- Mailing Lists
- in
- EP138: How do AirTags work?
Archives
- By thread 5369
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 182
EFFECTIVE WAREHOUSE OPERATION AND INVENTORY MANAGEMENT - MALAY VERSION - (2 & 3 Dec 2024)
The week in charts
EP138: How do AirTags work?
EP138: How do AirTags work?
WorkOS: Your app, Enterprise Ready. (Sponsored)WorkOS is a modern identity platform for B2B SaaS. → A complete user management solution along with SSO, Directory Sync (SCIM), and Fine-Grained Authorization (FGA). Ship SSO and SCIM this afternoon This week’s system design refresher:
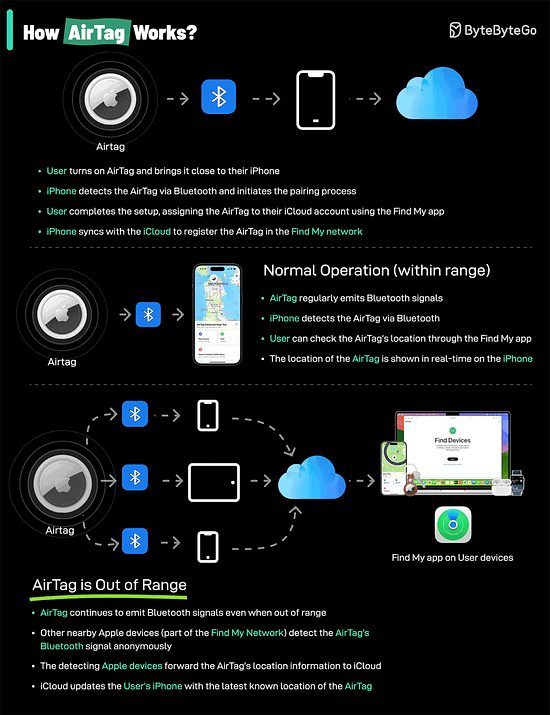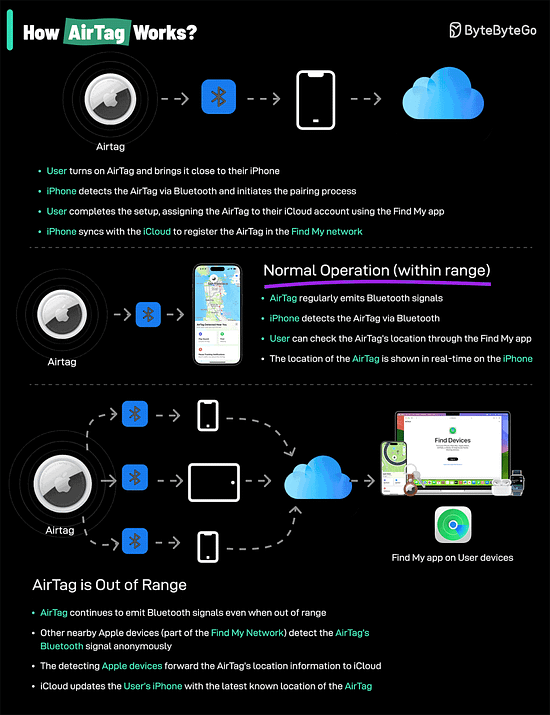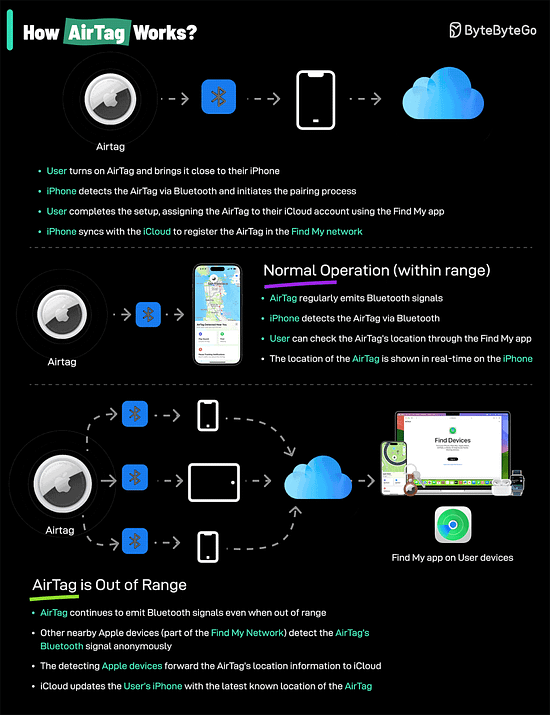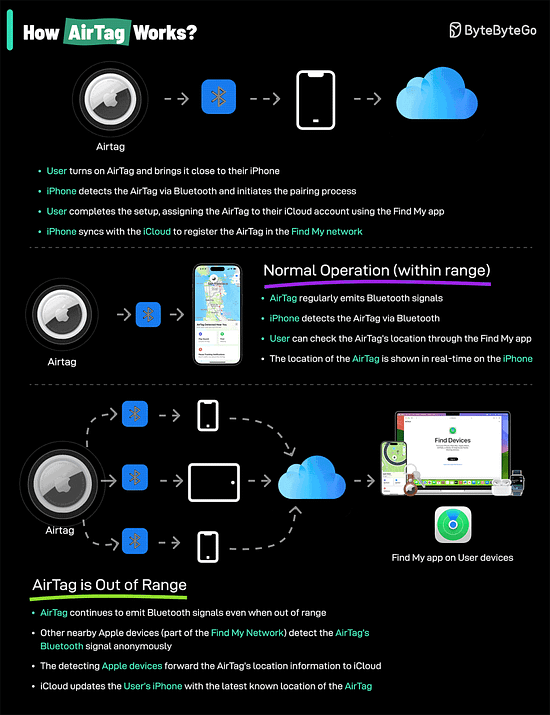
Big-O Notation in 3 Minutes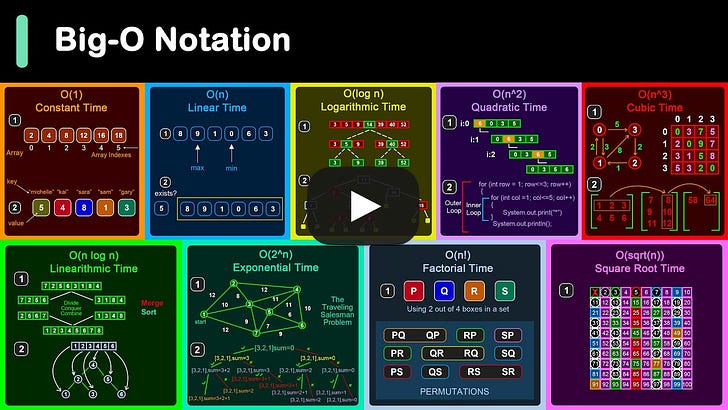 How do AirTags work?AirTags work by leveraging a combination of Bluetooth technology and the vast network of Apple devices to help you locate your lost items.
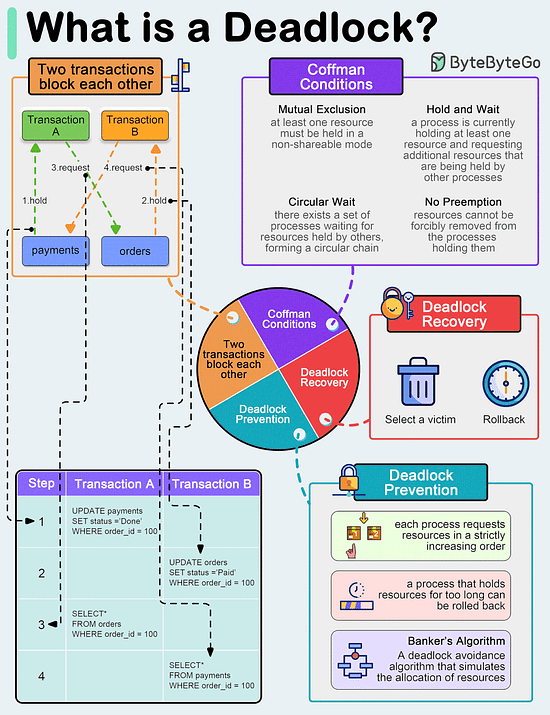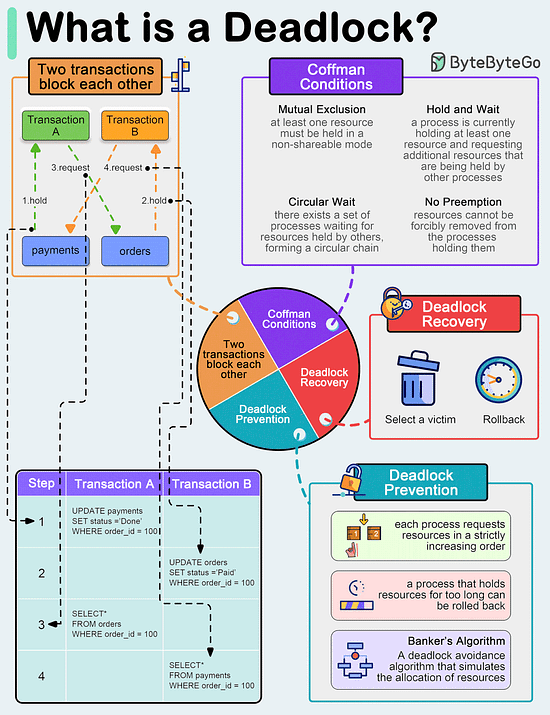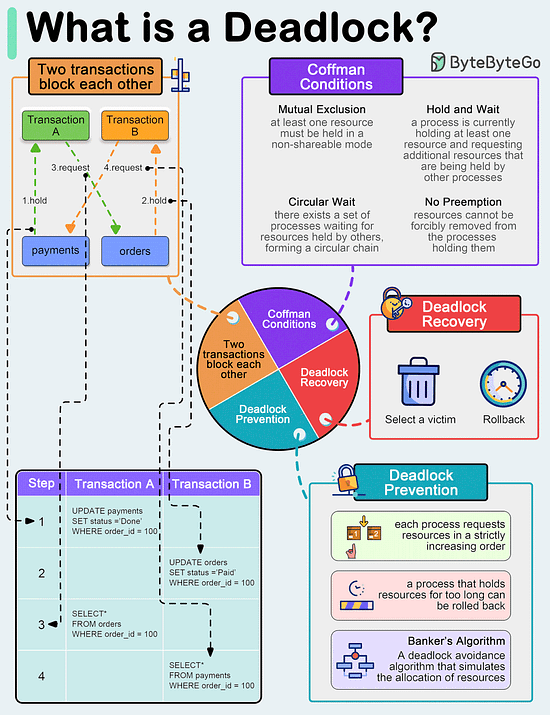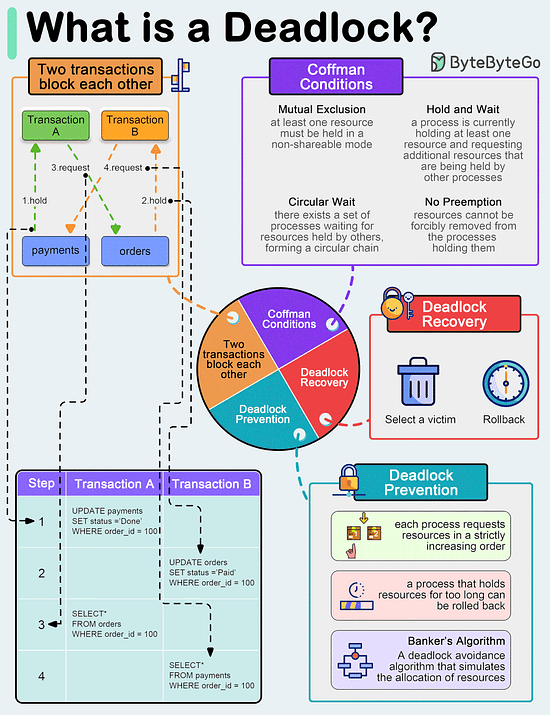
Limitations: 🚀pgai Vectorizer - Automate embeddings for search and RAG, all within PostgreSQL (Sponsored)Launch Alert: pgai Vectorizer automates embedding creation in PostgreSQL, keeping your embeddings up to date as your data changes—no manual syncing required. You can also test models, switch seamlessly, and manage everything with SQL. Available free on GitHub or fully managed in Timescale Cloud. What is a deadlock?A deadlock occurs when two or more transactions are waiting for each other to release locks on resources they need to continue processing. This results in a situation where neither transaction can proceed, and they end up waiting indefinitely.
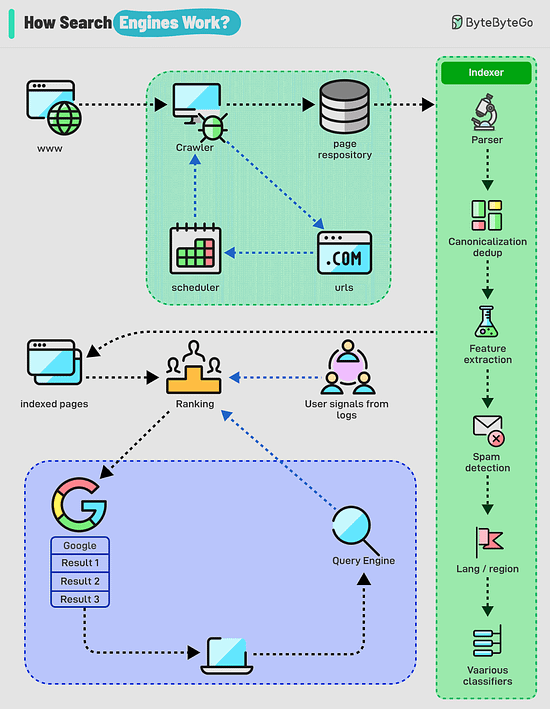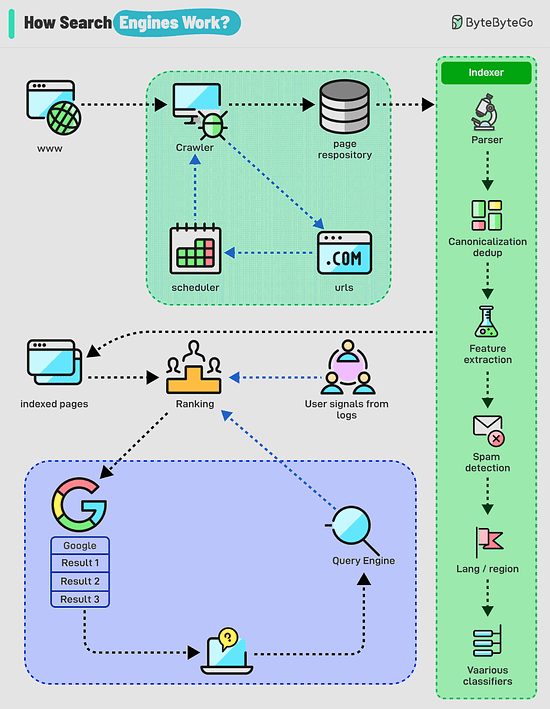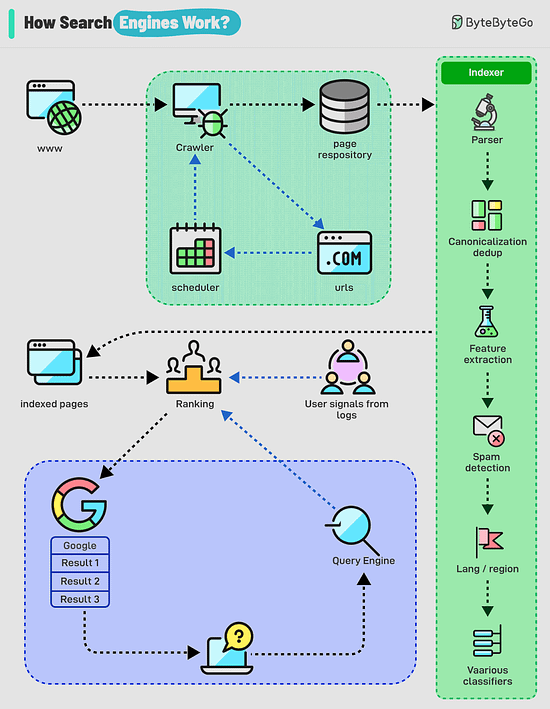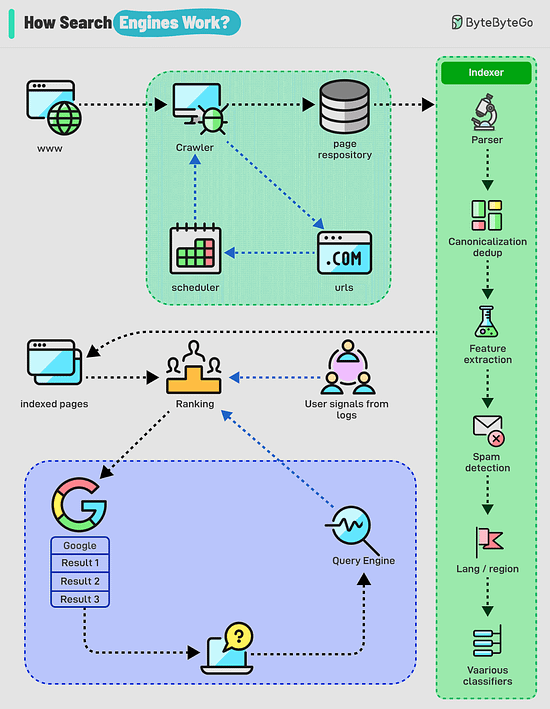
Over to you: have you solved any tricky deadlock issues? How Do Search Engines Work?Search engines work through a combination of three core processes:
SPONSOR USGet your product in front of more than 1,000,000 tech professionals. Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases. Space Fills Up Fast - Reserve Today Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com © 2024 ByteByteGo |
by "ByteByteGo" <bytebytego@substack.com> - 11:37 - 16 Nov 2024