- Mailing Lists
- in
- EP93: Is Passkey Shaping a Passwordless Future?
Archives
- By thread 5365
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 178
Eight priorities for CEOs in 2024
Middle managers don’t always want to be promoted. How should leaders reward them?
EP93: Is Passkey Shaping a Passwordless Future?
EP93: Is Passkey Shaping a Passwordless Future?
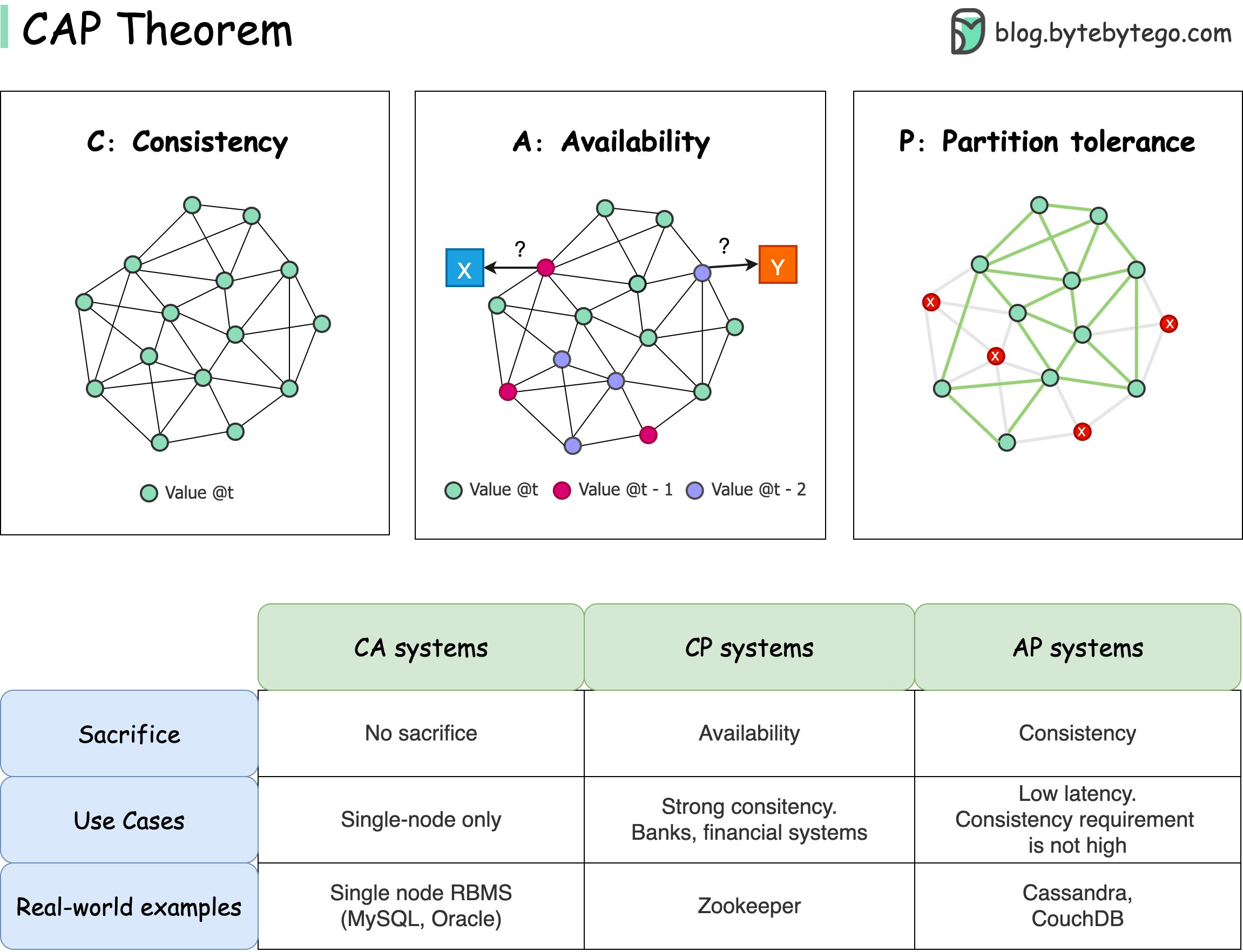
This week’s system design refresher:
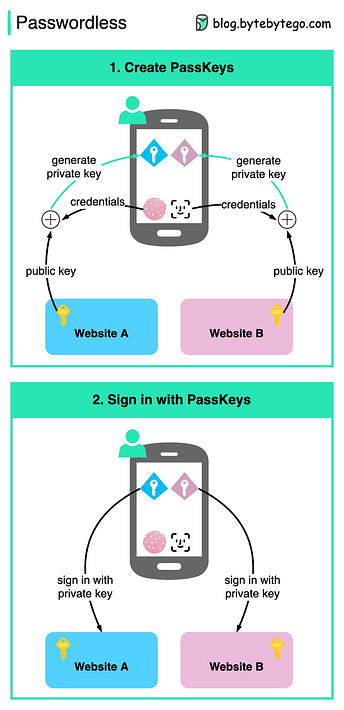
Implement passkey authentication in minutes (Sponsored)Join TikTok, Uber, Amazon, and other leading tech companies by giving your users a faster and more secure sign-in experience with passkeys. Building an in-house auth solution takes months and is a challenge to roll out to users. But there’s a better way. Passage by 1Password is a cross-platform, ready-to-ship auth solution for passkeys. ByteByteGo readers get an exclusive six-month free trial – just use the code ‘BYTEBYTEGO6MO’ once you sign up in the console. Top 9 Most Popular Types of API Testing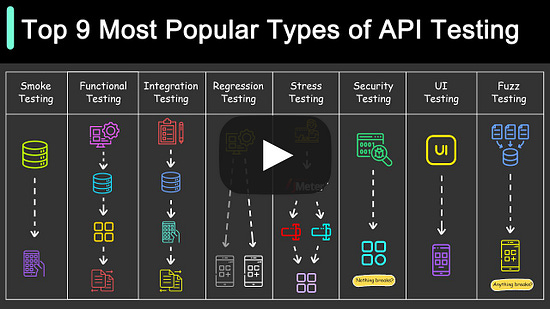 Is Passkey Shaping a Passwordless Future?Google announced PassKey support for both Android and Chrome recently. Passkeys, also backed by Apple and Microsoft, is claimed to be a significantly safer replacement for passwords. The diagram below shows how PassKeys work.
The end-user needs to confirm the account information and present their credentials (face ID, touch ID, etc.). A private key is generated based on the public key provided by the website. The private key is stored on the device.
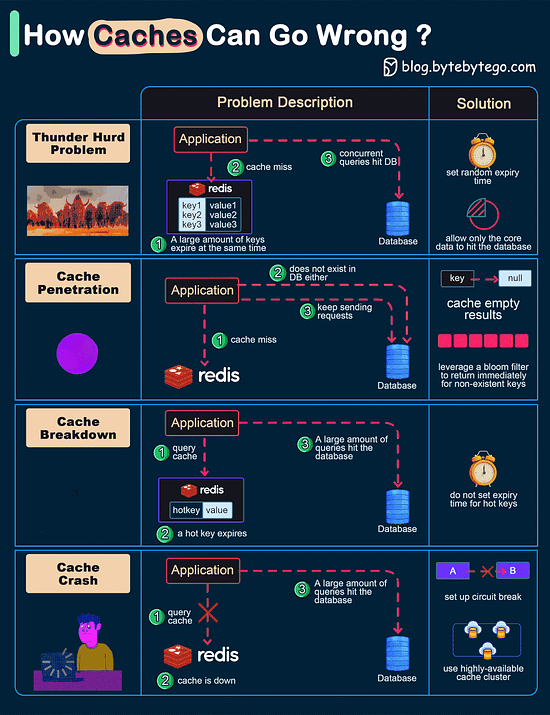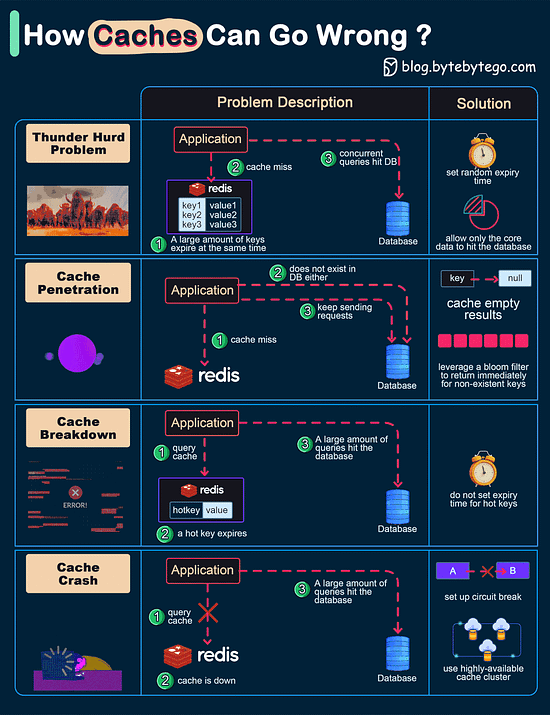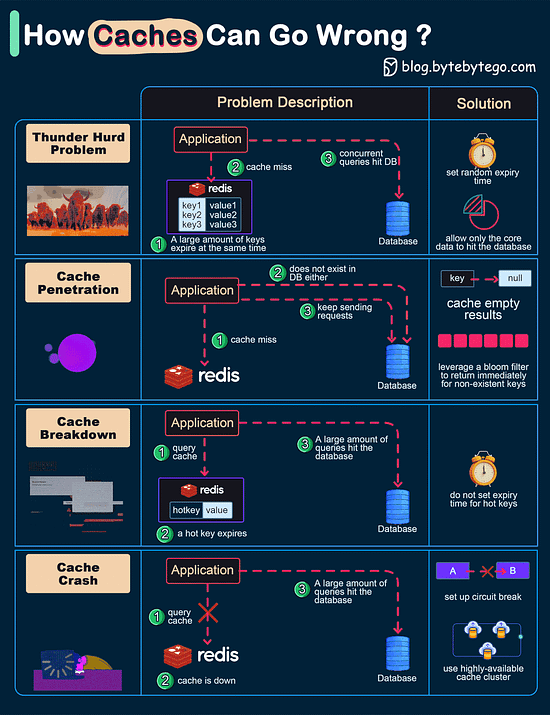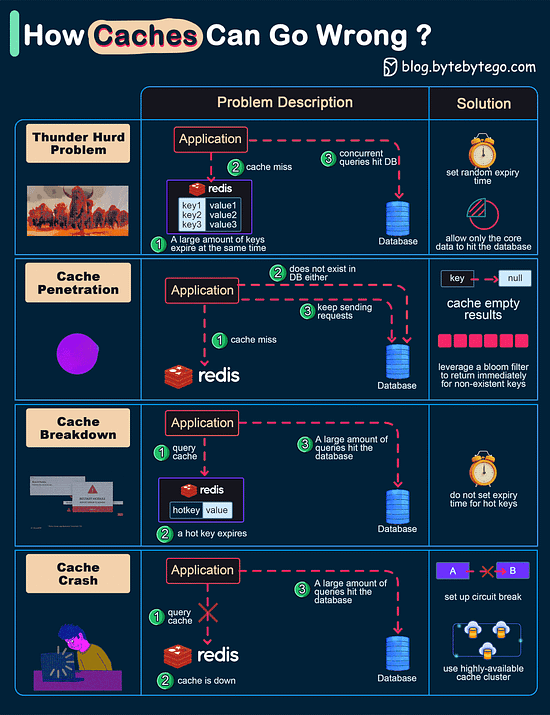
When the user tries to sign in to a website, they use the generated private key. Just select the account information and present the credentials to unlock the private key. Consequently, there is no risk of password leakage since no passwords are stored in the websites' databases. Passkeys are built on industry standards, and it works across different platforms and browsers - including Windows, macOS and iOS, and ChromeOS, with a uniform user experience. How can Cache Systems go wrong?The diagram below shows 4 typical cases where caches can go wrong and their solutions.
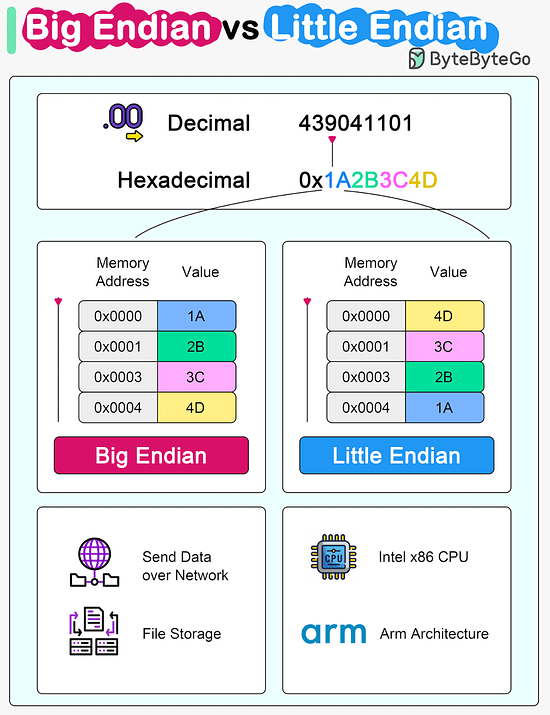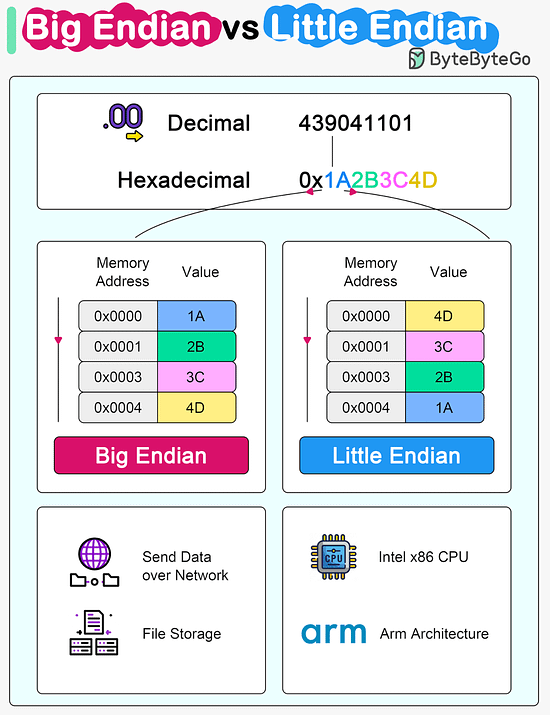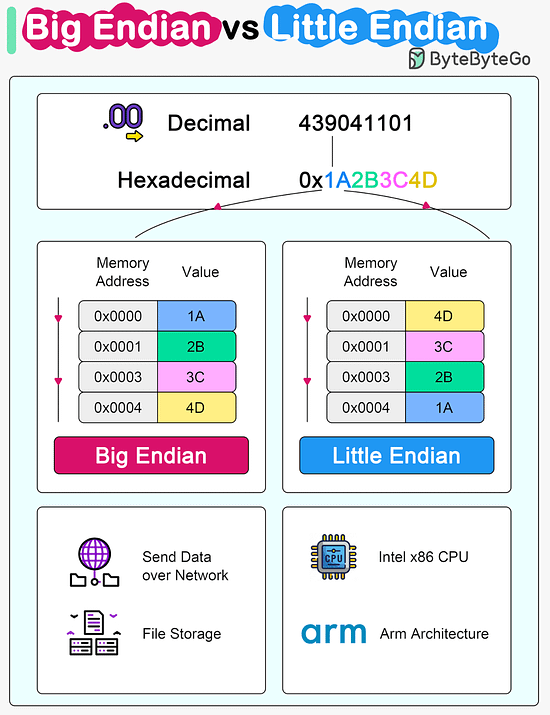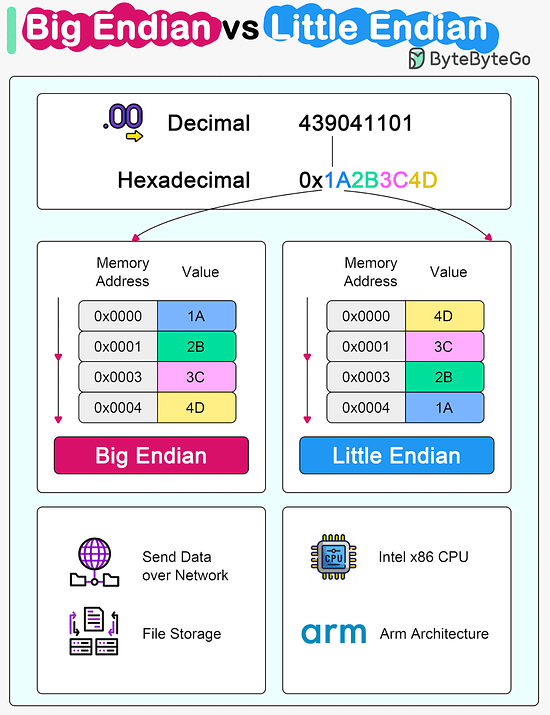
Over to you: Have you met any of these issues in production? Latest articlesIf you’re not a paid subscriber, here’s what you missed this month. To receive all the full articles and support ByteByteGo, consider subscribing: Big Endian vs Little EndianMicroprocessor architectures commonly use two different methods to store the individual bytes in memory. This difference is referred to as “byte ordering” or “endian nature”.
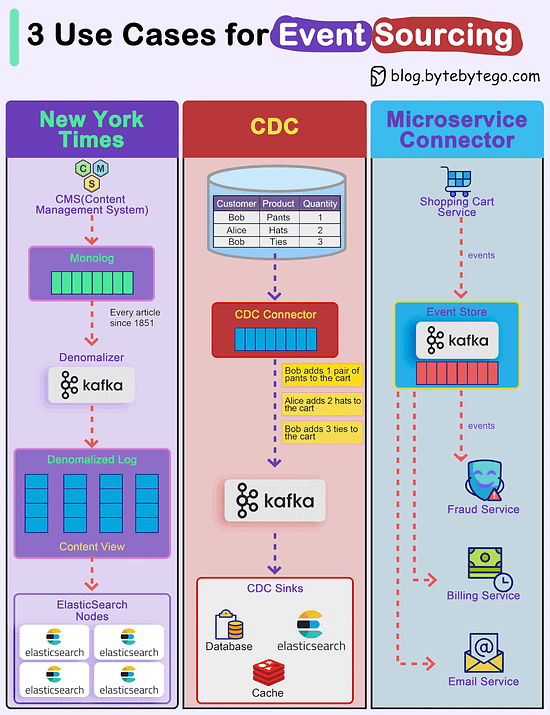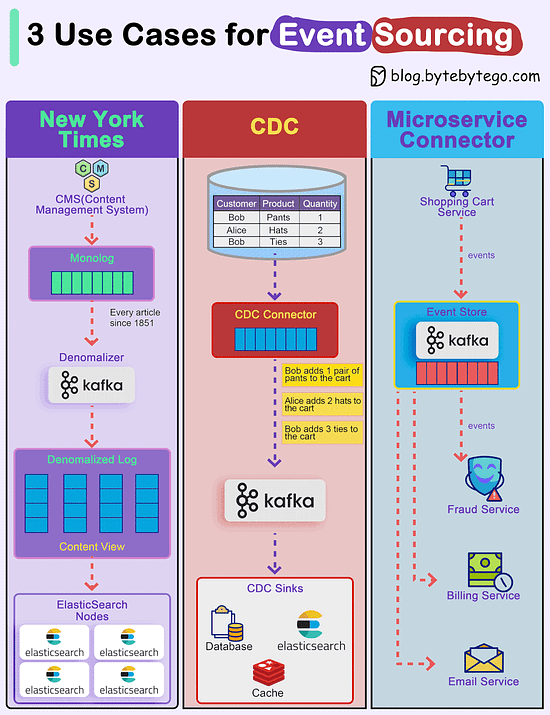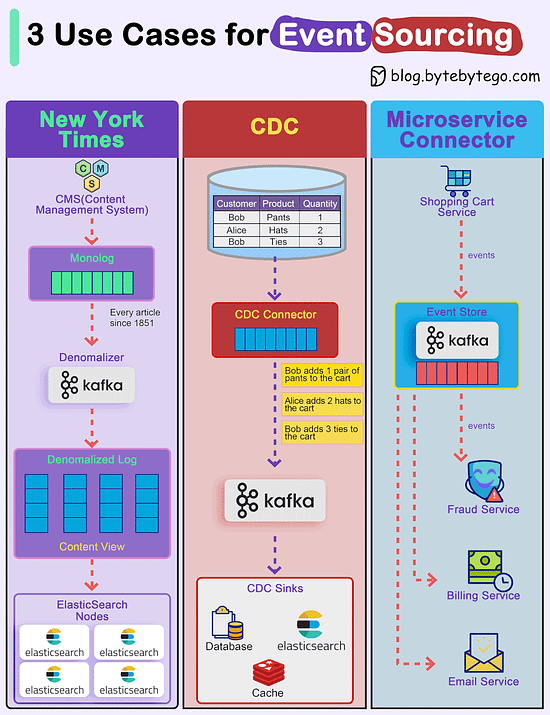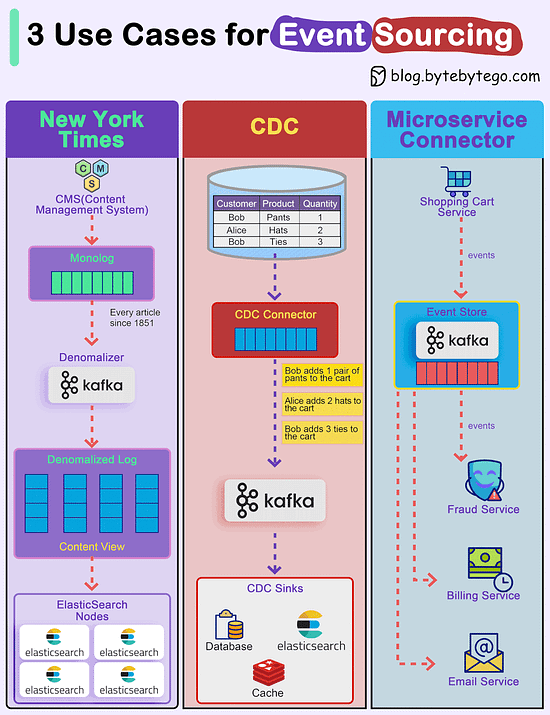
How do we incorporate Event Sourcing into the systems?Event sourcing changes the programming paradigm from persisting states to persisting events. The event store is the source of truth. Let's look at three examples.
Over to you: Have you used event sourcing in production? © 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:37 - 6 Jan 2024