Archives
- By thread 5228
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 40
-
Follow / UP
Hi, info@learn.odoo.com
I am curious to know whether you received my last email or not. Please let me know, if you are interested in our services or not. A prompt reply will be highly appreciated.
Thanks & Regards,
Nidhi Chauhan
From: Nidhi Chauhan
Sent: Wednesday, Jan 15, 2025 4:52 AM
To: info@learn.odoo.com
Subject: New Website, New Experience
Hi, info@learn.odoo.comHope you are doing well.
We are Website Development & Digital Marketing company based in india.
We are a professional Website Design & Re-Design Services Company.
Special Offer For: - Website Design Service / Re-Design Service Very Low-Price Packages,
Note: - I will be happy to send you our portfolio /pricing and Package /requirements details.
Thanks & Regards,
Nidhi Chauhan
by "Nidhi Chauhan" <seowebsitedising@gmail.com> - 06:57 - 6 Mar 2025 -
How MSC saved €500K with accurate shipping locations
How MSC saved €500K with accurate shipping locations
Guide on how to create a zip code map, how to avoid spending millions of dollars due to outdated shipping locations, and monthly changes.
2:00 minute read
🛥️ Avoid spending millions due to outdated shipping locations
🗺️ Guide on how to create a zip code map
🔎 Monthly changes
🏰 Cliopatria: Lost kingdoms & shifting empires
.png?width=100&upscale=true&name=Group%2055%20(1).png)
Avoid spending millions of dollars due to outdated shipping locations
Discover how the Mediterranean Shipping Company (MSC):
🗺️ Activated 3000 global locations per year.
💲 Eliminated repetitive data processing days for the data center, saving approximately €500k annually in operational costs.
⌛ Saved over 900 hours annually, cutting operational expenses, reducing financial penalties, and minimizing business disruptions.
.png?width=100&upscale=true&name=Group%2054%20(1).png)
Guide: How to create a zip code map
Want to turn raw data into a zip code map? This guide breaks it down step by step, helping you visualize trends, spot patterns, and make smarter decisions.

MONTHLY CHANGES
In February, we updated 10,493 rows in our postal database.
Postal database patches
(small changes)
Italy (Postcode), Montenegro (Alternative Names & Denormalized ID correction), Paraguay (Time zone), Uruguay (Suburbs)
Postal boundary updates
Spain
Postal boundary patches (small changes)
Bhutan, Ireland, France, Guatemala, Nicaragua, Portugal, United States
Administrative boundaries patches (small changes)
France, Norway
For a detailed changelog, take a look at the CSV file.
Cliopatria: Lost kingdoms & shifting empires
Ever wished you could time-travel through history’s shifting borders?
Cliopatria makes that possible.
This open-source dataset maps political boundaries from 3400 BCE to today, covering 1,600+ historical states, empires, and kingdoms.
Whether it’s the rise of Rome, the fall of Byzantium, or modern-day changes, Cliopatria captures it all in precise geospatial detail.
Built by the Seshat Global History Databank, it helps researchers, educators, and history buffs visualize the world's political evolution. And the best part? It’s free for everyone!
Follow us on LinkedIn for more geographical facts like this!
Kind regards,
Jerome & the GeoPostcodes team
PS: Interested in previous Monthly Product Updates? Read here.
GeoPostcodes, Bld Bischoffsheim 15, 1000 Bruxelles, Belgium
by "Jérôme from GeoPostcodes" <jerome@geopostcodes.com> - 06:47 - 6 Mar 2025 -
20+ innovations unveiled at New Relic Now
New Relic
20+ innovations unveiled at New Relic Now
 February 2025
February 2025Watch New Relic Now+ 2025 New Relic Now+ is now available on-demand—take a look now to uncover valuable insights, including:
- 20+ new innovations, including AI-powered predictions and agentic integrations.
- Key insights on using AI to drive efficiency and innovation.
- Real-world gains: How Intelligent Observability fuels business uptime and developer velocity.
- Customer insights from the American Red Cross and New York Life.
Watch on-demand 
New Relic Certification is live! We are excited to announce that New Relic Certifications are now live for a range of professional role-based observability certifications.
Whether you're just starting your observability journey, or are a seasoned pro, we encourage you to take the certification exams to get certified as an Observability Professional.
Get certified 
New Relic Now+ 2025: Guide to New Relic innovations for engineering excellence Learn all about the new products announced at our first New Relic Now+ that will help your team achieve its engineering efficiency goals.
Learn more 
 New Relic Now Live roadshows
New Relic Now Live roadshowsJoin us in person to learn how top companies use Intelligent Observability to drive better business outcomes, improve digital customer experiences, optimise cloud costs and boost productivity—and then get hands-on in a GameDay workshop.
This is a free event, so sign up today to save your space. We’ll wrap up the day with food, drinks, and fun:
New Relic University online workshopsCatch our recent New Relic workshops on-demand. These trainer-led workshops with hands-on labs will help you up-level your observability skills.
Watch now
Deploy DeepSeek models locally and monitor with New Relic AI Monitoring
New Relic’s DeepSeek integration allows developers to leverage its open-source, cost-effective capabilities while maintaining visibility into app performance.
Read the blogPostman on creating a strong digital customer experience
Postman's technology teams are responsible for maintaining top-level metrics such as reliability, availability, software resiliency and quality. The team looked to New Relic to level up their responsiveness to customer issues and escalations. Vijayant Singh, Head of Reliability Engineering, explains how.
Watch the video Use our documented IP ranges for seamless connectivityNew Relic teams are continuously reviewing potential improvements to our network and service configurations and providers. To support this, our endpoints, applications, and services need the ability to move between IPs within our documented ranges.
Use our documented IP ranges for seamless connectivityNew Relic teams are continuously reviewing potential improvements to our network and service configurations and providers. To support this, our endpoints, applications, and services need the ability to move between IPs within our documented ranges.
Not an existing New Relic user? Sign up for a free account to get started!

Need help? Let's get in touch.



This email is sent from an account used for sending messages only. Please do not reply to this email to contact us—we will not get your response.
This email was sent to info@learn.odoo.com Update your email preferences.
For information about our privacy practices, see our Privacy Policy.
Need to contact New Relic? You can chat or call us at +44 20 3859 9190.
Strand Bridge House, 138-142 Strand, London WC2R 1HH
© 2025 New Relic, Inc. All rights reserved. New Relic logo are trademarks of New Relic, Inc
by "New Relic" <emeamarketing@newrelic.com> - 04:49 - 6 Mar 2025 -
CNC Reliable Electrical products supporting you in cutting cost

YOUR BIGGEST CHALLENGE?
RISING COSTS.
OUR BIGGEST SOLUTION?

KEEPING IT AFFORDABLE.
As a leading brand in China since 1988, we have extensive experience in reliable electrical product supply. In recent 3 years, we’ve provided high-quality, fairly priced solutions to clients in over 100 countries, achieving 30% annual growth while supporting our partners’ profit growth by the same rate.
We’re dedicated to supporting the industry with quality, affordable products, including circuit breaker, Modular DIN Rail Product,power supply,meters,transformer,DC devices,new energy solution, and power distribution equipment.
Counter the rising costs of business with the affordably priced CNC ELECTRIC solutions.
The CNC ELECTRIC Team
Contact us directly by replying to this message
Learn more at cncele.com
Best Regards
The CNC ELECTRIC Team

cncele@cncele.com
by "customer" <customer@cncelectric.cn> - 04:45 - 6 Mar 2025 -
Strategic workforce planning: How are leading companies doing it?
On McKinsey Perspectives
5 best practices Brought to you by Alex Panas, global leader of industries, & Axel Karlsson, global leader of functional practices and growth platforms
Welcome to the latest edition of Only McKinsey Perspectives. We hope you find our insights useful. Let us know what you think at Alex_Panas@McKinsey.com and Axel_Karlsson@McKinsey.com.
—Alex and Axel
—Edited by Belinda Yu, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to the Only McKinsey Perspectives newsletter, formerly known as Only McKinsey.
Copyright © 2025 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey Perspectives" <publishing@email.mckinsey.com> - 01:49 - 6 Mar 2025 -
[FHL 10 Encore] 5 days away… (you registered?)
So many people told me this was the best FHL yet…Have you registered for the FHL 10 Encore yet???
If not, then go here and make sure you’re registered before we kick off FHL 10 Encore!(Pssst… you’ll see there are two options on the page – Option 1 is if you already bought a ticket to FHL 10 and option 2 is if you didn’t buy an FHL 10 ticket)...
We're just 5 days away from jumping back into FHL 10 ‘The Last Dance’ Encore… And I’m so fired up for this!! I can’t even tell you…
Seeing it again brings back all the excitement…. The ‘a-ha’ moments… The fun memories… The lightning bolts of inspiration that just hit you!!
I love it!
So, make sure you’re registered for the FHL 10 ‘The Last Dance’ Encore!
This is your chance to relive all of that… or experience it for the first time!
If you weren’t there live, you’re going to be blown away by ALL of the presentations! Everyone knocked it out of the park… Like… Grand Slam out of the park!
Josiah Grimes broke down his VSL process in a way that made so much sense.
Eileen Wilder taught us her B.I.T.S. Framework.
Ashley Kirkwood showed us how to use props to SELL.
The list goes on!!!
And remember… This isn’t a ‘cliffnotes’ version of FHL 10… This is THREE FULL DAYS OF FHL 10 GOLD!!
🗓️ Monday, March 10th, 2024 @ 10 MT / 12 PM ET.
🗓️ Tuesday, March 11th, 2024 @ 10 MT / 12 PM ET.
🗓️ Wednesday, March 12th, 2024 @ 10 MT / 12 PM ET.
REGISTER FOR FHL 10 ‘THE LAST DANCE’ ENCORE NOW >>
See you in the encore!
Russell Brunson
P.S. Don’t forget, you’re just one funnel away…
P.P.S. GO HERE TO REGISTER FOR FHL 10 ‘THE LAST DANCE’ ENCORE NOW >>
Marketing Secrets
3443 W Bavaria St
Eagle, ID 83616
United States
by "Russell Brunson" <newsletter@marketingsecrets.com> - 01:51 - 5 Mar 2025 -
Quick Rate Info
Hi,
Hope you're doing well. This's J from Hong-ocean. It's been a while since we last connected, and I wanted to reach out to see how things are going. Just wanted to touch base and remind you that we're here to support you with your shipping needs. If you have any questions or specific requirements, feel free to let me know.
Also, I wanted to share some recent price updates(40'):
XIAMEN TO LA : O/F 1700/40HQ
SHANGHAI TO NYC : O/F 2900/40HQ
NINGBO TO SAVANNAH: O/F 2900/40HQ
These rates are valid until Mar 14th
And of course it's not just China, any country we can. If you receive this message, please reply with the number 1 or whatever you prefer!
Looking forward to hearing from you.
Best regards,
J
by "Jeffery" <jeffery1@xinchen56.com> - 01:05 - 5 Mar 2025 -
[FHL 10 Encore] Did you register yet…?
This is an investment you’ll want to make…OK, we’re getting closer to the FHL 10 ‘The Last Dance’ ENCORE kick off! I hope you’re planning to re-watch FHL 10, or watch it for the first time!
Remember: This encore is THREE FULL DAYS!
Here are the days and times:
Monday, March 10th, 2024 @ 8am PT / 11am PT.
Tuesday, March 11th, 2024 @ 8am PT / 11am PT.
Wednesday, March 12th, 2024 @ 8am PT / 11am PT.
Here’s why I think you should plan on attending the encore:
Did you know it takes the average person 2-7 times to hear the same message before they take action. ?
If you’re like me, you’ll be lucky to retain maybe 20% of what they said at FHL 10. There’s just so much going on, and as much as I listen and take notes, I just can’t learn it all the first time around.
That’s why you should experience FHL 10 again!
REGISTER FOR FHL 10 ‘THE LAST DANCE’ ENCORE NOW >>
This is three full days of live video re-plays! And, it’s not just replays. There is a “live” element to the 3-day event, and you’ll have to register to see what I mean…
I promise you don’t want to miss this!
Get registered today right here, and clear your calendar for the first three days next week, and let’s relive FHL 10 ‘The Last Dance’ again!
See you in the encore!
© Etison LLC
By reading this, you agree to all of the following: You understand this to be an expression of opinions and not professional advice. You are solely responsible for the use of any content and hold Etison LLC and all members and affiliates harmless in any event or claim.
If you purchase anything through a link in this email, you should assume that we have an affiliate relationship with the company providing the product or service that you purchase, and that we will be paid in some way. We recommend that you do your own independent research before purchasing anything.
Copyright © 2018+ Etison LLC. All Rights Reserved.
To make sure you keep getting these emails, please add us to your address book or whitelist us. If you don't want to receive any other emails, click on the unsubscribe link below.
Etison LLC
3443 W Bavaria St
Eagle, ID 83616
United States
by "Todd Dickerson (ClickFunnels)" <noreply@clickfunnelsnotifications.com> - 10:51 - 5 Mar 2025 -
McKinsey Quarterly Classics special issue on leadership
Download the 200-page bonus issue New from McKinsey & Company
Complementing “The future of leadership,” the second issue in our yearlong celebration of McKinsey Quarterly’s 60th birthday, this bonus collection of 15 classic McKinsey Quarterly articles traces how leadership ideas and attitudes have evolved over the past six decades. Explore the timeless insights found in these hand-selected Quarterly articles—previously available only in archival print issues—from authors such as Marvin Bower.
And don’t miss our latest interactive on the future of the office. Using McKinsey’s modeled data in a series of visual representations of San Francisco, Tokyo, and London, it proposes that the offices of the future should be spaces with purpose, designed for connectivity, that are digitally enhanced, and that are oriented around sustainability.
Get access to all of this with a free digital Quarterly membership, which in this commemorative year includes special issues and bonus digital features. Plus, get past digital Quarterly issues and downloads of our 100 most important reports in The McKinsey Insights Store.This email contains information about McKinsey’s research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to our McKinsey Quarterly alert list.
Copyright © 2025 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey & Company" <publishing@email.mckinsey.com> - 10:31 - 5 Mar 2025 -
Procurement Management - Managing Supplier Selection & Negotiation, Sourcing & Tendering (16 & 17 Apri)l
Please call 012-588 2728
email to pearl-otc@outlook.com
HYBRID PUBLIC PROGRAM
PROCUREMENT MANAGEMENT - MANAGING SUPPLIER
SELECTION & NEGOTIATION, SOURCING & TENDERING
5 CPD Points Awarded by MBOT.
(** Choose either Zoom OR Physical Session)
Remote Online Training (Via Zoom) &
Dorsett Grand Subang Hotel, Selangor (Physical)
(SBL Khas / HRD Corp Claimable Course)
Date : 16 Apr 2025 (Wed) | 9am – 5pm By SH Yeo
17 Apr 2025 (Thu) | 9am – 5pm .
..
INTRODUCTION:
The key to an efficient procurement function is the ability to manage the proper selection of suppliers. The ability to select new suppliers or vendors which are able to provide the good support to the company operational needs makes the job of purchasing easier to manage.
In order to select the “perfect” supplier, an effective sourcing process + an efficient selection + ability to negotiate the best deal with the supplier is extremely important.
This program desires to bring these values to all the participants who decide to attend this 2 day interactive training program.
. .
TRAINING OBJECTIVES:
The training program was design with the following key objectives of learning to the participants:-
a) Effective Management of Sourcing and Tendering activities
b) Effective Selection Process during Sourcing and Tendering
c) Understand the different type of tendering and common issue in tendering
d) Effective negotiation preparation for supplier negotiation in sourcing and tendering
e) Understand the effective way of supplier evaluation and management
TRAINING METHODOLOGY:
This training will involve the following area to enhance learning:
a) Power point presentation
b) Case studies & Brain storming session
c) Discussion on subject of learning
d) Facilitating by trainer to enhance understanding of subject matter
e) Pre and Post test to evaluate participants understanding
LEARNING OBJECTIVES EXPECTED FROM PARTICIPANTS:
By the end of the 2-day interactive session, the learning curve achieve will enable the following:-
a) UNDERSTAND strategic sourcing and tendering role of procurement in business operation
b) APPRAISE and DISTINGUISH the type of strategy to be in place to manage tendering process to meet the objective of the company
c) MANAGING and carrying out effective negotiation with suppliers and other stake holders during tendering
d) DECIDING type of tendering to use depending on requirement and strategic advantages to the business organization
e) DIFFERENTIATE key differences between Sourcing and Tendering
f) IMPLEMENTING key areas of concern during selection process
PARTICIPANTS GROUP :
This training program is highly recommended for employees involve in the managing of the supply chain function in the company, for example, personnel from procurement, warehouse, logistics and planning department and finance.
OUTLINE OF WORKSHOP
Module 1 - Sourcing and Tendering
- Sourcing versus Tendering
- Type of Tendering
- Sourcing strategies
- Advantages and Disadvantages of Sourcing
- Advantage and Disadvantages of Tendering
- The Tendering Process in Open Tender
- Common term used in Tendering
Module 2 - Challenges in Tendering
- Key Reason why tender fails
- Reducing the risk in tender failure
- Managing conflict of Interest
- Red flag in Tendering and Sourcing
- Sourcing and Tendering best practices
- Case study
Module 3 – Suppliers Selection and Management Process
- Understanding the 10C + 1R selection
- Evaluation strategy for tendering
- Implementing Supplier On boarding and Off boarding system
- Type of Audits to conduct for supplier selection
- Case study
Module 4 – Managing Smart Negotiation
- Integrative Negotiation
- Distributive Negotiation
- Stages of Negotiation
- SWOT analysis
- Deciding red lines in negotiation
- Knowing your opponent traits
- The Soft Negotiator
- The Principled Negotiator
- The Hard Negotiator
- Traits of a good negotiator
- Bad Negotiator habits
- Mistakes made in Negotiation
- Body language in negotiation
- Clear planning of objectives and goals
- Understand when to walk away
- Managing Reject and counter offer
- Dealing with difficult negotiators
- WATNA strategies
- BATNA strategies
- Case study
** Certificate of attendance will be awarded for those who completed the course
ABOUT THE FACILITATOR
SH Yeo
Academic & Professional Qualifications
Certified HRDF Trainer (TTT certificate number 4669)
Certified Professional Trainer and Facilitator (University Malaya, Malaysia)
- Diploma in Human Resource Management (UK)
- Diploma in Production Management (USA)
- MBA in Supply Chain Management (USA)
- 33 year of management experience in supply chain and operation
- Trainer & consultant since 2008
Mr. Yeo is a very experienced supply chain and operational manager. During his working career, spanning over 33 years, he has held various positions as following:-
1987 - with International Paint (later known as Akzo Nobel International Paint) as a Storekeeper
1989 to 1992 @ Warehouse Executive
1992 to 1993 @ Warehouse Manager
1993 to 1998 @ Production Manager
1998 to 1999 @ join Melandas as a Logistics and Purchasing Manager.
1999 to 2004 @ join Dian Creative as a Material Manager
2004 to 2006 @ join Joubert SA Malaysia as Purchasing Manager
2006 to 2008 @ Procurement Manager
2008 to 2019 @ Supply Chain Manager and Company Director
His major achievements include the following:-
a) Increase productivity in the production department by providing intrinsic and extrinsic motivation to the employees from 1993 to 1998.
b) Making major decision to advise a MNC company to drop LMW warehousing scheme and adopting MITI PC1 and 2 exemption system to help company to be more competitive in the local and oversea market in 1998.
c) Co coordinating Kastam licensing and reporting to solve company reporting and licensing issue with Kastam
d) Establishing control and procedure and bringing awareness to employee on important of supply chain control in 2004 until 2019 and achieving 100% shipment performances to customers
e) Involve in negotiating with a major customer from Europe to secure new contract and beside visiting overseas suppliers for performances improvement and selection of new suppliers
f) Carry out new product development by working with engineering and design team and suppliers, including spending on site at supplier premise to solve new product design issue
g) Introduced new procedures in warehouse and operation for better control of operation and reporting system
h) Managing and conducting cost reduction management program from 2008 to 2013 and reduce cost for the company by up to RM6.5 mil.
i) Involve in managing suppliers contract and involving in proposing and drafting new contract and contract renewal for suppliers from 2008 until 2019 (early retirement) by working with suppliers and internal stakeholders with guidance from legal expert.
j) Managing Non Disclosure Agreement with suppliers to protect company intellectual property
He has been conducting training since 2008 and recently retired as a fulltime supply chain manager and company director to concentrate on full time training and coaching.
His areas of training based on his many years experiences in the industry are as following:-
- Inventory and Warehouse Management
- Supply Chain Management
- Cost Reduction
- Strategic Procurement and Purchasing Management
- Import and Export Documentation Process
- International Payment Risk Mitigation
- Negotiation
- Incoterms and Impact on Trade
- Trade Financing
- Risk on Procurement Fraud
- Letter of Credit and Documentary control
- Procurement contract management
- Incoterms 2020 – Benefit, Risk and Cost on Rule of Delivery
(SBL KHAS / HRD Corp Claimable Course)
TRAINING FEE
14 hours Remote Online Training (Via Zoom)
RM 1,296.00/pax (excluded 8% SST)
2 days Face-to-Face Training (Physical Training at Hotel)
RM 2,250.00/pax (excluded 8% SST)
Group Registration: Register 3 participants from the same organization, the 4th participant is FREE.
(Buy 3 Get 1 Free) if Register before 7 April 2025. Please act fast to grab your favourite training program!We hope you find it informative and interesting and we look forward to seeing you soon.
Please act fast to grab your favorite training program! Please call 012-588 2728
or email to pearl-otc@outlook.com
Do forward this email to all your friends and colleagues who might be interested to attend these programs
If you would like to unsubscribe from our email list at any time, please simply reply to the e-mail and type Unsubscribe in the subject area.
We will remove your name from the list and you will not receive any additional e-mail
Thanks
Regards
Pearl
by "pearl@otcmsb.com.my" <pearl@otcmsb.com.my> - 09:23 - 5 Mar 2025 -
more information for Your Telecoms Consultant?
more information for Your Telecoms Consultant?
Good morning,
I wondered if the email below regarding Birchwood Golf Club was of interest. If you require any further information, or if you would like to discuss the partnership in more detail, drop me an email back.
Best wishes,
Jack StevensAccount Manager0113 5197 994
Jack Stevens <jack@w1g.biz> wrote:
Hi there,
I hope you're well, I wanted to reach out because Your Telecoms Consultant has been recommended to us, and we have a unique opportunity that you may be interested in.
The My Caddie Golf Platform featuring Birchwood Golf Club can help you and the team generate business from our members and visitors, we are looking for a local Telecommunication Company to become our official partner.
Aligning your business with such a prestigious establishment can elevate your brand image and generate a positive association in the minds of potential customers.
Here are some of the features you will receive in the partnership:
- Exclusivity for your sector.
- Providing you with exposure on the members and visitors iPhone app.
- Exposure on the members and visitors Android app.
- Your branding on the flyovers on one of the holes on our Birchwood Golf Club web flyovers which is trackable and targeted to your demographic within the local area.
- Access to our networking groups between all partners and plus ones.
- Complimentary golf for you to entertain clients, colleagues and guests.
The cost is the equivalent of just £26 per week for a 2-year partnership + £399 Artwork (one-off, optional) + VAT.
Artwork is optional but if you want us to do it for you, you can change it up to 8 times over the 2 years so every quarter you can revamp it and put new offers on. We'll also give It to you for further marketing.
I have reached out to a number of companies locally and will be operating on a first come first serve basis so if the above is of interest please let me know as soon as possible to avoid disappointment.
Best wishes,
Jack StevensAccount Manager0113 5197 994
We have sent this email to info@learn.odoo.com having found your company contact details online. If you don't want to get any more emails from us you can stop them here.
West 1 Group UK Limited, registered in England and Wales under company number 07574948. Our registered office is Unit 1 Airport West, Lancaster Way, Yeadon, Leeds, West Yorkshire, LS19 7ZA.
Disclaimer: Our app operates independently. While we provide authentic and accurate hole-by-hole guides, we do not have a direct association with Birchwood Golf Club or claim any endorsement from them. We aim to offer golfers a reliable guide as they navigate their favourite courses. As a value-add for our advertisers, we offer free tee times at Birchwood Golf Club which we procure as any customer would, directly from the venue. We also host networking events, which may be held a various local venues as well as online sessions.Furthermore, advertisers have the unique opportunity to be featured in our flyovers of each golf hole. All offerings are subject to availability and terms.
by "Jack Stevens" <jack@w1g.biz> - 08:39 - 5 Mar 2025 -
Follow-UP
Hi,I am curious to know whether you received my last email or not. Please let me know, if you are interested in our services or not. A prompt reply will be highly appreciated.Thanks & Regards,
Khushi Thakur
From: Khushi Thakur
Sent: Wednesday, Jan 15, 2025 4:52 AM
Subject: New Website, New Experience
Hi,Hope you are doing well.We are Website Development & Digital Marketing company based in india.We are a professional Website Design & Re-Design Services Company.Special Offer For: - Website Design Service / Re-Design Service Very Low-Price Packages,Note: - I will be happy to send you our portfolio /pricing and Package /requirements details.Thanks & Regards,
Khushi Thakur
by "Khushi Thakur" <seotoprankingfastservices@hotmail.com> - 07:21 - 5 Mar 2025 -
Global M&A activity: What to expect in 2025
On McKinsey Perspectives
Reasons for optimism Brought to you by Alex Panas, global leader of industries, & Axel Karlsson, global leader of functional practices and growth platforms
Welcome to the latest edition of Only McKinsey Perspectives. We hope you find our insights useful. Let us know what you think at Alex_Panas@McKinsey.com and Axel_Karlsson@McKinsey.com.
—Alex and Axel
•
Compelling factors in 2025. Could global M&A markets bounce back in 2025? It’s true that dealmakers’ decisions are likely to be complicated by issues such as leadership transitions and geopolitical tensions. But McKinsey Senior Partners Jake Henry and Mieke Van Oostende note a variety of reasons that support an optimistic—perhaps even bullish—case for 2025. For instance, macroeconomic conditions are more favorable than in years past, with economies proving their resilience—and corporates in search of deals tend to have strong balance sheets and cash positions.
—Edited by Belinda Yu, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to the Only McKinsey Perspectives newsletter, formerly known as Only McKinsey.
Copyright © 2025 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey Perspectives" <publishing@email.mckinsey.com> - 01:28 - 5 Mar 2025 -
Purchase Order
Dear All,I am Elena Francesco from Deca S.P.A.We came across your company during our search for suppliers and are interested in your products.Could you please send us your data sheet for our reference and perusal. We will revert to you with our RFQ as soon as possible.Also note that the quality of the products must be guaranteed to enable us to establish a good business relationship.I would be pleased to read from you.Thank youLooking forward to your reply.Best Regards
Elena FrancescoSenior Sales Manager,Deca S.P.A.47899 Serravalle, Ciarulla.San Marinoelenafrancessco052@gmail.com
by "Elena Francesco" <hector7710@hotmail.com> - 11:07 - 4 Mar 2025 -
ERP Vendors Are Paying Attention—Here’s What You Need to Know
ERP Vendors Are Paying Attention—Here’s What You Need to Know
Hi MD Abul,
Lately, we’ve been talking a lot about ERP vendors—their evolving strategies, challenges, and how they’re adapting to industry shifts. And it’s clear they’re listening. Many have reached out to our team, showing just how important these conversations are.
If you’re following these trends, you might find a recent blog insightful. It explores:
- How Composable ERP is Reshaping the Industry – Why more organizations are moving toward modular solutions
- What ERP Vendors Are Doing Differently – From pricing models to product roadmaps, how their strategies are evolving
- What This Means for Your Digital Transformation – Key factors to consider when evaluating your ERP options
With so much changing in the ERP space, understanding these shifts is crucial for making informed decisions.
Would love to hear your thoughts—are you seeing these changes firsthand?
Best regards,
Eric Kimberling
Third Stage Consulting 384 Inverness Pkwy Suite Englewood Colorado
You received this email because you are subscribed to Marketing Information from Third Stage Consulting.
Update your email preferences to choose the types of emails you receive.
Unsubscribe from all future emails
by "Eric Kimberling" <eric.kimberling@thirdstage-consulting.com> - 04:59 - 4 Mar 2025 -
[FHL 10 Encore!!!] Did you register yet…?!?
FHL 10 ‘The Last Dance’ is an investment you’ll never regret!OK, we’re down to less than a week until the FHL 10 ENCORE ‘The Last Dance’ kick off!
And… I hope you’re marking your calendars now to re-watch FHL 10, or watch it for the first time!
This encore is THREE FULL DAYS! Here are the days and times:
🗓️ Monday, March 10th, 2024 @ 8am PT / 11am ET
🗓️ Tuesday, March 11th, 2024 @ 18am PT / 11am ET
🗓️ Wednesday, March 12th, 2024 @ 8am PT / 11am ET
👉 CLICK HERE to Register for FHL 10 ‘The Last Dance’ Encore Now! 👈
I’m sure you’ve heard this before…
But there are legit scientific studies that say it takes the average person 2-7 times to hear the same message before they take action.
And if we’re being honest… If we were just listening to the speakers at FHL 10, we probably retained maybe 20% of what they said (if that… )
That’s why you need to experience FHL 10 again!
We have the FHL 10 Encore, so you can re-watch the incredible presentations from the comfort of your home… take notes… And really, truly absorb it!!
Ready to Take Action? Secure Your Spot for FHL 10 Encore Now!
YES! I’m In – Let’s Do This!! →It’s not a cliffnotes version of FHL 10.
This is three full days of live video re-plays! (There is a “live” element to the 3-day event, and you’ll have to register to see what I mean… ;)
Doesn’t matter if you were there and you’ll be re-watching….
Or if you missed it, and you’ll be seeing these presentations and the insane magic of FHL 10 for the first time…
I promise you don’t want to miss this!!!
Get registered today right here, and clear your calendar for the first three days next week, and let’s relive FHL 10 ‘The Last Dance’ again!!
See you in the encore!
Russell Brunson
P.S. Don’t forget, you’re just one funnel away…
P.P.S. GO HERE TO REGISTER FOR FHL 10 ‘THE LAST DANCE’ ENCORE NOW >>
Marketing Secrets
3443 W Bavaria St
Eagle, ID 83616
United States
by "Russell Brunson" <newsletter@marketingsecrets.com> - 01:13 - 4 Mar 2025 -
[FHL 10 Encore] Register to watch the replay!
For those that missed FHL 10 ‘The Last Dance’...Todd here again!
Well, the last FHL ever was harder than I expected to get up on the FHL stage with Russell for the last time.
Yes, we’re turning the page, but does it have to end?
I’ve been getting lots of emails over the last couple weeks, asking if we will allow people to re-watch the presentations.
(Or watch them for the first time because they couldn’t make it to Vegas…)
And the answer is yes!
This is your chance to watch all of those life-changing presentations one more time and soak in all of the awesome speakers and presenters.
Are you up for that?
And remember, this isn’t a cliffnotes version of FHL 10… We’re showing pretty much ALL of the presentations virtually!
It’s going to be NEXT MONDAY, TUESDAY, and WEDNESDAY (March 10th - 12th - Starting every day at 8am PT / 11am PT ).
FHL 10 was honestly one… if not the best FHL we’ve ever had!
See you in the encore!
© Etison LLC
By reading this, you agree to all of the following: You understand this to be an expression of opinions and not professional advice. You are solely responsible for the use of any content and hold Etison LLC and all members and affiliates harmless in any event or claim.
If you purchase anything through a link in this email, you should assume that we have an affiliate relationship with the company providing the product or service that you purchase, and that we will be paid in some way. We recommend that you do your own independent research before purchasing anything.
Copyright © 2018+ Etison LLC. All Rights Reserved.
To make sure you keep getting these emails, please add us to your address book or whitelist us. If you don't want to receive any other emails, click on the unsubscribe link below.
Etison LLC
3443 W Bavaria St
Eagle, ID 83616
United States
by "Todd Dickerson (ClickFunnels)" <noreply@clickfunnelsnotifications.com> - 12:17 - 4 Mar 2025 -
How Uber Built Odin to Handle 3.8 Million Containers
How Uber Built Odin to Handle 3.8 Million Containers
The details in this post have been derived from Uber Engineering Blog and other sources.͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ Forwarded this email? Subscribe here for moreBuilding AI Apps on Postgres? Start with pgai (Sponsored)
pgai is a PostgreSQL extension that brings more AI workflows to PostgreSQL, like embedding creation and model completion. pgai empowers developers with AI superpowers, making it easier to build search and retrieval-augmented generation (RAG) applications. Automates embedding creation with pgai Vectorizer, keeping your embeddings up to date as your data changes—no manual syncing required. Available free on GitHub or fully managed in Timescale Cloud.
Disclaimer: The details in this post have been derived from Uber Engineering Blog and other sources. All credit for the technical details goes to the Uber engineering team. The links to the original articles are present in the references section at the end of the post. We’ve attempted to analyze the details and provide our input about them. If you find any inaccuracies or omissions, please leave a comment, and we will do our best to fix them.
In the early days, the engineers at Uber had to take care of databases and storage systems manually. Whenever they needed to set up, update, or fix something, they followed written instructions called "runbooks". These runbooks were like a step-by-step guide.
As Uber grew, this manual process became overwhelming. They had thousands of databases spread globally, and managing them by hand was a slow and difficult process prone to mistakes.
To solve this, Uber created Odin, an automated system that manages all these databases and storage clusters without human intervention. Unlike older systems that work with only specific types of databases, Odin is technology-agnostic, meaning it can handle many different databases and storage systems seamlessly.
Odin helps Uber’s engineers organize, scale, and maintain their storage infrastructure, ensuring everything runs smoothly and reliably. In this article, we will look at a comprehensive breakdown of Odin and the challenges Uber faced while developing it.
The Scale of Odin
Since 2014, Uber’s data infrastructure has expanded at an unprecedented scale.
What started with a few hundred hosts has now evolved into a massive fleet of over 100,000 hosts, supporting a huge number of stateful workloads.
These workloads are essential for Uber’s real-time services, including ride-hailing, food delivery, and payment processing, all of which depend on highly available and scalable storage solutions.
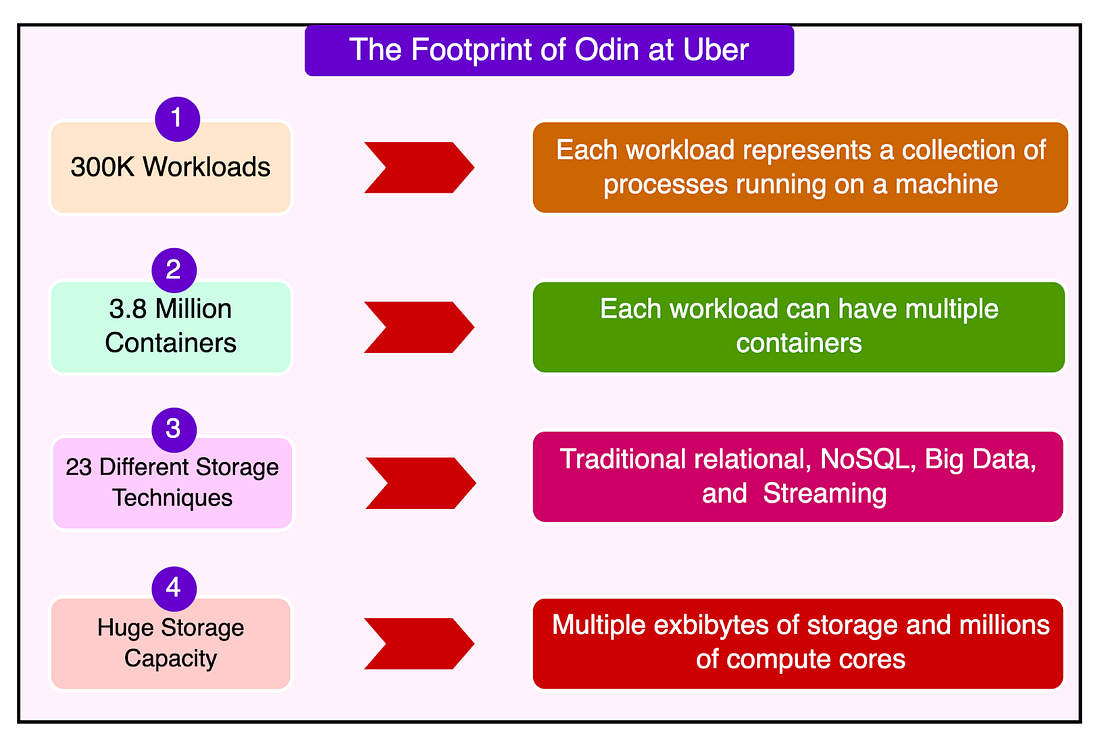
As per an estimate, Uber’s fleet collectively manages multiple exbibytes of storage. To put this into perspective 1 exbibyte equals 1,152,921.5 terabytes (TB). Multiple exbibytes place Uber’s storage in the zettabyte-scale range.
This level of storage capacity is necessary because Uber generates massive volumes of real-time data, such as:
Ride and trip history
GPS tracking logs
User profiles and payment transactions
Machine learning models
Operational logs.
Odin allows Uber to manage this enormous ecosystem through automation, self-healing mechanisms, and efficient resource scheduling. It is responsible for handling:
300,000 workloads, where each workload represents a collection of processes running on a machine, similar to Kubernetes pods.
3.8 million individual containers, which means each workload can have multiple containers running different components of Uber’s stateful services.
In essence, Odin optimizes how storage is allocated and accessed to ensure fast read/write performance while preventing unnecessary duplication and inefficiency. Odin is also technology-agnostic, meaning it doesn’t just manage a single type of database or storage system but instead integrates with 23 different storage technologies, including:
Traditional Online Databases such as MySQL (relational) and Cassandra (distributed NoSQL database)
Big Data and Streaming Platforms such as HDFS, Kafka, and Presto
Resource Scheduling and Workflow Management such as Yarn and Buildkite
Each of these technologies serves a specific purpose within Uber’s ecosystem, and Odin ensures they can all operate efficiently within the same unified infrastructure. For example:
MySQL and Cassandra require high availability and read/write consistency, so Odin ensures replicas are correctly placed and synchronized.
Kafka requires high-throughput storage and low-latency access, so Odin manages partition distribution across nodes.
HDFS and Presto require large-scale batch processing, so Odin makes sure that storage resources are efficiently utilized.
Odin’s Architecture and Design Principles
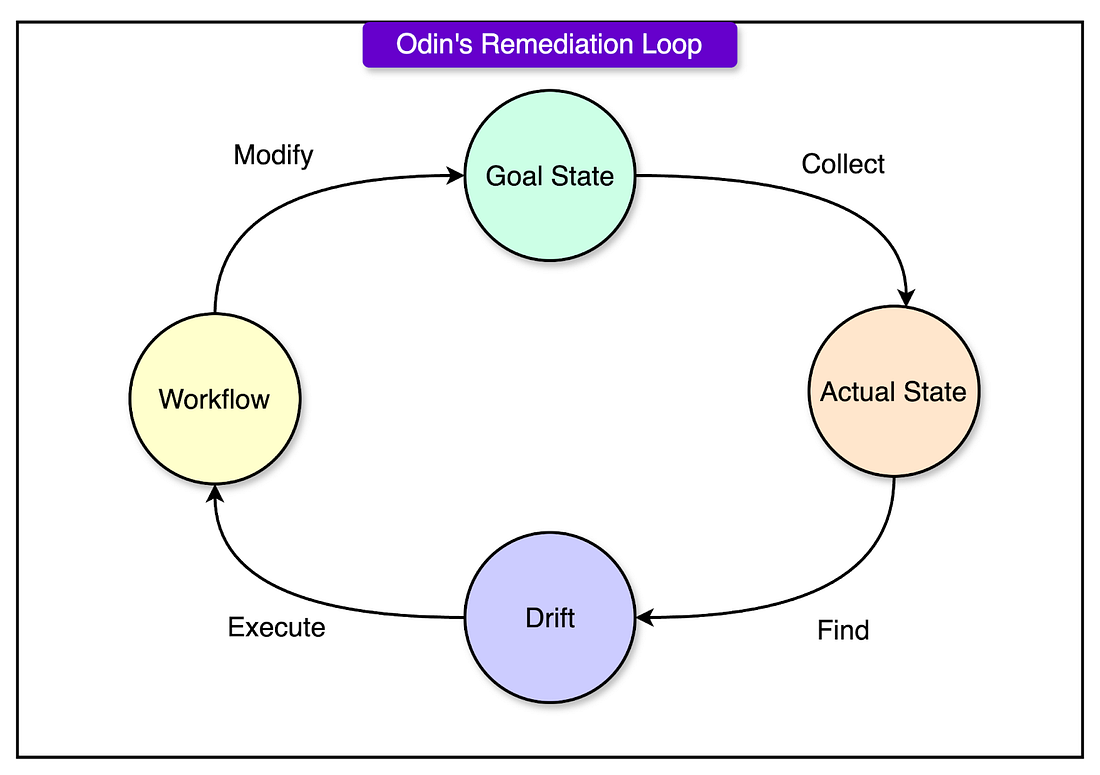
Unlike traditional imperative systems that require explicit commands to perform tasks, Odin follows a declarative model where engineers define what the system should look like (goal state) rather than how to achieve it.
To maintain the goal state, Odin employs self-healing remediation loops that continuously monitor the system state and detect deviations. If any deviation is found, it takes corrective actions automatically without human intervention.
See the diagram below that shows the steps within Odin’s remediation loop.
For example, an engineer defines that a database should always have three replicas. Odin automatically ensures this is always the case. If a replica fails or a node crashes, Odin self-heals by spinning up a new instance to meet the goal state.
This design is similar to Kubernetes but optimized for stateful workloads such as databases and large-scale storage systems.
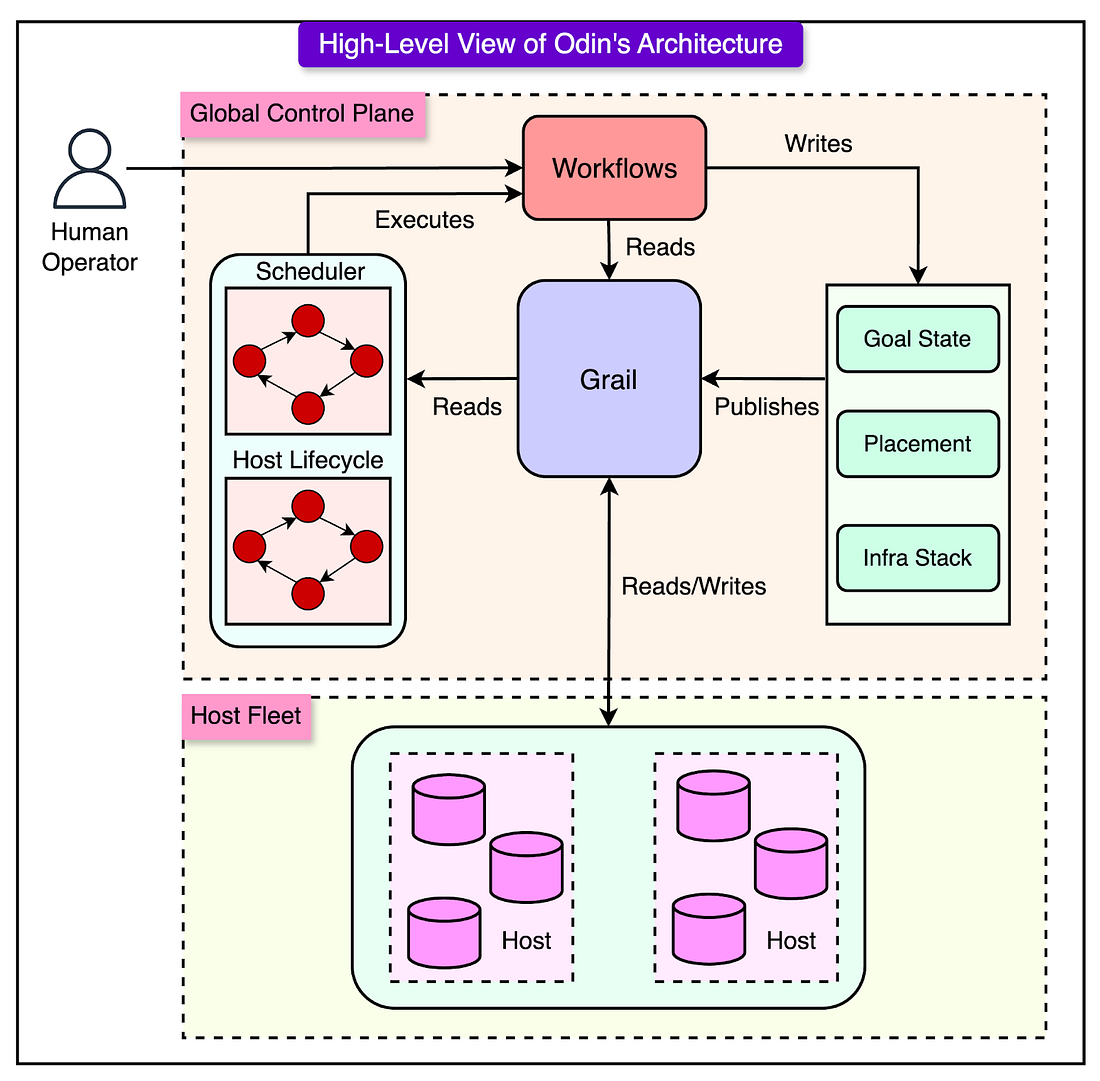
The diagram below shows a high-level view of Odin’s architecture.
The key architectural components of Odin are as follows:
1 - Grail: The Data Integration Platform
Odin’s intelligence depends on having an accurate and up-to-date view of Uber’s global infrastructure. This is handled by Grail.
Grail provides a real-time snapshot of all hosts, containers, and workloads across Uber’s infrastructure. It works similarly to the Kubernetes API Server but at a much larger scale. It allows engineers and remediation loops to query global system state instantly, enabling informed scheduling and decision-making.
The key advantages of Grail are as follows:
Operates across tens of thousands of hosts in multiple data centers and cloud regions.
Works with all storage technologies managed by Odin.
Unlike traditional database monitoring tools that operate per data center, Grail aggregates data across all Uber locations.
2 - Remediation Loops
At the core of Odin’s automation capabilities are remediation loops.
Each remediation loop is a separate microservice. This allows independent development and deployment without affecting other parts of the system. It follows a four-step cycle:
Inspect the goal state (what the system should look like).
Collect the actual state (what the system currently looks like).
Identify discrepancies between the goal and the actual state.
Trigger corrective actions using Cadence workflows.
This process is continuous, ensuring that Odin actively maintains stability and performance.
3 - The Control Plane
Odin’s control plane is responsible for orchestrating workloads, scheduling tasks, and managing cluster topology.
The core responsibilities of the Control Plane are as follows:
Workload Scheduling: It decides where and how workloads should be deployed based on system health, resource availability, and performance needs.
Cluster Management and Topology Decisions: Determines how databases and storage clusters should be distributed across Uber’s infrastructure.
Workflow Execution (via Cadence): Engineers interact with the control plane through Cadence workflows. These workflows define specific actions, such as upgrading a database or rescheduling workloads.
4 - Host-Level Agents
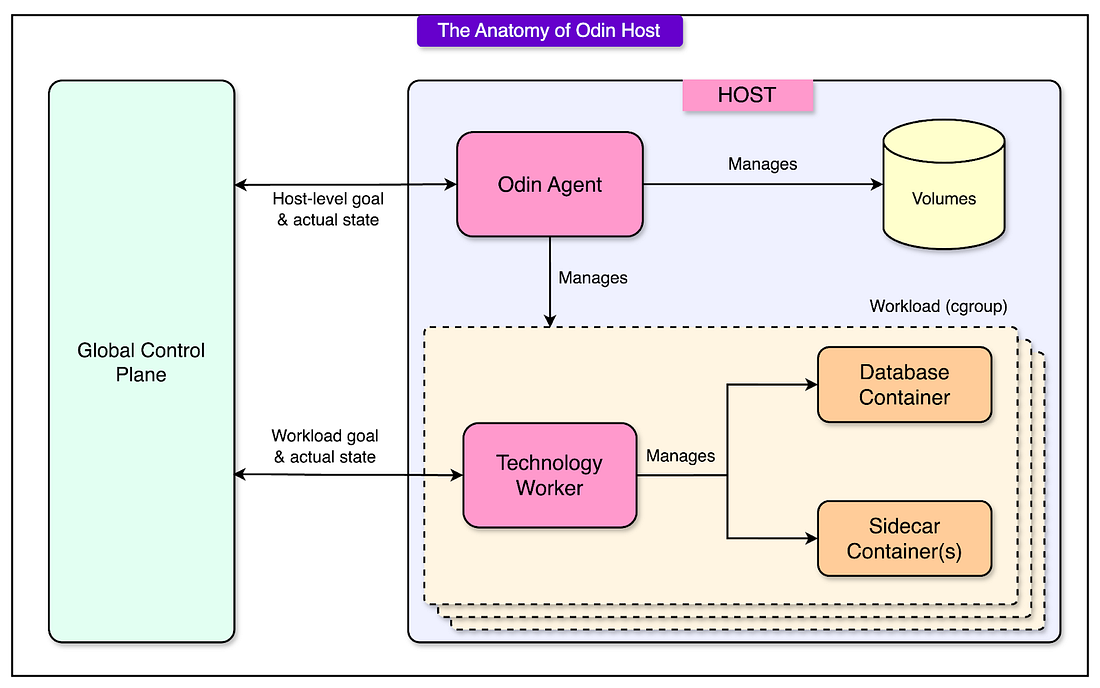
Odin’s architecture separates global control from local execution using two host-level agents.
Odin-Agent: This runs on every host in Uber’s infrastructure and handles generic host-level tasks, such as resource allocation (CPU, memory, and disk), container lifecycle management, and disk volume and cgroup management.
Technology-Specific Worker: A containerized agent that runs inside each database or storage workload. It is tailored to the specific technology being used (for example, MySQL and Cassandra). This agent ensures that the database internals align with the goal state.
See the diagram below that shows the two host-level agents in more detail.
By separating general host management (Odin-Agent) from database-specific logic (Worker), Odin maintains standardization and customization across different workloads.
Odin’s Key Features and Innovations
As mentioned, Odin is a stateful workload management system designed to handle Uber’s massive-scale database and storage infrastructure.
1 - Self Healing System
Odin continuously compares the desired goal state with the actual state of the system. If a deviation is detected, it automatically triggers corrective actions through Cadence workflows.
No human intervention is required in this process. The system detects and fixes failures autonomously. This eliminates downtime caused by manual debugging. Moreover, Odin constantly fine-tunes itself to maintain optimal performance.
2 - High Availability and Fault Tolerance
Odin ensures high availability through dynamic workload rescheduling and failure-handling mechanisms.
60% of workloads are rescheduled each month to balance resource utilization. Workloads move between hosts dynamically to optimize performance and maintain resilience against failures. Odin makes real-time rescheduling decisions based on resource usage, fault tolerance, and availability requirements.
One of Odin’s key innovations is its make-before-break strategy. Before shutting down a workload, Odin provisions a replacement instance. The old instance is only removed once the new one is fully operational. This approach is important for stateful workloads like databases, where shutting down a node without a replacement can cause data loss, unavailability, or increased latency.
3 - Efficient Storage Management
When Odin was introduced, containerizing databases was still a relatively uncommon and controversial practice. However, Uber fully embraced containerized stateful workloads.
An innovation Odin brought to the table was placing multiple database instances on a single host. Traditionally, databases run on dedicated machines, wasting resources. Odin enables up to 100 databases to be colocated on the same host by managing CPU, memory, and disk allocation.
Unlike traditional NAS-based database solutions, Odin relies on locally attached SSDs and HDDs. This results in lower latency, higher throughput, and reduced costs.
4 - Workload Identity and Stateful Migration
Stateful applications require persistent identity across rescheduling events. Unlike Kubernetes StatefulSets, which assigns a stable pod identity, Odin takes a different approach.
In this approach, workload identity is preserved across rescheduling events. Data replication is performed before workload termination. Goal-state propagation ensures that the new instance picks up exactly where the old one left off. In other words, the workload transition is seamless, with no downtime or loss of service.
Challenges and Optimization Strategies in Odin
Managing a platform as large as Odin comes with significant engineering challenges.
As Uber scaled, Odin had to evolve from a human-driven system to a fully automated, highly coordinated, and resilient infrastructure management platform.
Some key takeaways are as follows:
The manual workload management was no longer scalable. Fleet-wide optimizations were needed for resiliency, cost savings, upgrades, and data center migrations.
Uncoordinated operations (like workload migrations and container upgrades) could take down clusters. Consensus-based databases needed careful migration strategies.
A global coordination system was needed to solve these problems. This was done using predefined budgets for allowable disruptions and enforcing platform-wide global concurrency constraints.
Conclusion
Odin represents a significant leap in stateful workload management, enabling Uber to scale its infrastructure from hundreds to over 100,000 hosts while maintaining high availability, cost efficiency, and operational stability.
By transitioning from manual, human-driven operations to an intent-based, self-healing, and automated orchestration system, Odin has eliminated inefficiencies and minimized downtime in Uber’s mission-critical storage systems.
The key innovations behind Odin, such as self-healing remediation loops, intelligent workload rescheduling, make-before-break migrations, and platform-wide coordination mechanisms, have allowed Uber to achieve 95%+ resource utilization.
As Uber continues to grow, Odin is set to evolve further, integrating new optimizations, smarter automation, and deeper AI-driven workload management.
References:
Like
Comment
Restack
© 2025 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe
by "ByteByteGo" <bytebytego@substack.com> - 11:36 - 4 Mar 2025 -
How Our Live Scoring & Tech Create an Unforgettable Day
Keep the excitement going with real-time leaderboards... Hello Sir/Madam,
When you host a corporate golf day with us at Poulton Park Golf Club, you’re not just getting a round of golf—you’re investing in an immersive, high-tech experience:
- Live Scoring System: Keep the excitement going with real-time leaderboards displayed on screens throughout the venue.
- Drone Footage: Capture unique aerial shots and dynamic videos that make perfect promotional material.
- High-Quality Visuals: We showcase sponsor banners, your company branding, and instant scoring updates to keep everyone engaged.
These features ensure your event stands out from the crowd. However, our diary is rapidly filling, and once we’re fully booked, we can’t guarantee bringing our entire suite of technology to each requested date.

Curious about how this could look for your event? Reply to this email or call me on +44 (0)7441 351 701, and we’ll find the best package for your team.
Best Regards
Josh Budz
Senior Business Development Manager
corporategolfday.com
+44 (0)121 2709072
+44 (0)7441 351 701


by "Josh - Corporate Golf Day" <info@corporategolfer.co.uk> - 04:02 - 4 Mar 2025 -
What it will take to boost Europe’s competitiveness
On McKinsey Perspectives
The cost of underperformance Brought to you by Alex Panas, global leader of industries, & Axel Karlsson, global leader of functional practices and growth platforms
Welcome to the latest edition of Only McKinsey Perspectives. We hope you find our insights useful. Let us know what you think at Alex_Panas@McKinsey.com and Axel_Karlsson@McKinsey.com.
—Alex and Axel
•
Lagging investment. The prosperity and sovereignty of nations increasingly depend on technology, McKinsey Senior Partner Solveigh Hieronimus and coauthors note. Yet despite the region’s potential for technological leadership, large European businesses invest less than their US counterparts—particularly in technology. Indeed, between 2015 and 2022, Europe’s corporations underinvested by €700 billion per year when compared with US corporations, while corporate returns on invested capital in Europe also lagged those in the US.
—Edited by Belinda Yu, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to the Only McKinsey Perspectives newsletter, formerly known as Only McKinsey.
Copyright © 2025 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey Perspectives" <publishing@email.mckinsey.com> - 01:28 - 4 Mar 2025