Archives
- By thread 5360
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 173
-
SEE YOU IN DUBAI CONFERENCE
Dear friend,
Good day, greeting from Kianna and GLA network.
The world's logistics elite are here for you!
What are you waiting for?
Welcome to the 12th GLA Global Logistics Conference
Event Name: The 12th GLA Global Logistics Conference
Host By: GLA Global Logistics Alliance
Event Date: May 15-18, 2025 (4 days)
Host City: Dubai, UAE
Event Venue: Grand Hyatt Dubai
Event Address: Sheikh Rashid Road, Dubai, P.O. Box 7978, United Arab Emirates
Expected Attendees: 2000+ PAX
Best regards,
Kianna Zhang
GLA Overseas Department
Mobile:
(86) 190-7616-6986
Email:
Company:
GLA Co.,Ltd
Website:
Address:
No. 2109, 21st Floor, HongChang, Plaza, No. 2001, Road Shenzhen, China
Conference register: https://www.glafamily.com/summit/gla.php/home/index/registration/refer/Kianna
(Notice: If you would not like to receive email blush, please inform us timely. We will delete your data from the database)
by "Kianna" <member166@glafamily.com> - 09:24 - 24 Dec 2024 -
Choosing resilience through uncertainty
Meet the moment: Chapter 3 of 4 New from McKinsey & Company
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to our McKinsey Global Institute alert list.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey & Company" <publishing@email.mckinsey.com> - 03:15 - 24 Dec 2024 -
66
Dear friend
I trust this message finds you well.
I am Jeffery, representing Hongocean, a trusted freight forwarding company based in China.
I'm excited to share with you our current market situation, which are highly competitive and designed to cater to your shipping needs. Please find the details below:
1. YT to LA O/F:$3550/40HQ
2. SH to NY O/F: $4000/40HQ
we can realeased the space to your supplier right now
Validity time is 12 .31
Should you require any additional information, have queries, or wish to make a booking, please don't hesitate to reach out to me directly.
I look forward to the prospect of working with you.
by "Jeffery" <nat@cctsupplier.com> - 11:38 - 24 Dec 2024 -
Estimating & Take-Off Services.
Hi, We at Estimen LLC, are offering complete accuracy in Material Quantity Take-offs and Cost Estimation of projects. We do both residential and commercial project estimates for renovation as well as new constructions and have more than 15 years of experience. Please let us know if you need any estimating services regarding your projects. Simply send over your plans for a custom quote for our service charges and turnaround time. Thank you! Best Regards, Estimation Department BD Manager | Estimen LLC
by jhointykilrtik@gmail.com - 09:49 - 24 Dec 2024 -
Application for the Position of Openbravo/Etendo/iDempiere ERP Techno Functional Consultant – Design Architect
Dear Sir,Please find my information below.
https://www.linkedin.com/in/mdabulkhayer/
Customizations on Different ERP and Digital Transformations.
Client: Aware Corporation Limited., Thailand
- Thailand Based Business Operation and Customization (Vat, Tax and SSO etc. on ERP System
- Loan and Advance Management on ERP System
- Google and Cloud Bill Importing into System on ERP System
- Quotation Management - External Tools using Java. on ERP System
- Openbravo Integration POS - External Tools using .Net and MongoDB.
on ERP System
- Openbravo Integration E-Commerce - External Tool using Magento 2.
- All reports excel with formulas. (Balance Sheet, Profit and Loss, Inventory, Income Summary, Cash Flow, etc.) on ERP System
- IT Asset Management, Manage IT Services with Demand Planning on ERP System
- Accounting Asset Management with Change the Depreciation Method and Process with write of and Sales on ERP System
Client: RoyiSal Co,. Ltd., Bangkok, Thailand,Requirement Analysis and GAP Analysis.1. Jewelry Industry ERP system using Odoo, Hubspot, Clickup, Weladee and PowerBI2. PDV Management3. Production/Manufacturing Process Automation4. Quality Control Management5. Procurement6. Inventory and Merchandising7. HR and Attendance with Payroll8. Sales and CRM with B2B and B2C and D2C9. Marketing and E-Commerce10. Accounting and Finance Management11. IT Management and Services12. Data Section for Artificial Intelligence (AI) and Data analysis using PowerBI and Power PlatformClient: Khayal Al-Watania Company, Saudi Arabia
1. Point of Sales for Restaurant (Java POS)
2. Point of Sales for Restaurant (Web POS)
3. Human Resource Management with Access Control Integration
4. Inter-Company Management
5. Physical Inventory Enhancement
6. Costing Process Enhancement
7. Customer Relation Management with Call Center Solution
Client: Al-Safi, Saudi Arabia
1. Warehouse Management
Client: LBG Business Group, Saudi Arabia
1. Production Cake Management
Client: National Development Engineering Ltd., Bangladesh
1. Tender and Costing Module
2. LC Management with Back 2 Back LC
3. Rate Analysis Management
Client: Placer Textiles Ltd., Bangladesh
1. Buyer Order Management and Processing
Client: Bengal Group Ltd., Bangladesh
1. Office Management with Google Charts and Attendance Devices Direct Integration
2. Recurring Billing and Integration Payment Processing using Mobile Apps.
Client: Jamal Uddin Textiles Ltd., Bangladesh
1. Human Resource Management with Access Control Integration
Habib Clinic and Diagnostic Center Ltd., Bangladesh
1. Human Resource Management with Access Control Integration
RAK Ceramics Ltd., Bangladesh and UAE
1. Time and Attendance Management with Access Control and SAP ERP
Client: Chunk Restaurant, Bangladesh
1. Point of Sales for Restaurant (Java POS)
2. Daily Inventory Management
3. Daily/Weekly/Monthly Web Sales Monitoring using Mobile Apps
4. Daily/Weekly/Monthly Inventory Monitoring using Mobile Apps
Client: Nitto Ponno., Bangladesh
1. Point of Sales for Shop (Java POS)
Client: Chapai Foods., Bangladesh
1. Point of Sales for Restaurant (Java POS)
I am skilled at Oracle SQL, PL/SQL, Java, TypeScript, NodeJS with Express, BackboneJS, ReactJS, Postgresql, and Python on Odoo ORM, Data Warehouse Concept with PowerBI, and Integration with Hubspot, ClickUP, Weladee, Openbravo/Etendo/Orisha Retail and Odoo.
Regards,
MD Abul Khayer
by "MD Abul Khayer" <khayerkazi@gmail.com> - 06:29 - 23 Dec 2024 -
McKinsey Global Institute: 2024 in charts
Dive in New from McKinsey Global Institute
•
Global connections: Exploring how flows of goods, services, people, capital, and ideas shape economies
•
Resources of the world: Building, powering, and feeding the world sustainably
•
Productivity and prosperity: Creating and harnessing the world’s assets most productively
•
Human potential: Maximizing and achieving the potential of human talent
•
Technology and markets of the future: Exploring the next big arenas of value and competition
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to our McKinsey Global Institute alert list.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey & Company" <publishing@email.mckinsey.com> - 12:41 - 23 Dec 2024 -
RE : Looking for Saudi Arabia agent
Dear agent,
Greeting from Cara and GLA family. Trust you are doing great.
I sincerely invite you to join GLA platform and cover the increasing request from/to Saudi Arabia from our GLA members.
Above 75% of GLA Members are first-class agents with wide range of primary resources. GLA fulfills all your needs for your business development and resources integration, in terms of finding reliable agents and getting huge volume of inquiries from/to your area.
Besides, We are planning to hold the 12th GLA Global Logistics Conference:
Ø Event Name: The 12th GLA Global Logistics Conference
Ø Host By: GLA Global Logistics Alliance
Ø Event Date: May 15 - 18, 2025 (4 days)
Ø Host City: Dubai, UAE
Ø Expected Attendee: 1500+
Ø From: 130+ countries
Ø 1-on-1 Meeting: 51 times per pax
The early bird price for the 12th GLA Conference is now open till 31st Dec 2024! Please don’t miss this opportunity to attend the conference as a GLA member.
If you want to know more, please don’t hesitate to contact me.
Best regards,
Cara Chen
GLA Overseas department
Mobile:
(86) 190-7616-6926 (WhatsApp|Wechat)
Email:
Company:
GLA Co.,Ltd
Website:
Address:
No. 2109, 21st Floor, HongChang, Plaza, No. 2001, Road Shenzhen, China
The 12th GLA Conference – Dubai, UAE on 15th - 18th May 2025 – click here for registration
Ø The 11th GLA Conference in Bangkok Thailand, online album
Ø The 10th GLA Conference in Dubai UAE, online album
Ø The 9th GLA Conference in Hainan China, online album
【Notice Agreement No 7】
7. GLA president reserves the right to cancel or reject membership or application.
company shall cease to be a member of GLA if:
a) the Member does not adhere to GLA terms and conditions
b) the Member gives notice of resignation in writing to the GLA.
c) No good reputation in the market.
d) Have bad debt records in the GLA platform or in the market
by "Cara" <member226@glafamily.com> - 05:20 - 23 Dec 2024 -
Viktory Gym: migliorare il flusso di cassa
Ciao team di Viktory Gym,
Ho visto il vostro sito web - ottime offerte fitness. Come palestra, il flusso di cassa può essere una sfida. Qomodo fornisce liquidità istantanea attraverso soluzioni di pagamento digitale, offrendo rate senza interessi per i clienti.
Ci siamo associati con Mastercard per servire le PMI come voi.
Interessati a saperne di più?
by gianluca@smartqomodo.com - 05:06 - 23 Dec 2024 -
Essential leadership lessons from 2024: A leader’s guide
Leading Off
Connection is key
by "McKinsey Leading Off" <publishing@email.mckinsey.com> - 04:32 - 23 Dec 2024 -
Did you miss any of our most-read issues?
Only McKinsey Perspectives
Succession planning, navigating geopolitics, and vulnerability Brought to you by Alex Panas, global leader of industries, & Axel Karlsson, global leader of functional practices and growth platforms
Thanks for reading Only McKinsey Perspectives! We’re taking some time off for the holidays, but we’ll be back in your inbox on January 13. We’ll continue delivering actionable insights on the day’s news, as only McKinsey can, including those that will headline the World Economic Forum’s upcoming Annual Meeting in Davos, Switzerland. In the meantime, enjoy revisiting some of our most-read recent issues:
And because year’s end is a good time for cleanup, take a moment to revisit your subscriptions too—and to find out about any new ones, like McKinsey’s Davos Daily. This limited-run email series explores key themes of the World Economic Forum's Annual Meeting through a carefully curated roundup of McKinsey insights—daily for eight days, starting January 18. Sign up with one click.
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to the Only McKinsey Perspectives newsletter, formerly known as Only McKinsey.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey Perspectives" <publishing@email.mckinsey.com> - 01:15 - 23 Dec 2024 -
Re: Beauty Industry Professionals list
Hope you are doing well!
We have a Newly Updated OPT-IN database which will help you in reaching Beauty Industry Professionals across North America, UK, Europe and Global.
Job Titles:
· Beauty Industry Consultants
· Beauty Procurement/Purchasing
· Chain Salon Buyer
· Department Store Buyer
· Distributors / Drug Store Buyer
· Estheticians / Importers/Exporters
· International Buyer
· Investment Companies
· Licensed Makeup Artists
· Manufacturer- Representatives
· Manufacturers / Nail Technicians
· OTC/Beauty Retailers
· Packaging Vendors or Suppliers
· Pharmaceutical Companies
· Raw Material Suppliers
· Retail Buyers / Salon/Spa Managers
· Salon/Spa Owners / School Owners
· Specialty Store Buyer / Stylist/Cosmetologists
· Transportation/Shipping Logistics
· Venture Capitalists
The list includes Name, Company, Title, Employee & Revenue Size, Industry, SIC Code, Fax, Website, Physical Address, Phone Number and Verified Email Address.
Please fill in the below details and revert back on the same email, If you would like to add any other criteria (Which mean business to you).
Target Criteria:
· Industry you would like to reach: _______?
· Job title: _______?
· Geography: _______?
We can also help you in E mail and data appending solutions which can help in holding back your lost customers.
Look forward to hearing from you. Thanks!!
Warm Regards,
Christy chay
Marketing Executive
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
We respect your privacy, if you want to remove it from this list. Please reply back with the subject line as “Leave Out”.
by "Christy Chay" <christy@datachamberusa.com> - 10:54 - 22 Dec 2024 -
Meet the partners behind our best 2024 insights on resilience
Turn insights to impact New from McKinsey & Company
In a rapidly evolving world, resilience in the face of uncertainty remains as important as ever. Meet some of McKinsey's impact partners and explore their top insights of the year on risk, sustainability, productivity, and more. Then turn hindsight into foresight by diving into "Meet the moment," our interactive year-in-review experience.
To see more essential reading on topics that matter, visit McKinsey Themes.
— Edited by Esther Chung, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to our McKinsey Global Institute alert list.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey & Company" <publishing@email.mckinsey.com> - 01:00 - 22 Dec 2024 -
The quarter’s top themes
McKinsey&Company
At #1: 18 industries that could reshape the global economy In the fourth quarter of 2024, our top ten posts from McKinsey Themes highlight generative AI, the organization of the future, interviews with industry leaders, and more. At No. 1 is “18 industries that could reshape the global economy,” which features must-read insights from McKinsey’s Kweilin Ellingrud, Homayoun Hatami, and more. Read on for our full top 10.
3. The skills revolution and the future of learning and earning
October is National Learning and Development Month in the US, but technology is changing the nature of work all around the world. As organizations deploy these new technologies—including automation and artificial intelligence—how can they support current employees and prepare the future workforce for success? Fly above competitors
“Today’s leaders must master complex issues such as digital transformation, inflation, disrupted global supply chains, scarce talent, a lack of diversity, cybersecurity, and climate change, as well as an awakened search for purpose among employees,” say McKinsey senior partners Dana Maor, Kurt Strovink, Ramesh Srinivasan, and senior partner emeritus Hans-Werner Kaas. Read more
This email contains information about McKinsey’s research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you are a registered member of the Top Ten Most Popular newsletter.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Top Ten" <publishing@email.mckinsey.com> - 10:50 - 22 Dec 2024 -
The week in charts
The Week in Charts
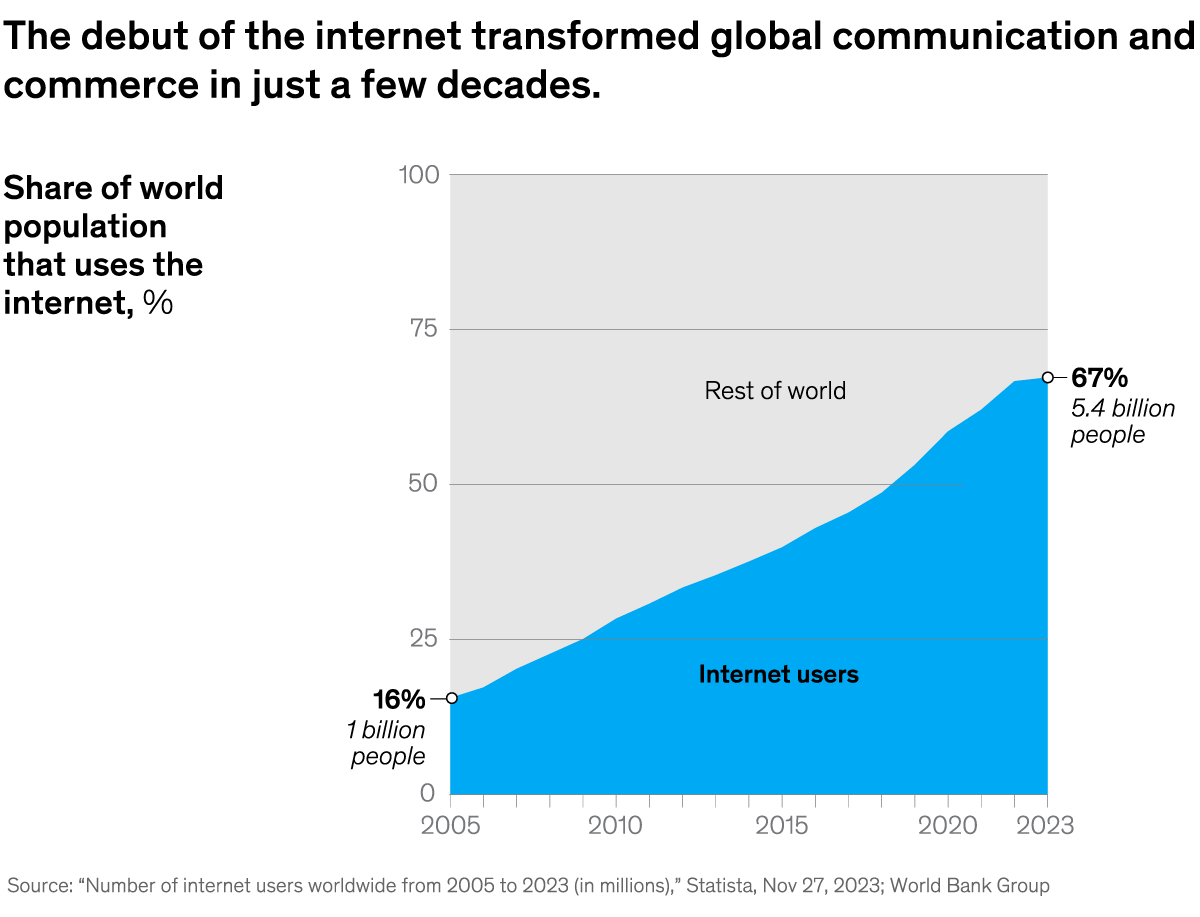
The internet’s broad reach, energy demand, and more Share these insights
Did you enjoy this newsletter? Forward it to colleagues and friends so they can subscribe too. Was this issue forwarded to you? Sign up for it and sample our 40+ other free email subscriptions here.
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to The Week in Charts newsletter.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Week in Charts" <publishing@email.mckinsey.com> - 03:47 - 21 Dec 2024 -
Is your entire company thinking like a marketer? It should be.
Marketing *is* the company Brought to you by Alex Panas, global leader of industries, & Axel Karlsson, global leader of functional practices and growth platforms
Welcome to the latest edition of McKinsey Classics. We hope you find our perspectives useful. Let us know what you think at Alex_Panas@McKinsey.com and Axel_Karlsson@McKinsey.com.
—Alex and Axel
December 2024
In honor of the 60th birthday of McKinsey Quarterly, the McKinsey Classics newsletter is dedicating a full year to enduring Quarterly articles that were ahead of their time. Enjoy, and check out other celebration highlights such as special themed issues and bonus digital features.
One thing is certain: you can never be too certain about consumer behavior. Where and how shoppers interact with a company’s product is always evolving. An organization’s marketing function should evolve as well. Even back in 2011, the authors of this McKinsey Quarterly classic observed that a successful marketing function can no longer rely on the traditional approach of disparate marketing efforts. Instead, marketers must engage effectively with customers across the entire consumer journey. And to achieve that, everyone in an organization needs to think like a marketer.
Ensuring that a company’s marketing function is firing on all cylinders across the entire organization involves four crucial dimensions: embed core marketing activities across multiple functions; establish marketing councils to help boost management coordination; prioritize the gathering of customer insights and behavior; and engage in comprehensive data analysis to act on new consumer data.
Today’s consumer environment is only getting more complex, and consumers themselves ever savvier. To learn how to meet the marketing moment, read our 2011 classic “We’re all marketers now.”Read our latest thinking on this classic topic
— Edited by Drew Holzfeind, editor, Chicago
Is there a classic business topic you’d like us to feature? Send us an email—we’d love to hear from you.
Share these insights
Did you enjoy this newsletter? Forward it to colleagues and friends so they can subscribe too. Was this issue forwarded to you? Sign up for it and sample our 40+ other free email subscriptions here.
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to our McKinsey Classics newsletter.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Classics" <publishing@email.mckinsey.com> - 12:12 - 21 Dec 2024 -
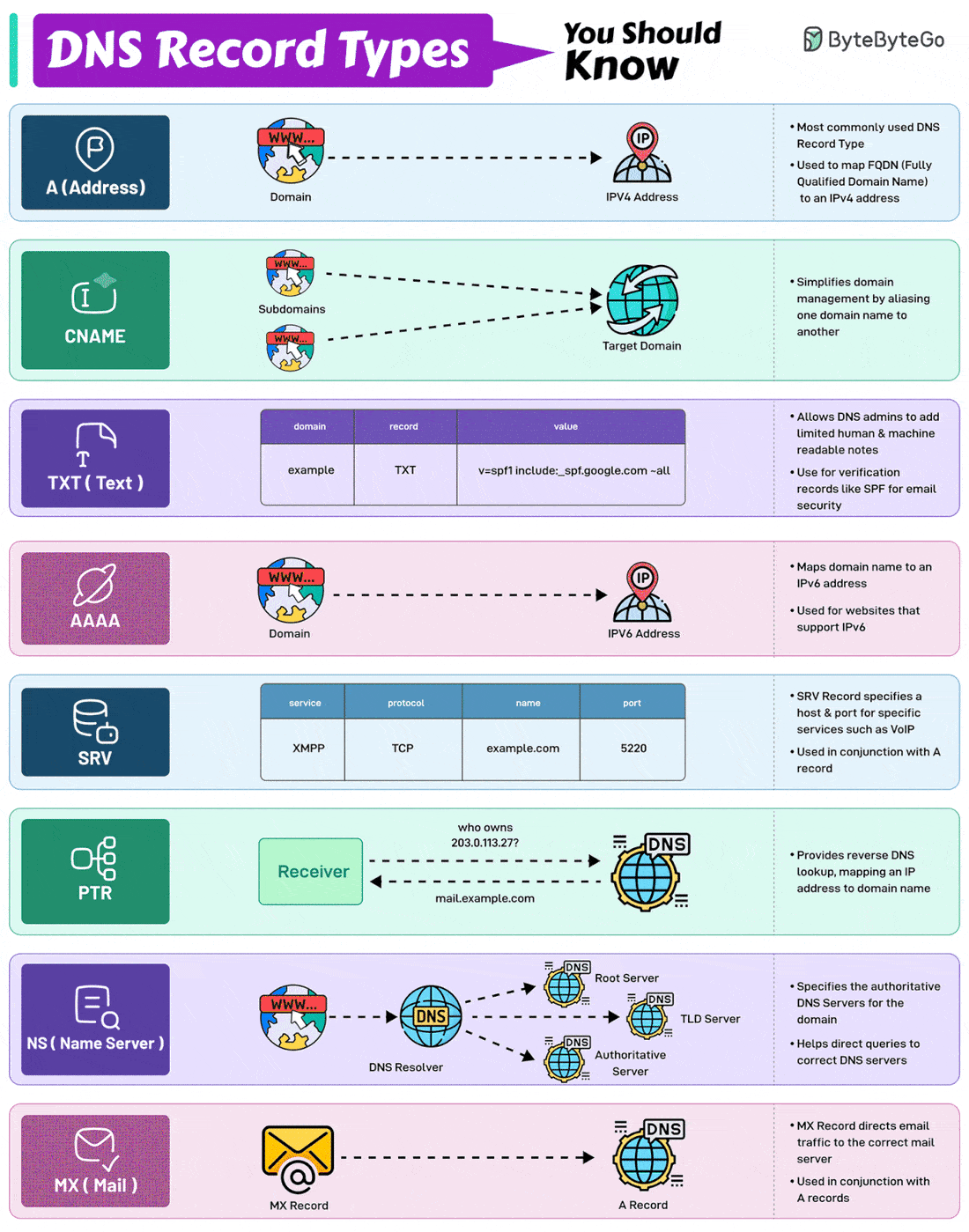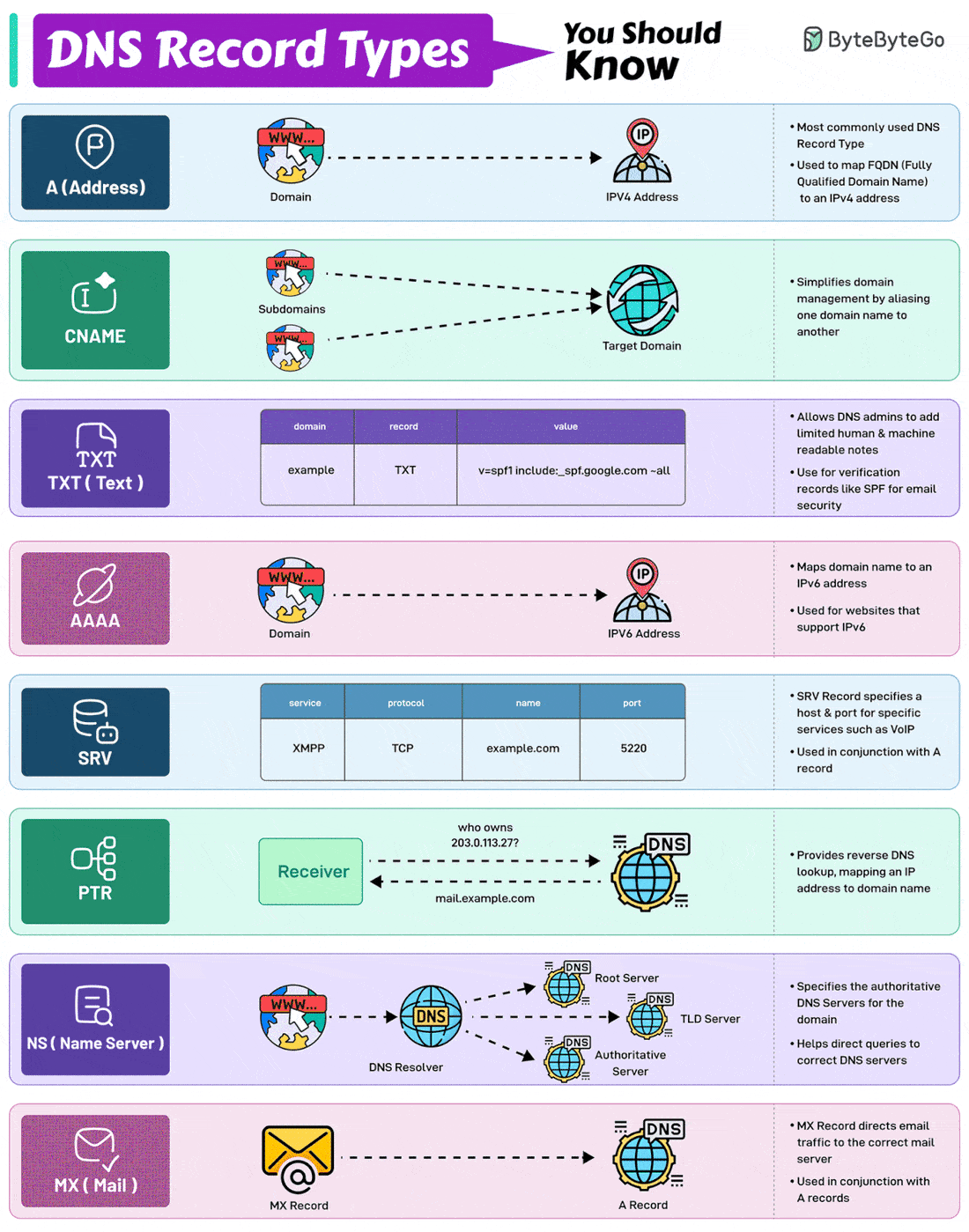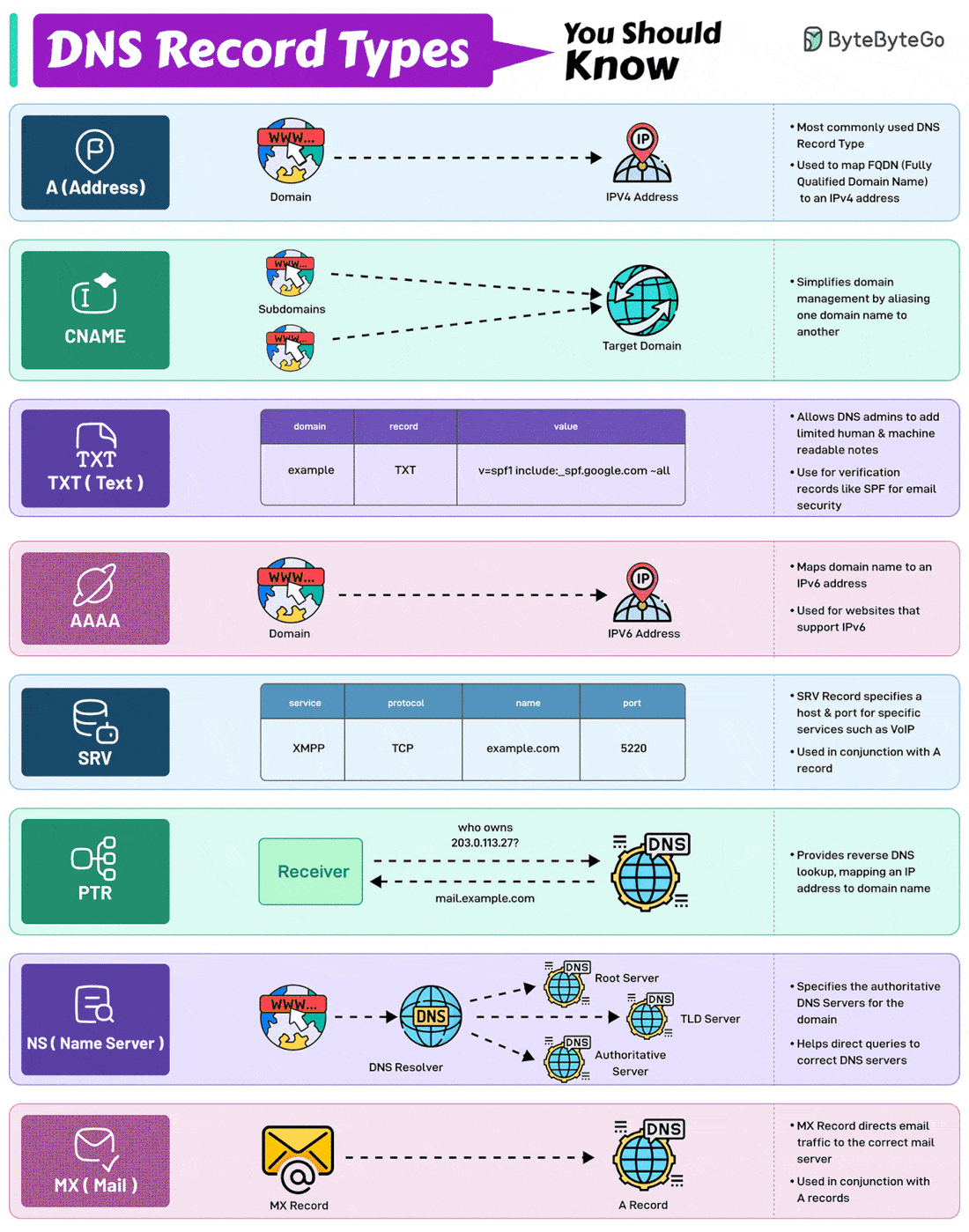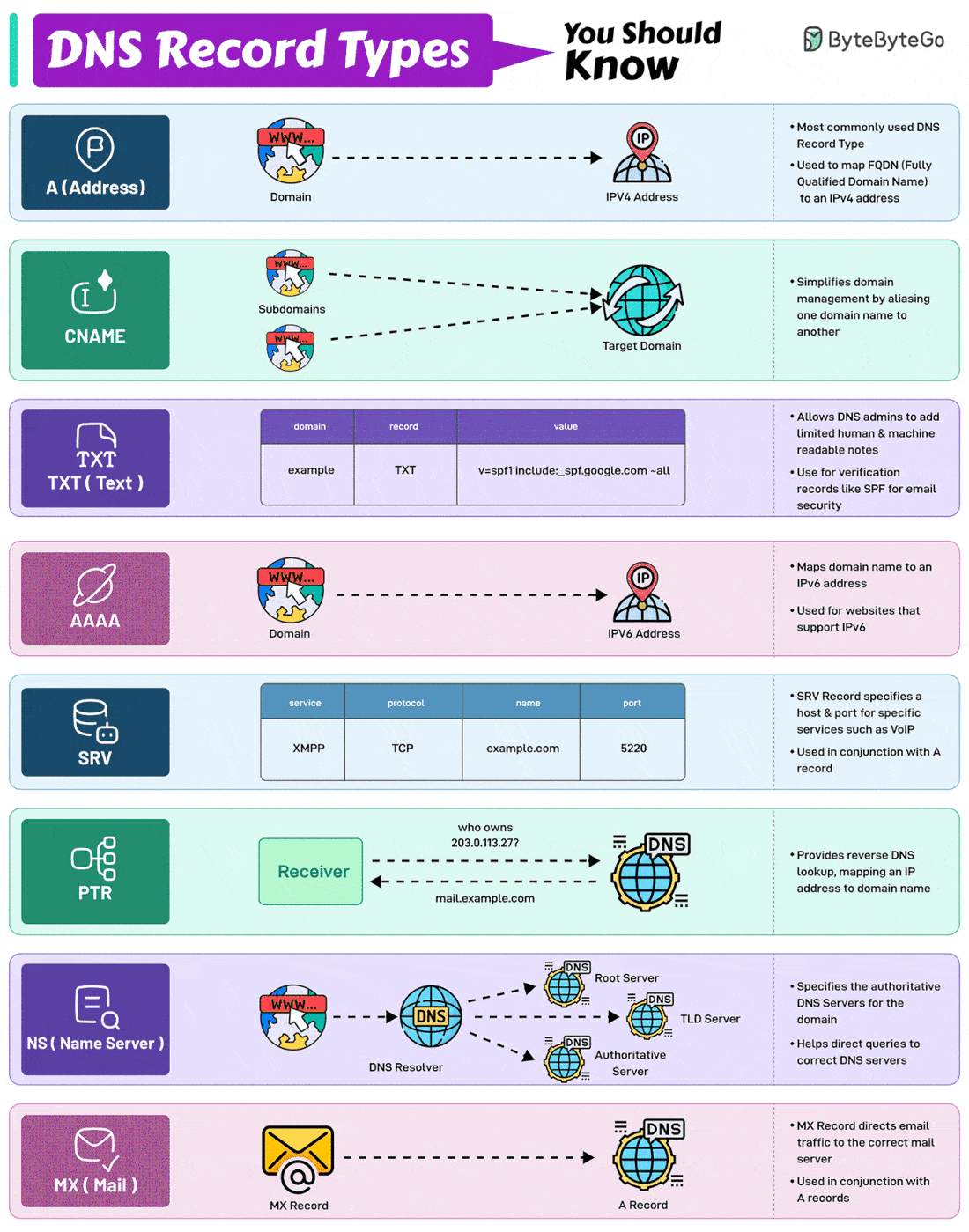
EP143: DNS Record Types You Should Know
EP143: DNS Record Types You Should Know
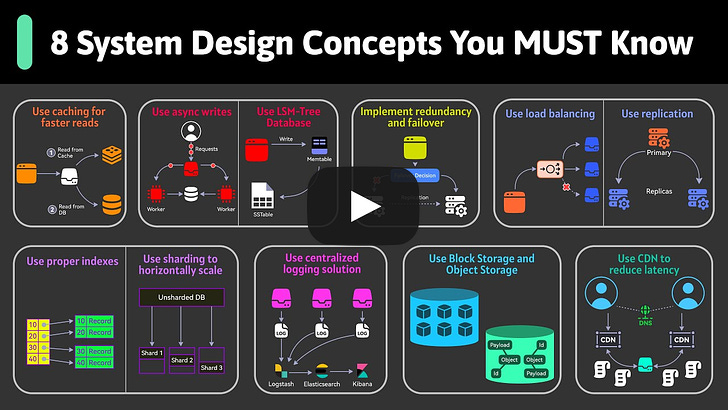
Here are the 8 most commonly used DNS Record Types.͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ Forwarded this email? Subscribe here for moreThis week’s system design refresher:
8 Most Important System Design Concepts You Should Know (Youtube Video)
DNS Record Types You Should Know
Polling Vs Webhooks
API Vs SDK!
How Netflix Really Uses Java?
Big O Notation 101: The Secret to Writing Efficient Algorithms
The Ultimate Kubernetes Command Cheatsheet
SPONSOR US
8 Most Important System Design Concepts You Should Know
DNS Record Types You Should Know!
Here are the 8 most commonly used DNS Record Types.
A (Address) Record
Maps a domain name to an IPv4 address. It is one of the most essential records for translating human-readable domain names into IP addresses.CNAME (Canonical Name) Record
Used to alias one domain name to another. Often used for subdomains, pointing them to the main domain while keeping the actual domain name hidden.AAAA Record
Similar to an A record but maps a domain name to an IPv6 address. They are used for websites and services that support the IPv6 protocol.PTR Record
Provides reverse DNS lookup, mapping an IP address back to a domain name. It is commonly used in verifying the authenticity of a server.MX Record
Directs email traffic to the correct mail server.NS (Name Server) Record
Specifies the authoritative DNS servers for the domain. These records help direct queries to the correct DNS servers for further lookups.SRV (Service) Record
SRV record specifies a host and port for specific services such as VoIP. They are used in conjunction with A records.TXT (Text) Record
Allows the administrator to add human-readable text to the DNS records. It is used to include verification records, like SPF, for email security.
Over to you: Which other DNS Record Type have you seen?
Polling Vs Webhooks
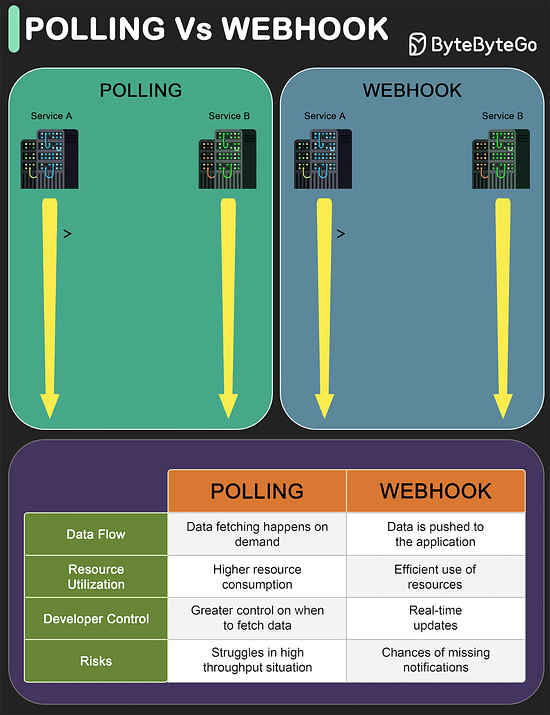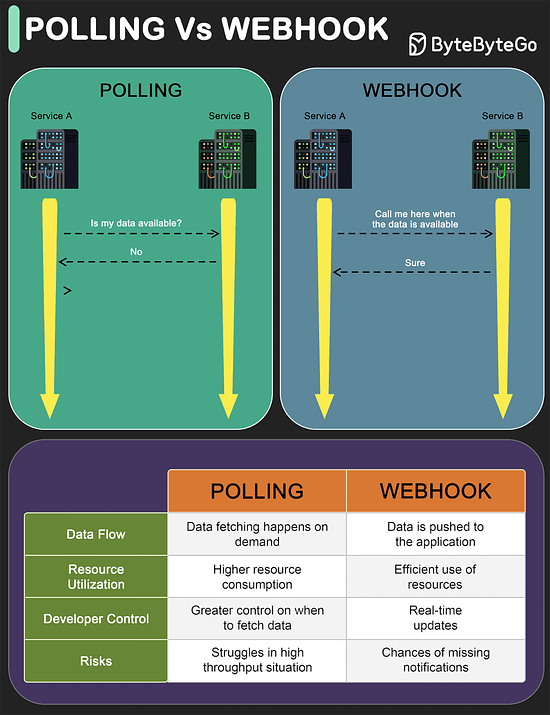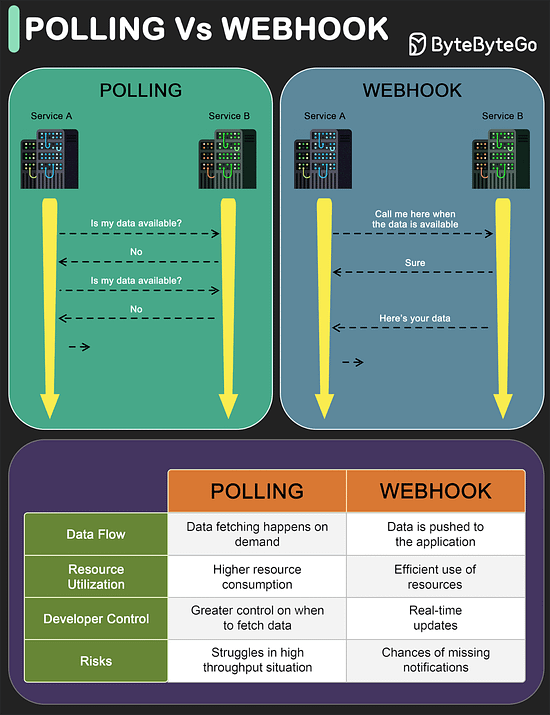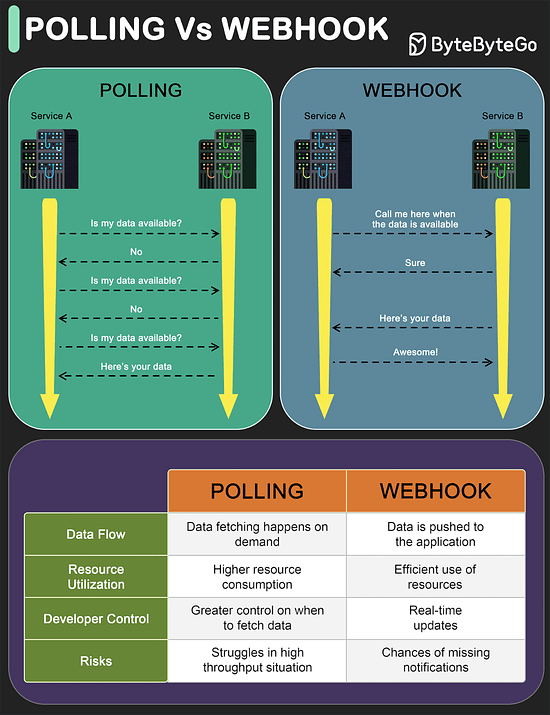
Polling
Polling involves repeatedly checking the external service or endpoint at fixed intervals to retrieve updated information.
It’s like constantly asking, “Do you have something new for me?” even where there might not be any update.
This approach is resource-intensive and inefficient.
Also, you get updates only when you ask for it, thereby missing any real-time information.
However, developers have more control over when and how the data is fetched.
Webhooks
Webhooks are like having a built-in notification system.
You don’t continuously ask for information.
Instead you create an endpoint in your application server and provide it as a callback to the external service (such as a payment processor or a shipping vendor)
Every time something interesting happens, the external service calls the endpoint and provides the information.
This makes webhooks ideal for dealing with real-time updates because data is pushed to your application as soon as it’s available.
So, when to use Polling or Webhook?
Polling is a solid option when there is some infrastructural limitation that prevents the use of webhooks. Also, with webhooks there is a risk of missed notifications due to network issues, hence proper retry mechanisms are needed.
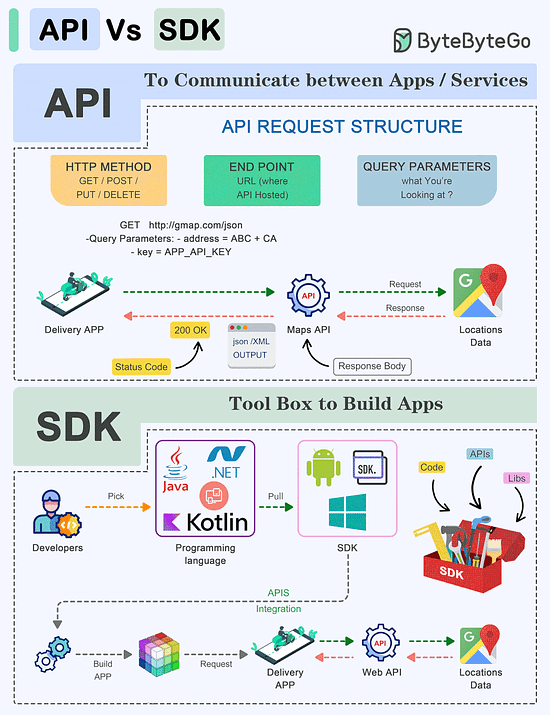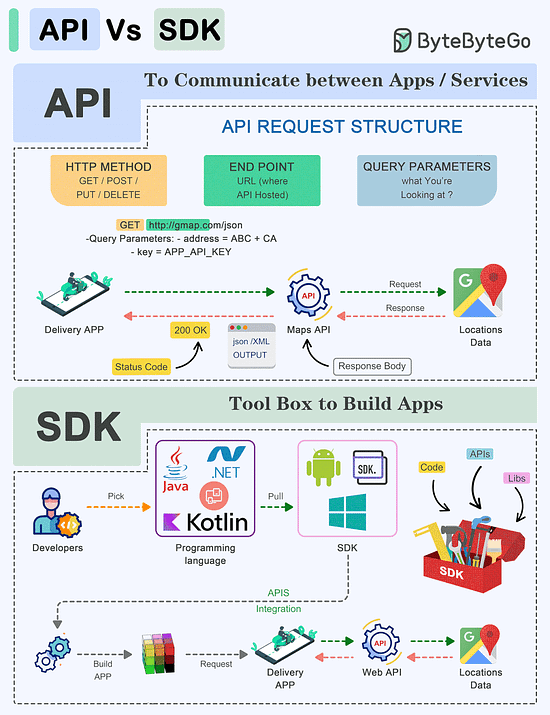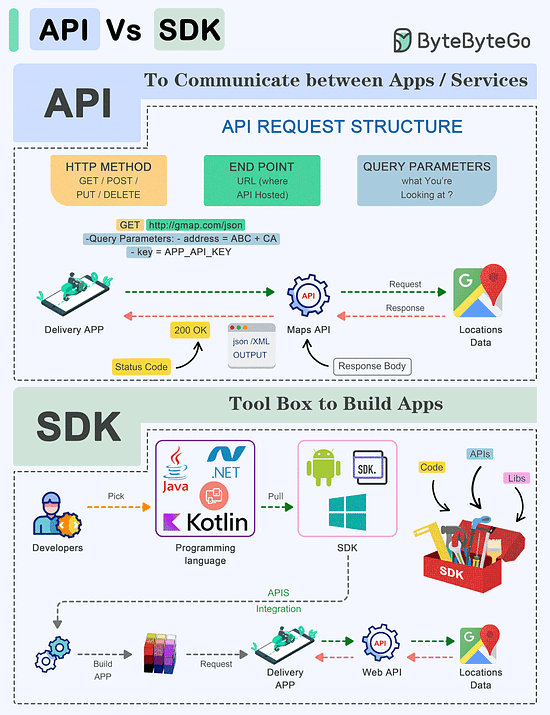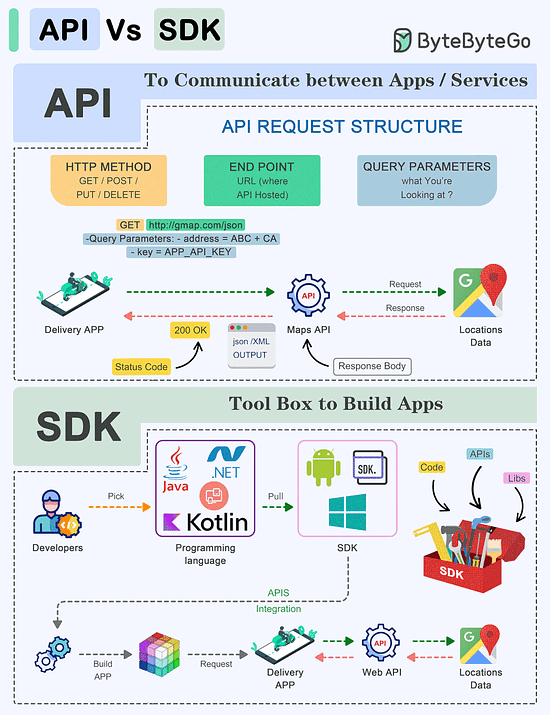
Webhooks are recommended for applications that need instant data delivery. Also, webhooks are efficient in terms of resource utilization especially in high throughput environments.API Vs SDK!
API (Application Programming Interface) and SDK (Software Development Kit) are essential tools in the software development world, but they serve distinct purposes:
API:
An API is a set of rules and protocols that allows different software applications and services to communicate with each other.It defines how software components should interact.
Facilitates data exchange and functionality access between software components.
Typically consists of endpoints, requests, and responses.
SDK:
An SDK is a comprehensive package of tools, libraries, sample code, and documentation that assists developers in building applications for a particular platform, framework, or hardware.Offers higher-level abstractions, simplifying development for a specific platform.
Tailored to specific platforms or frameworks, ensuring compatibility and optimal performance on that platform.
Offer access to advanced features and capabilities specific to the platform, which might be otherwise challenging to implement from scratch.
The choice between APIs and SDKs depends on the development goals and requirements of the project.
Over to you:
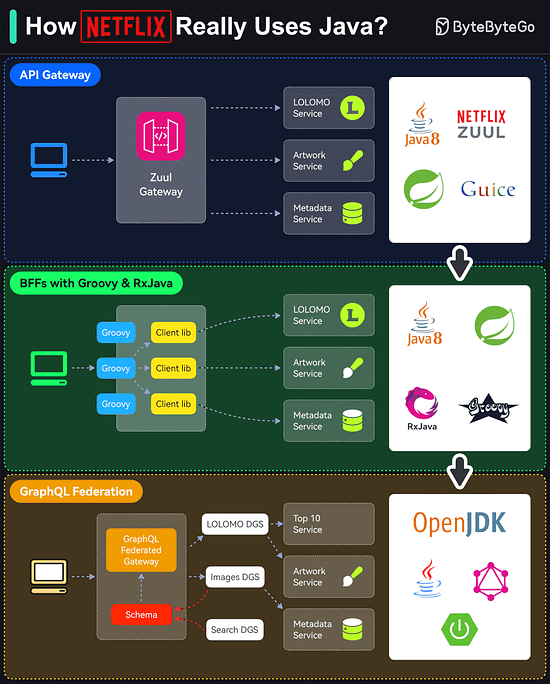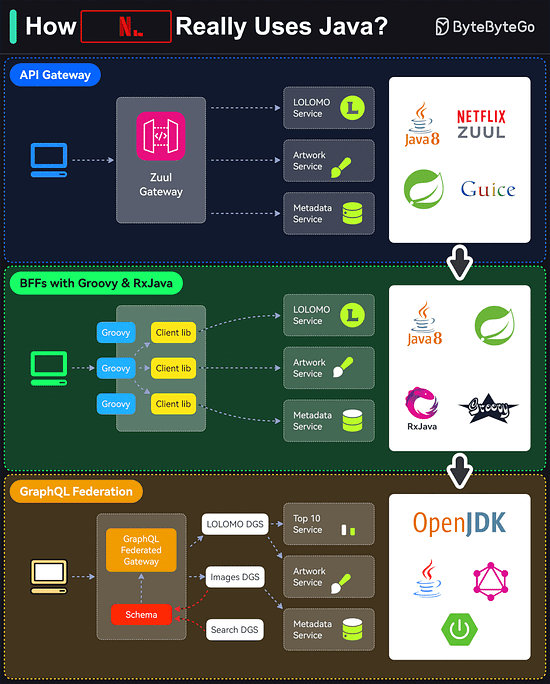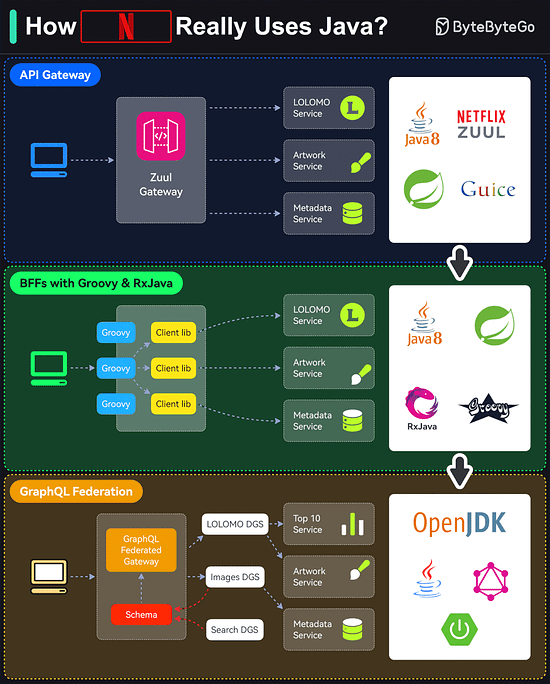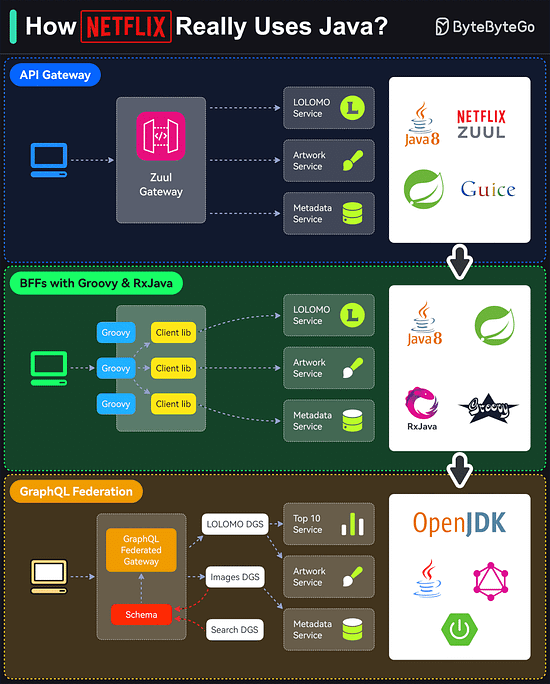
Which do you find yourself gravitating towards – APIs or SDKs – Every implementation has a unique story to tell. What's yours?How Netflix Really Uses Java?
Netflix is predominantly a Java shop.
Every backend application (including internal apps, streaming, and movie production apps) at Netflix is a Java application.
However, the Java stack is not static and has gone through multiple iterations over the years.
Here are the details of those iterations:API Gateway
Netflix follows a microservices architecture. Every piece of functionality and data is owned by a microservice built using Java (initially version 8)BFFs with Groovy & RxJava
Using a single gateway for multiple clients was a problem for Netflix because each client (such as TV, mobile apps, or web browser) had subtle differences.
To handle this, Netflix used the Backend-for-Frontend (BFF) pattern. Zuul was moved to the role of a proxyGraphQL Federation
The Groovy and RxJava approach required more work from the UI developers in creating the Groovy scripts. Also, reactive programming is generally hard.
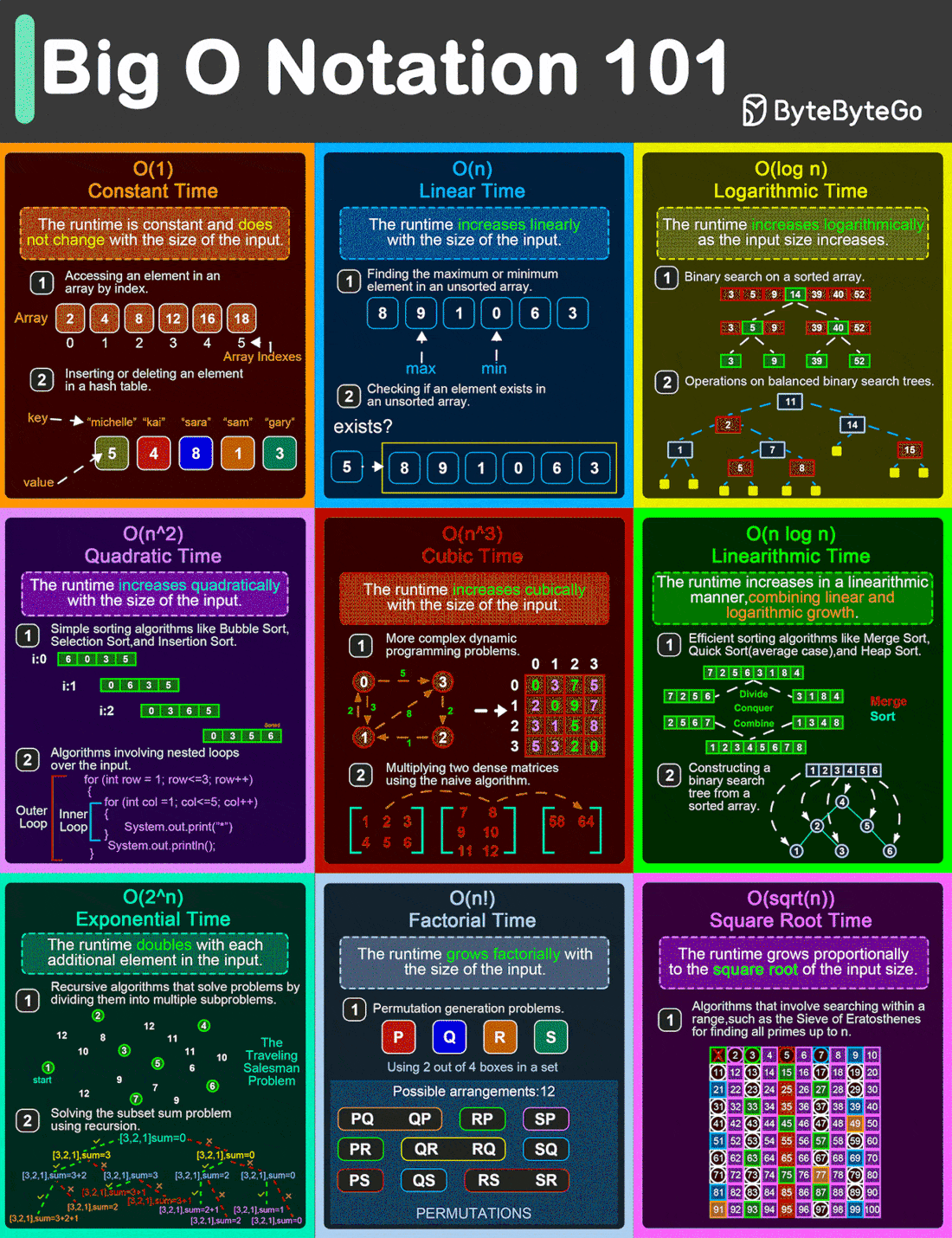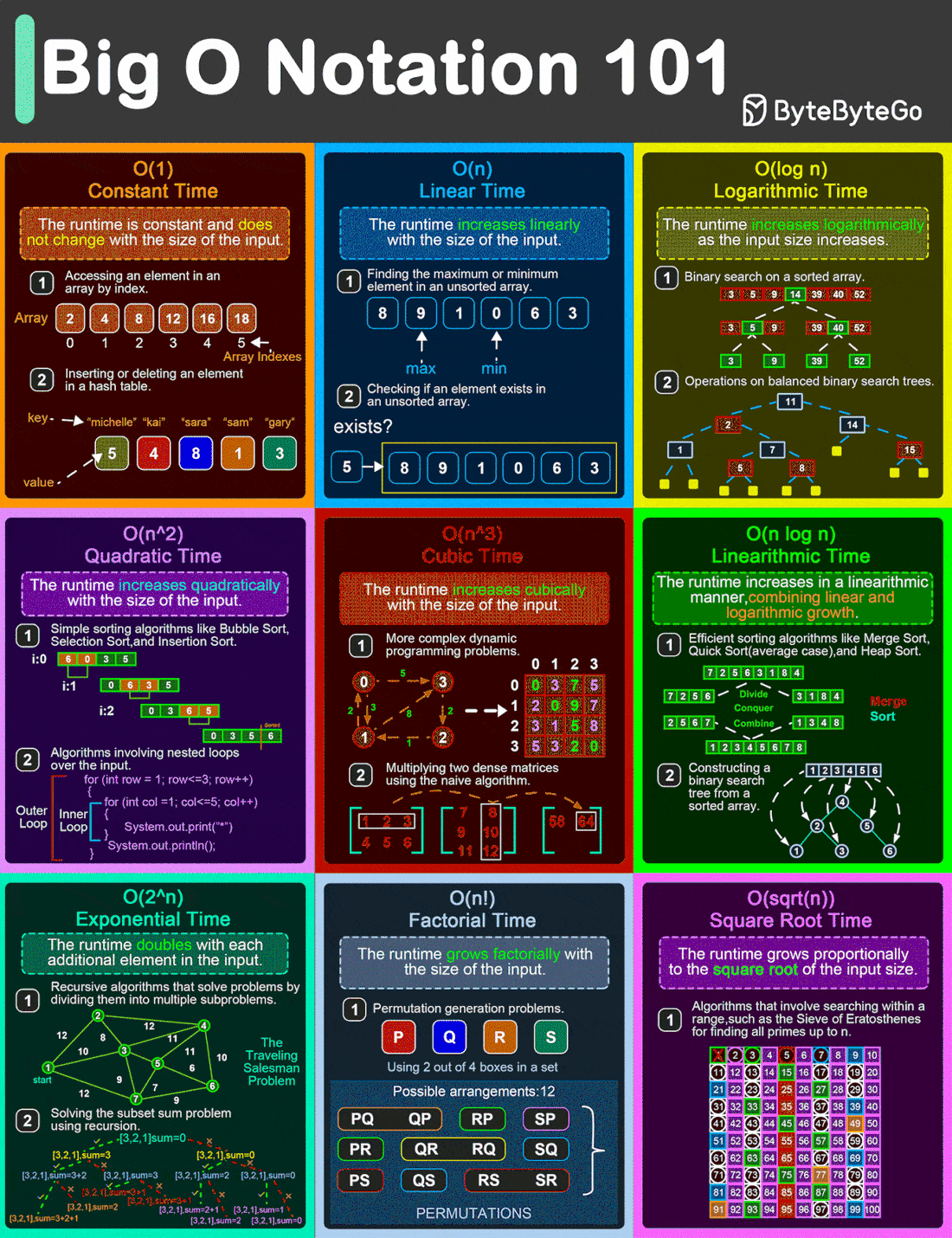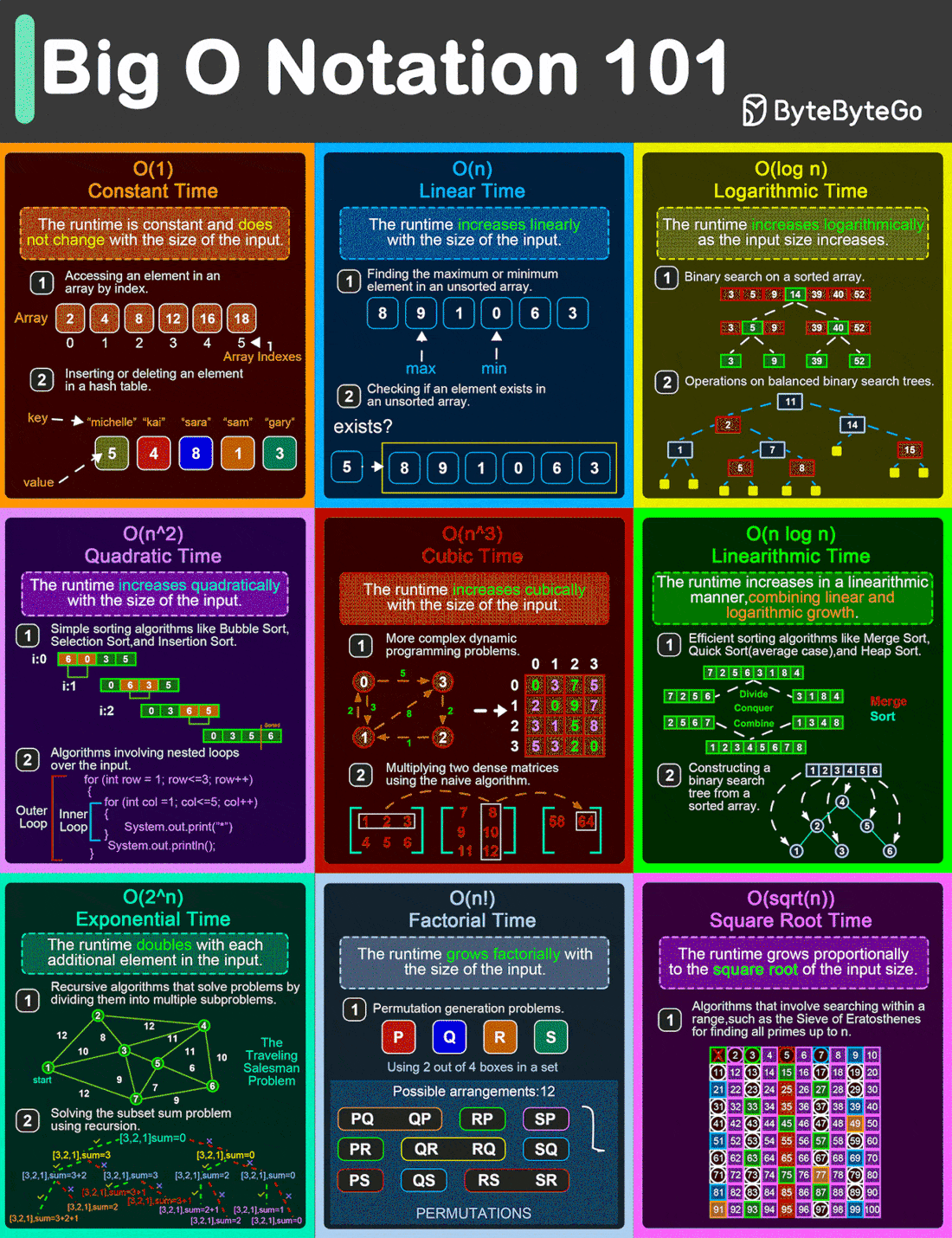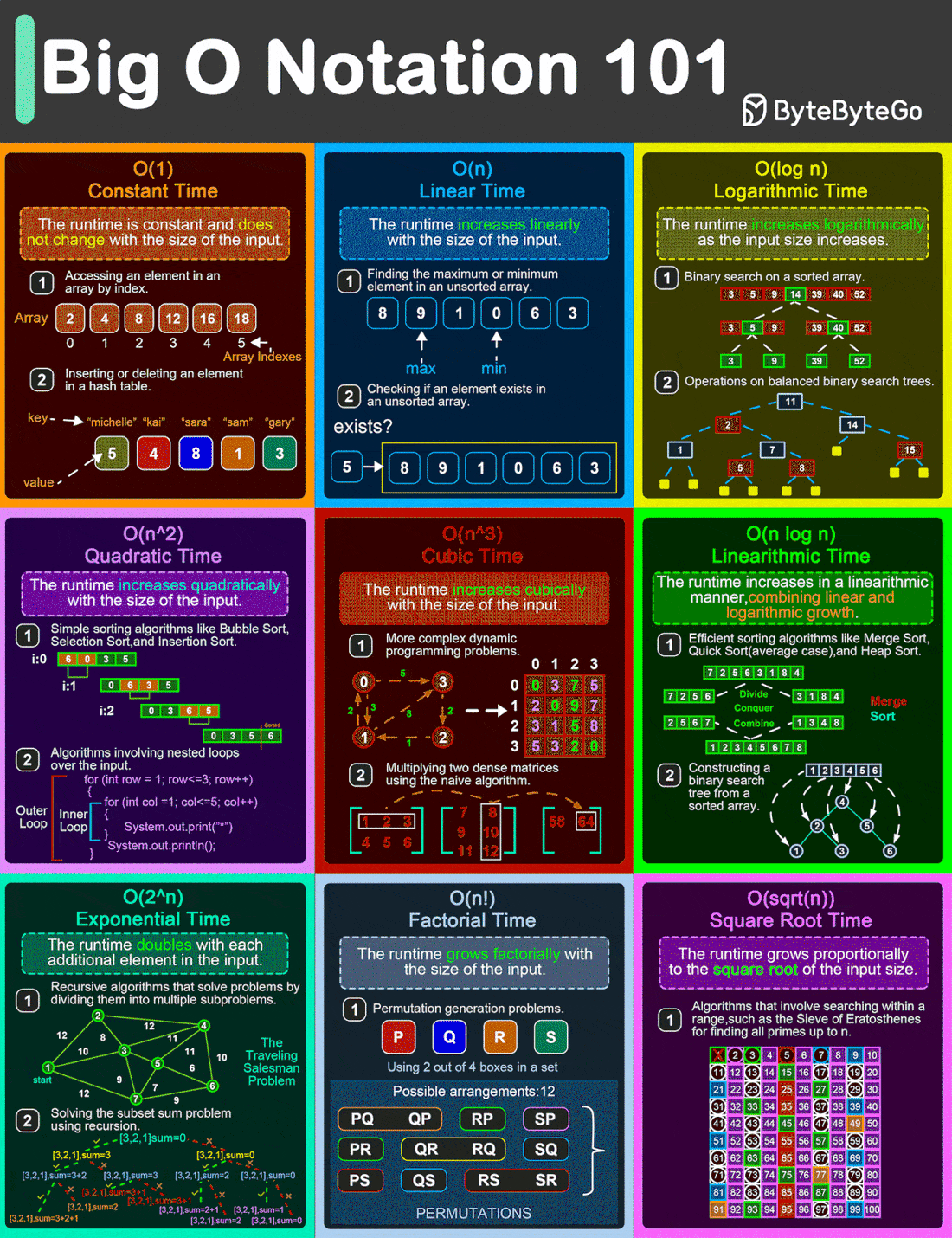
Big O Notation 101: The Secret to Writing Efficient Algorithms
From simple array operations to complex sorting algorithms, understanding the Big O Notation is critical for building high-performance software solutions.
O(1)
This is the constant time notation. The runtime remains steady regardless of input size. For example, accessing an element in an array by index and inserting/deleting an element in a hash table.O(n)
Linear time notation. The runtime grows in direct proportion to the input size. For example, finding the max or min element in an unsorted array.O(log n)
Logarithmic time notation. The runtime increases slowly as the input grows. For example, a binary search on a sorted array and operations on balanced binary search trees.O(n^2)
Quadratic time notation. The runtime grows exponentially with input size. For example, simple sorting algorithms like bubble sort, insertion sort, and selection sort.O(n^3)
Cubic time notation. The runtime escalates rapidly as the input size increases. For example, multiplying two dense matrices using the naive algorithm.O(n logn)
Linearithmic time notation. This is a blend of linear and logarithmic growth. For example, efficient sorting algorithms like merge sort, quick sort, and heap sortO(2^n)
Exponential time notation. The runtime doubles with each new input element. For example, recursive algorithms solve problems by dividing them into multiple subproblems.O(n!)
Factorial time notation. Runtime skyrockets with input size. For example, permutation-generation problems.O(sqrt(n))
Square root time notation. Runtime increases relative to the input’s square root. For example, searching within a range such as the Sieve of Eratosthenes for finding all primes up to n.
Over to you: What else will you add to better understand the Big O Notation?
The Ultimate Kubernetes Command Cheatsheet
Kubernetes is an open-source container orchestration platform. It automates the deployment, scaling, and management of containerized applications.
Initially developed by Google, Kubernetes is now maintained by CNCF (Cloud Native Computing Foundation).
This cheat sheet contains the most important Kubernetes commands for different purposes:Kubernetes Setup
General Cluster Management
Kubernetes Deployments
Kubernetes Pod Inspection
Troubleshooting and Configuration
Miscellaneous commands related to services, config maps, and managing ingresses.
Over to you: Which other Kubernetes command will you add to the list?
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com.
Like
Comment
Restack
© 2024 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe
by "ByteByteGo" <bytebytego@substack.com> - 12:08 - 21 Dec 2024 -
Introducing McKinsey’s Davos Daily: a limited-edition email series
Your guide to parsing today’s most critical global challenges New from McKinsey & Company
As next month’s World Economic Forum Annual Meeting approaches, we invite you to take advantage of our first-ever limited-run email series: McKinsey’s Davos Daily. This set of emails is available only for the duration of the conference and offers McKinsey expert insights to enhance your understanding of the year’s convening theme, which in 2025 is “Collaboration for the Intelligent Age.”
Each day you will receive a carefully curated roundup of McKinsey insights that delve into the core priorities of the conference. Series topics this year include AI transformation, geopolitics, space, 21st-century leadership, and more. Here’s what you can expect next month:•
Day 1: A forward-looking pre-conference bundle to set the stage
•
Days 2-7: A daily roundup of articles and reports on the conference’s main themes
•
Day 8: Takeaways and reflections
Sign up in one click to receive this free, limited-run series that dives deep into the themes of the Annual Meeting to help you parse today’s most critical global challenges.
This email contains information about McKinsey’s research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you are a registered member of mckinsey.com.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey & Company" <publishing@email.mckinsey.com> - 04:18 - 20 Dec 2024 -
The future of wellness
Only McKinsey Perspectives
To your health Brought to you by Alex Panas, global leader of industries, & Axel Karlsson, global leader of functional practices and growth platforms
Welcome to the latest edition of Only McKinsey Perspectives. We hope you find our insights useful. Let us know what you think at Alex_Panas@McKinsey.com and Axel_Karlsson@McKinsey.com.
—Alex and Axel
•
Prioritizing health. The business of health is thriving. McKinsey’s latest Future of Wellness research, which surveyed more than 5,000 consumers in China, the UK, and the US, finds that the global consumer wellness market is generating $1.8 trillion per year. For McKinsey partner Anna Pione, the fact that consumers are increasingly concentrating on their health is a given. However, “[w]hat surprised us and continues to surprise us every year is how much of a priority it is,” Pione remarks.
—Edited by Belinda Yu, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to the Only McKinsey Perspectives newsletter, formerly known as Only McKinsey.
Copyright © 2024 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey Perspectives" <publishing@email.mckinsey.com> - 01:19 - 20 Dec 2024 -
🎉 Cheers to a Bright New Year with Remote!
🎉 Cheers to a Bright New Year with Remote!
Your monthly global update from Remote has landed, check it out!.png?width=204&upscale=true&name=Logo%20Horizontal%20(3).png)

Featured news
Happy Holidays from all of us at Remote 🎄

As the holiday season approaches, we want to take a moment to express our heartfelt gratitude for being a part of our community. 2024 was a big year for Remote, and we couldn't have done it without your support and trust.
Here's to a wonderful season and an even brighter new year ahead! Keep your eyes peeled for big things coming in 2025 👀

Featured blogs
Maximize Your End-of-Year Planning
With the year winding down, it's time to align your goals and set your team up for success. Discover actionable strategies to make the most of year-end planning and start the next year strong.
What’s Next for US Labor Policy?
From workplace trends to shifting regulations, staying ahead of labor policy changes is critical. Explore our forecast for what US labor policy changes could mean for businesses in 2024.

Upcoming events
Join Remote at HR Technologies France
Join Remote at HR technologies France at Paris Exhibition Center, Porte de Versailles, on January 29 and 30th for the first HRtech and EdTech tradeshow of the year. The Remote team will welcome you at booth L41 to discuss your international employment needs and discuss how to quickly recruit, pay, and manage teams anywhere in any currency using our unique HR platform.

On-demand webinar
Watch Now: From Complexity to Simplicity – Managing Global Benefits
Discover how our integrated platform streamlines global benefits and payroll. Watch our on-demand webinar, From Complexity to Simplicity, and transform the way you support your employees.
The HR platform for global businesses
Remote makes running global teams simple. Hire, manage, and pay anyone, anywhere. Book a personal consultation with an expert to discuss your unique HR needs.







You received this email because you are subscribed to
News & Offers from Remote Europe Holding B.V
Update your email preferences to choose the types of emails you receive.
Unsubscribe from all future emailsRemote Europe Holding B.V
Copyright © 2024 Remote Europe Holding B.V All rights reserved.
Kraijenhoffstraat 137A 1018RG Amsterdam The Netherlands
by "Remote" <hello@remote-comms.com> - 07:43 - 19 Dec 2024 -
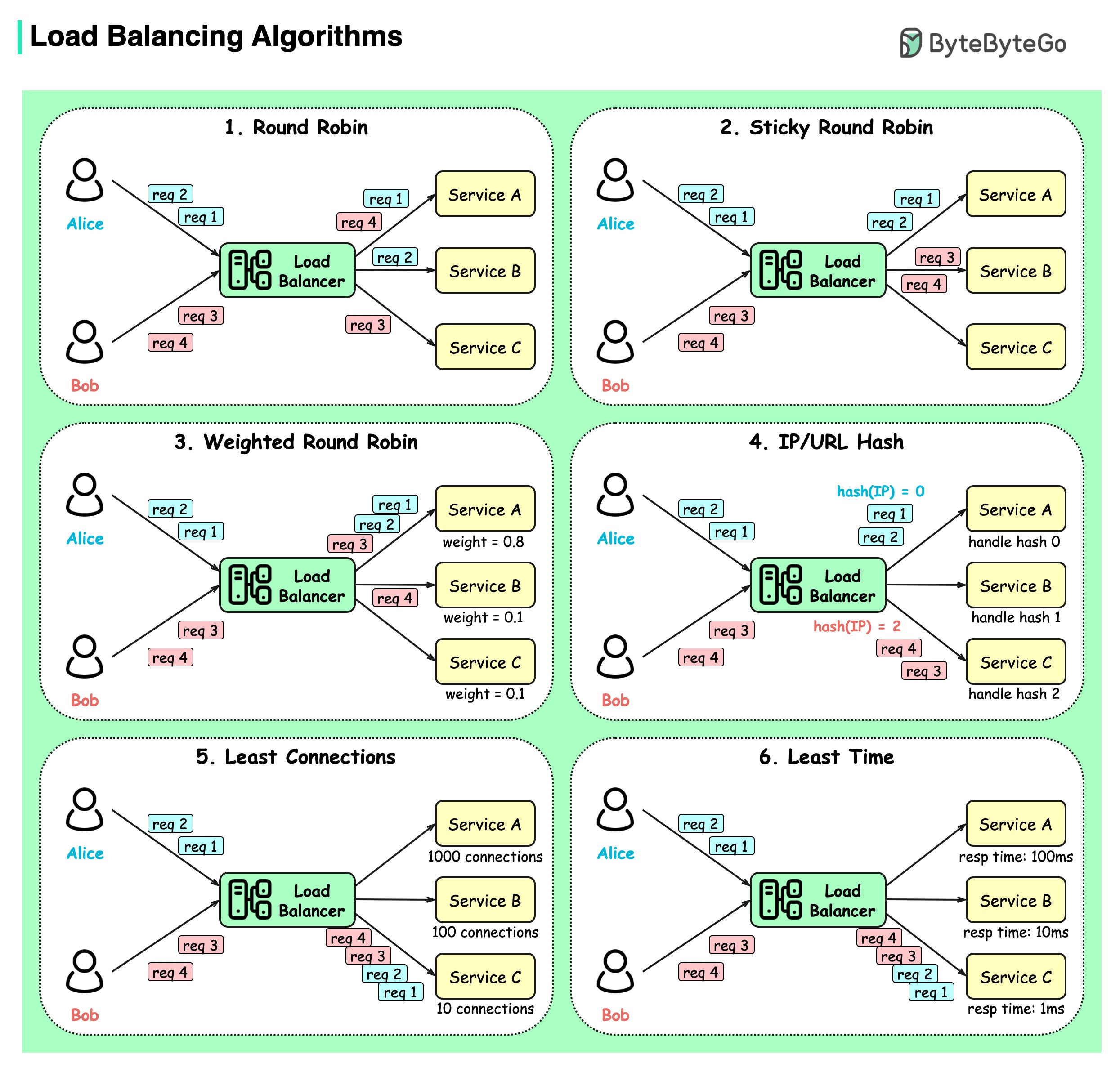
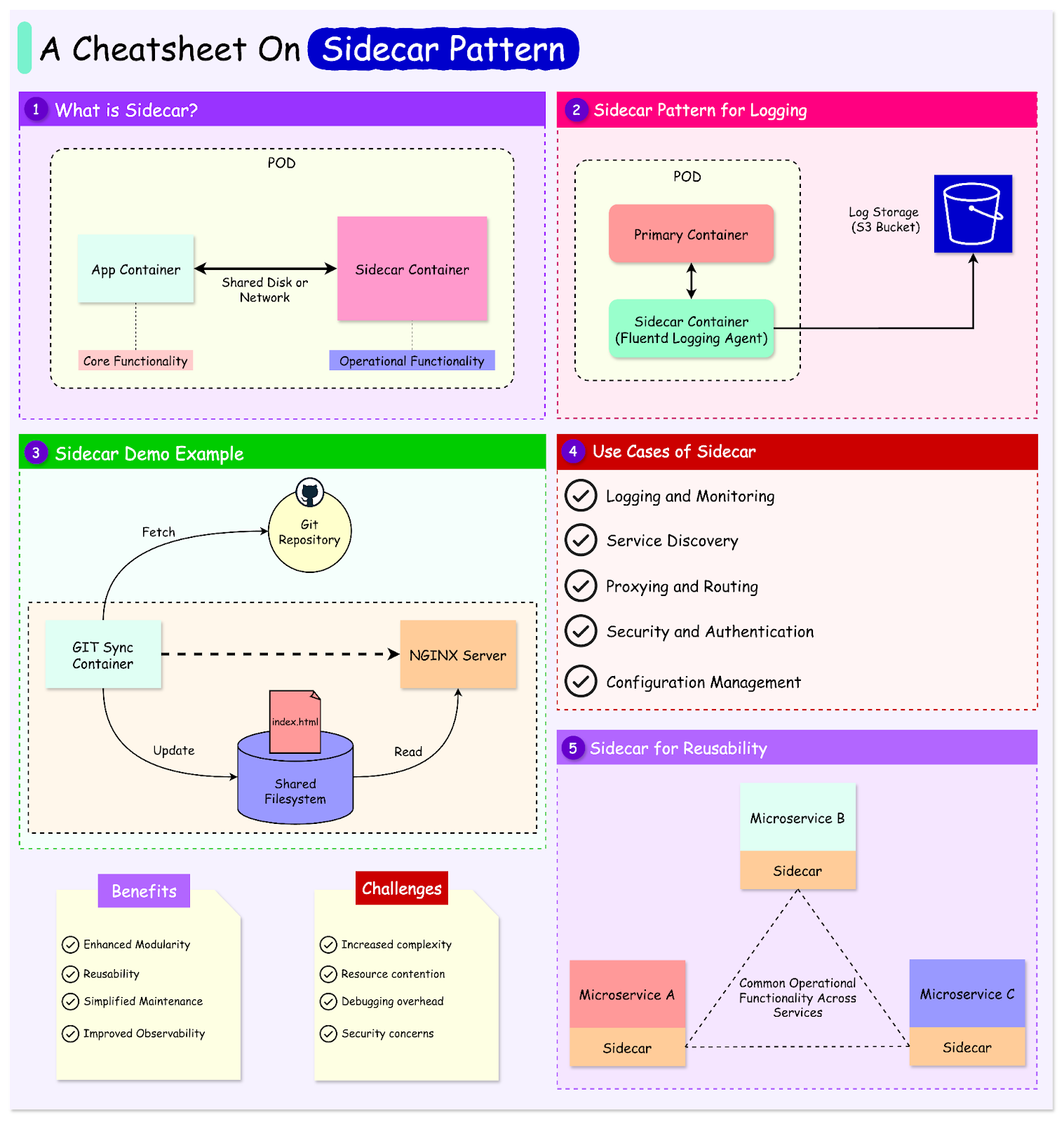
The Sidecar Pattern Explained: Decoupling Operational Features
The Sidecar Pattern Explained: Decoupling Operational Features
Design patterns are reusable solutions to common problems in software design.͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ Forwarded this email? Subscribe here for moreLatest articles
If you’re not a subscriber, here’s what you missed this month.
Database Performance Demystified: Essential Tips and Strategies
Mastering Modern Authentication: Cookies, Sessions, JWT, and PASETO
Stateless Architecture: The Key to Building Scalable and Resilient Systems
Distributed Caching: The Secret to High-Performance Applications
To receive all the full articles and support ByteByteGo, consider subscribing:
Design patterns are reusable solutions to common problems in software design. They provide a structured approach to solving architectural challenges without reinventing the wheel each time.
The sidecar pattern is one such design pattern that has gained prominence in modern software engineering.
At its core, the sidecar pattern pairs a secondary process or service (the "sidecar") with a primary application to handle complementary tasks. These tasks include logging, monitoring, proxying, security, or configuration management. The sidecar runs alongside the main application, sharing the same host or container, but remains logically and operationally independent.
The sidecar pattern can be compared to a motorcycle with a sidecar. The motorcycle (the primary service) is the main driver, responsible for the core functionality, like transporting a person. The sidecar (the auxiliary service) carries additional tools or passengers, assisting the main vehicle without interfering with its operation.
Similarly, in software systems, the sidecar extends the capabilities of the primary application without being tightly coupled to it.
In this article, we’ll learn about the sidecar pattern in detail and understand how it works. In the end, we will also look at its benefits and challenges that can help us make better decisions when using the pattern.

Continue reading this post for free in the Substack app
Like
Comment
Restack
© 2024 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe
by "ByteByteGo" <bytebytego@substack.com> - 11:36 - 19 Dec 2024








































.png?width=300&upscale=true&name=image(2).png)
.png?width=300&upscale=true&name=image(3).png)