| This week’s system design refresher: CAP, BASE, SOLID, KISS, What do these acronyms mean? Single Sign-On (SSO) explained in simple terms Imperative Vs Functional Vs Object-oriented Programming Data Pipelines Overview
Are lofty DevOps ideals translating into better results for companies? Has AI begun to show an impact on software team productivity? This 2023 report by the DevOps Research and Assessment (DORA) team at Google and LinearB collates research from over 36,000 professionals worldwide, covering: Key outcomes from DORA (including measures and benchmarks for high performers) DORA metric performance across applications Technical and cultural performance predictors The impact of AI and cloud infrastructure
Now, you can get a free copy of the full report. Get Your Free Copy
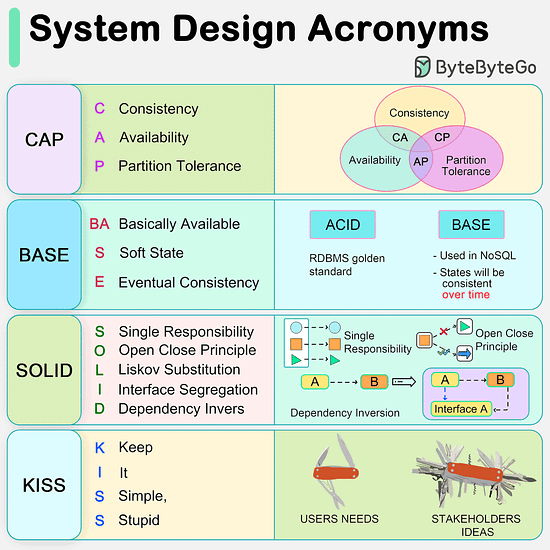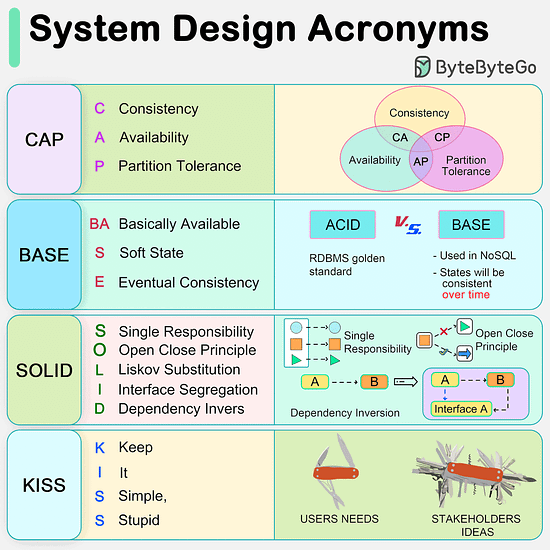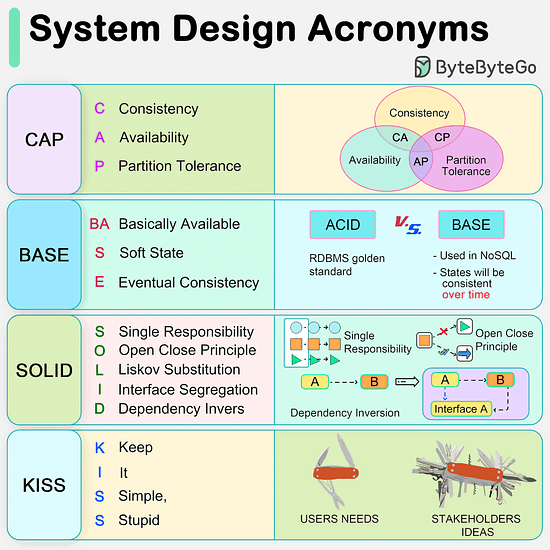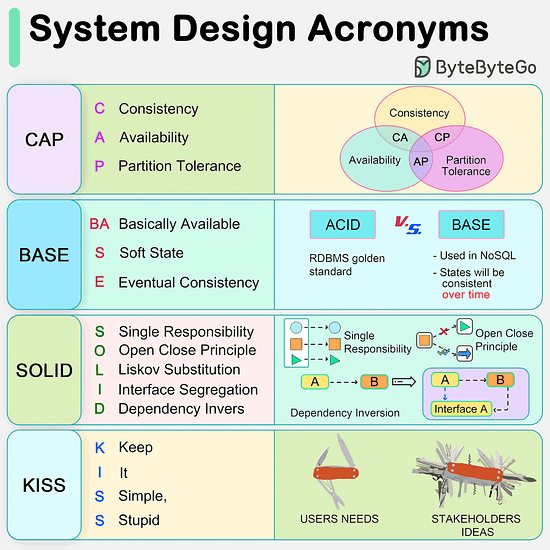
CAP, BASE, SOLID, KISS, What do these acronyms mean?The diagram below explains the common acronyms in system designs. CAP
CAP theorem states that any distributed data store can only provide two of the following three guarantees:
1. Consistency - Every read receives the most recent write or an error.
2. Availability - Every request receives a response.
3. Partition tolerance - The system continues to operate in network faults.
However, this theorem was criticized for being too narrow for distributed systems, and we shouldn’t use it to categorize the databases. Network faults are guaranteed to happen in distributed systems, and we must deal with this in any distributed systems.
You can read more on this in “Please stop calling databases CP or AP” by Martin Kleppmann. BASE
The ACID (Atomicity-Consistency-Isolation-Durability) model used in relational databases is too strict for NoSQL databases. The BASE principle offers more flexibility, choosing availability over consistency. It states that the states will eventually be consistent. SOLID
SOLID principle is quite famous in OOP. There are 5 components to it.
1. SRP (Single Responsibility Principle)
Each unit of code should have one responsibility.
2. OCP (Open Close Principle)
Units of code should be open for extension but closed for modification.
3. LSP (Liskov Substitution Principle)
A subclass should be able to be substituted by its base class.
4. ISP (Interface Segregation Principle)
Expose multiple interfaces with specific responsibilities.
5. DIP (Dependency Inversion Principle)
Use abstractions to decouple dependencies in the system. KISS
"Keep it simple, stupid!" is a design principle first noted by the U.S. Navy in 1960. It states that most systems work best if they are kept simple.
Over to you: Have you invented any acronyms in your career?
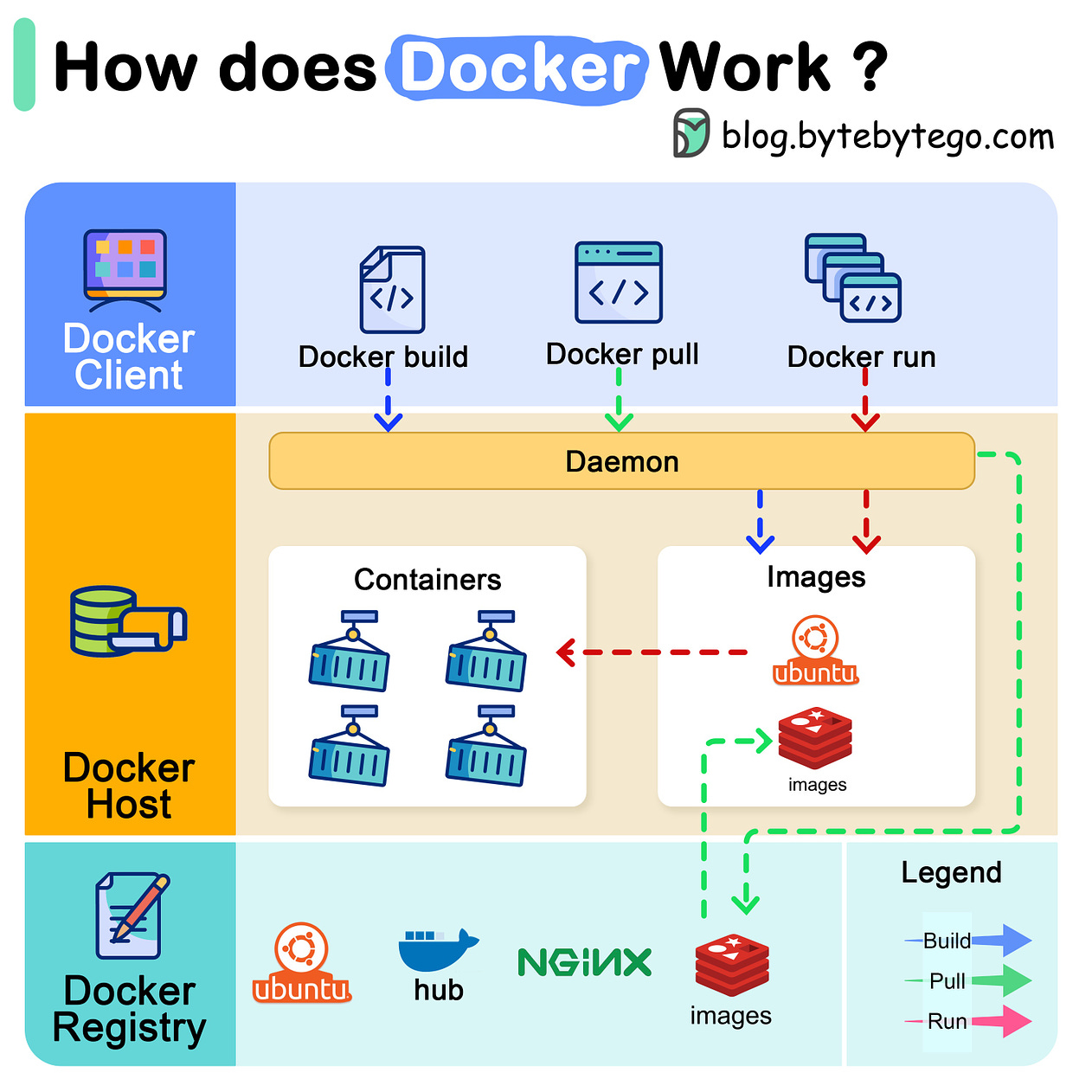
Latest articlesIf you’re not a paid subscriber, here’s what you missed this month. Does Serverless Have Servers? A Crash Course in Docker Shipping to Production Kubernetes: When and How to Apply It A Crash Course in Kubernetes
To receive all the full articles and support ByteByteGo, consider subscribing:
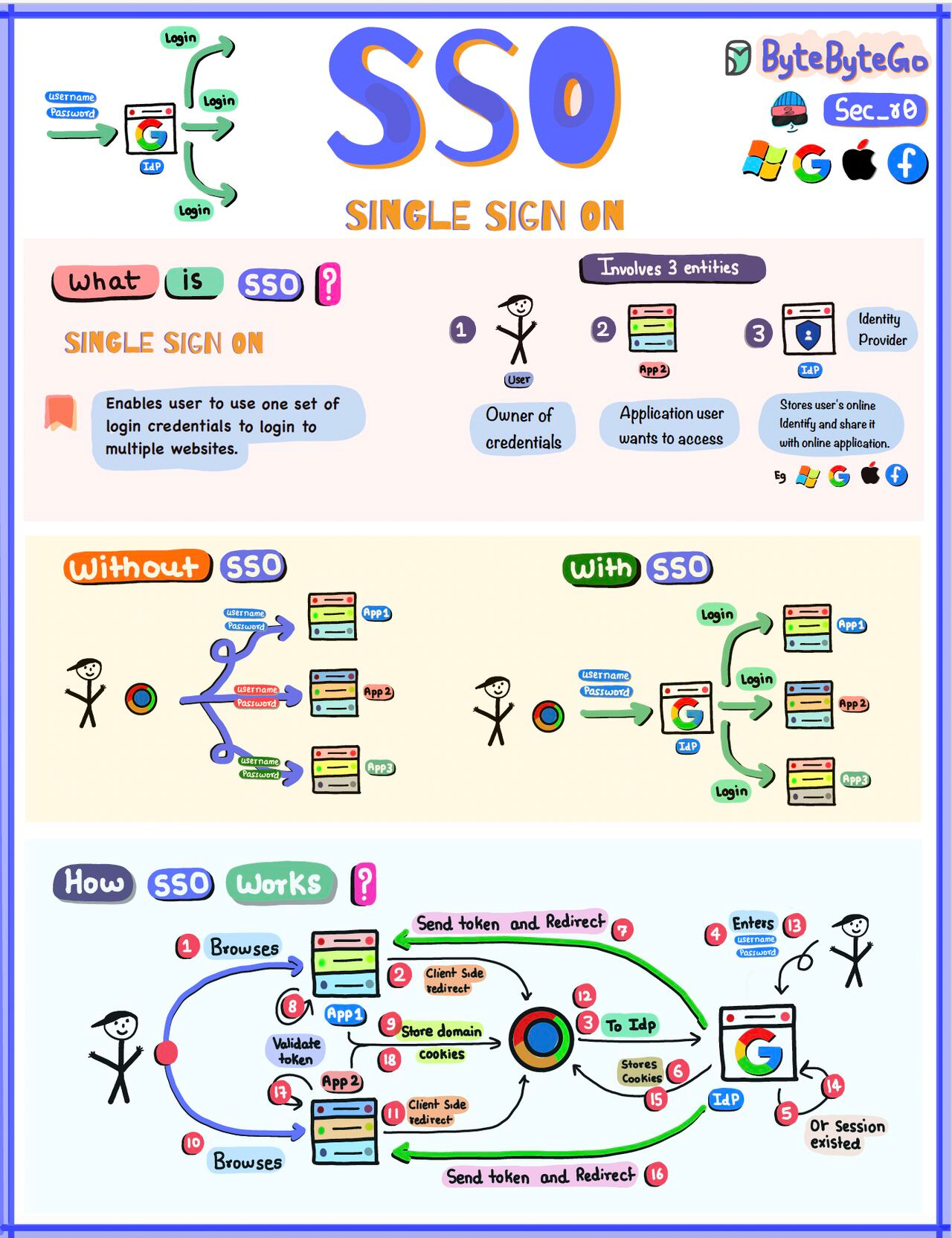
Single Sign-On (SSO) explained in simple termsThe concepts of SSO revolve around the three key players: the User, the Identity Provider (IDP), and the Application. The end-user or individual who seeks access to various applications. Identity Provider (IDP): An entity responsible for user authentication and verification. Common IDPs include Google, Facebook, and company-specific systems. Application: The software or service that the user wants to access. Applications rely on the IDP for user authentication. With SSO, users can seamlessly log in to various applications with a single set of credentials, enhancing convenience and security.
Single Sign-On (SSO) simplifies user access by enabling them to log in to multiple applications with a single set of credentials, enhancing the user experience and reducing password fatigue. It also centralizes security and access management, improving security, streamlining access control, and saving time and costs.
Over to you: What's your perspective on the future of secure authentication in the digital realm?
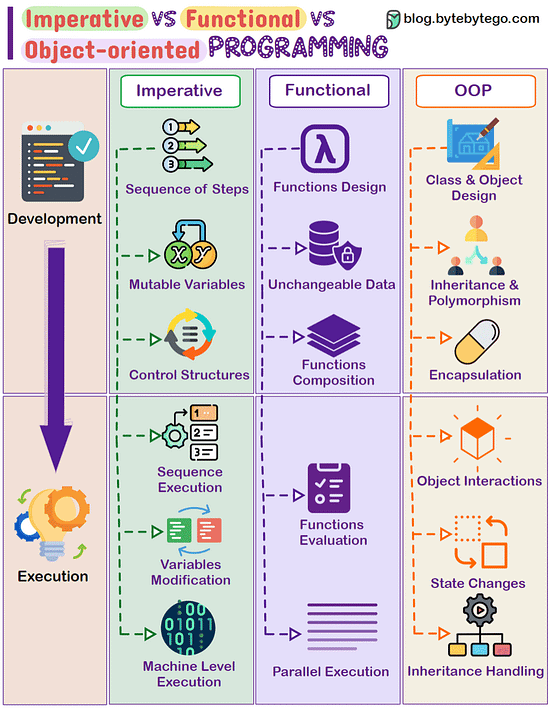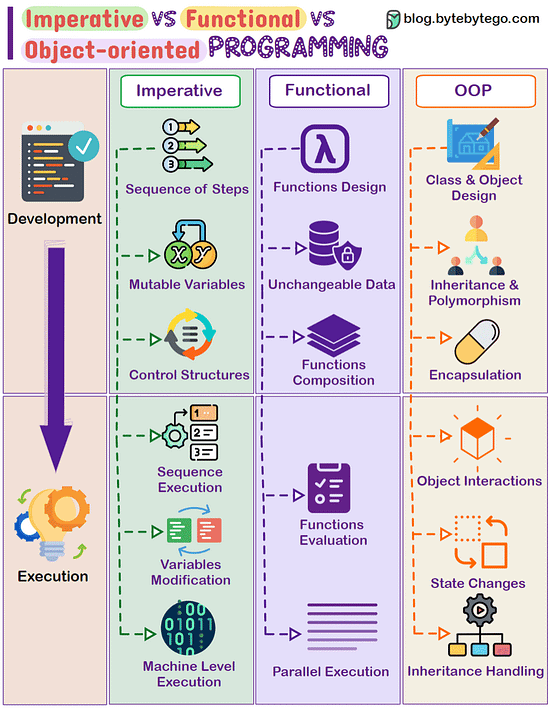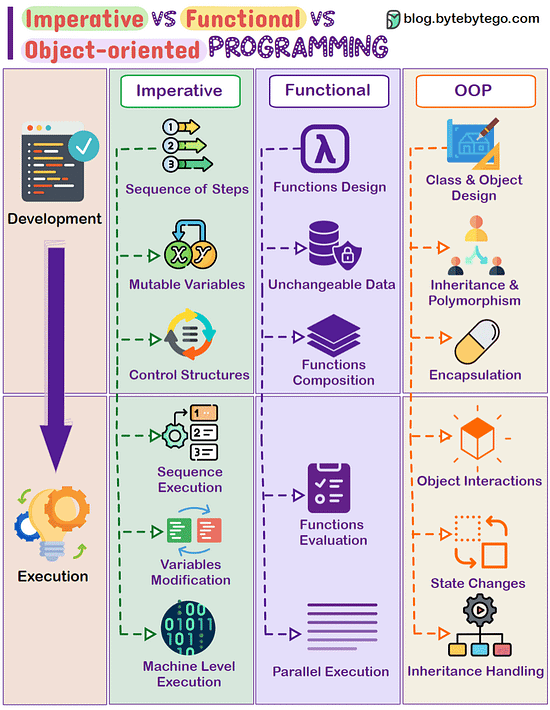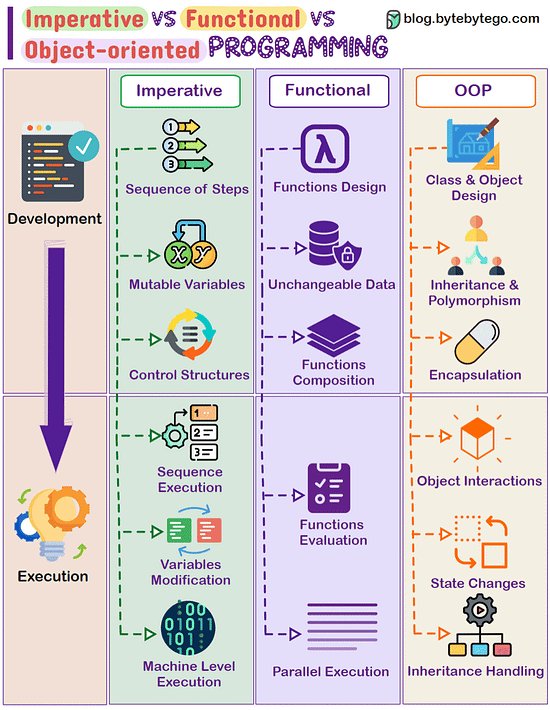
Imperative Vs Functional Vs Object-oriented Programming In software development, different programming paradigms offer unique ways to structure code. Three main paradigms are Imperative, Functional, and Object-oriented programming, each with distinct approaches to problem-solving. Imperative Programming:
- Works by changing program state through a sequence of commands.
- Uses control structures like loops and conditional statements for execution flow.
- Emphasizes on mutable data and explicit steps for task completion.
- Examples: C, Python, and most procedural languages. Functional Programming:
- Relies on pure functions, emphasizing computation without side effects.
- Promotes immutability and the avoidance of mutable state.
- Supports higher-order functions, recursion, and declarative programming.
- Examples: Haskell, Lisp, Scala, and functional features in languages like JavaScript. Object-oriented Programming:
- Focuses on modeling real-world entities as objects, containing data and methods.
- Encourages concepts such as inheritance, encapsulation, and polymorphism.
- Utilizes classes, objects, and interfaces to structure code.
- Examples: Java, C++, Python, and Ruby.
Over to you: Which one resonates with your coding style? Ever had an 'aha' moment while using a particular paradigm? Share your perspective.
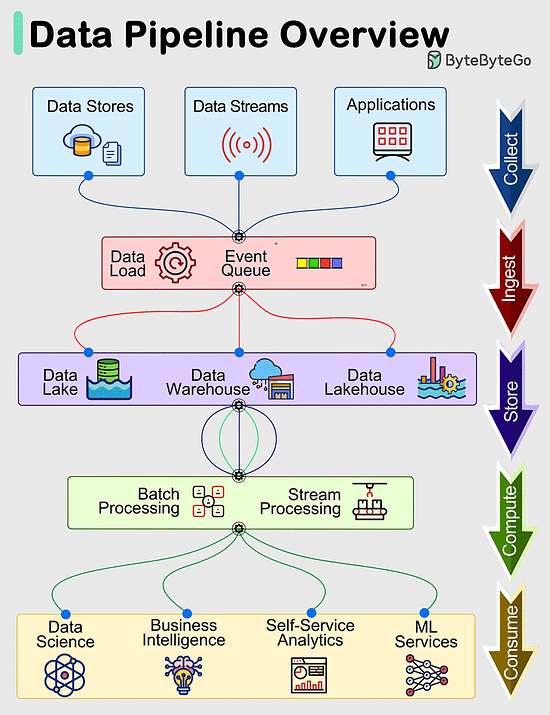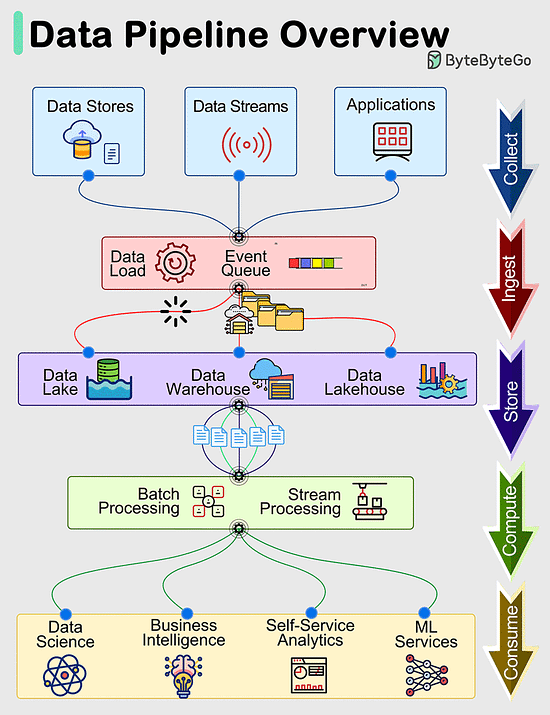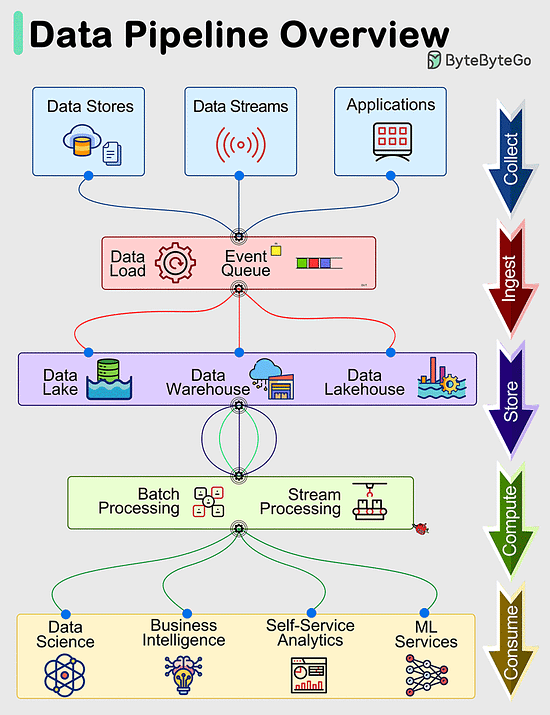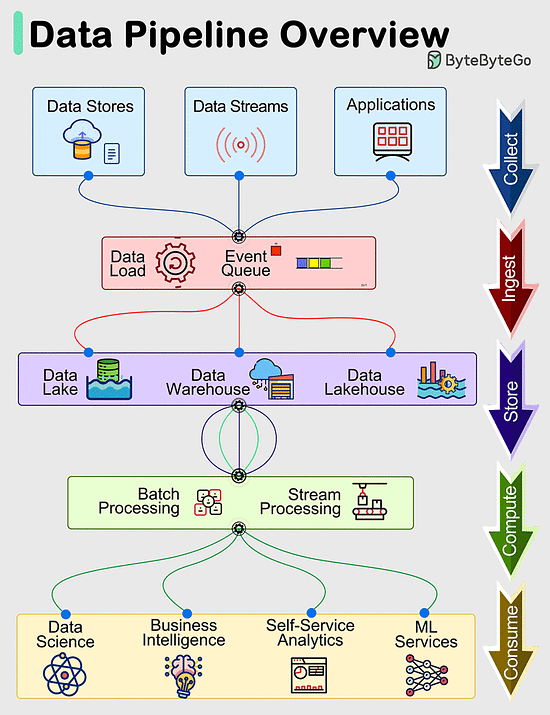
Data Pipelines OverviewData pipelines are a fundamental component of managing and processing data efficiently within modern systems. These pipelines typically encompass 5 predominant phases: Collect, Ingest, Store, Compute, and Consume. Collect:
Data is acquired from data stores, data streams, and applications, sourced remotely from devices, applications, or business systems. Ingest:
During the ingestion process, data is loaded into systems and organized within event queues. Store:
Post ingestion, organized data is stored in data warehouses, data lakes, and data lakehouses, along with various systems like databases, ensuring post-ingestion storage. Compute:
Data undergoes aggregation, cleansing, and manipulation to conform to company standards, including tasks such as format conversion, data compression, and partitioning. This phase employs both batch and stream processing techniques. Consume:
Processed data is made available for consumption through analytics and visualization tools, operational data stores, decision engines, user-facing applications, dashboards, data science, machine learning services, business intelligence, and self-service analytics.
The efficiency and effectiveness of each phase contribute to the overall success of data-driven operations within an organization.
Over to you: What's your story with data-driven pipelines? How have they influenced your data management game? © 2023 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe  
| |