- Mailing Lists
- in
- EP72: OAuth 2.0 Explained With Simple Terms
Archives
- By thread 5315
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 127
Cómo usar la IA generativa para crear valor
You’re invited to the latest DevCon workshop: How To Build a Smart Queue Management System
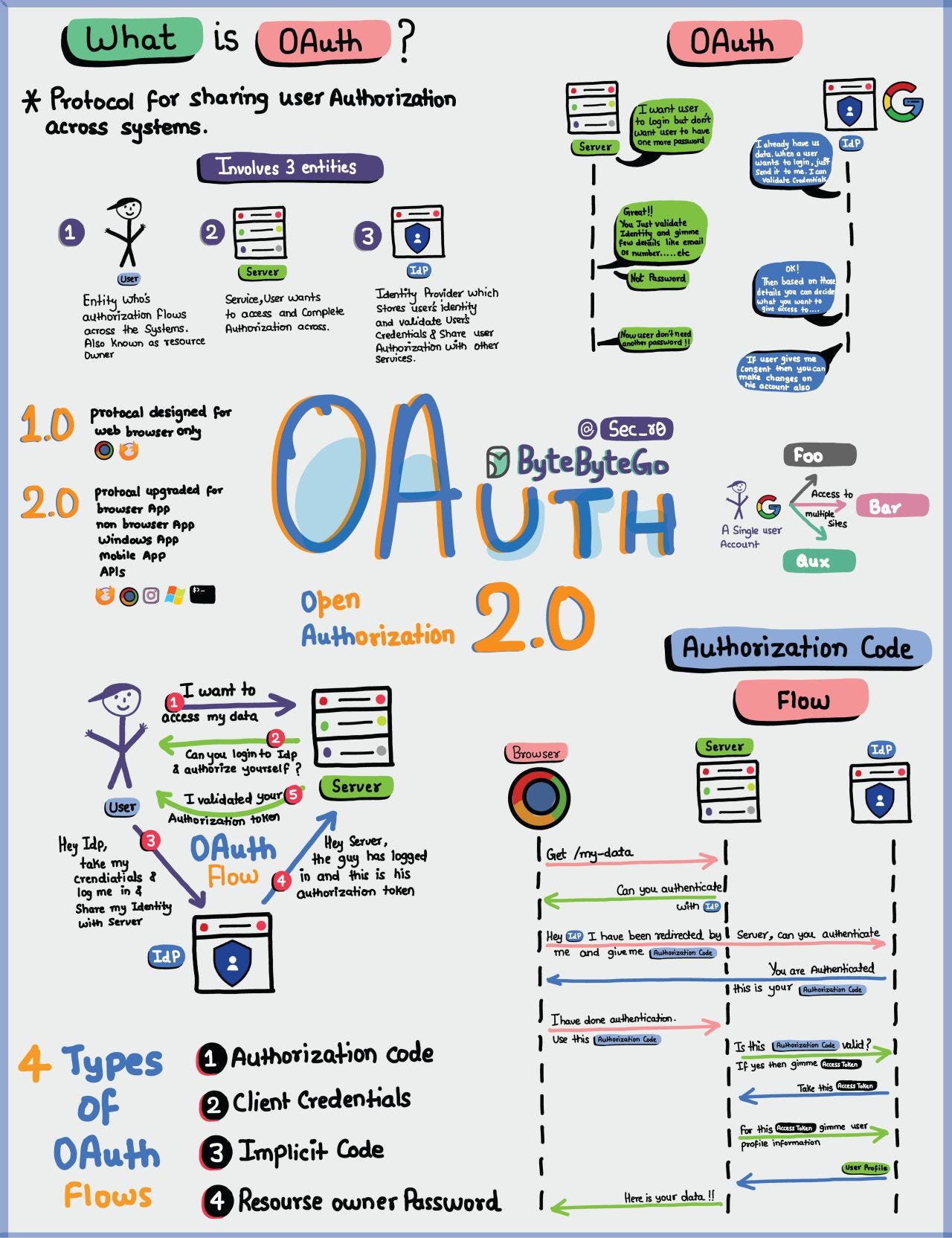
EP72: OAuth 2.0 Explained With Simple Terms
EP72: OAuth 2.0 Explained With Simple Terms
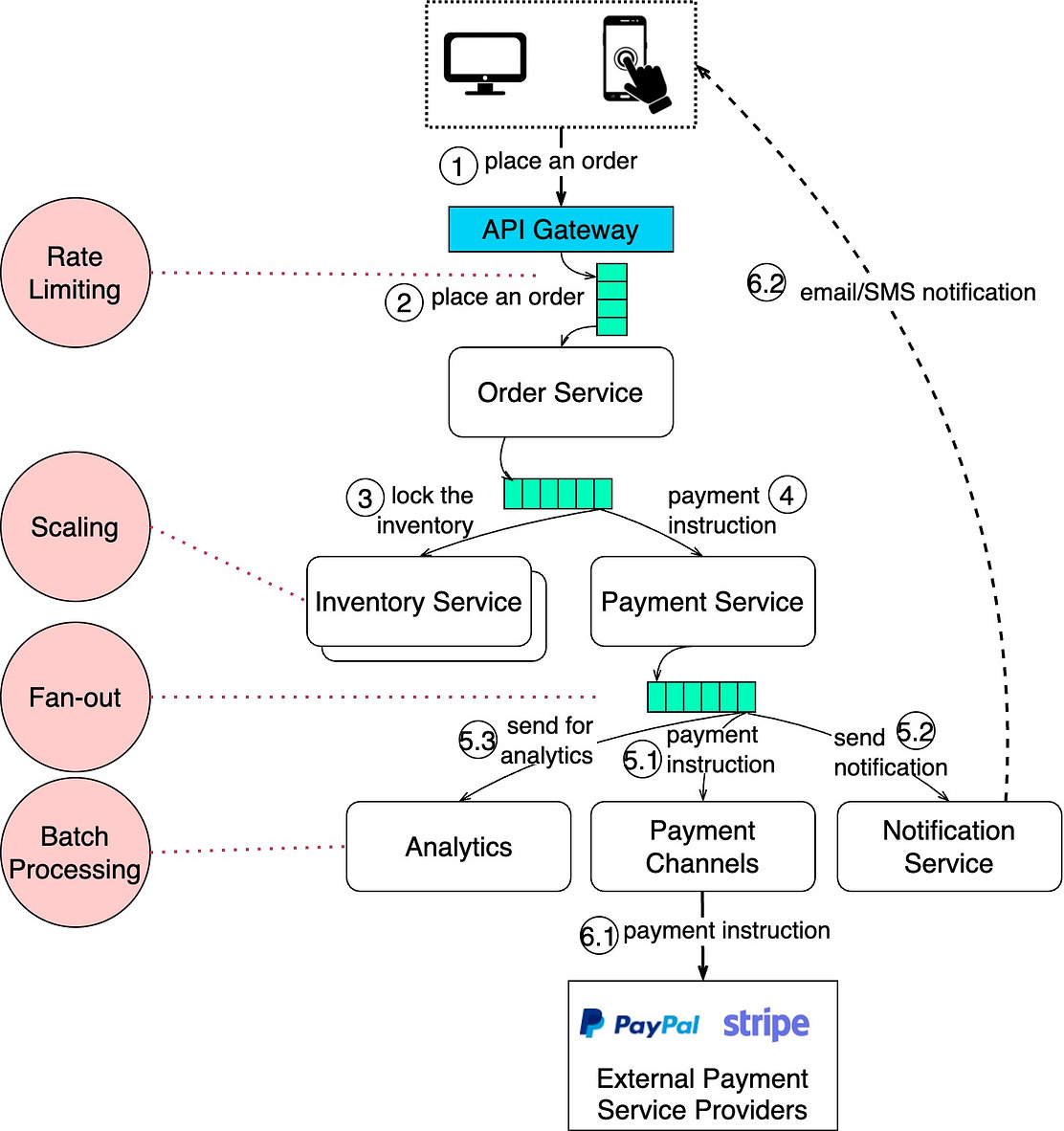
This week’s system design refresher:
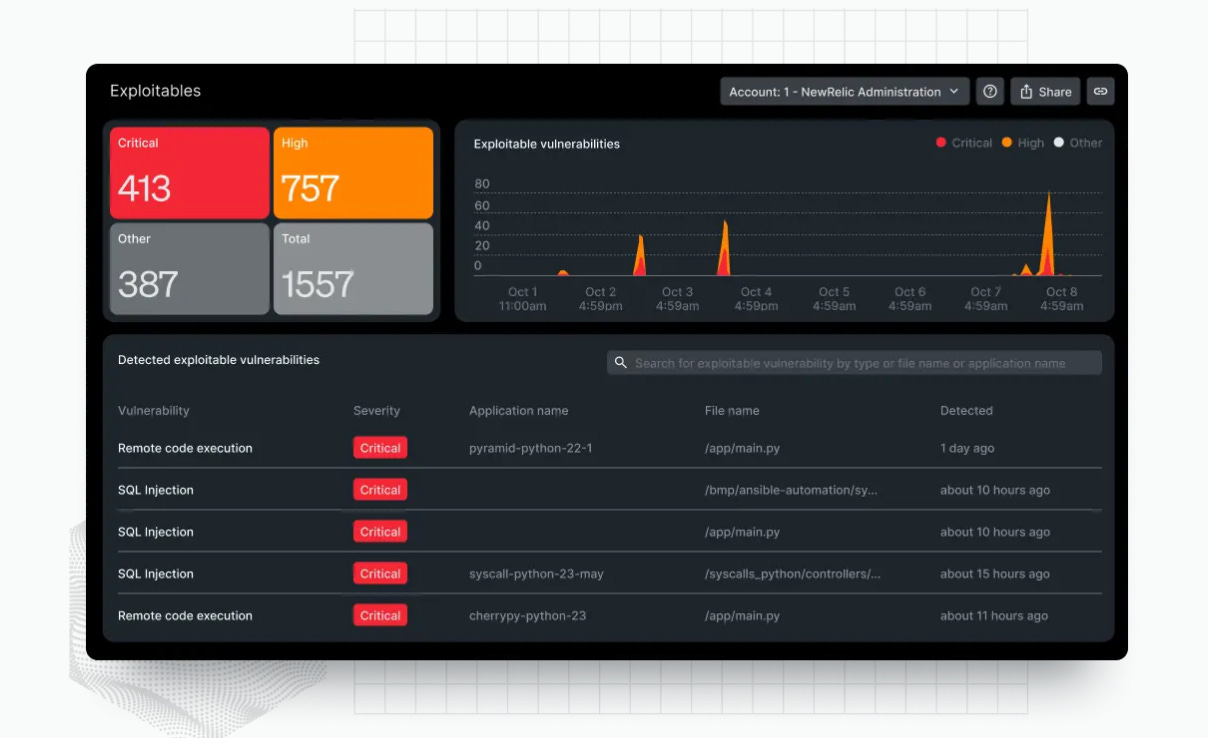
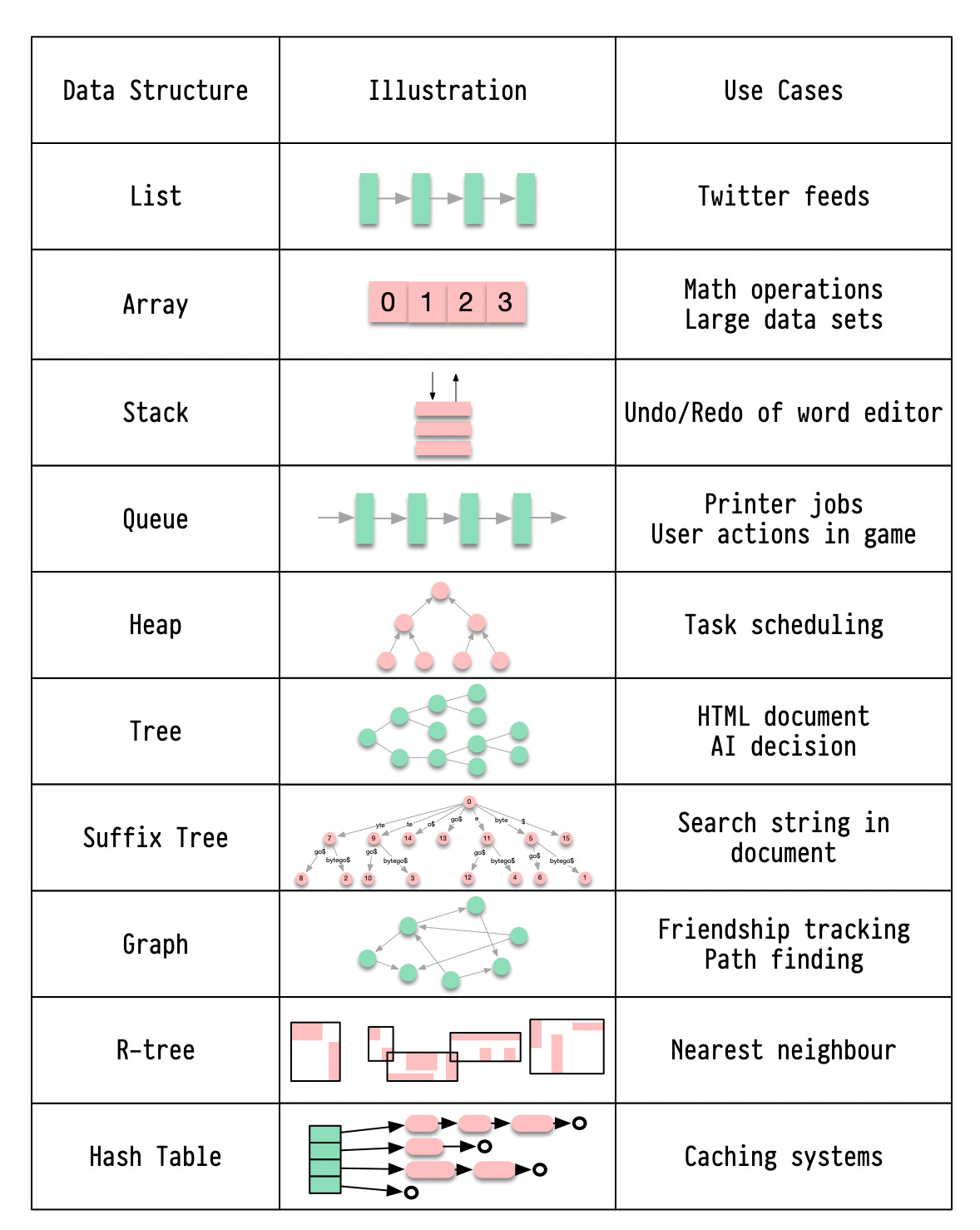
Introducing New Relic Interactive Application Security Testing (IAST)(Sponsored)New Relic Interactive Application Security Testing (IAST) is now in public preview! Engineers, DevOps, and security teams can now find, fix, and verify high-risk vulnerabilities early and accurately to build more secure applications—and ship code faster. Git Merge vs. Rebase vs. Squash Commit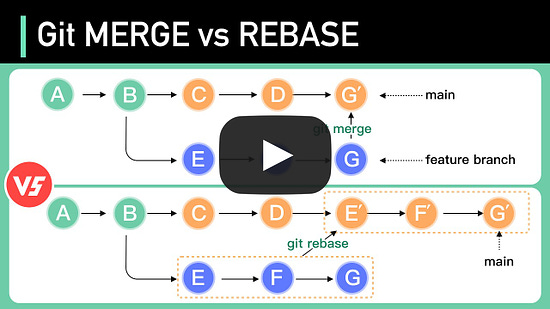 Oauth 2.0 Explained With Simple TermsOAuth 2.0 is a powerful and secure framework that allows different applications to securely interact with each other on behalf of users without sharing sensitive credentials. The entities involved in OAuth are the User, the Server, and the Identity Provider (IDP). Latest articlesIf you’re not a paid subscriber, here’s what you missed this month.
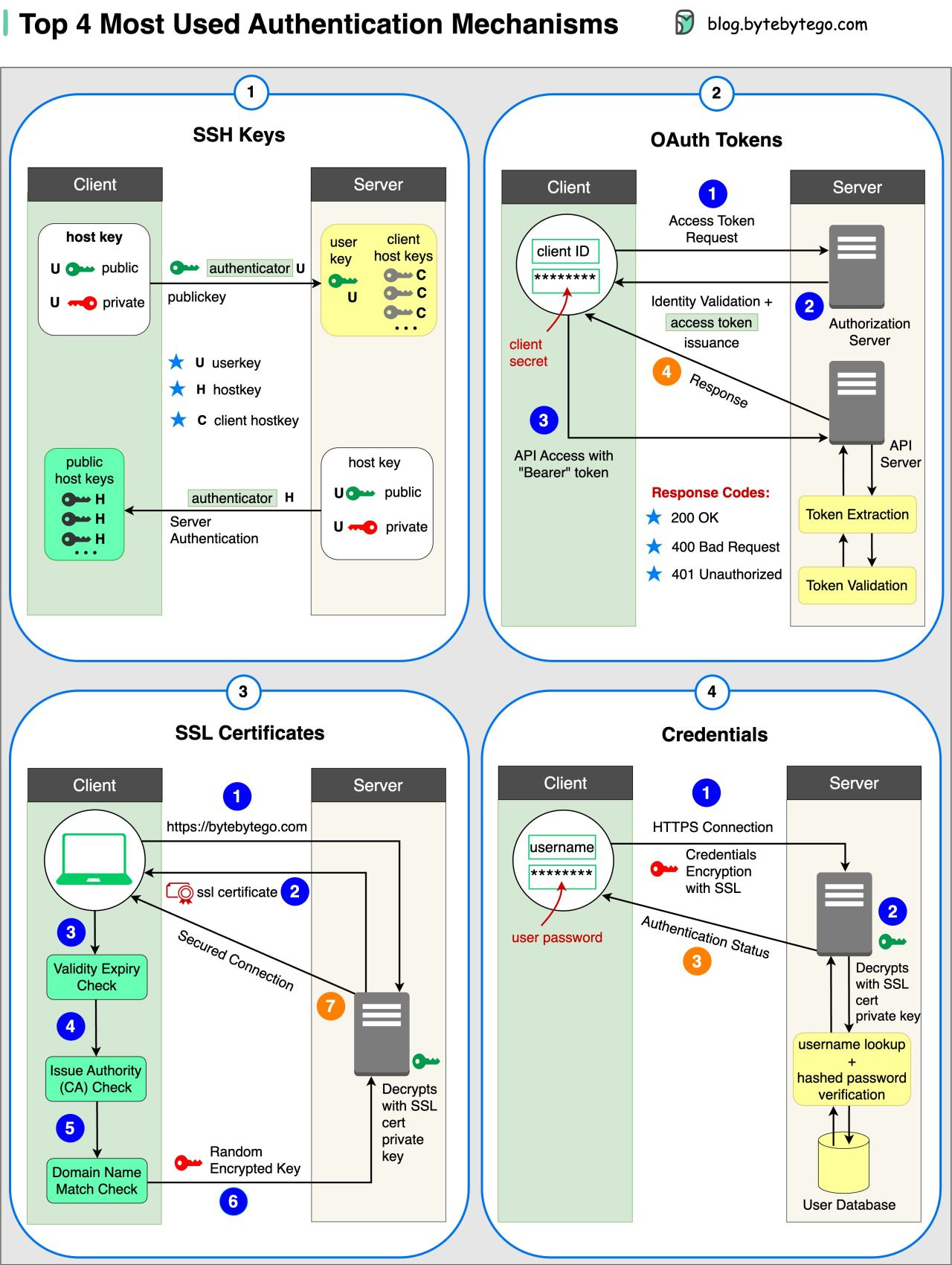
To receive all the full articles and support ByteByteGo, consider subscribing: Top 4 Forms of Authentication Mechanisms
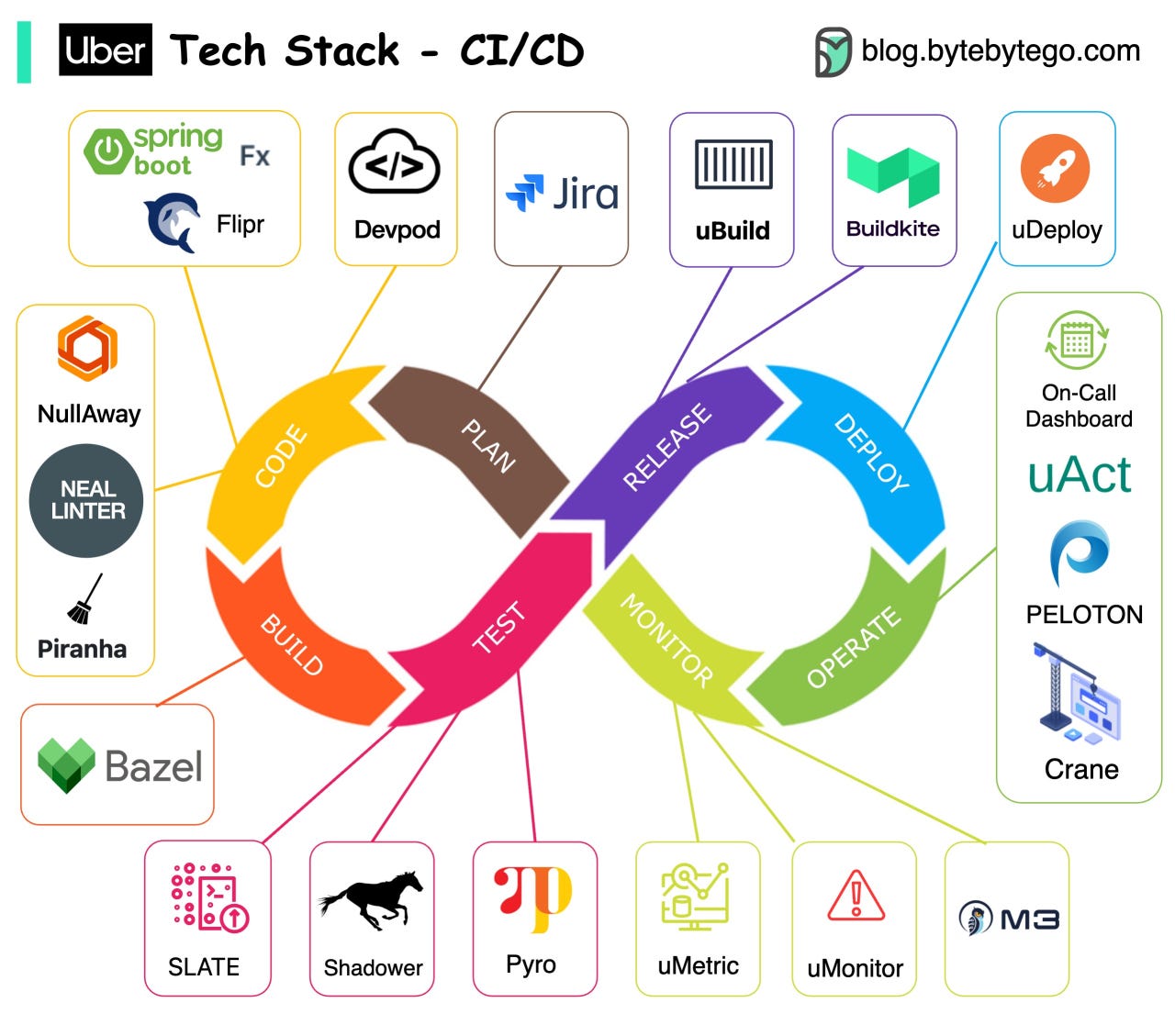
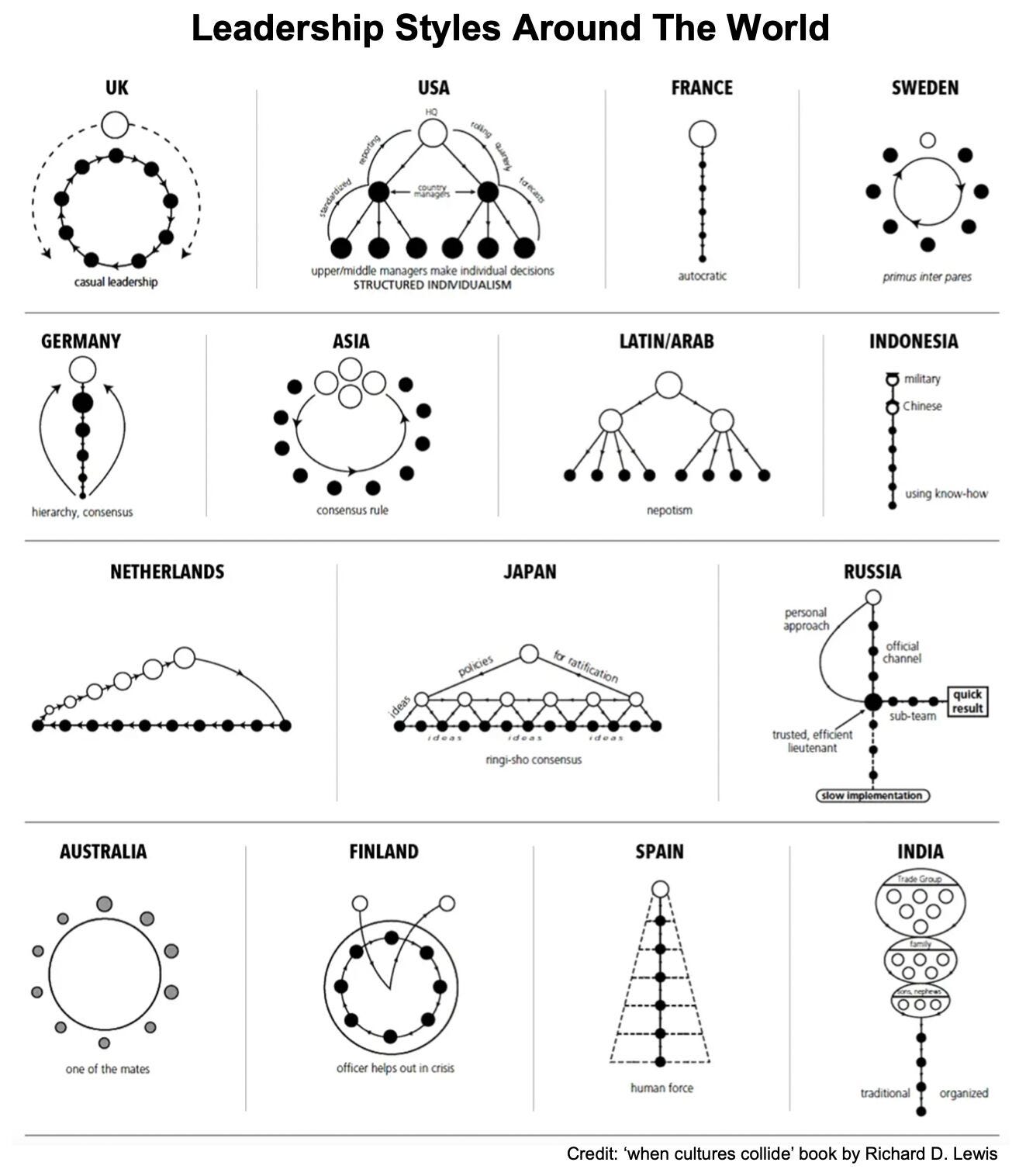
Over to you: How do you manage those security keys? Is it a good idea to put them in a GitHub repository? Guest post by Govardhana Miriyala Kannaiah. Uber Tech Stack - CI/CDUber is one of the most innovative companies in the engineering field. Let’s take a look at their CI/CD tech stacks. Note: This post is based on research on Uber engineering blogs. If you spot any inaccuracies, please let us know. Leadership Styles Around The WorldDifferent leadership styles can be profoundly influenced by cultural differences. Do you agree with the diagram? Credit: ‘When cultures collide’ book by Richard D. Lewis Latest articlesHere are the latest articles you may have missed: To receive all the full articles and support ByteByteGo, consider subscribing: © 2023 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:35 - 12 Aug 2023