- Mailing Lists
- in
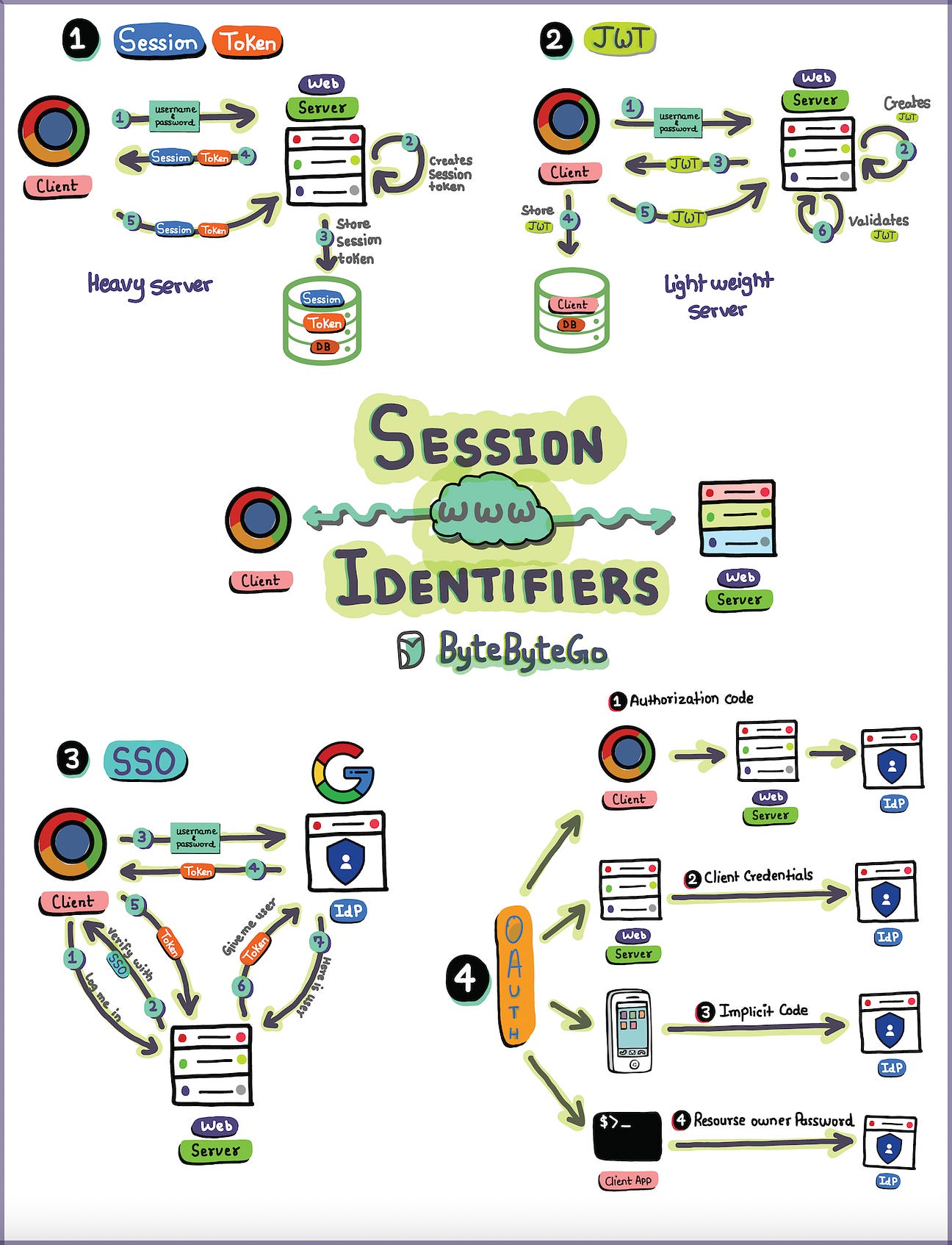
- Sessions, Tokens, JWT, SSO, and OAuth in One Diagram
Archives
- By thread 5359
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 172
Sessions, Tokens, JWT, SSO, and OAuth in One Diagram
Sessions, Tokens, JWT, SSO, and OAuth in One Diagram
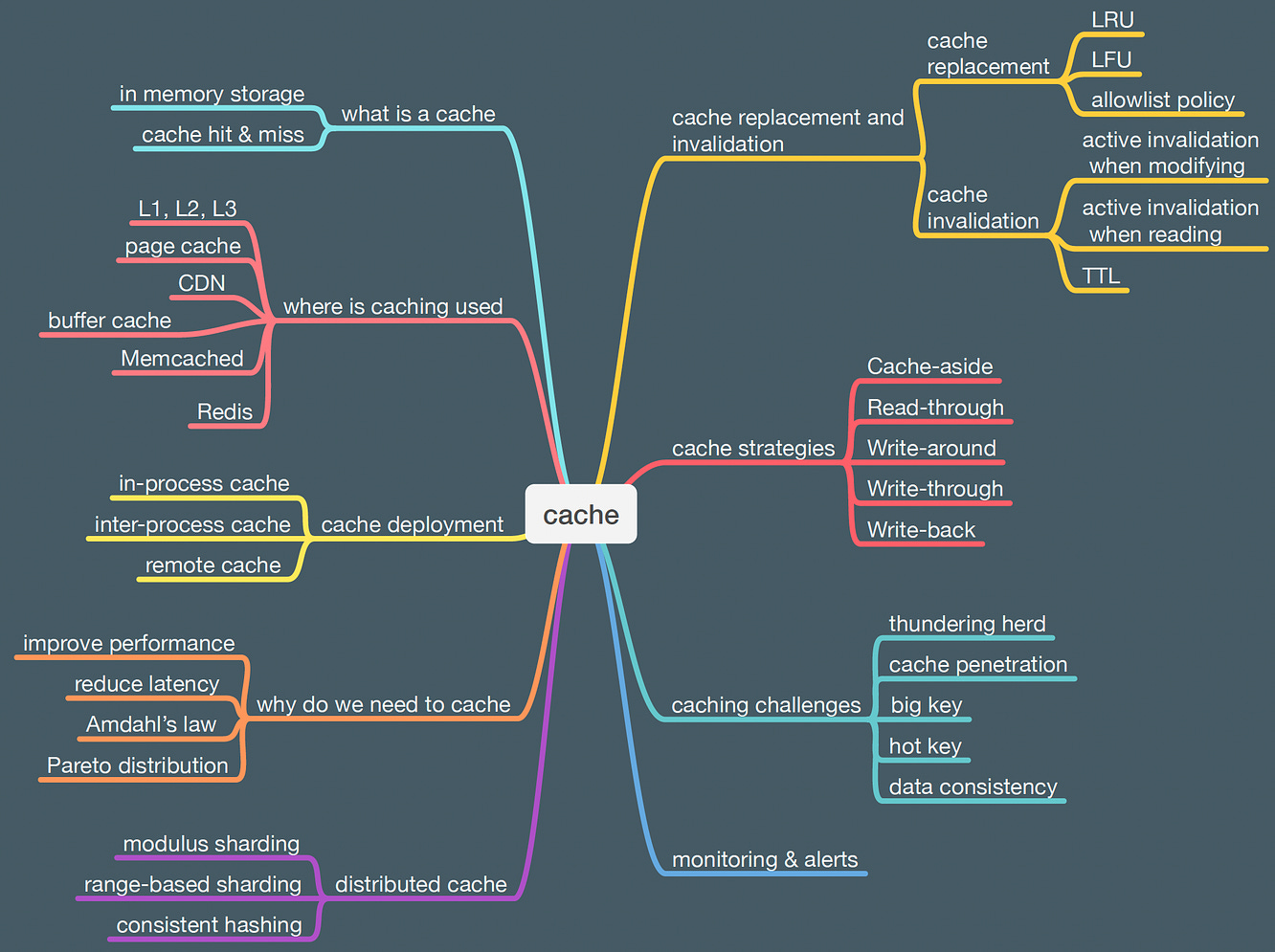
This week’s system design refresher:
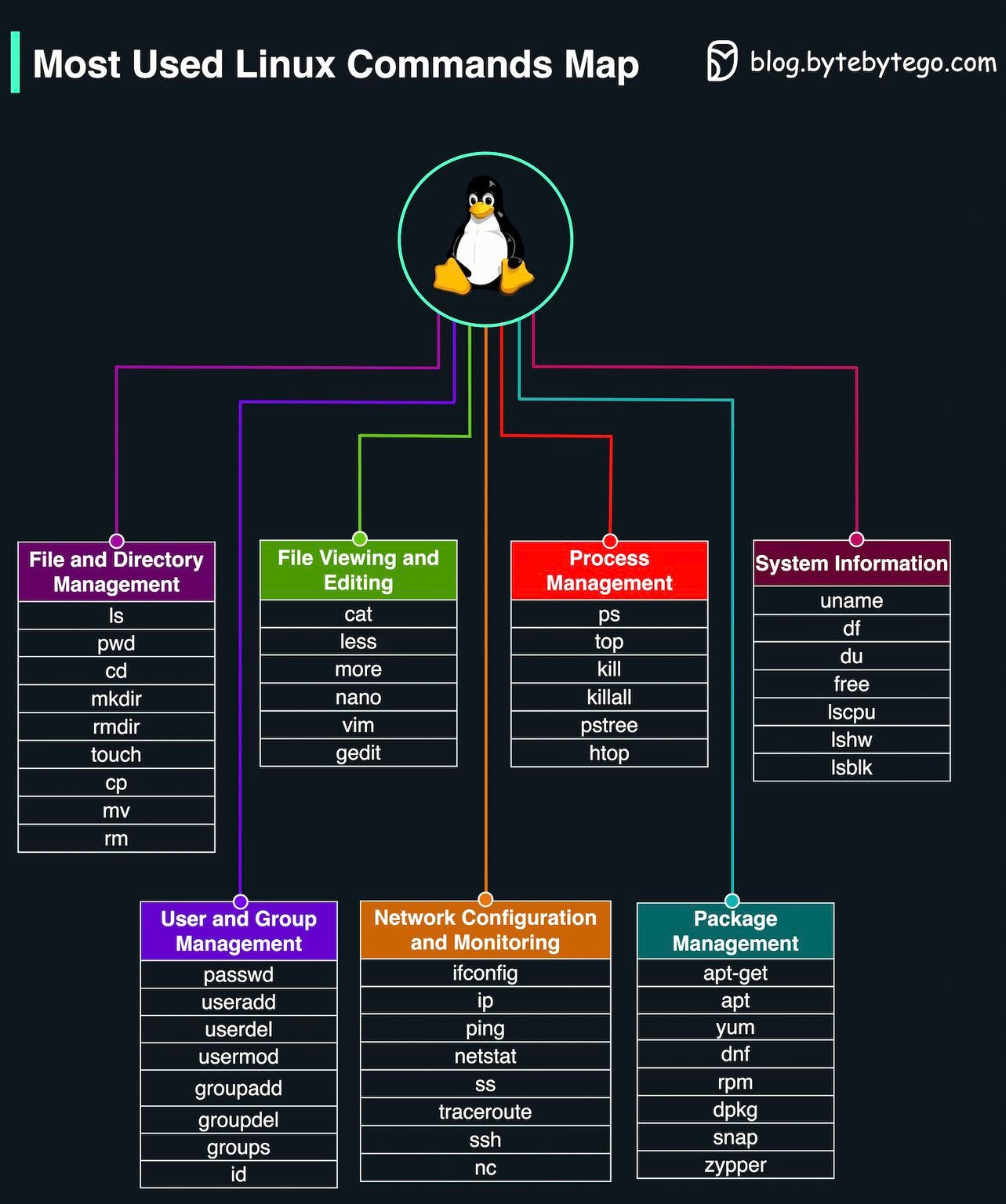
Free tickets to P99 CONF - 60+ low-latency engineering talks (Sponsored)P99 CONF is the technical conference for anyone who obsesses over high-performance, low-latency applications. Engineers from Netflix, Google, Meta, Twitter, TikTok, Uber + more will be sharing 60+ talks on topics like Rust, Go, Zig, distributed data systems, Kubernetes, edge, and AI/ML. Join 15K of your peers for an unprecedented opportunity to learn from experts like Gwen Shapira, Bryan Cantrill, Jens Axboe, Avi Kivity, Jon Haddad, Armin Ronacher, Liz Rice & more – for free, from anywhere. Bonus: Registrants are eligible to win 500 free swag packs and get 30-day access to the complete O’Reilly library & learning platform, plus free digital books. Software Engineer Promo is SUPER easy - DO THIS Explaining Sessions, Tokens, JWT, SSO, and OAuth in One DiagramUnderstanding these backstage maneuvers helps us build secure, seamless experiences. How do you see the evolution of web session management impacting the future of web applications and user experiences? Latest articlesIf you’re not a subscriber, here’s what you missed this month. To receive all the full articles and support ByteByteGo, consider subscribing: Most Used Linux Commands Map
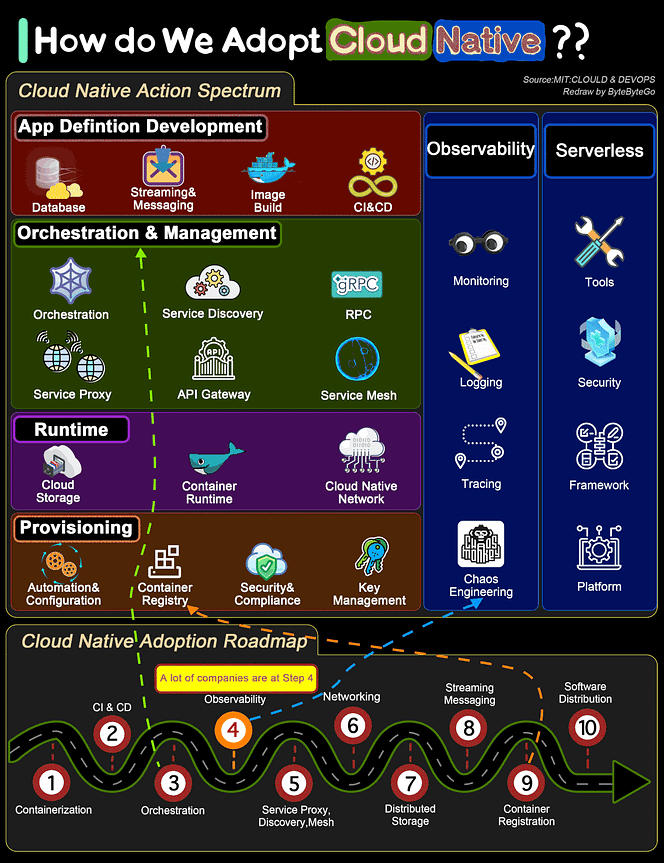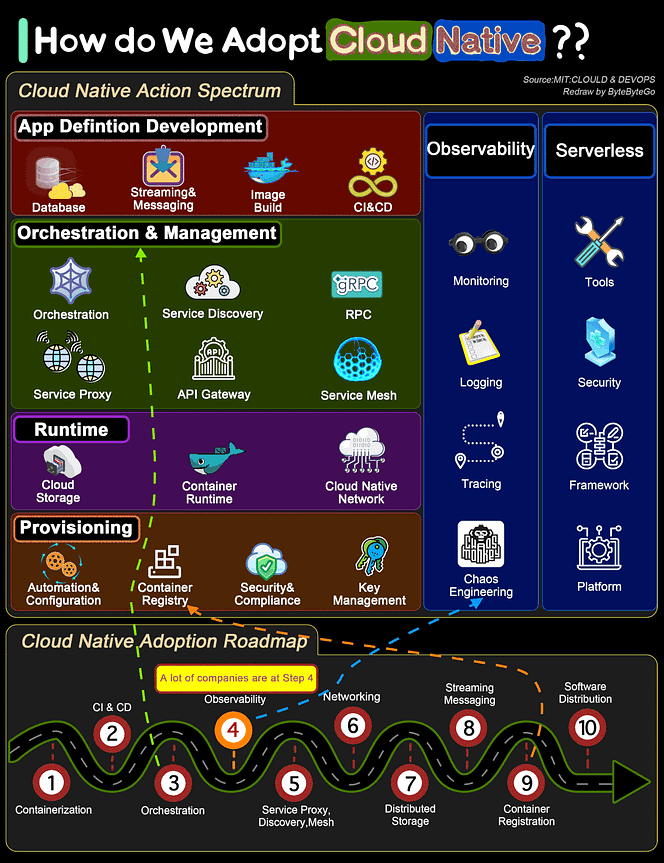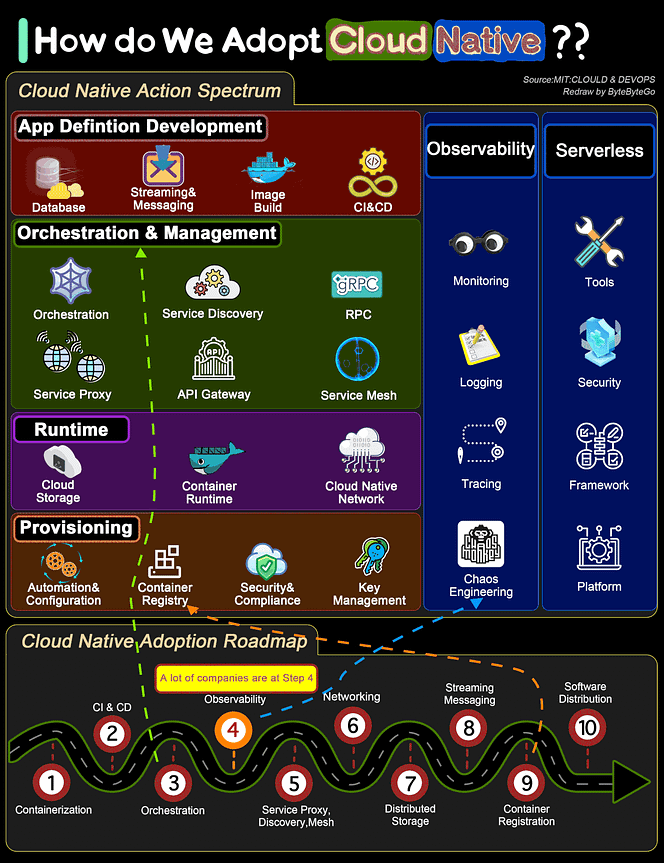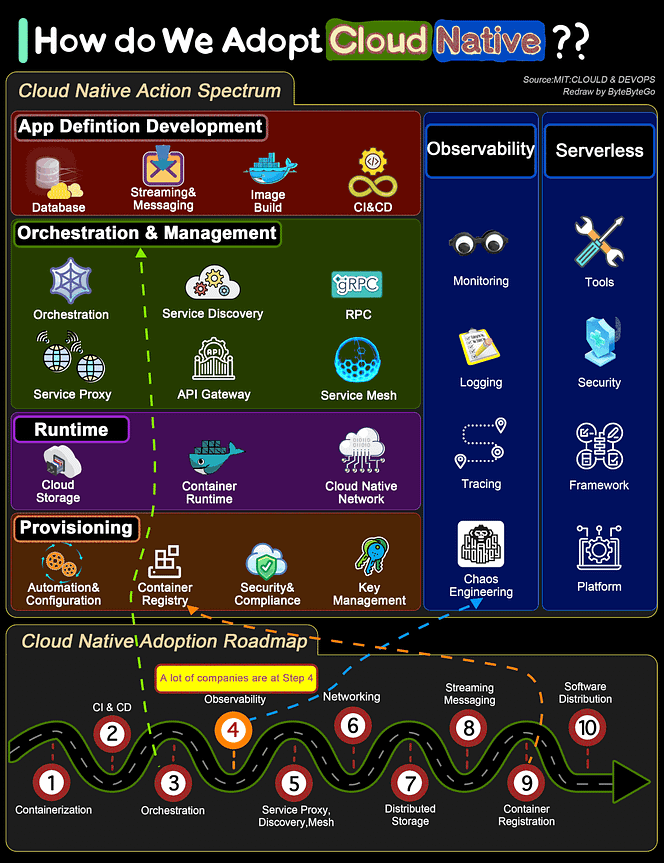
Over to you: Which command category did you use the most in your daily Linux tasks? Guest post by Govardhana Miriyala Kannaiah How do we transform a system to be Cloud Native?The diagram below shows the action spectrum and adoption roadmap. You can use it as a blueprint for adopting cloud-native in your organization. For a company to adopt cloud native architecture, there are 6 aspects in the spectrum:
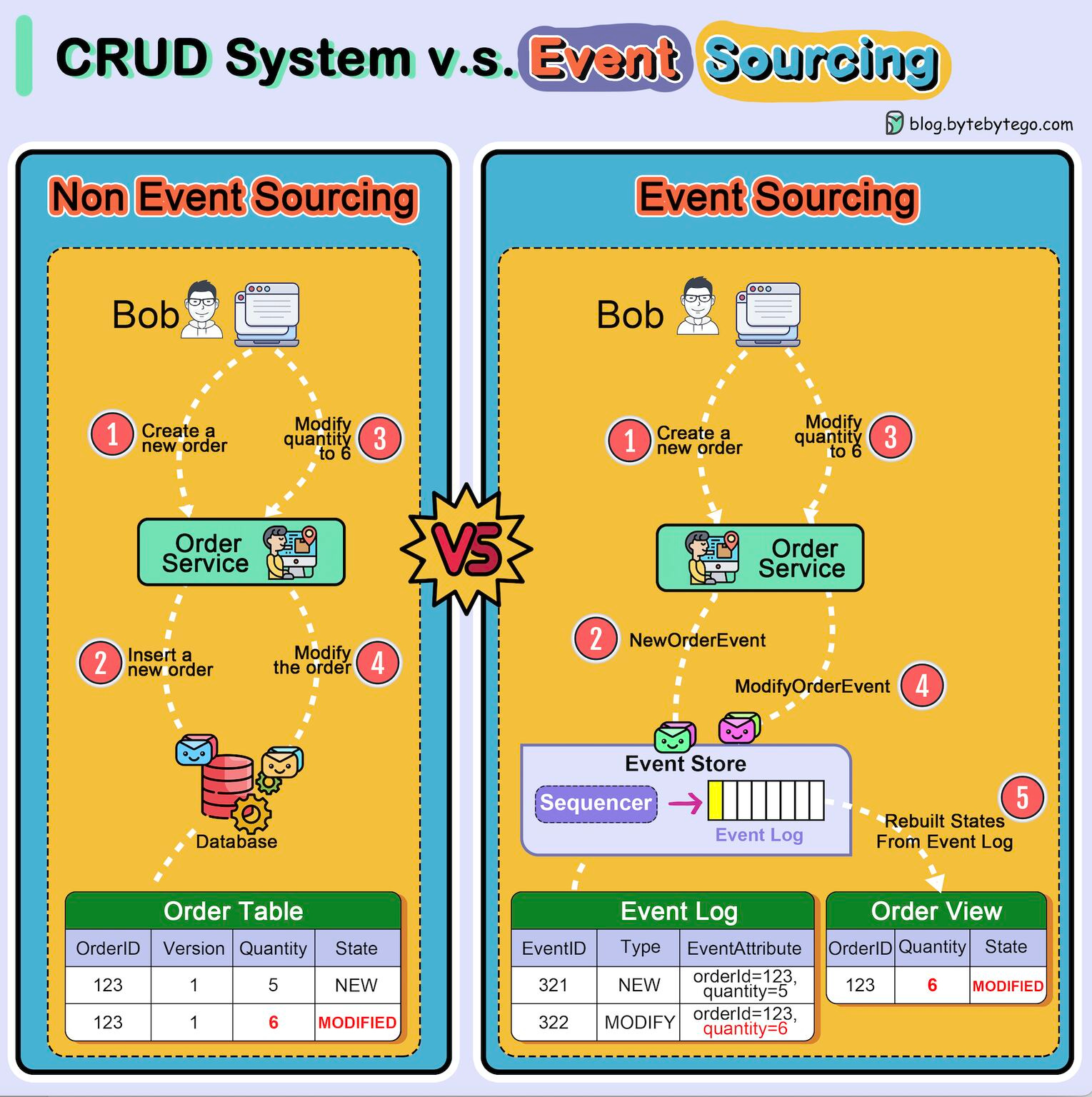
Over to you: Where does your system stand in the adoption roadmap? Reference: Cloud & DevOps: Continuous Transformation by MIT What is Event Sourcing?The diagram below shows a comparison of normal CRUD system design and event sourcing system design. We use an order service as an example. The event sourcing paradigm is used to design a system with determinism. This changes the philosophy of normal system designs. How does this work? Instead of recording the order states in the database, the event sourcing design persists the events that lead to the state changes in the event store. The event store is an append-only log. The events must be sequenced with incremental numbers to guarantee their ordering. The order states can be rebuilt from the events and maintained in OrderView. If the OrderView is down, we can always rely on the event store which is the source of truth to recover the order states. Let's look at the detailed steps.
Over to you: Which type of system is suitable for event sourcing design? Have you used this paradigm in your work? Latest articlesHere are the latest articles you may have missed: To receive all the full articles and support ByteByteGo, consider subscribing: © 2023 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:37 - 30 Sep 2023