- Mailing Lists
- in
- Mastering Modern Authentication: Cookies, Sessions, JWT, and PASETO
Archives
- By thread 5358
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 171
Dive into the data: The State of Observability in Europe report
How do you foster meaningful connections with stakeholders?
Mastering Modern Authentication: Cookies, Sessions, JWT, and PASETO
Mastering Modern Authentication: Cookies, Sessions, JWT, and PASETO
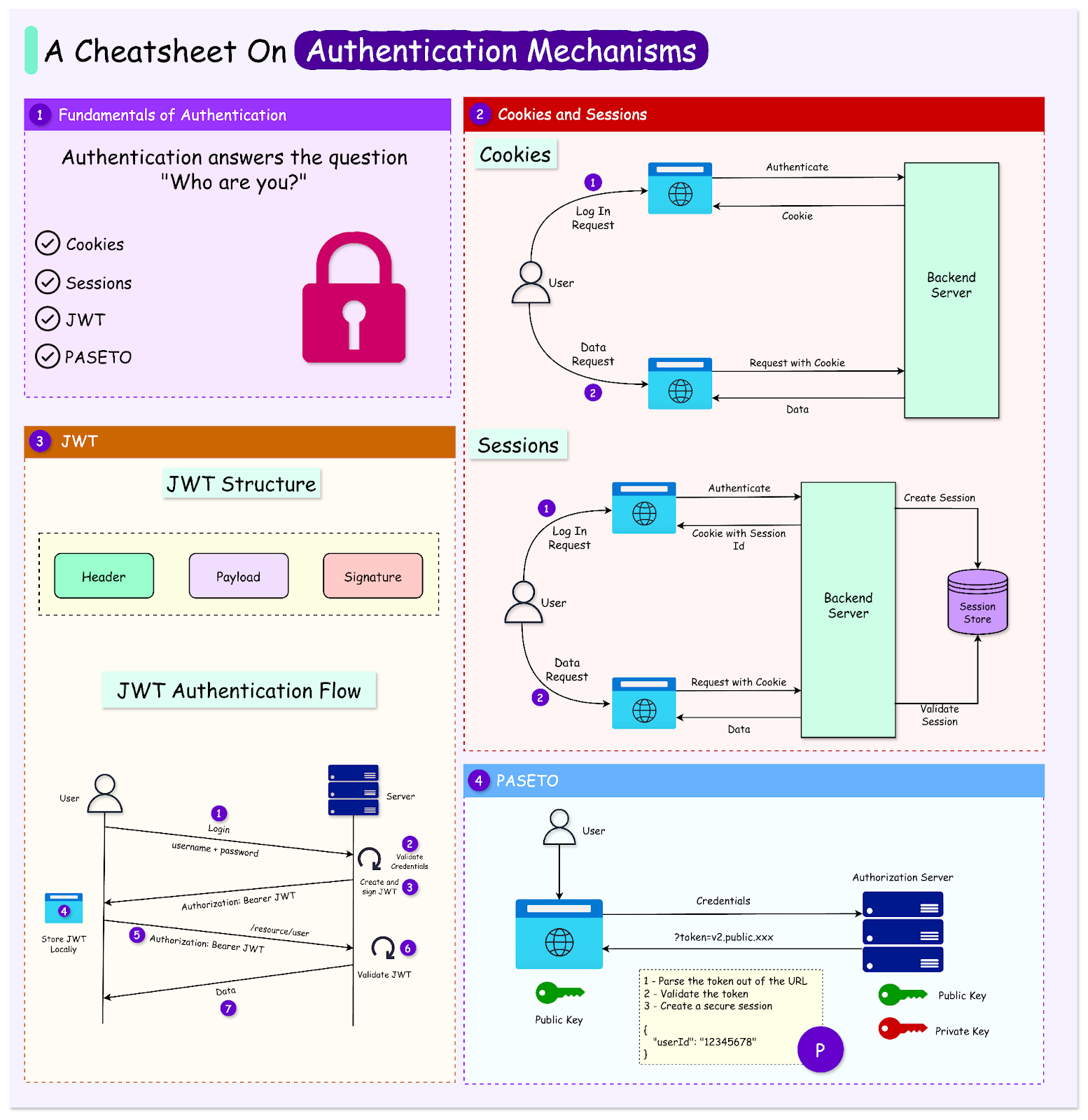
Authentication serves as the first line of defense in ensuring the security of applications and the sensitive data they handle. Whether it’s a personal banking app, a corporate platform, or an e-commerce website, effective authentication mechanisms are needed to verify the identity of users and safeguard their access to resources. Authentication ensures that only authorized users gain access to specific data or actions within an application. Without proper authentication, applications are vulnerable to unauthorized access, data breaches, and malicious attacks, potentially resulting in significant financial loss, reputational damage, and privacy violations. In addition to security, authentication plays a critical role in the user experience. By effectively identifying users, applications can provide personalized services, remember user preferences, and enable functionalities like Single Sign-On (SSO) across platforms. With evolving threats, implementing secure and efficient authentication is more challenging than ever. Developers must navigate between competing priorities such as:
To tackle these challenges, developers rely on various authentication mechanisms. In this post, we’ll explore multiple authentication mechanisms used in modern applications and also study their advantages and disadvantages. Fundamentals of Authentication... Continue reading this post for free in the Substack app© 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:37 - 5 Dec 2024