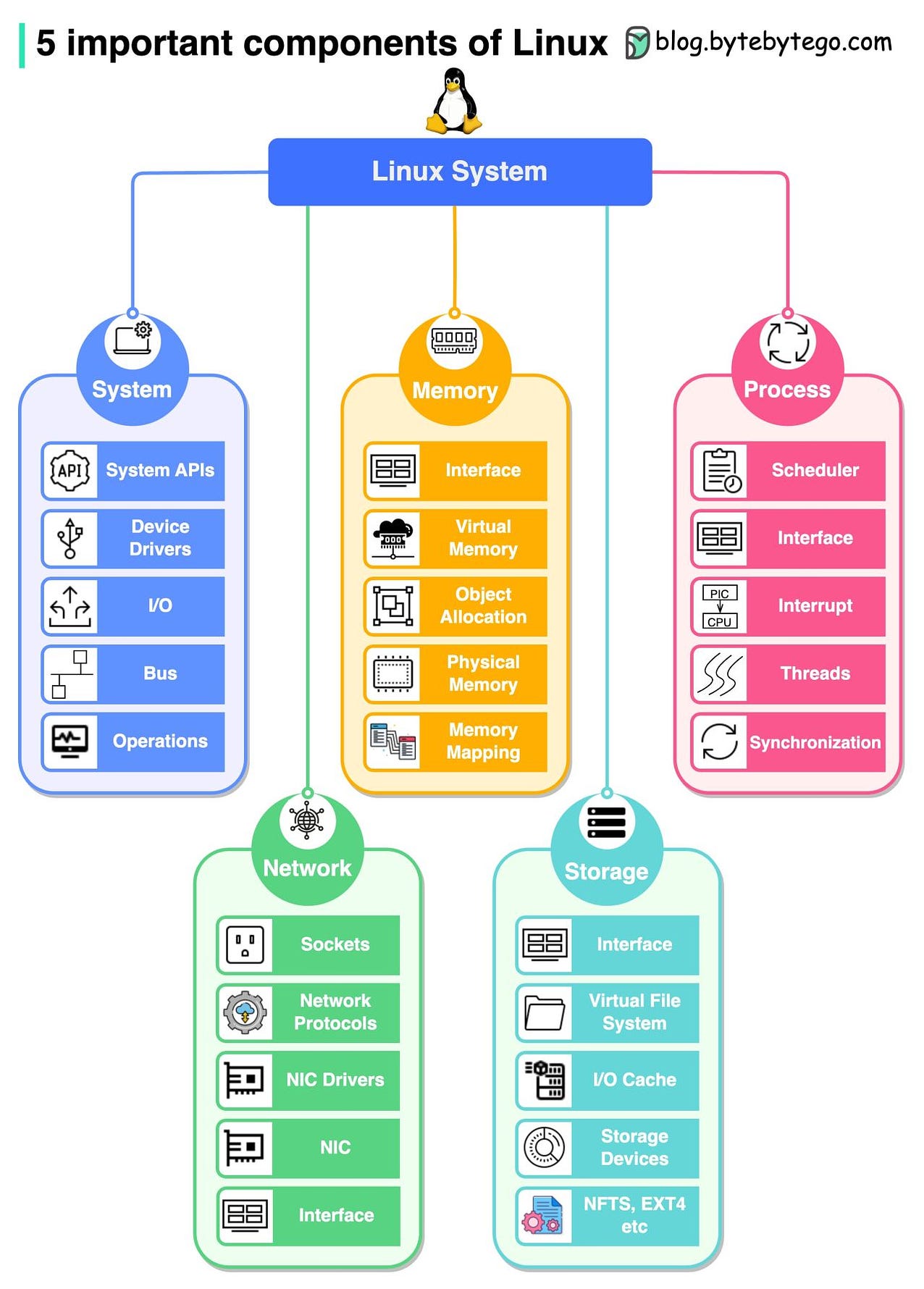
Over to you: Which type of server do you find most crucial in your online experience? Guest post by Govardhana Miriyala Kannaiah. Learning Linux system
SPONSOR US📈Feature your product in the biggest technology newsletter on Substack ByteByteGo is the biggest technology newsletter on Substack with 500,000 readers working at companies like Apple, Meta, Amazon, Google, etc. They have the influence and autonomy to make large purchase decisions. If you are interested in sponsoring us, please send an email to hi@bytebytego.com. Latest articlesHere are the latest articles you may have missed: To receive all the full articles and support ByteByteGo, consider subscribing: © 2023 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:38 - 22 Jul 2023