Archives
- By thread 5360
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 173
-
There’s a whole new way for advertisers to reach consumers
Re:think
Advertising will never be the same FRESH TAKES ON BIG IDEAS
ON THE FUTURE OF ADVERTISING
The sea changes that are upending advertisingMarc Brodherson
Advertising is an amazing industry. It’s worth about a trillion dollars globally, grows above GDP, and is either the primary business model or one of the fastest-growing ones for at least five of the top ten companies by global market cap. Advertising matters to traditional media companies and tech giants, big brands and small businesses, agencies and other ad services and tech providers, and now even to nonmedia consumer companies that are starting advertising businesses.
There’s been a sea change, which is now accelerating, in traditional brand advertising as consumers spend their time differently and tech giants compete with traditional TV advertising. Younger audiences are spending more time watching short-form mobile videos—versus traditional TV content—and playing video games that are normally less amenable to advertising. Combined with the rise of ad-free streaming, these trends make it harder than ever to reach audiences who can pay to avoid ads, and they raise socioeconomic questions about who has to see them.
Another growing trend is large tech platforms launching ad-supported tiers for their streaming products and moving into the most valuable ad category of all: live sports. At minimum, this will make the market even more competitive for legacy TV and further collapse the boundaries between brand and performance marketing as well as digital and TV marketing.
But the biggest trend right now is the rise of e-commerce companies building advertising businesses by selling access to their consumers. We call this retail media or commerce media. This is a new way for advertisers to reach consumers. Right now, retail brands with consumer data can reach customers at the moment they express interest in a product. They sell sponsored listings, which then pop up to consumers as suggested products. In some cases, these lines of business are worth tens of billions of dollars, with margins that can exceed 20 times traditional retail margins. The investor community is starting to recognize commerce media as a material part of company valuations, though retailers are primarily known for selling consumer goods rather than ads.
Retail media is expanding to players like rideshare and delivery companies, which know users’ locations and can put relevant ads in the apps at the right time. Hotel chains are doing it, credit card companies and banks are looking at it, and airlines have the potential to get into it—they have screens on planes and in apps, and physical media such as billboards and in-flight magazines in the terminal, on the jet bridge, or on the plane.“By 2028, we believe that spending in retail and commerce media will be bigger than for all of global television and streaming advertising.”
ABOUT THIS AUTHOR
Marc Brodherson is a senior partner in McKinsey’s New York office.
MORE FROM THIS AUTHOR
UP NEXT
Anna Pione on wellness
After the COVID-19 pandemic moved into its endemic phase, investors and consumer executives wondered whether the wellness industry—which grew exponentially during the pandemic—would have staying power. The upshot: consumer interest in the space has never been higher.
This email contains information about McKinsey’s research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to our McKinsey Quarterly alert list.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Quarterly" <publishing@email.mckinsey.com> - 02:14 - 7 Feb 2024 -
Panama Canal restrictions are expected to shake up global supply chains
On Point
Our analysis of the slowdown Brought to you by Liz Hilton Segel, chief client officer and managing partner, global industry practices, & Homayoun Hatami, managing partner, global client capabilities
•
More time at sea. The slowdown at the Panama Canal will likely shake up regular shipping routes. A ship traveling from Asia to the Caribbean that would typically cross east through the Panama Canal (taking about 26 days) could instead go west around the Cape of Good Hope (taking about 39 days), McKinsey senior partner John Murnane and coauthors explain. A ship going from the west coast of South America to the Caribbean that would typically use the Panama Canal (taking about six days) could instead cross through the Strait of Magellan, completing what is essentially a full loop around South America (taking about 31 days).
— Edited by Jana Zabkova, senior editor, New York
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this newsletter because you subscribed to the Only McKinsey newsletter, formerly called On Point.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey" <publishing@email.mckinsey.com> - 01:08 - 7 Feb 2024 -
A Crash Course in P2P
A Crash Course in P2P
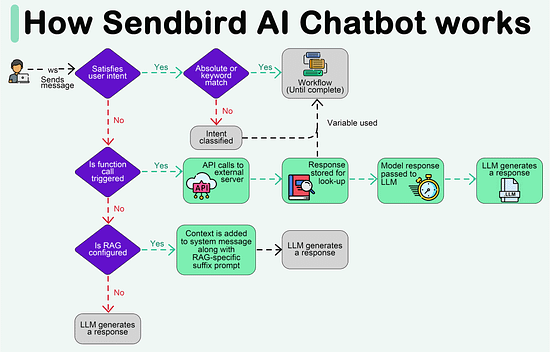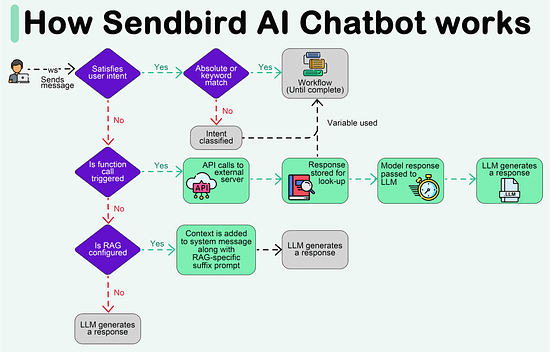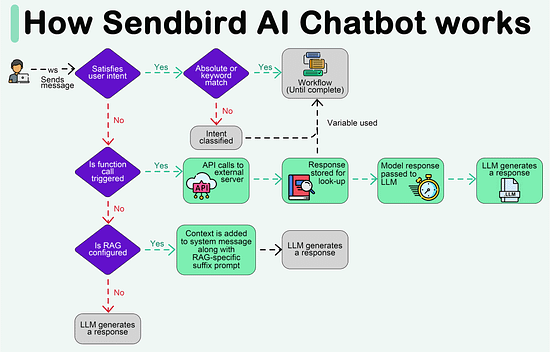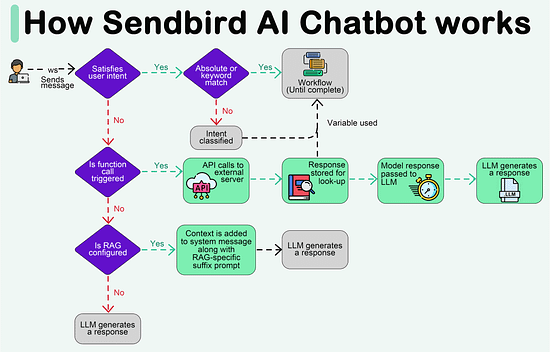
Create your free AI chatbot (Sponsored) Meet Sendbird SmartAssistant, a customizable chatbot powered by OpenAI’s GPT engine. The only chatbot that can be presented in your brand, trained with your own content, and deployed via low-to-no code. In this interactive Demo you will see how Sendbird offers: Forwarded this email? Subscribe here for moreCreate your free AI chatbot (Sponsored)
Meet Sendbird SmartAssistant, a customizable chatbot powered by OpenAI’s GPT engine. The only chatbot that can be presented in your brand, trained with your own content, and deployed via low-to-no code. In this interactive Demo you will see how Sendbird offers:
LLM flexibility, with integrations into ChatGPT, PaLM2, LLaMa2, Sagemaker
Security & privacy, with support for private or open-sourced models
Fast customization, with chat UI components for quick deployment
Scalability, with existing infrastructure supporting 7 Billion+ messages every month
Try SmartAssistant, part of Sendbird's AI-embedded communications platform across chat, messaging, voice, and video APIs, to enable faster, deeper engagement with your customers.
A Crash Course in P2P
In this issue, we are diving deep into the world of P2P (peer-to-peer) networks. It's all about computers talking directly to each other. We will take you on a cool journey, checking out how P2P networks evolved, the different P2P models, and the nitty-gritty details of how they work. We will talk about the challenges faced by P2P networks and a sneak peek into the future where blockchain and DeFi make things even more interesting.
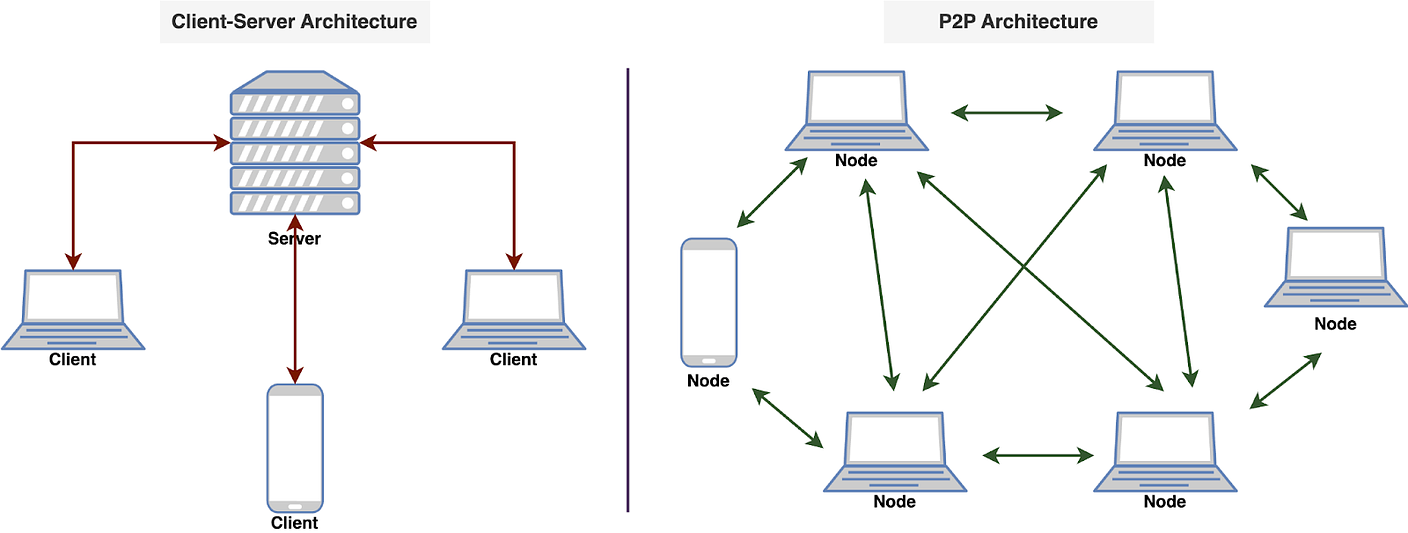
A P2P network is a type of network in which different computers communicate with each other directly without the need for a central server. The peer in the term indicates that all participating computers/systems are equal. These computers are also called nodes.
In a traditional network architecture (known as the client-server architecture), there is usually one server and multiple clients. If two clients want to communicate with each other, the message has to first reach the server and then the server sends the message to the second client.
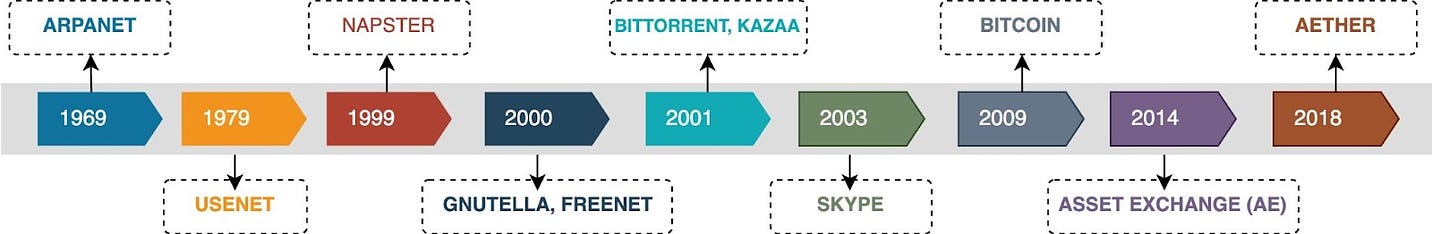
History of P2P networks
We start our discussion of P2P with the history of such networks, as it is not a recent concept. The evolution of P2P networks is a fascinating journey spanning several decades, marked by groundbreaking developments and innovations. Here is a timeline of key P2P applications and transformative moments in the history of P2P.
Types of P2P models
We would like to discuss how the P2P networks operate, but before we do that, it is important to understand the different ways in which peer-to-peer networks can be structured or categorized based on their functionalities. So, here are some common types of P2P models.
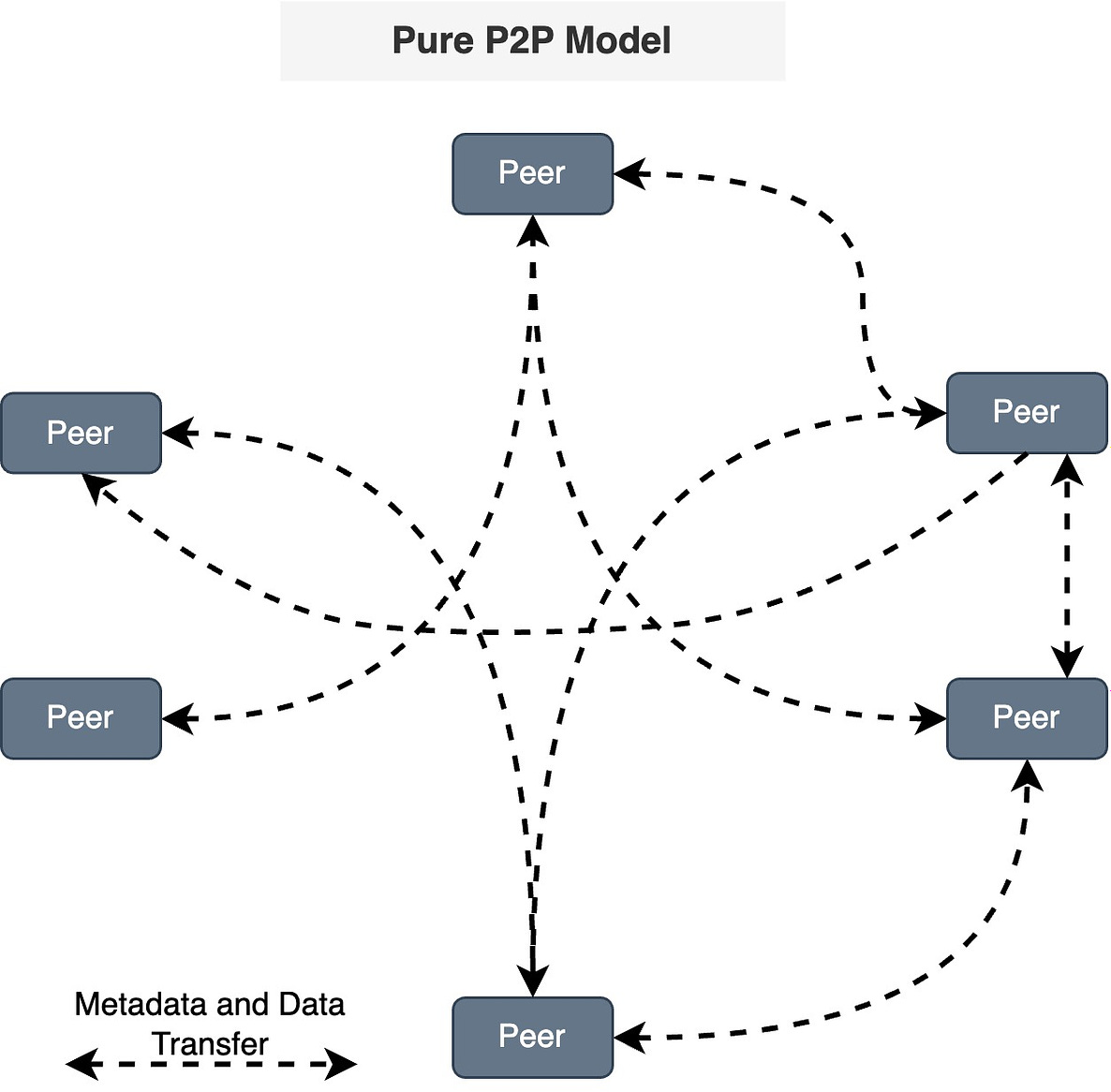
Pure P2P model
In this model, there is no central server or authority, and each node can act both as a client and a server.
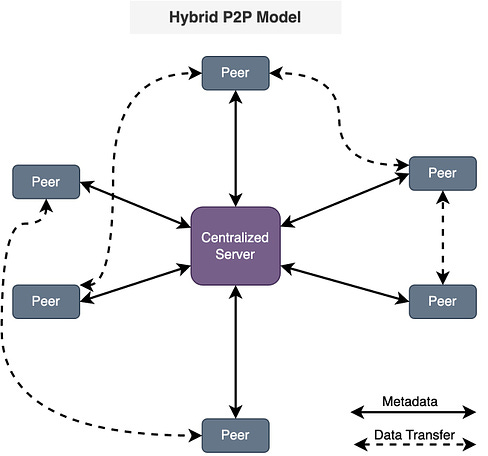
Hybrid P2P model
This model makes use of centralized servers for facilitating initial connection and peer discovery. Further communication between peers is carried out in a decentralized manner. This approach balances the benefits of a decentralized network with the efficiency of centralized coordination.
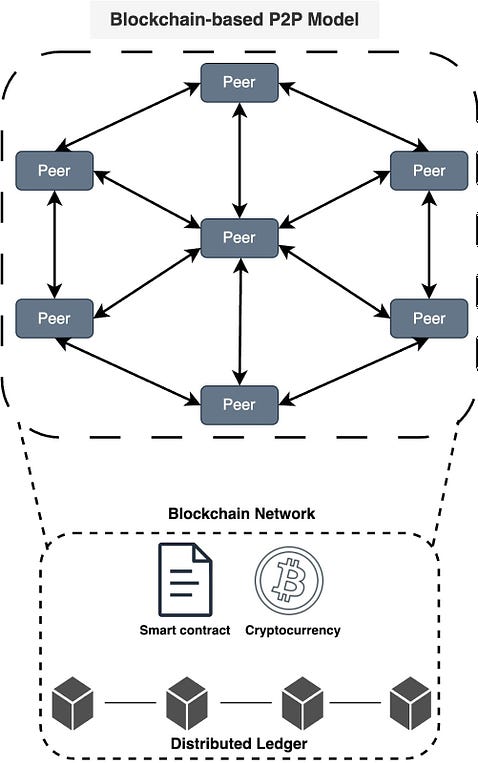
Blockchain-based P2P model
A blockchain-based Peer-to-Peer model refers to a decentralized network architecture where the principles of P2P interaction are combined with blockchain technology. In this model, blockchain serves as the underlying distributed ledger or database that records and verifies transactions, creating a secure and transparent environment for peer-to-peer interactions. This model is often associated with decentralized applications (DApps) and platforms that leverage the capabilities of blockchain for various purposes.
Latest articles
If you’re not a paid subscriber, here’s what you missed this month.
To receive all the full articles and support ByteByteGo, consider subscribing:
How the P2P network operates
Now, we are all set to discuss how a typical P2P network operates. As discussed earlier, the P2P network is an example of a decentralized architecture where each node has equal status and is capable of both requesting and providing resources or services. P2P networks can be used for various applications, including file sharing, communication, distributed computing, and more.
Here is a general overview of how a P2P network operates.
Node Initialization
When a new node in a P2P network boots up, it doesn’t know anything about the network, because there is no central server. Usually, developers provide a list of trusted nodes written directly into the code of the P2P client application that can be used for initial peer discovery. These trusted nodes could be centralized servers or peers depending upon the P2P application.
A node is usually identified by the following node triple: IP address, Port number, and node ID. The node ID should be unique with no collisions between peers. There are several methods to achieve this:
Node ID is a random number generated once the P2P client is installed.
Node id is a hash of the computer’s network card MAC address and hard disk serial number
Take the example of Bitcoin, when a Bitcoin client starts, it checks its database for a list of reliable peers, if no such list is found it will use the default list hard coded into the software by the developers. Once the client has found a peer it will periodically look for new peers. The hard-coded list is just a bootstrap, once the client has a few nodes connected it doesn't need the original list anymore. The Bitcoin P2P system is designed to be very fault-tolerant and decentralized.
Discovery and Connection
After the node initialization, it needs a way to discover and connect with other nodes in the network. There are different methods for peer discovery in a P2P network. Some of the methods are discussed below.
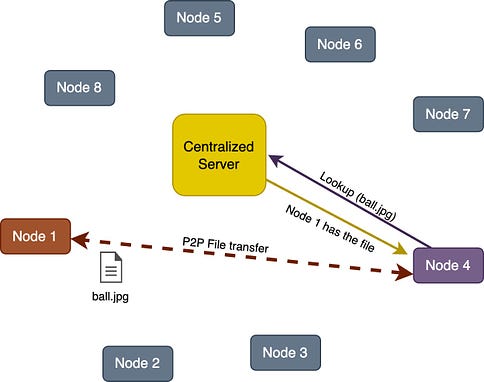
Centralized Server / Tracker Server: In this method, there is a central server that has information about all nodes in the network. When a new node wants to join the P2P network, it first contacts the central server which provides the new node the information about other peers. The new node can then communicate directly with other nodes. This method may seem like client-server architecture. However, the server is only used for peer discovery and not for actual communication since after peer discovery, the communication among peers occurs directly.
The central server is also called a tracker in some P2P applications that maintains a list of active peers in the network. All existing peers periodically communicate with the tracker to confirm their availability and get a fresh list of all available peers. The hybrid P2P model utilizes this approach.
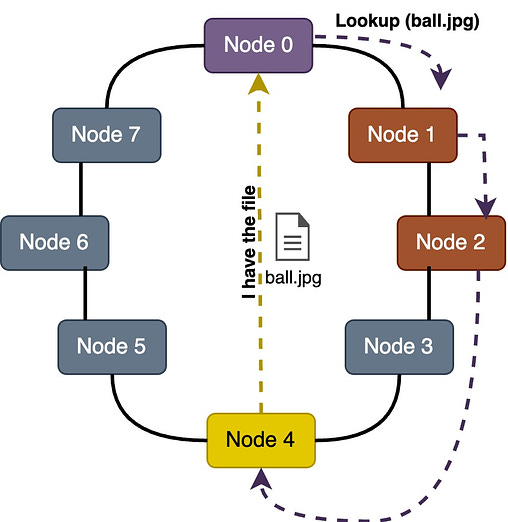
Distributed Hash Tables (DHTs): It is a decentralized method for peer discovery commonly used in P2P networks. Nodes are assigned a unique identifier, and a distributed hash table is used to map these identifiers to IP addresses. When a node wants to discover another peer, it can perform a lookup in the DHT to find the corresponding IP address. The pure P2P model utilizes this approach.
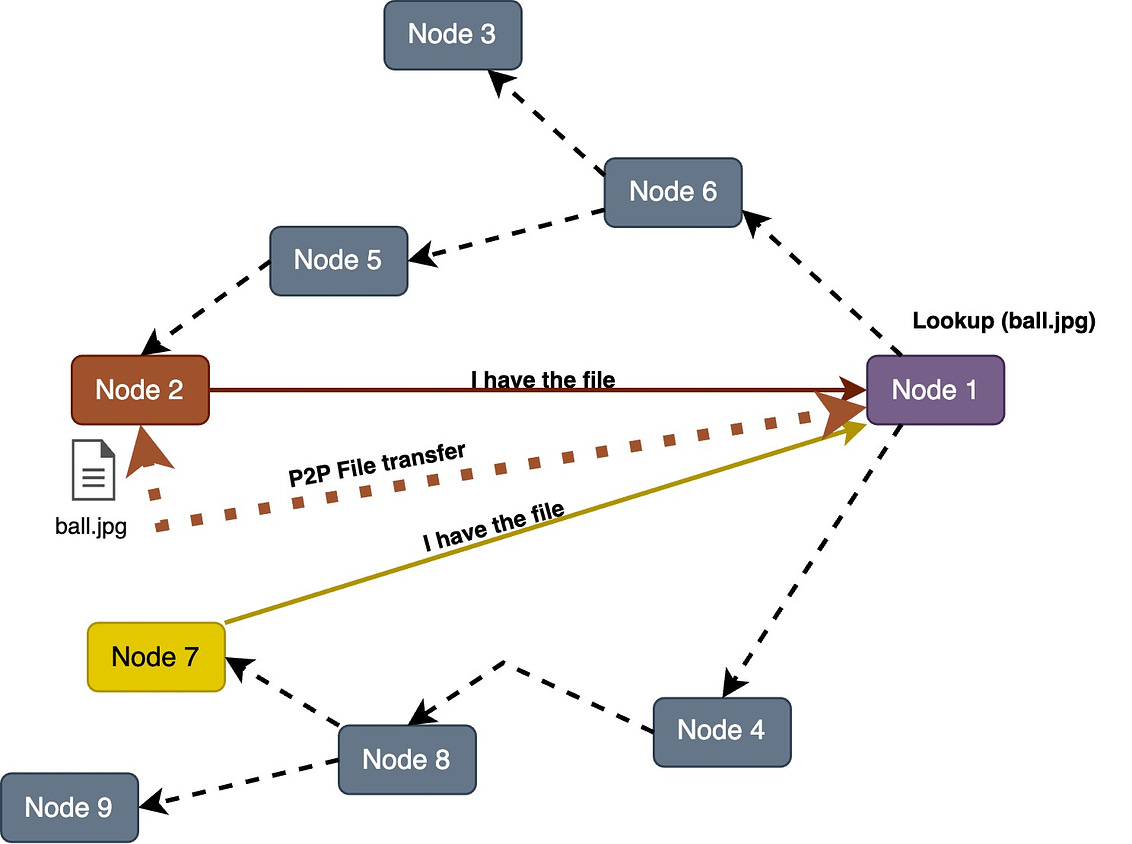
Broadcasting and Multicasting: Nodes may broadcast their presence or send multicast messages to the network. Other nodes can listen to these broadcasts or messages to discover peers. This method is more common in smaller, local P2P networks.
For example, when a node sends a broadcast file request to the network, all peers who can provide the file send the message to the requester node. The node then chooses the specific peer to get the file from.
Distributed Data Storage
Peers in a P2P network share resources directly with each other. Resources can include files, computational power, or other services. So, the question is, how these resources are being stored in a P2P network? We can understand this with the help of an example. In a file-sharing P2P network, each peer contributes a portion of its storage to host parts of files. This results in a distributed storage system where the complete file is reconstructed by combining contributions from multiple peers in the network.
Routing and Lookup
Every node maintains a lookup table (also called a routing table) where it stores the node information (IP, Port, and ID) of the closest peers it knows of. The implementation for lookup tables varies based on the topology, but all share a common principle - they enable nodes to identify the peer closest to any given node ID. If the peer has the data it will route it back to the query originator, if not, it will route the query to the closest node it has on its lookup table, this process continues recursively until the node that has the data is found.
Depending on the P2P protocol, there exist different metrics to define the distance between the node ID of two peers. For example, the very popular peer-to-peer protocol Kademlia uses the XOR-metric.
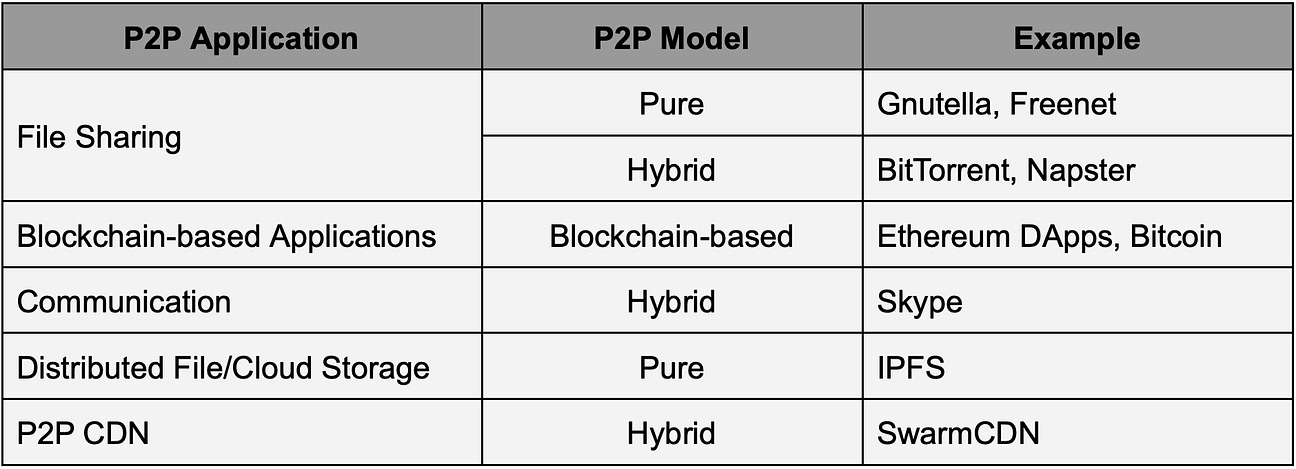
Real-life applications of P2P network
P2P networks have some cool real-life applications. Here are some common P2P applications along with the respective models they often fall into:
Advantages of P2P network
Decentralization
P2P networks are designed to operate in a decentralized manner, meaning there is no central server or authority controlling the network.
Redundancy and reliability
The data is not placed in just one peer’s storage. Multiple peers have a copy of the same data which prevents a single point of failure - unlike the traditional client-server architecture where the central server has the data and can be lost if the server fails. Since data is distributed across multiple nodes, P2P networks are inherently redundant. If one node fails or leaves the network, the data can still be retrieved from other nodes, enhancing reliability.
Scalability
A P2P network is more scalable than a traditional client-server architecture. In a traditional client-server architecture, a single server has to handle all requests. If there are too many client requests, the server may not be able to handle all of the requests. However, in the case of P2P, each request is not necessarily handled by a single node, thus providing scalability.
Distributed computing
P2P networks can be used for distributed computing tasks where processing is distributed among multiple nodes. This is beneficial for tasks that require significant computational power.
File Sharing and content distribution
P2P networks, especially those using protocols like BitTorrent, excel in distributing large files efficiently. Users can download and upload simultaneously, reducing the load on individual servers.
Privacy and anonymity
In P2P systems, users may enjoy increased privacy and anonymity as they communicate directly with peers without relying on a central server. This can be advantageous in applications where privacy is a concern.
Challenges in P2P network
Let’s now discuss, some of the challenges in P2P networks.
Security concerns
P2P networks can be more vulnerable to security threats, including unauthorized access, malware distribution, etc.
Dependency on peer availability
The availability of data in a P2P network depends on the willingness and availability of peers to share that data. If certain nodes leave the network or become unresponsive, it can affect the availability of resources.
Legal and copyright issues
P2P networks are known to share and spread copyrighted material. Sharing copyrighted material can lead users to legal issues.
For example, Metallica (a music band) filed a lawsuit against Napster in 2000. Napster was shut down in 2001. In another incident, the alleged owner of one of the biggest torrent sites, i.e., kickasstorrents, was arrested by the US authorities from Poland back in 2016. Similarly, another famous torrent site for movies YIFY Torrents or YTS also went down in 2015 after facing a lawsuit from Motion Picture Association of America.
Regulatory frameworks for P2P networks
P2P networks are playing a significant role in shaping the Internet's future. Nevertheless, it's crucial to address specific legal and ethical considerations. For instance:
Sharing copyrighted material without permission is a strict no-go.
For blockchains, implementing KYC (know your customer) procedures for every user is important. This helps prevent potential issues, such as, money laundering and other illegal transactions through cryptocurrencies.
Security in P2P networks is paramount. Measures must be in place to prevent any unauthorized access by hackers to users' computers on the network.
It's essential to ensure that no malware spreads through the P2P network.
What lies ahead for the P2P networks?
P2P networks have gained traction in recent years when it comes to file sharing and cryptocurrency. With the advent of DeFi (decentralized finance) on blockchain, the future of P2P networks looks greener than ever. DeFi platforms allow people to lend or borrow funds from others without relying on any financial institute or brokerage. The most prominent blockchain that supports DeFi is the Ethereum blockchain.
Furthermore, P2P could play a role in how our smart devices communicate. Imagine your smart fridge and coffee maker having a direct chit-chat without involving a server. They might even plan your breakfast together. Sounds fun! isn’t it?
Recap
Here is what we have covered in this newsletter:
P2P networks follow decentralized architecture where inherently there is no central server acting as authority.
We have discussed the different models of P2P networks such as pure, hybrid, and blockchain-based P2P networks.
A detailed description of how a generic P2P network operates is discussed in this issue.
We have presented the advantages and challenges of P2P networks, together with some of the instances of the legal and copyright issues faced by P2P applications in the past.
The future of the P2P network looks brighter than ever with the advent of blockchain and DeFi technologies.
Like
Comment
Restack
© 2024 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe
by "ByteByteGo" <bytebytego@substack.com> - 11:38 - 6 Feb 2024 -
[Online workshop] Level up your Kubernetes observability with New Relic
New Relic

Are you familiar with Kubernetes, but want to gain a deeper understanding of some powerful kubectl commands to explore the cluster, work with labels, annotations and Helm settings to configure your environment from an observability perspective using the Prometheus agent? Then this interactive workshop is for you.
Register for our free workshop, "Level up your Kubernetes observability with New Relic" on 22nd February at 10 am GMT/ 11 am CET to learn how to get hands-on with a working Kubernetes environment, improve your understanding of the Prometheus Agent and how to make configuration changes that affect the metrics sent to New Relic. Join New Relic’s Kubernetes and observability expert, Harry Kimpel, to get hands-on with a live Kubernetes environment.
During the webinar, New Relic experts will take a technical dive into configuring the Prometheus agent, best practices and strategies, covering topics including:- Install the Prometheus Agent (and other New Relic components) into a Minikube cluster
- Work with Kubernetes labels and annotations to incrementally ingest new Prometheus metrics into your New Relic account
- View the data ingest in real-time with a supplemental New Relic dashboard specifically built for this Instruqt lab
- Learn how to manipulate data ingest by dropping labels and metrics using Prometheus Agent configuration techniques
Save Your Spot Need help? Let's get in touch.



This email is sent from an account used for sending messages only. Please do not reply to this email to contact us—we will not get your response.
This email was sent to info@learn.odoo.com Update your email preferences.
For information about our privacy practices, see our Privacy Policy.
Need to contact New Relic? You can chat or call us at +44 20 3859 9190.
Strand Bridge House, 138-142 Strand, London WC2R 1HH
© 2024 New Relic, Inc. All rights reserved. New Relic logo are trademarks of New Relic, Inc

by "New Relic" <emeamarketing@newrelic.com> - 07:06 - 6 Feb 2024 -
What can gen AI do for real estate?
On Point
7 steps to realize value Brought to you by Liz Hilton Segel, chief client officer and managing partner, global industry practices, & Homayoun Hatami, managing partner, global client capabilities
•
Getting value from gen AI. Gen AI technology comes at a favorable time for the real estate industry, as investors have gained access to a vast trove of client, community, and property data. When used as input for gen AI tools, such data could be leveraged to customize those platforms, enabling them to identify new commercial opportunities and increase revenue, McKinsey senior partner Matt Fitzpatrick and coauthors explain. However, realizing the full value of gen AI isn’t as simple as adopting one of the major foundational models. Companies should be prepared to address challenges in implementation and scaling.
— Edited by Vanessa Burke, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this newsletter because you subscribed to the Only McKinsey newsletter, formerly called On Point.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey" <publishing@email.mckinsey.com> - 01:42 - 6 Feb 2024 -
Video Telematics Solution - Monitor the Behavior of Vehicles and Drivers
Video Telematics Solution - Monitor the Behavior of Vehicles and Drivers
Change the way your clients track and monitor their fleet with our advanced video telematics software.
Change the way your clients track and monitor their fleet with our advanced video telematics software.
Catch a glimpse of what our software has to offer

Multiple Camera Support
Our software enables multiple camera support for a comprehensive view inside and outside the vehicle.

Identify Risky Behavior
Monitor risky driver behavior, including speeding, harsh braking, and other unsafe driving habits.

Redefine Visibility
Make a visual record of the tiniest details of your vehicle’s journey. With ready-to-access visual data displayed in real-time, see what the driver is doing.

24X7 Live Streaming
Access video recordings instantly anywhere, anytime with our mobile app support. Enjoy multiple channel access and flexible viewing options.

ADAS
ADAS uses sensors and cameras to detect potential hazards and alert drivers to potential risks.

Driver Monitoring System
DMS monitors driver behavior, including fatigue and distraction. The system gets real-time alerts and detailed reports.
.png?width=1200&upscale=true&name=statics%20data%20of%20video%20telematics%20(1).png)
Learn how our video telematics can help your business grow

Uffizio Technologies Pvt. Ltd., 4th Floor, Metropolis, Opp. S.T Workshop, Valsad, Gujarat, 396001, India
by "Sunny Thakur" <sunny.thakur@uffizio.com> - 07:00 - 5 Feb 2024 -
So you want to be a board director: A leader’s guide
Welcome aboard Brought to you by Liz Hilton Segel, chief client officer and managing partner, global industry practices, & Homayoun Hatami, managing partner, global client capabilities
Serving on a board of directors is an unequivocal opportunity for leaders to develop new skills, hone their business acumen, and expand their personal and professional networks. And boards themselves benefit from the fresh perspectives that new directors bring to the boardroom. But for those who haven’t taken the plunge, the “how” of joining a corporate board is less than clear. Board membership is also a significant investment of time, especially as the board’s role—and the range of issues that come across a board member’s proverbial desk—continues to expand and evolve. We’ll take a look at specific ways to get started on your board journey and what success looks like once you’re there.
While the path to board membership may seem winding or murky, McKinsey senior partner Celia Huber and colleagues outline six steps that board-curious leaders can take. Wherever leaders are on the journey, they shouldn’t underestimate the value of asking questions: an “ask, don’t tell” policy is an important way for directors to contribute and clarify their role. “First-time directors often find it difficult to step away from an operator mentality,” the authors say. A director’s job “isn’t to offer solutions but to probe and constructively challenge management’s proposals to make executives reflect on their decisions. Your objective should be to help the management team see ten steps ahead.” With so many competing priorities to weigh, the ability to ask thoughtful questions about everything from generative AI (gen AI) to the company’s purpose is paramount.
That’s the percentage of directors who, in a global survey, believe their organizations are unprepared to manage the next large-scale crisis. In a conversation about preparing for extraordinary risks, McKinsey’s Celia Huber and colleagues note the importance of identifying “predictable surprises”: events that would, with great certainty, change a company’s entire business. Boards, and new directors in particular, have a critical part to play in this process. “If the board engages in approving strategy, it’s helpful to ask, ‘What would cause this strategy to fail?’” says senior partner emeritus Nora Aufreiter. “New members are sometimes best at identifying long-term core risks because they can step back and ask simple questions that longtime directors may not think of or assume the organization knows the answer to.”
That’s senior partner Asutosh Padhi discussing the board’s role in building a resilient organization: that is, a company that can change course when faced with a potential shock. So much of a director’s job is a balancing act. Collectively, boards must also walk and chew gum at the same time in preparing their companies for both the current moment and what’s to come. “Fundamentally, board members can think about the balance between defensive versus offensive responses to crisis, short-term versus long-term trade-offs, and appropriately challenging management,” says senior partner Ida Kristensen.
While the board’s role is continually changing, the people part of its work is perhaps more critical than ever—especially for the person at the top. “Being CEO is a lonely job,” says Nicolai Tangen, the CEO of Norges Bank Investment Management (NBIM), in an interview with senior partner Frithjof Lund. “CEOs need someone they can talk to and trust. You are there not only to ask the right questions but also to look for signs of stress and burnout and provide early support to CEOs in need.” And while CEO succession remains a fundamental board responsibility, broader issues of talent, skill development, and organizational culture are now firmly on the agenda.
Popular wisdom suggests that there’s no such thing as a stupid question. Indeed, the willingness to ask questions—even ones that seem obvious or tough—is an important way for prospective and new directors to showcase their intellectual curiosity and ways of thinking, including when interviewing for the role. That can be easier said than done for new members who are just getting their bearings. If you’re reluctant to speak up at the start of your tenure, take a page from Albert Einstein’s book. One way to contribute to board discussions from the start is “question storming”: that is, starting a problem-solving session by asking as many questions (more than 50!) as you can about the problem at hand. Once you and your board colleagues have some answers, a solution will be much easier to reach.
Lead by asking questions.
– Edited by Daniella Seiler, executive editor, Washington, DC
Share these insights
Did you enjoy this newsletter? Forward it to colleagues and friends so they can subscribe too. Was this issue forwarded to you? Sign up for it and sample our 40+ other free email subscriptions here.
This email contains information about McKinsey’s research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to the Leading Off newsletter.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Leading Off" <publishing@email.mckinsey.com> - 04:35 - 5 Feb 2024 -
Attitudes about college are changing. What should US higher ed leaders do?
On Point
5 actions to support students Brought to you by Liz Hilton Segel, chief client officer and managing partner, global industry practices, & Homayoun Hatami, managing partner, global client capabilities
•
Learning and earning. US higher education faces tough times. Although people clearly benefit from securing a postsecondary degree—earning more money over their lifetimes, for instance—enrollment growth is slowing, student debt is at an all-time high, and many Americans are developing a dimmer view of institutions of higher learning. In light of these challenges, the sector should still set a bold goal: to graduate ten million more students than currently projected over the next 20 years, McKinsey senior partner Jonathan Law and coauthors suggest.
— Edited by Belinda Yu, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this newsletter because you subscribed to the Only McKinsey newsletter, formerly called On Point.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey" <publishing@email.mckinsey.com> - 11:08 - 4 Feb 2024 -
Zooming in on the Black resident experience
Black History Month begins Brought to you by Liz Hilton Segel, chief client officer and managing partner, global industry practices, & Homayoun Hatami, managing partner, global client capabilities
New from McKinsey & Company
“People shape places, and places in turn shape outcomes for people.” So write McKinsey’s JP Julien, Duwain Pinder, Shelley Stewart III, and coauthors in a new report from the McKinsey Institute for Black Economic Mobility that reveals substantial differences in overall outcomes for US Black residents across community profiles—as well as substantial gaps between Black and White residents in virtually every county. How can investors, companies, philanthropies, and public-sector leaders devise solutions that are transformative for Black residents and the trajectory of their communities? As Black History Month kicks off, check out these insights to understand the role of community in racial equity, as well as the opportunities that exist to advance outcomes for Black residents.
To see more essential reading on topics that matter, visit McKinsey Themes.
— Edited by Eleni Kostopoulos, managing editor, New York
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to our McKinsey Global Institute alert list.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey & Company" <publishing@email.mckinsey.com> - 06:45 - 3 Feb 2024 -
The week in charts
The Week in Charts
Gen AI in fashion, future-proof jobs, and more Share these insights
Did you enjoy this newsletter? Forward it to colleagues and friends so they can subscribe too. Was this issue forwarded to you? Sign up for it and sample our 40+ other free email subscriptions here.
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to The Week in Charts newsletter.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Week in Charts" <publishing@email.mckinsey.com> - 03:21 - 3 Feb 2024 -
Shifts in the geometry of global trade
Plus, 10 digital and AI ideas shaping business Global trade patterns are reconfiguring, and increased investment into a range of developing economies suggests further trade reconfiguration in coming years. What can business leaders do to position their organizations for uncertainty? In a report from the McKinsey Global Institute, Jeongmin Seong, Olivia White, Michael Birshan, Lola Woetzel, and coauthors explore shifts in the geometry of global trade—and their many implications. Our second featured story examines how a Panama Canal slowdown could affect various trade segments and stakeholders. Other highlights in this month’s issue include the following topics:
Ten unsung digital and AI ideas shaping business
Keeping your eye on where value comes from is still the name of the game.
Rewire for value capture
Closing the women’s health gap: A $1 trillion opportunity to improve lives and economies
Investments addressing the women’s health gap could add years to life and life to years—and potentially boost the global economy by $1 trillion annually by 2040.
Take a holistic approach
The trends defining the $1.8 trillion global wellness market in 2024
Our latest Future of Wellness survey finds that consumers are taking greater control over their health—and expect companies to provide effective, science-backed solutions.
7 areas of growth
How CEOs can mitigate compounding risks
When risks combine, the cumulative impact can have existential consequences. But leaders can prevent compounding risks from sneaking up on them by adapting risk processes to manage multiple threats.
Be prepared
What to expect in US healthcare in 2024 and beyond
A new perspective on how technology, transformation efforts, and other changes have affected payers, health systems, healthcare services and technology, and pharmacy services.
See what’s ahead
How to identify employee disengagement
More than half of employees say they’re disengaged at work—with implications for both morale and value creation. Do any of these behaviors seem familiar?
Take the quiz
McKinsey Themes
Browse our essential reading on the topics that matter.
Get up to speed
McKinsey Explainers
Find direct answers to complex questions, backed by McKinsey’s expert insights.
Learn more
McKinsey on Books
Explore this month’s best-selling business books prepared exclusively for McKinsey Publishing by Circana.
See the lists
McKinsey Chart of the Day
See our daily chart that helps explain a changing world—as we strive for sustainable, inclusive growth.
Dive in
McKinsey Classics
Is there a link between the strategic moves of new CEOs and the performance of their companies? Read our 2016 classic “How new CEOs can boost their odds of success” to learn more.
Rewind
The Daily Read
Our Daily Read newsletter features revealing research and inspiring interviews to empower you—and those you lead.
Subscribe now— Edited by Eleni Kostopoulos, managing editor, New York
Share these insights
Did you enjoy this newsletter? Forward it to colleagues and friends so they can subscribe too. Was this issue forwarded to you? Sign up for it and sample our 40+ other free email subscriptions here.
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you are a registered member of our Monthly Highlights newsletter.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Highlights" <publishing@email.mckinsey.com> - 11:45 - 3 Feb 2024 -
EP97: 10 Good Coding Principles to Improve Code Quality
EP97: 10 Good Coding Principles to Improve Code Quality
This week’s system design refresher: How Disney Hotstar Captures One Billion Emojis (Youtube video) 10 Good Coding Principles to improve code quality Top Network Security Cheatsheet How does a VPN work? Explaining 9 types of API testing What is a cookie? Forwarded this email? Subscribe here for moreThis week’s system design refresher:
How Disney Hotstar Captures One Billion Emojis (Youtube video)
10 Good Coding Principles to improve code quality
Top Network Security Cheatsheet
How does a VPN work?
What is a cookie?
ScyllaDB Summit | Feb 14-15 | Free + Virtual (Sponsored)
Join thousands of your peers for an unprecedented opportunity to learn from experts at Discord, Disney, Expedia, Zee, ShareChat, Paramount & more – for free, from anywhere.
30+ talks on NoSQL, Kafka, Kubernetes, and AI/ML system architectures and best practices, plus interactive hands-on training.Discord Keynote: Everything's great until the database is down. Bo Ingram, staff engineer at Discord and author of ScyllaDB in Action, shares lessons from their database outage so that you can learn from their mistakes.
Book Bonus: Register this week to get Database Performance at Scale and an early access copy of ScyllaDB in Action.
How Disney Hotstar Captures One Billion Emojis!
Subscribe to our YouTube Channel Now
10 Good Coding Principles to improve code quality
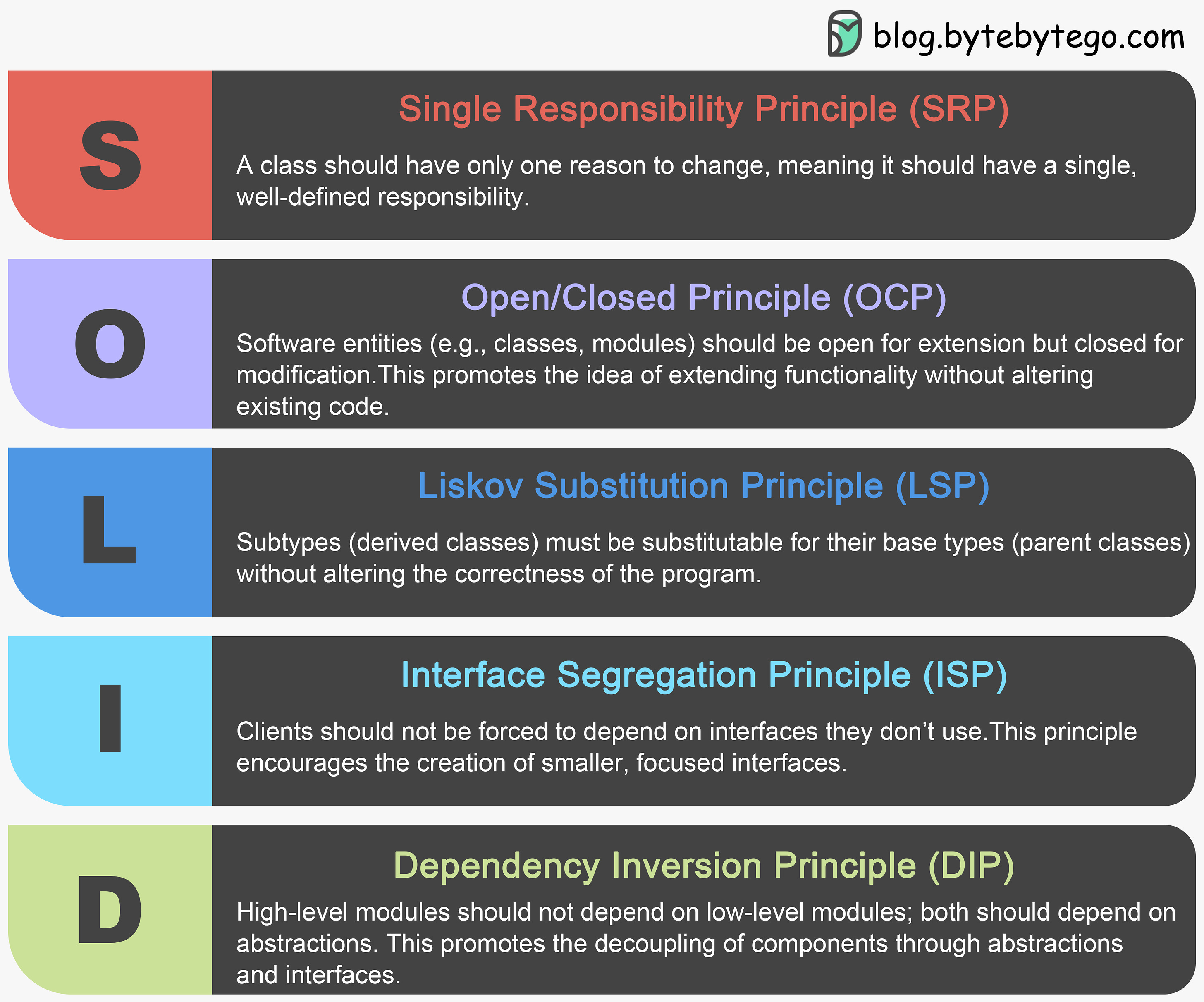
Software development requires good system designs and coding standards. We list 10 good coding principles in the diagram below.
01 Follow Code Specifications
When we write code, it is important to follow the industry's well-established norms, like “PEP 8”, “Google Java Style”, adhering to a set of agreed-upon code specifications ensures that the quality of the code is consistent and readable.02 Documentation and Comments
Good code should be clearly documented and commented to explain complex logic and decisions, and comments should explain why a certain approach was taken (“Why”) rather than what exactly is being done (“What”). Documentation and comments should be clear, concise, and continuously updated.03 Robustness
Good code should be able to handle a variety of unexpected situations and inputs without crashing or producing unpredictable results. Most common approach is to catch and handle exceptions.04 Follow the SOLID principle
“Single Responsibility”, “Open/Closed”, “Liskov Substitution”, “Interface Segregation”, and “Dependency Inversion” - these five principles (SOLID for short) are the cornerstones of writing code that scales and is easy to maintain.05 Make Testing Easy
Testability of software is particularly important. Good code should be easy to test, both by trying to reduce the complexity of each component, and by supporting automated testing to ensure that it behaves as expected.06 Abstraction
Abstraction requires us to extract the core logic and hide the complexity, thus making the code more flexible and generic. Good code should have a moderate level of abstraction, neither over-designed nor neglecting long-term expandability and maintainability.07 Utilize Design Patterns, but don't over-design
Design patterns can help us solve some common problems. However, every pattern has its applicable scenarios. Overusing or misusing design patterns may make your code more complex and difficult to understand.08 Reduce Global Dependencies
We can get bogged down in dependencies and confusing state management if we use global variables and instances. Good code should rely on localized state and parameter passing. Functions should be side-effect free.09 Continuous Refactoring
Good code is maintainable and extensible. Continuous refactoring reduces technical debt by identifying and fixing problems as early as possible.10 Security is a Top Priority
Good code should avoid common security vulnerabilities.
Over to you: which one do you prefer, and with which one do you disagree?
Latest articles
If you’re not a paid subscriber, here’s what you missed this month.
To receive all the full articles and support ByteByteGo, consider subscribing:
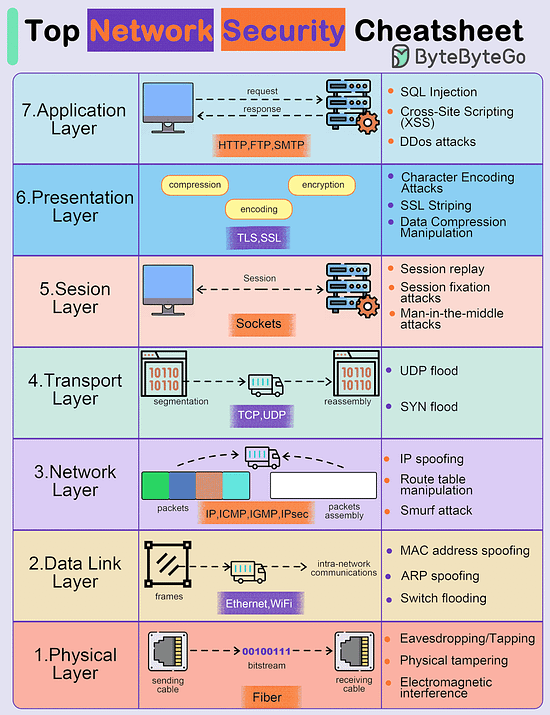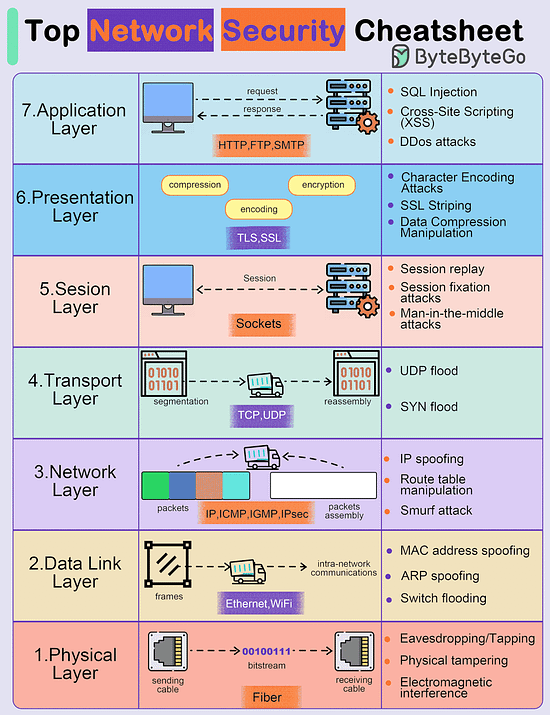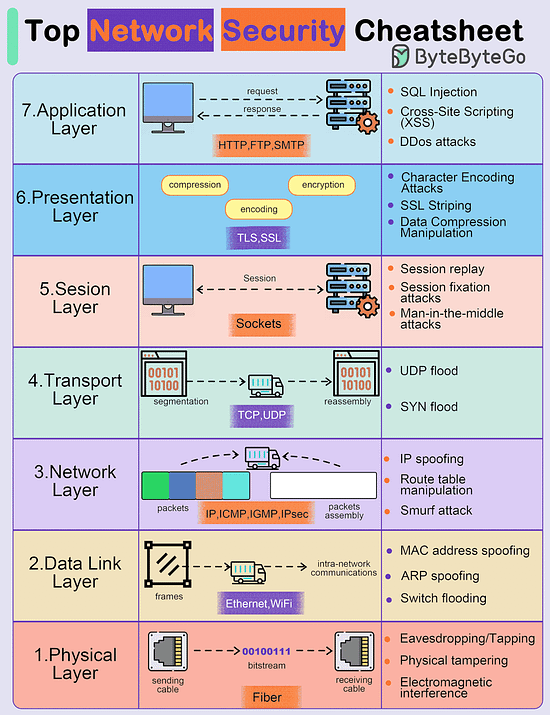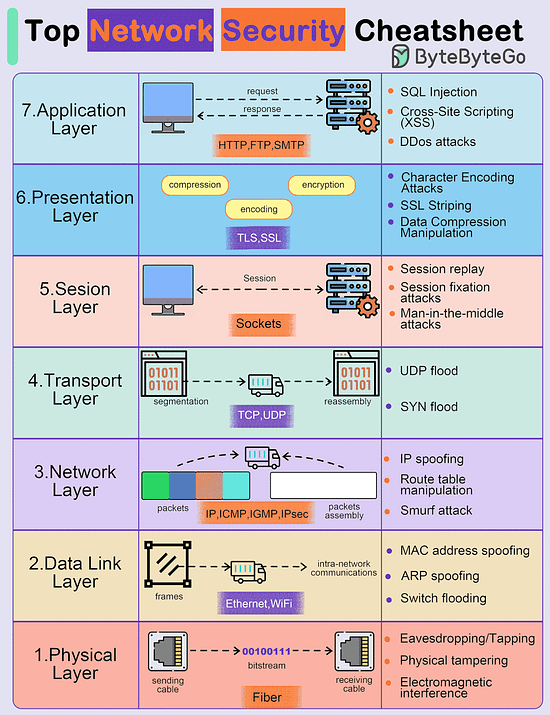
Top Network Security Cheatsheet
The diagram below shows some possible network attacks in 7 OSI model layers.
Application Layer
- Pushing
- Malware injection
- DDos attacksPresentation Layer
- Encoding/decoding vulnerabilities
- Format string attacks
- Malicious code injectionSession Layer
- Session hijacking
- Session fixation attacks
- Brute force attacksTransport Layer
- Man-in-the-middle attacks
- SYN/ACK floodNetwork Layer
- IP spoofing
- Route table manipulation
- DDos attacksData Link Layer
- MAC address spoofing
- ARP spoofing
- VLAN hoppingPhysical Layer
- Wiretapping
- Physical tampering
- Electromagnetic interference
Over to you - What did we miss?
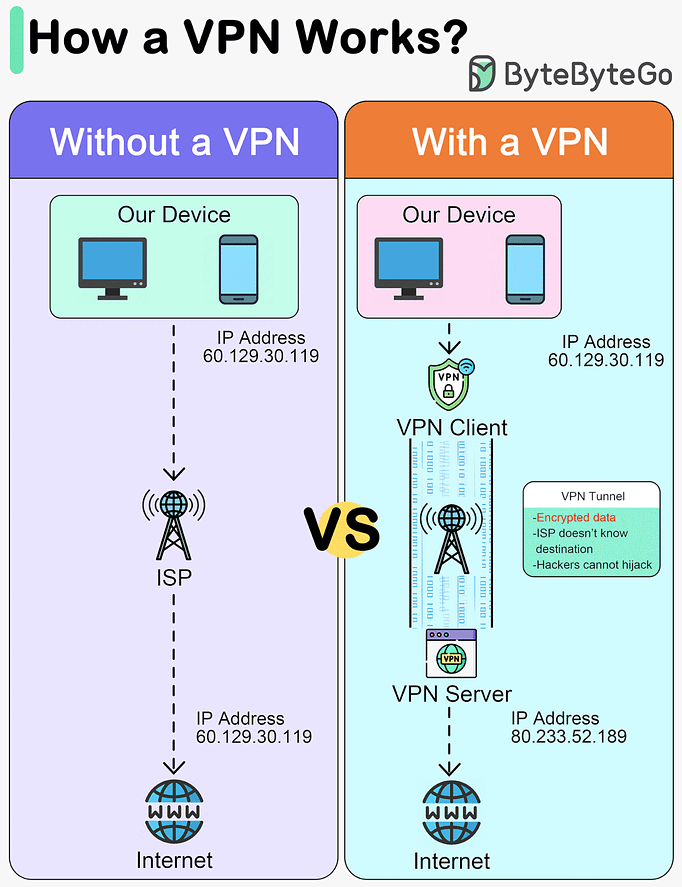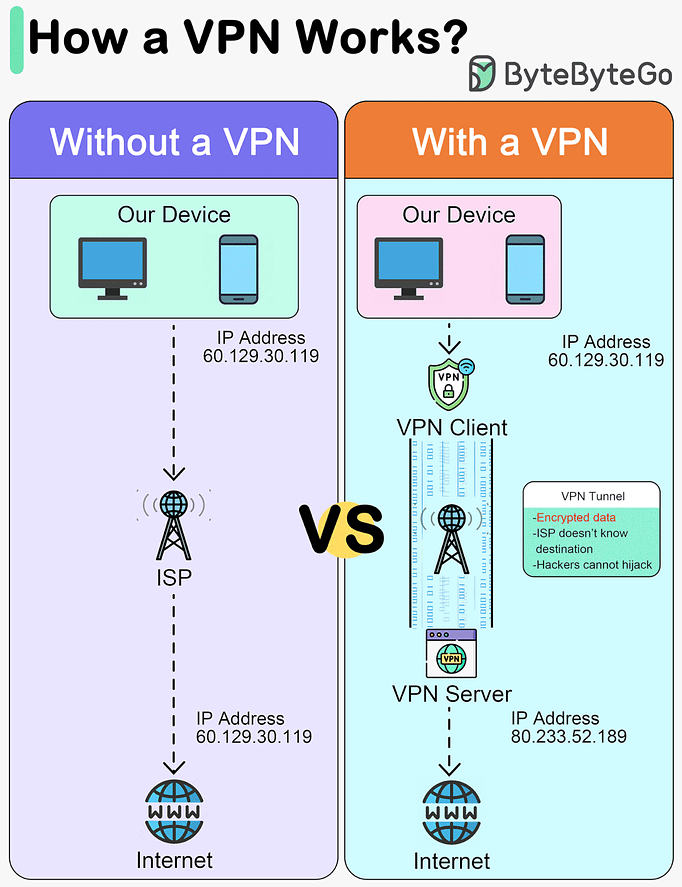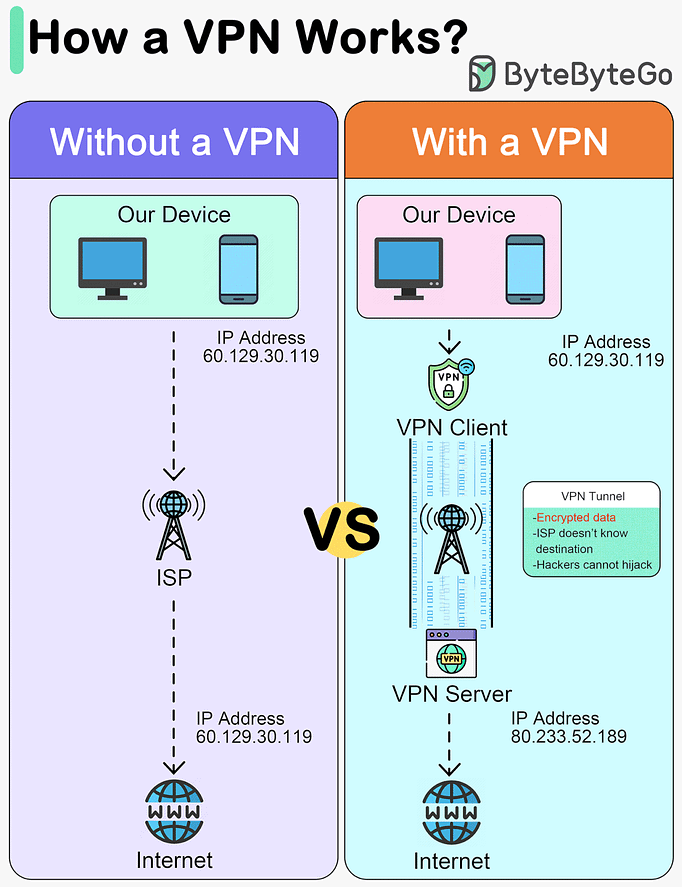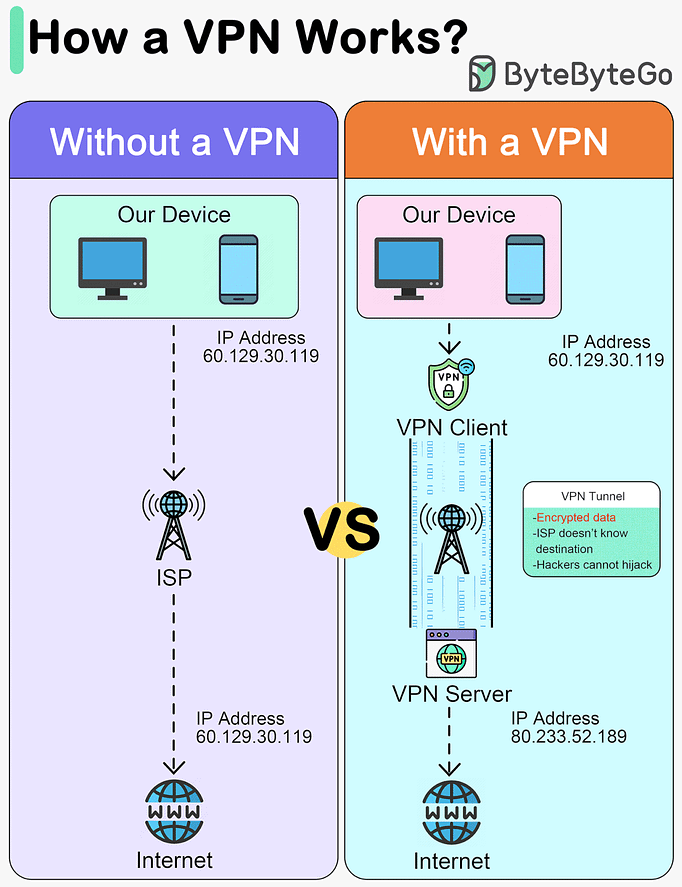
How does a VPN work?
This diagram below shows how we access the internet with and without VPNs.
A VPN, or Virtual Private Network, is a technology that creates a secure, encrypted connection over a less secure network, such as the public internet. The primary purpose of a VPN is to provide privacy and security to data and communications.
A VPN acts as a tunnel through which the encrypted data goes from one location to another. Any external party cannot see the data transferring.
A VPN works in 4 steps:Step 1 - Establish a secure tunnel between our device and the VPN server.
Step 2 - Encrypt the data transmitted.
Step 3 - Mask our IP address, so it appears as if our internet activity is coming from the VPN server.
Step 4 - Our internet traffic is routed through the VPN server.
Advantages of a VPN:
Privacy
Anonymity
Security
Encryption
Masking the original IP address
Disadvantages of a VPN:
VPN blocking
Slow down connections
Trust in VPN provider
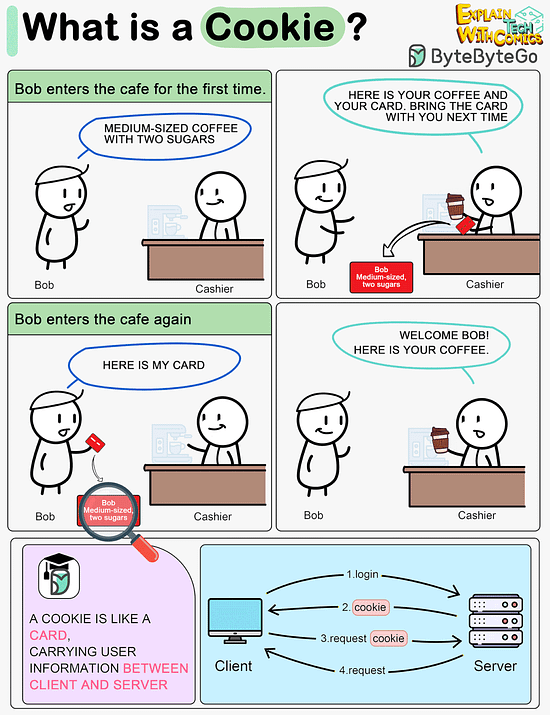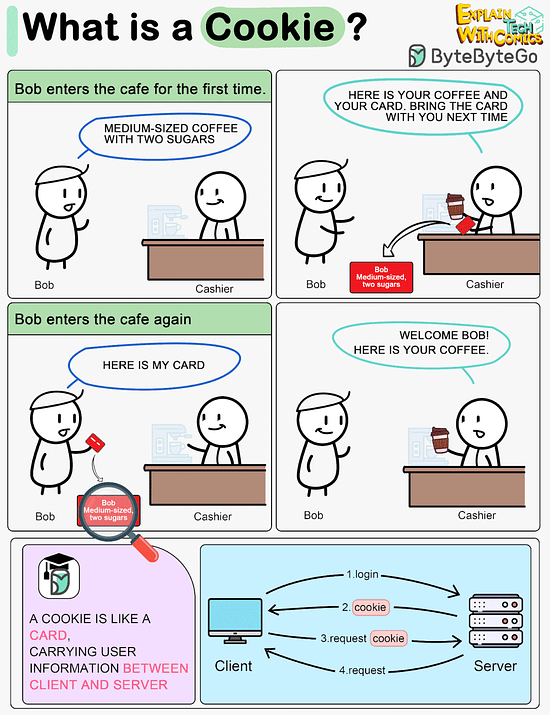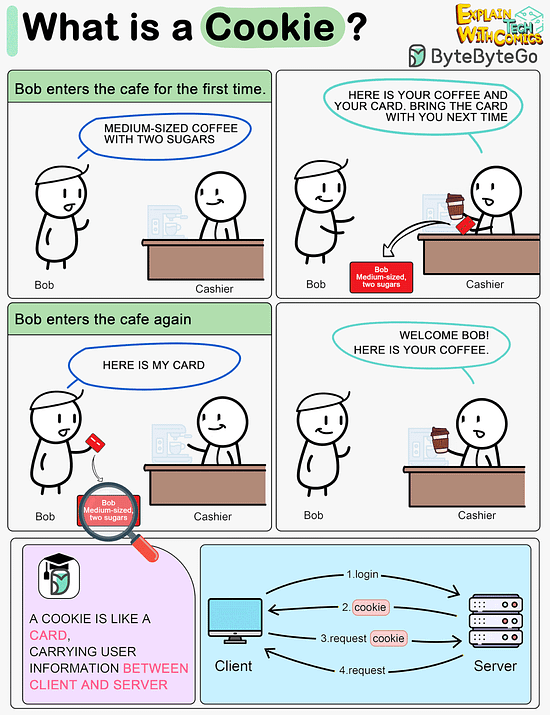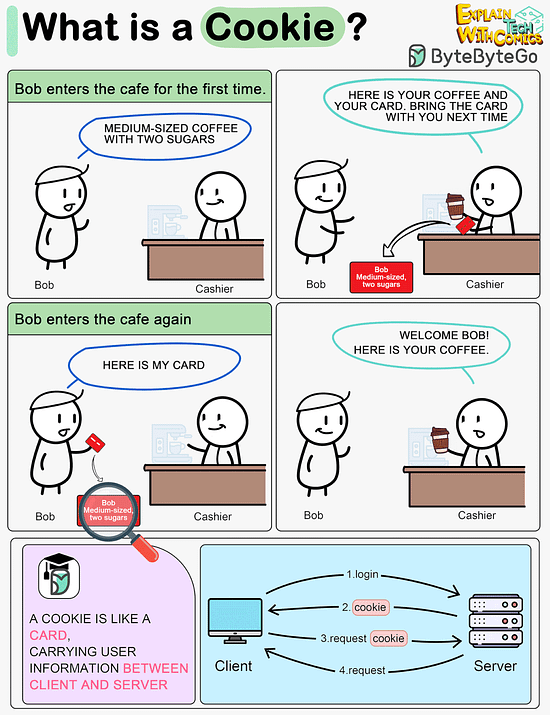
What is a cookie?
Imagine Bob goes to a coffee shop for the first time, orders a medium-sized espresso with two sugars. The cashier records Bob’s identity and preferences on a card and hands it over to Bob with a cup of coffee.
The next time Bob goes to the cafe, he shows the cashier the preference card. The cashier immediately knows who the customer is and what kind of coffee he likes.
A cookie acts as the preference card. When we log in to a website, the server issues a cookie to us with a small amount of data. The cookie is stored on the client side, so the next time we send a request to the server with the cookie, the server knows our identity and preferences immediately without looking into the database.Like
Comment
Restack
© 2024 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe
by "ByteByteGo" <bytebytego@substack.com> - 11:38 - 3 Feb 2024 -
What are the essentials of innovation?
On Point
Five fundamentals of innovation culture Brought to you by Liz Hilton Segel, chief client officer and managing partner, global industry practices, & Homayoun Hatami, managing partner, global client capabilities
•
Out-innovating your peers. The best companies don’t just outgrow their competitors—they out-innovate them as well. In the face of constant disruptions, leading companies become “innovative growers,” excelling at growth and innovation and outperforming their peers in the process. In fact, most of the 50-plus companies McKinsey identified as innovative growers achieved TSR above their industry median between 2012 and 2022, partner Rebecca Doherty and coauthors explain.
— Edited by Belinda Yu, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this newsletter because you subscribed to the Only McKinsey newsletter, formerly called On Point.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey" <publishing@email.mckinsey.com> - 01:31 - 2 Feb 2024













.png)