- Mailing Lists
- in
- EP95: Linux File System Explained
Archives
- By thread 5365
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 178
Global trade reconfiguration, talent in 2024, competitiveness and growth in Europe, and more: The Daily Read weekender
You’re a new CEO. Act quickly and think like an outsider.
EP95: Linux File System Explained
EP95: Linux File System Explained
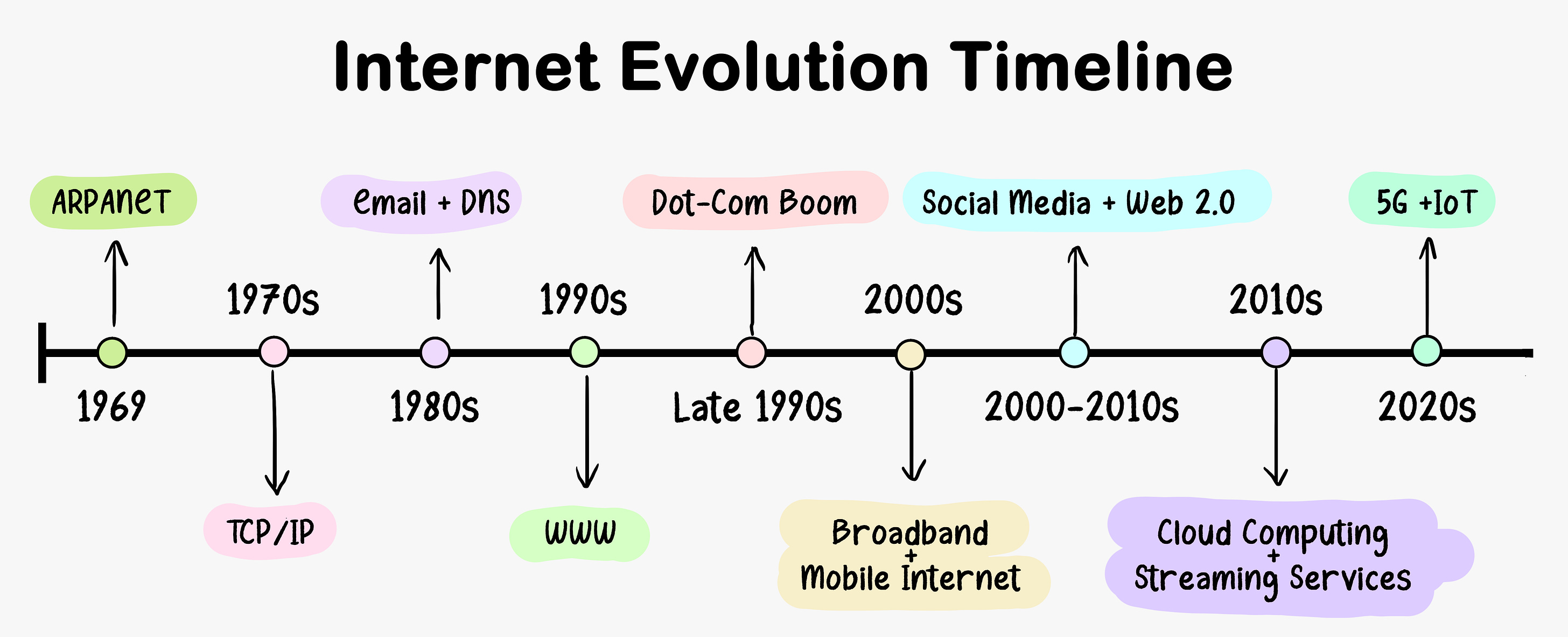
This week’s system design refresher:
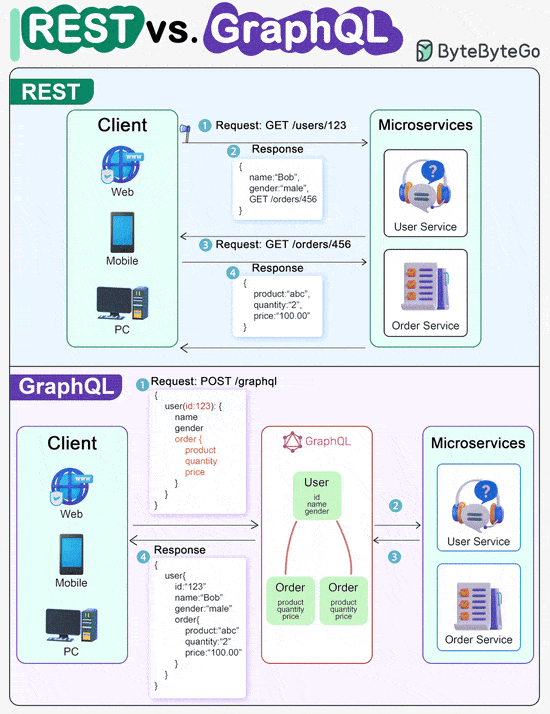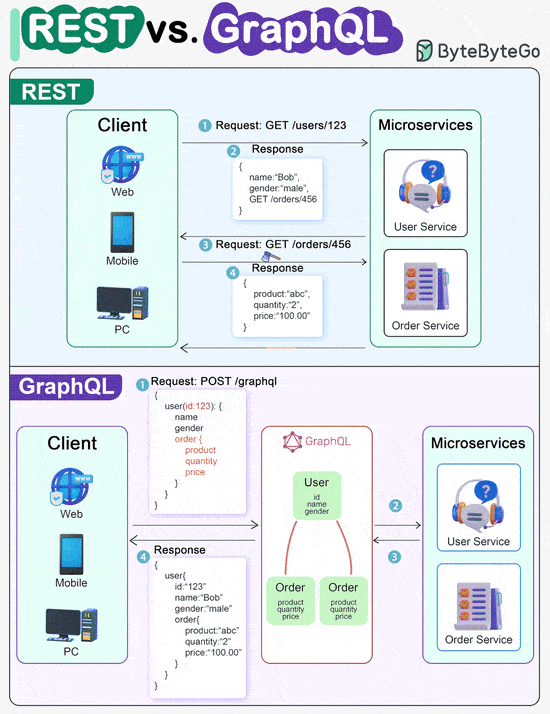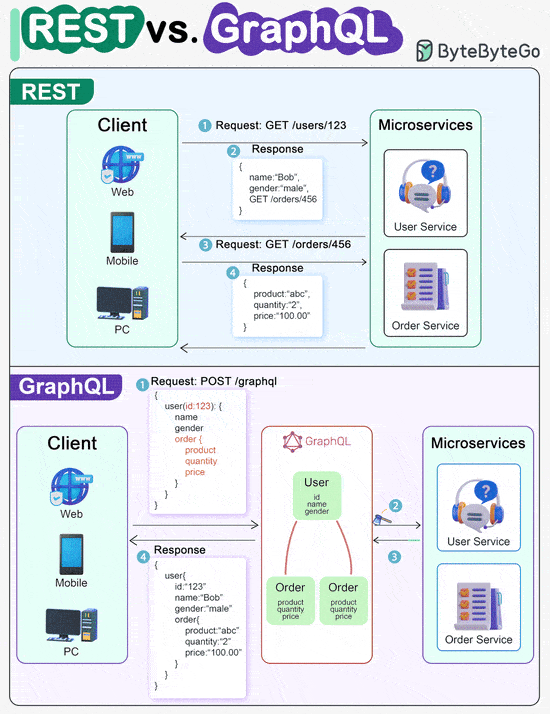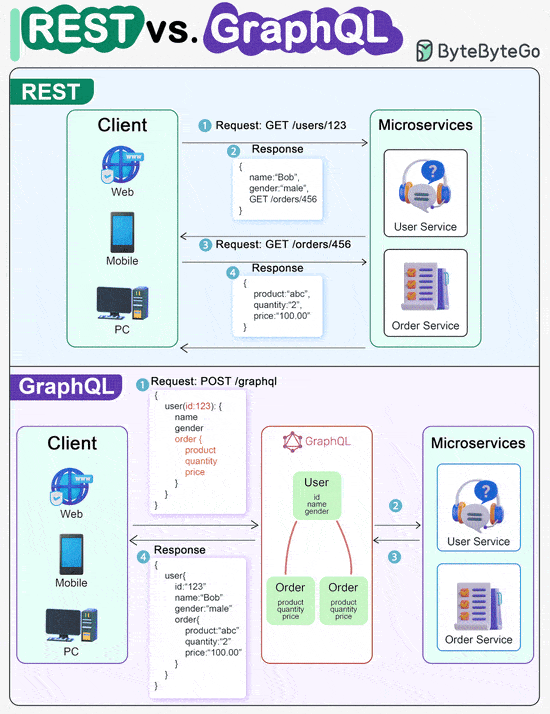
ScyllaDB Summit | Feb 14-15 | Free + Virtual (Sponsored)Join thousands of your peers for an unprecedented opportunity to learn from experts at Discord, Disney, Expedia, Zee, ShareChat, Paramount & more – for free, from anywhere. Discord Keynote: Everything's great until the database is down. Bo Ingram, staff engineer at Discord and author of ScyllaDB in Action, shares lessons from their database outage so that you can learn from their mistakes. Bonus: Register this week to win one of 300 free SWAG PACKS. Linux File System Explained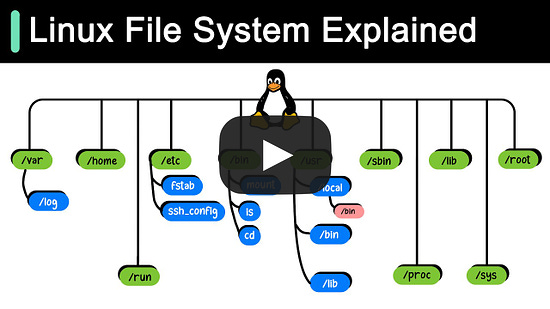 REST API Vs. GraphQLWhen it comes to API design, REST and GraphQL each have their own strengths and weaknesses. REST
GraphQL
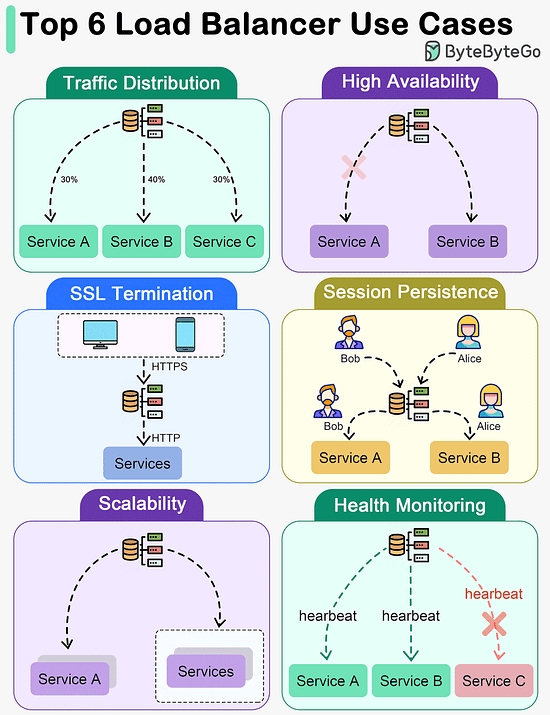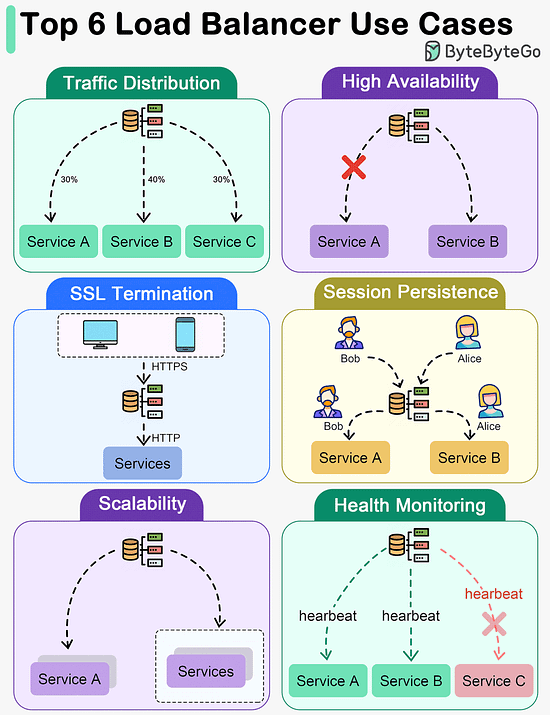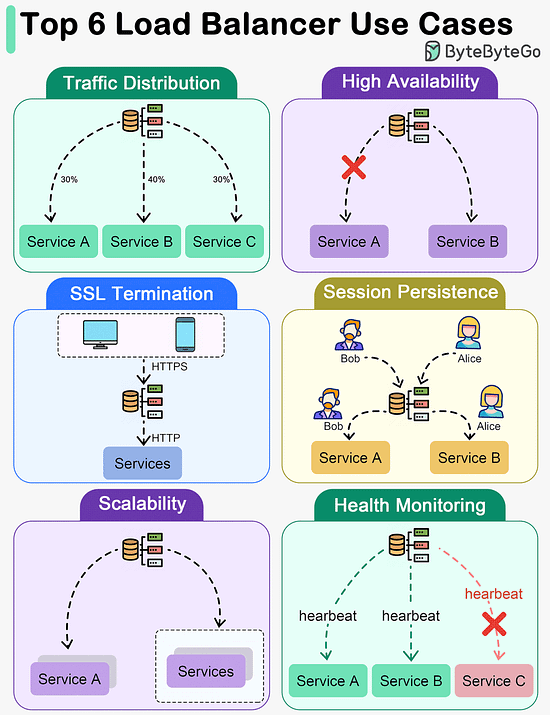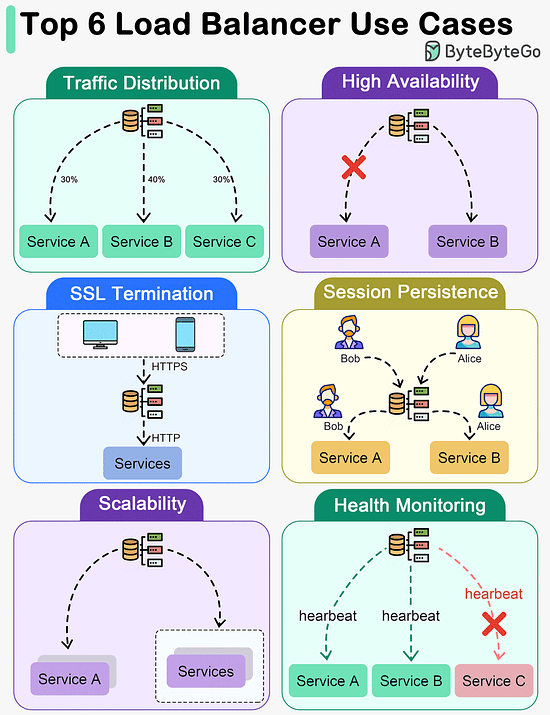
The best choice between REST and GraphQL depends on the specific requirements of the application and development team. GraphQL is a good fit for complex or frequently changing frontend needs, while REST suits applications where simple and consistent contracts are preferred. Key Use Cases for Load BalancersThe diagram below shows top 6 use cases where we use a load balancer.
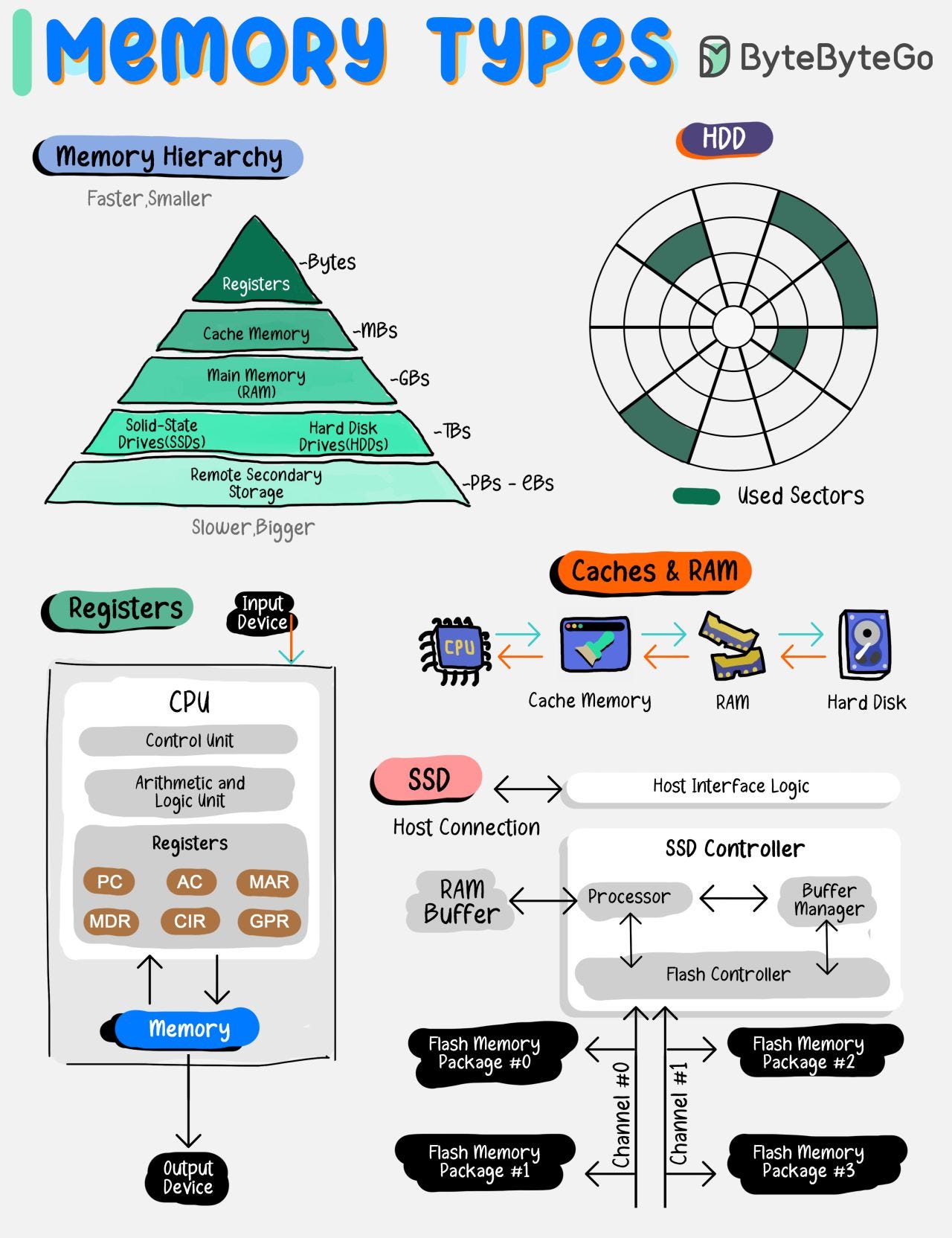
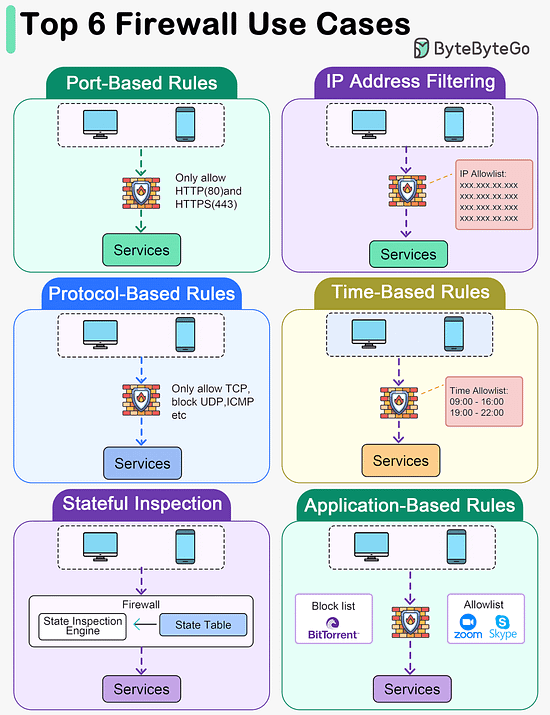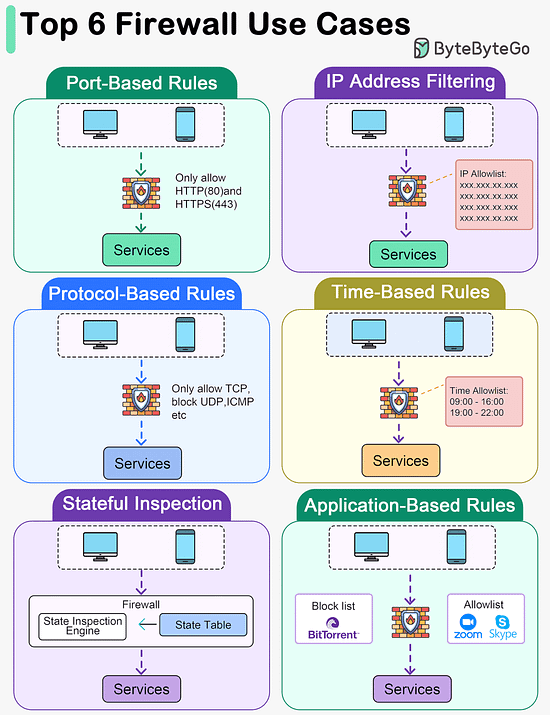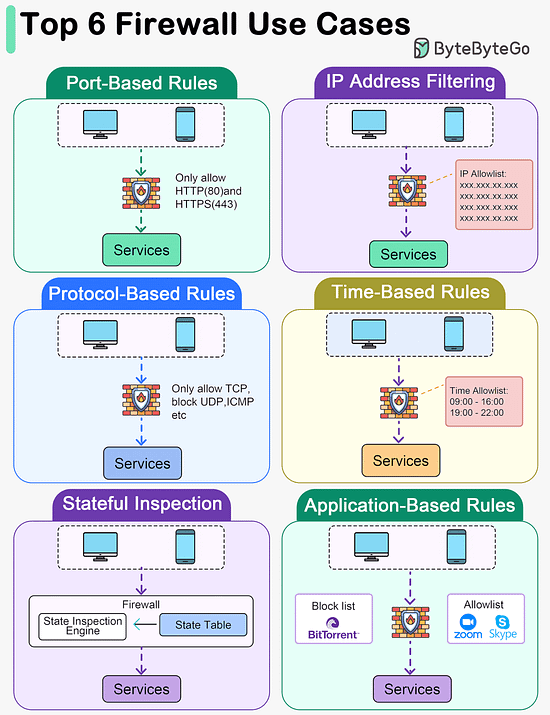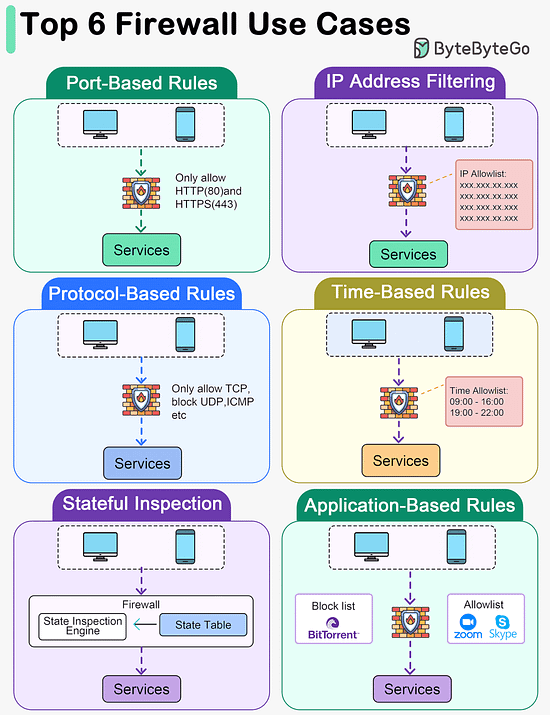
Latest articlesIf you’re not a paid subscriber, here’s what you missed this month. To receive all the full articles and support ByteByteGo, consider subscribing: Types of memory. Which ones do you know?Memory types vary by speed, size, and function, creating a multi-layered architecture that balances cost with the need for rapid data access. By grasping the roles and capabilities of each memory type, developers and system architects can design systems that effectively leverage the strengths of each storage layer, leading to improved overall system performance and user experience. Top 6 Firewall Use Cases
SPONSOR USGet your product in front of more than 500,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com © 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:36 - 20 Jan 2024