Archives
- By thread 5362
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 175
-
A leader’s guide to the Davos 2025 agenda
Leading Off
Collaborate and innovate
by "McKinsey Leading Off" <publishing@email.mckinsey.com> - 02:05 - 13 Jan 2025 -
What can you expect from Davos this year?
Only McKinsey Perspectives
Key issues for 2025 Brought to you by Alex Panas, global leader of industries, & Axel Karlsson, global leader of functional practices and growth platforms
Welcome to the latest edition of Only McKinsey Perspectives. We hope you find our insights useful. Let us know what you think at Alex_Panas@McKinsey.com and Axel_Karlsson@McKinsey.com.
—Alex and Axel
•
Beyond the agenda. In more than 300 seminars, the delegates at this year’s WEF Annual Meeting are expected to discuss major global issues, including geopolitical shifts, new sources of economic growth, and an inclusive energy transition. Still, some topics—such as the gender gap, women’s health, and the value of science and medicine—deserve greater attention than they will likely receive, a group of WEF Young Global Leaders (YGLs) share with McKinsey Global Publishing’s Raju Narisetti.
—Edited by Belinda Yu, editor, Atlanta
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to the Only McKinsey Perspectives newsletter, formerly known as Only McKinsey.
Copyright © 2025 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Only McKinsey Perspectives" <publishing@email.mckinsey.com> - 01:39 - 13 Jan 2025 -
Taste the Difference: Premium Canned Oranges Just for You!
Dear info,
Wishing you a wonderful day!
I’m Ruby from Lvfanda Foodstuff Company, where we specialize in top-notch canned fruits and vegetables.
Are you still searching for the perfect canned foods? Our canned oranges have been successfully exported to Japan, Europe, America, and the Middle East, receiving outstanding feedback from our clients.
As we prepare for the new harvest, I invite you to share your specific requirements so I can offer you our best pricing.
We also provide samples for you to evaluate our quality before making a decision.
Excited to hear from you soon!
Warm regards,
Ruby
Jiande Xinanjiang Lvfanda Food Co., Ltd
by "manager" <manager@lfdfood.com> - 11:27 - 12 Jan 2025 -
GRAB YOUR SEAT !!! BASIC GREENHOUSE GAS (GHG) ACCOUNTING, MITIGATION, AUDIT AND REPORTING TRAINING (10 - 11 March 2025)
GRAB YOUR SEAT!!!
Please call 012-588 2728
email to pearl-otc@outlook.com
FACE-TO-FACE PUBLIC PROGRAM
BASIC GREENHOUSE GAS (GHG) ACCOUNTING,
MITIGATION, AUDIT AND REPORTING TRAINING
(6 CPD Approved by EiMAS - EiMAS 2024/CPD0584/MFA)
8 CDP Points Awarded by Suruhanjaya Tenaga
(Claimable CPD MBOT : 12 Points)
Venue : Wyndham Grand Bangsar Kuala Lumpur Hotel (SBL Khas / HRD Corp Claimable Course)
Date : 10 March 2025 (Mon) | 9am – 5pm By Shaharuddin
11 March 2025 (Tue) | 9am – 5pm . .
INTRODUCTION:
Many organizations are starting to think about how to manage their greenhouse gas (GHG) emissions for a number of reasons: to minimize their impact on the planet, to prepare for regulation and address evolving disclosure requirements, to increase energy efficiency and/or to build their profile as an environmental leader. Building an inventory of your sources and emissions (eg., carbon footprint) is an essential first step to assessing risks, reducing emissions and tracking your performance.
This course aims at professionals responsible for measuring, reporting and managing carbon dioxide and other greenhouse gas (GHG) emissions for their organization. This training course will cover the basics of GHG accounting for organizations. The course materials are based on the WRI/WBCSD GHG Protocol Corporate Standard, while referring to the ISO 14064: Part 1 international standard for GHG inventories.
This course will provide you the latest information regarding GHG emissions accounting and management and focuses on areas such as: background to climate change, developing a carbon accounting system, managing GHG emissions and options for reducing GHG emissions. You will also be equipped to communicate effectively the imperative of reducing the GHG emissions with colleagues.
This training is designed to provide participants with essential understanding of carbon accounting approaches and methodologies based on ISO14064 and the GHG Protocol: Corporate Accounting and Reporting Standards. These standards besides have formed the basis of many local and international schemes, they also provide tools for industries and governments in developing their programs to reduce greenhouse gas (GHG) emissions.
OBJECTIVE:
This programme will enable participants to :-
- Understand the Greenhouse Gas Protocol’s Corporate Standard
- Understand the ISO 14064 Standard
- Enable to identify GHG sources of emissions
- Enable participants to prepared GHG calculations
- Enable participants to determine GHG mitigation
- Understand the assess GHG audit and verification processes
- Understand the learn to prepare reports
WHO SHOULD ATTEND:
Safety committees who are responsible for identifying GHG sources, prepared GHG calculations, determine mitigation, assess GHG audit processes.
LEARNING METHODOLOGY:
This training will involve the use of slides, handout material, practical tools, sharing of actual cases, Q & A and appropriate videos.
OUTLINE OF WORKSHOP
DAY ONE
9.00 am - 10.30 am
- Overview of GHG Accounting
- Introduction to GHG Accounting and Its Value to Businesses & Investors
- Terminology
- Accounting Process Overview
- Current Industry Initiatives
- Interactive Exercise 1
10.30 am - 10.45 am Tea Break
10.45 am - 1.00 pm
- The Science Behind GHG Accounting
- Why Do We Track GHG Emissions
- The Science of the GHG Effect
- The 6 GHGs, Their Impacts, and Sources
- Global Warming Potential (GWP)
- Interactive Exercise 2
1.00 pm - 2.00 pm Lunch
2.00 pm - 3.30 pm
- The Process of GHG Accounting Part 1
- Best Practices from GHG Protocol
- Defining Organizational Boundaries
- Defining Operational & Legal Boundaries
- Identifying Emissions Sources and Collecting Data
- Defining Units and Referencing Emissions Factors
- Common Pitfalls & Considerations
- Best Practices
3.30 pm - 3.45 pm Tea Break
3.45 pm - 5.00 pm
- The Process of GHG Accounting Part 2
- Purpose and Benefits of ISO 14064
Introduction of the ISO 14064-1:2006 Greenhouse gases — Part 1: Specification with guidance at the organization level for quantification and reporting of greenhouse gas emissions and removals
Introduction of ISO 14064-2:2018 Greenhouse gases — Part 2: Specification with guidance at the project level for quantification, monitoring and reporting of greenhouse gas emission reductions or removal enhancements
Introduction of ISO 14064-3:2018 Greenhouse gases — Part 3: Specification with guidance for the validation and verification of greenhouse gas assertions
DAY TWO
9.00 am - 10.30 am
- Example Scope 1 & 2 Calculations
- Interactive Exercise 3
- How to quantify and report GHG emissions
- Step-by-step inventory preparation
- Using the emission factors
- Fuel emission factors
- Stationary combustion fuel
- Transport fuel
- Biofuels and biomass
- Transmission and distribution losses for reticulated gases
- Purchased electricity, heat and steam emission factors
10.30 am - 10.45 am Tea Break
10.45 am - 1.00 pm
- Example Scope 3 Calculations & Challenges
- Interactive Exercise 4
- Fuel emission factors
- Refrigerant and other gases use emission factors
- Indirect business-related emission factors
- Travel emission factors
- Freight transport emission factors
1.00 pm - 2.00 pm Lunch
2.00 pm - 3.30 pm
- GHG Accounting in Corporations & Emissions Reports and Current State of GHG Accounting
- Why Corporations Should Measure GHG Emissions
- Investment Context Use Cases - Mandates & Compliance
- GHG Reductions & Planned Impact (Scope 4 Emissions)
3.30 pm - 3.45 pm Tea Break
3.45 pm - 5.00 pm
- Producing a GHG report
- Interpreting Emissions Reports
- Additional Tools & Resources
- Qualified Assessment
- Verification Procedure with Third Party
** Certificate of attendance will be awarded for those who completed the course
ABOUT THE FACILITATOR
MR MOHD SHAHARUDDIN
- Diploma in Industrial Chemistry, UiTM.
- BEng (Hons) Chemical Engineering, Univ. South Wales, UK
- Master of Environment, UPM
- Certified PSMB Trainer (Exemption)
Shaharuddin is an HSE Consultant and Trainer with more than 22 years of industrial related working experience. He specializes in providing training and consultancy services, especially in Dangerous Goods, Hazardous Chemicals, Hazardous Wastes, Process Plant Safety, Industrial Hygiene and Environmental Management. His HSE consultancies services covering various type of industries such as in oil & gas industries, chemical specialty plant, plastic & rubber based industry, automotive industries, pulp & paper manufacturing, woodworking industries, electroplating and electronic plant, steelmaking industries, food & beverage industries, paint manufacturing, construction industries, healthcare industries, utilities provider for water & wastewater treatment plant ,solid waste management company and an off-site facility for treatment and disposal of scheduled wastes.
Shaharuddin has experience as a registered Safety & Health Officer and as a Competent Person for Monitoring of Noise Exposure at Work with DOSH. He has involved in Dangerous Goods, Hazardous Chemicals or Scheduled Waste towards compliance program under the USECHH 2000 Regulation, UN Dangerous Goods Legislation and Scheduled Waste Regulation. He had a vast experience as a DOSH registered Assessor for Chemical Health Risk Assessment and also as an Industrial Hygiene Technician I & II, both for Testing and examination of Local Exhaust Ventilation and Chemical Exposure Monitoring. With these multiple industrial hygiene competencies, he had successfully conducted a great numbers of hazardous chemical assessment and monitoring projects throughout Malaysia. As a registered trainer with HRDF and DOSH, Shaharuddin has been actively conducting training on HSE particularly on Safe Handling of Hazardous Chemical/Dangerous Goods and Scheduled Waste Management. He has wide experience in conducting training and providing ISO consultancy to guide companies in implementing ISO 14001, OHSAS 18001 ,Carbon Footprint Assessment , Green Productivity Assessment, Life Cycle Assessment and Cleaner Production Program, for various types of industries in Malaysia. He also involve in giving training and consultancy to industries using chemicals in Chemical Management for Product Stewardship Program to comply with International Chemical Laws such as REACH, WEEE and RoHS.
Academically, Shaharuddin hold Diploma in Industrial Chemistry from UiTM. He also holds Bachelor Degree in Chemical Engineering ( Majoring in Process Safety, Environmental & Energy Management) from University of Glamorgan, Wales, UK and Master of Environmental Science from UPM with Project on Hazardous Chemical Management. He also holds Certificate in Indoor Air Quality Assessor from NIOSH, Certificate in Green Building Index Facilitator from Malaysia Green Building Council, Certificate of Green Productivity Trainer & Consultant from Asian Productivity Centre, Japan , a Certificate of Green Industry Auditor & Certificate of Environmental Auditor from Department of Environment, Malaysia and a Certificate of Energy Management System from UNIDO, and a Certificate in Z50 Green Technology Compliance – ILO-CIAST.
(SBL Khas / HRD Corp Claimable Course)
TRAINING FEE
2 days Face-to-Face Public Program
RM 2,250.00/pax
(excluded 8% SST)
Group Registration: Register 3 participants from the same organization, the 4th participant is FREE.
(Buy 3 Get 1 Free) if Register before 25 Feb 2025. Please act fast to grab your favourite training program!We hope you find it informative and interesting and we look forward to seeing you soon.
Please act fast to grab your favorite training program! Please call 012-588 2728
or email to pearl-otc@outlook.com
Do forward this email to all your friends and colleagues who might be interested to attend these programs
If you would like to unsubscribe from our email list at any time, please simply reply to the e-mail and type Unsubscribe in the subject area.
We will remove your name from the list and you will not receive any additional e-mail
Thanks
Regards
Pearl
by "sump@otcmsb.com.my" <sump@otcmsb.com.my> - 09:17 - 12 Jan 2025 -
Registration confirmation
Hi MD Abul,Thanks for registering for Master Odoo ERP Accounting Free Training! We're excited you can join us.DescriptionDiscover how to master Odoo ERP Accounting in this free 90-minute training, designed to help accountants, bookkeepers, and finance professionals streamline workflows, grow their careers, and serve clients with confidence.Date and timeTue, 14 Jan, 20:30 GMT+7See you soon!
by "StreamYard" <yourfriends@onair.streamyard.com> - 08:31 - 12 Jan 2025 -
Finish signing in to ByteByteGo Newsletter
Email from Substack
 Here’s a link to sign in to ByteByteGo Newsletter. This link can only be used once and expires in one hour. If expired, please try signing in again here.
Here’s a link to sign in to ByteByteGo Newsletter. This link can only be used once and expires in one hour. If expired, please try signing in again here.Sign in now © 2025 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104998
by "ByteByteGo" <bytebytego@substack.com> - 08:26 - 12 Jan 2025 -
Finish signing in to ByteByteGo Newsletter
Email from Substack
 Here’s a link to sign in to ByteByteGo Newsletter. This link can only be used once and expires in one hour. If expired, please try signing in again here.
Here’s a link to sign in to ByteByteGo Newsletter. This link can only be used once and expires in one hour. If expired, please try signing in again here.Sign in now © 2025 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104797
by "ByteByteGo" <bytebytego@substack.com> - 08:26 - 12 Jan 2025 -
Exploring Potential Partnership for High-Quality Brake Linings from Leading Manufacturer in China
Dear purchasing manager,
I am very glad to write to you! From the internet,we got your company information, I wonder if we have the chance to cooperate in the near future. We are a factory of brake lining in China, and we have been in this field for many years, so we are confident to support you competitive price and high quality.
If you need more information, please go to our website:https://www.zjcdbrakelining.com/.
Mayebe now you have regular partners if so, please leave my message in your emailbox. Maybe someday it will be useful. If you are interested,please kindly return us, well-trained engineer will offer you any technical support.
Yours sincerely
Sam
by "Lucas" <Lucas@zjcd-brakelining.com> - 07:25 - 12 Jan 2025 -
Discover the world of LEEMO TEA - your perfect tea partner
Dear customer
Hello! I am a representative from LEEMO TEA, a leading tea brand in China. Today, I am very honored to introduce you to our high-quality tea series, which not only represents our commitment to excellence, but also reflects our firm belief in sustainable development and social responsibility.
At LEEMO TEA, we know that tea is more than just a drink, it is a culture and a life attitude. Our tea leaves come directly from the most fertile tea gardens in China, and each leaf is carefully selected and processed to ensure that every sip is the ultimate enjoyment of taste.
Why choose LEEMO TEA?
Unparalleled quality: We promise to follow the highest standards at every step, from planting to packaging, to ensure that every leaf of tea can show its best flavor.
Sustainable and ethical: We are committed to sustainable agricultural practices, supporting local community development, protecting the environment, and making every cup of tea meaningful.
Diverse choices: Whether you prefer refreshing green tea, rich black tea or any other variety, LEEMO TEA can meet your needs and take you on a journey of taste buds.
Our mission is to bring the charm of tea to young people around the world and make tea a lifestyle, not just an everyday drink. If you are interested in our products or would like to discuss cooperation opportunities, please feel free to reply to this email. We look forward to starting this wonderful tea journey with you.
Thank you for considering LEEMO TEA as your tea supplier. We look forward to providing you with excellent products and services.
Best wishes!
LEEMO TEA Team
by "Ava" <Ava@starryshining.com> - 07:22 - 12 Jan 2025 -
Reliable Chinese manufacturer in the pigment industry
Dear info,
Good day.
This is Joanna from XT Pigment. We are a Manufacturing&Trading company for Iron Oxide Pigment with 25 years experience. I recently came across your company while researching potential partners in the pigment sector.
Our iron oxide pigment could be used for Cement, Concrete, Paint, Mulch&Fertilizer with high Coverage&excellent Weather Resistance. Please advise your main application and I will quote you accordingly.
Free sample with 200g, 300g or 500g for quality evaluation. Attachments for your reference, please kindly check it.
Hope we could do help you in this field and create a win-win situation. Looking forward to your reply.
Best Regards,
Joanna

by "Jean Max" <xbjmlq@gmail.com> - 01:56 - 12 Jan 2025 -
Connect with Confidence: Telsto’s Comprehensive RF Connector Solutions!
Hello info,
Nice day!
Telsto supply site materials for mobile towers like RF Connectors, Coaxial Jumper & Feeder Cables, Gel Seal Closure, Cold Shrink Tube, Leaky Clamp, Hoisting Grip etc.
Telsto connectors are designed and produced to own features as below.

· High quality materials, excellent V.S.W.R performance and low intermodulation.
· Fast and easy installation.
· Waterproof IP68.
· Supply customized services.
· Environment resistance ensures long life and consistent performance.
Any questions please kindly contact us without hesitation, we'd be glad to support.
Best regards,
Mattelyn bokan
by "Mattelyn bokan" <mattelynbokan9108932@gmail.com> - 01:49 - 12 Jan 2025 -
Shenzhen HUANET Provide DWDM/OTN FTTH solution
We have over 20 years experience on the fiber optic products. We research and develop the DWDM/ONT/DCI System, we provide Huawei/zte /Fiberhome OLT and ONU, optical module and swtich. Contact me for more information! Africa Tech Festival,Date: November 12th~14th, 2024,Booth No.:D91A.
by "Anna" <Anna@szhuanet.com> - 06:55 - 11 Jan 2025 -
Unlock Your Production Potential with Our powder compacting press !
Dear info,
I hope this message finds you well!
I’m Jerry from Dongguan Yihui Hydraulic Machinery Co., Ltd., and I’m excited to introduce you to our top-selling powder compacting press .
Are you currently producing components that require precision and efficiency? If so, I would love to learn more about your products and the materials you use. Understanding your specific needs will help us recommend the ideal force and configuration for your operations.
Our powder compacting press has gained popularity across the globe, with satisfied customers in the United States, Germany, South Africa, and many more. With 24 years of experience, we pride ourselves on delivering high-quality machinery at competitive prices, backed by international certifications like CE and ISO.
Please feel free to share your product drawings and specifications, and let’s explore how we can enhance your production line together!
Looking forward to your response.
Best Regards,
Jerry
WA:+8613925853679
by "Jawa Bayudan" <jawabayudan@gmail.com> - 05:18 - 11 Jan 2025 -
The week in charts
The Week in Charts
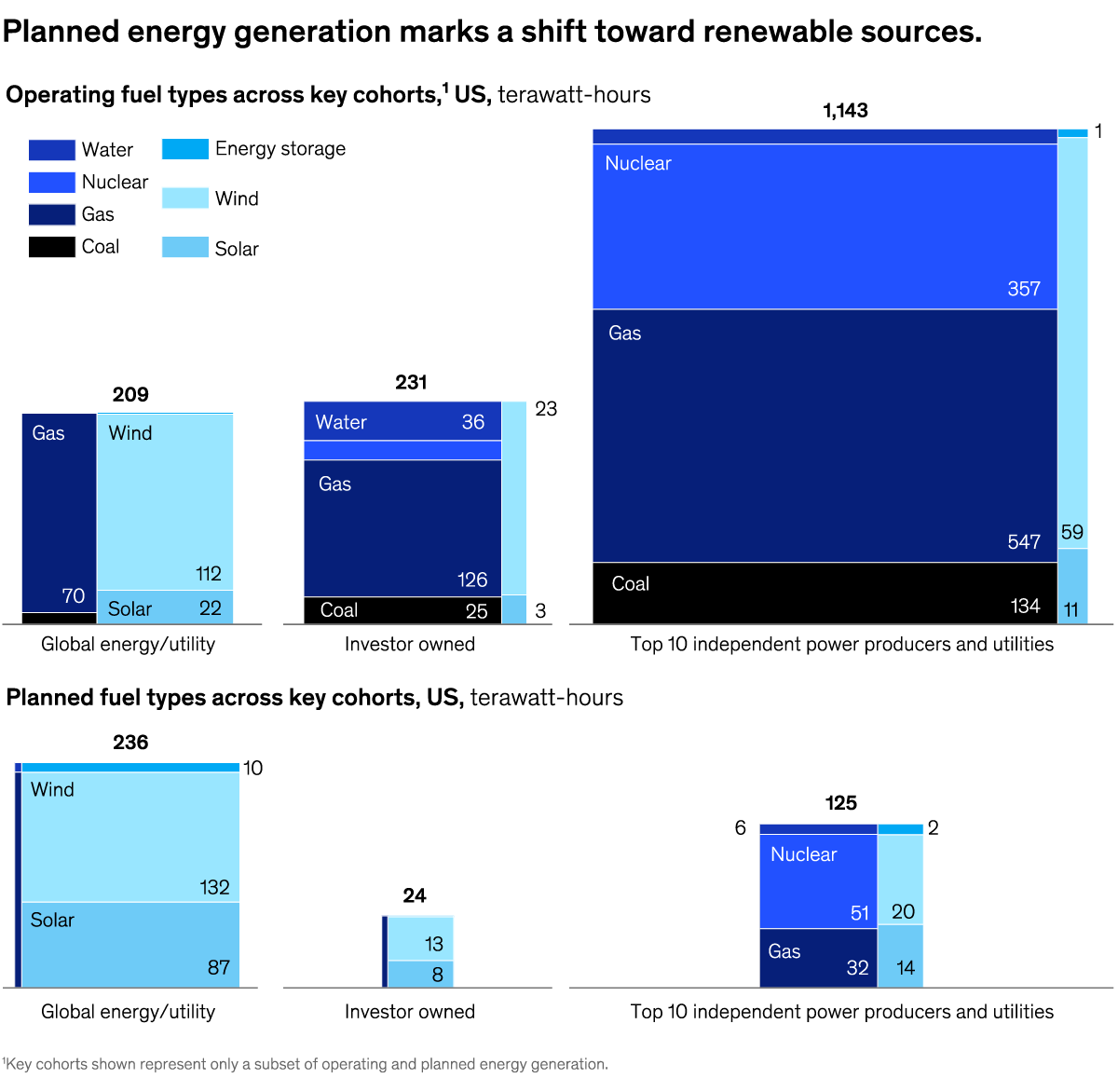
Renewable energy sources, shifts in global trade, and more Share these insights
Did you enjoy this newsletter? Forward it to colleagues and friends so they can subscribe too. Was this issue forwarded to you? Sign up for it and sample our 40+ other free email subscriptions here.
This email contains information about McKinsey's research, insights, services, or events. By opening our emails or clicking on links, you agree to our use of cookies and web tracking technology. For more information on how we use and protect your information, please review our privacy policy.
You received this email because you subscribed to The Week in Charts newsletter.
Copyright © 2025 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "McKinsey Week in Charts" <publishing@email.mckinsey.com> - 03:31 - 11 Jan 2025 -
EP145: Infrastructure as Code Landscape
EP145: Infrastructure as Code Landscape
This week’s system design refresher:͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ Forwarded this email? Subscribe here for more✂️Cut your QA cycles down to minutes with QA Wolf (Sponsored)
If slow QA processes bottleneck you or your software engineering team and you’re releasing slower because of it — you need to check out QA Wolf.
Their AI-native approach gets engineering teams to 80% automated end-to-end test coverage and helps them ship 5x faster by reducing QA cycles from hours to minutes.
QA Wolf takes testing off your plate. They can get you:
Unlimited parallel test runs
24-hour maintenance and on-demand test creation
Human-verified bug reports sent directly to your team
Zero flakes guaranteed
The benefit? No more manual E2E testing. No more slow QA cycles. No more bugs reaching production.
With QA Wolf, Drata’s team of 80+ engineers achieved 4x more test cases and 86% faster QA cycles.
This week’s system design refresher:
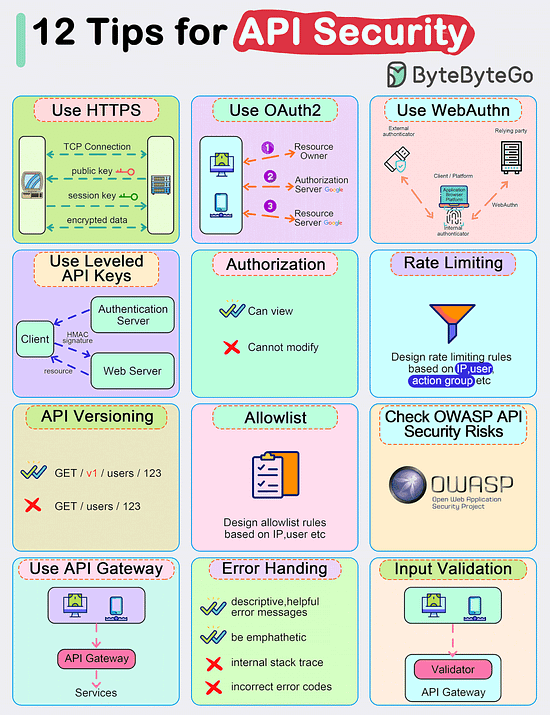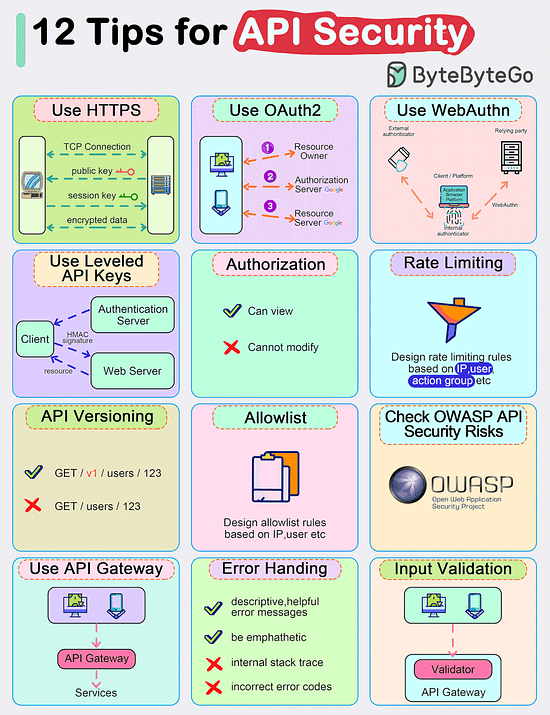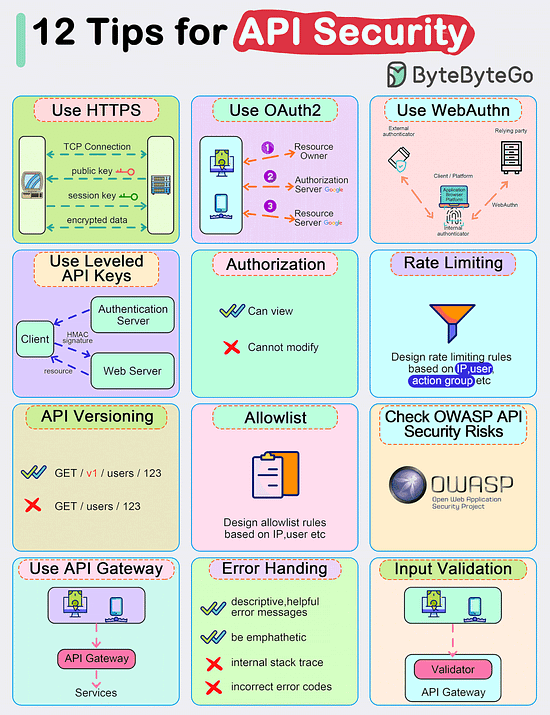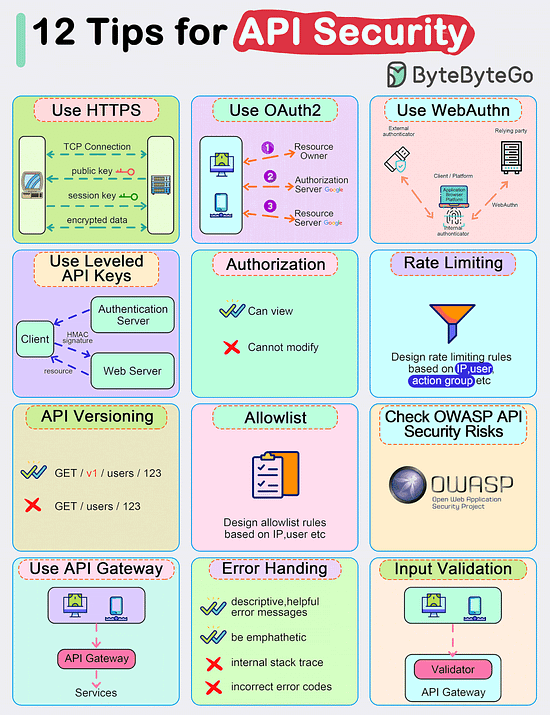
Top 12 Tips for API Security
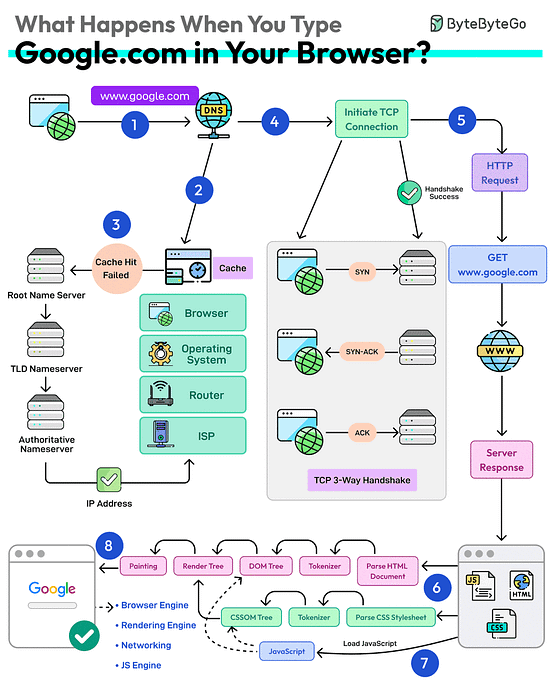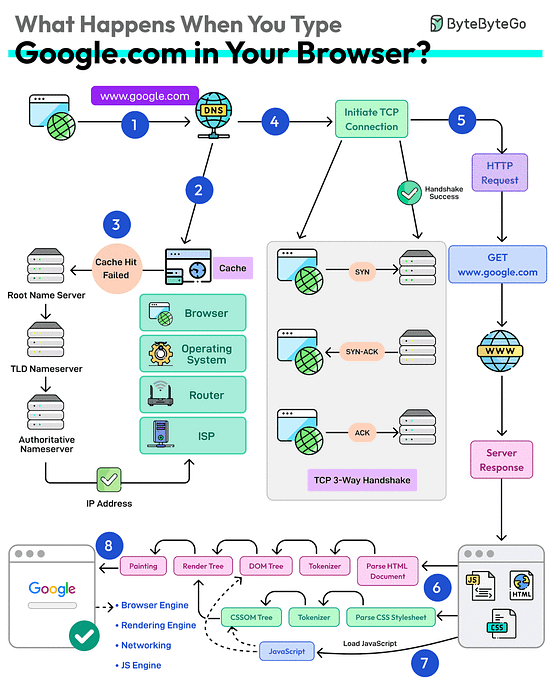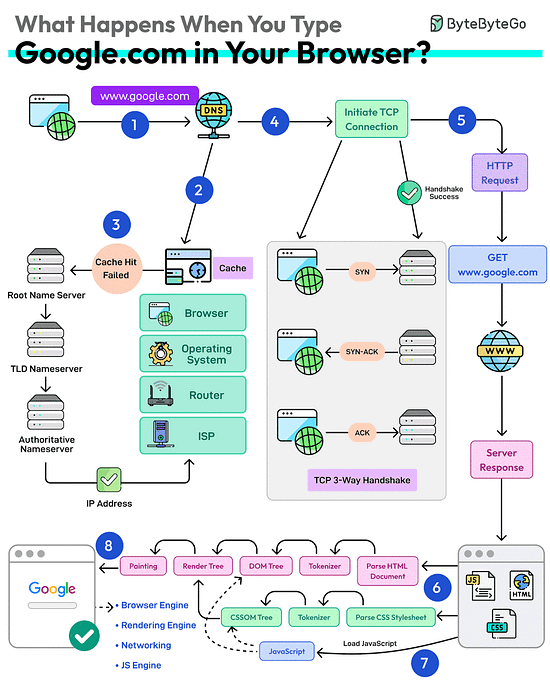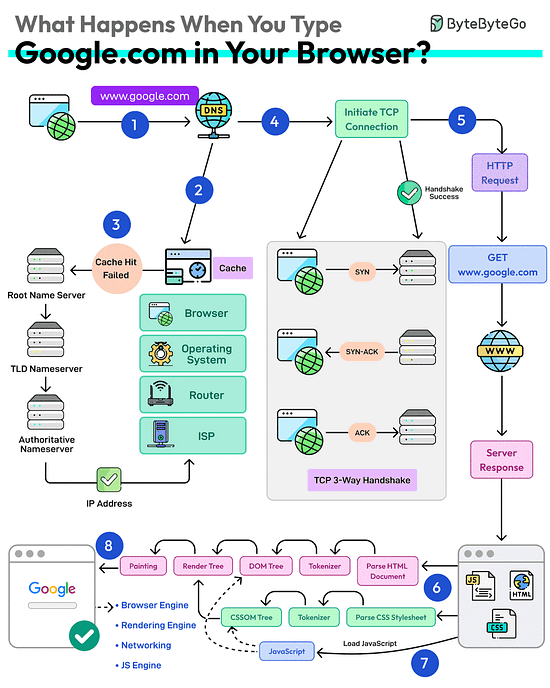
What happens when you type google .com into a browser?
A Cheatsheet on Infrastructure as Code Landscape
Why is Kafka fast?
A Crash Course on Architectural Scalability
SPONSOR US
Top 12 Tips for API Security
Use HTTPS
Use OAuth2
Use WebAuthn
Use Leveled API Keys
Authorization
Rate Limiting
API Versioning
Whitelisting
Check OWASP API Security Risks
Use API Gateway
Error Handling
Input Validation
What happens when you type google .com into a browser?
First up, you type the website address in the browser’s address bar.
The browser checks its cache first. If there’s a cache miss, it must find the IP address.
DNS lookup begins (think of it as looking up a phone number). The request goes through different DNS servers (root, TLD, and authoritative). Finally, the IP address is retrieved.
Next, your browser initiates a TCP connection like a handshake. For example, in the case of HTTP 1.1, the client and server perform a TCP three-way handshake with SYN, SYN-ACK, and ACK messages.
Once the handshake is successful, the browser makes an HTTP request to the server and the server responds with HTML, CSS, and JS files.
Finally, the browser processes everything. It parses the HTML document and creates DOM and CSSOM trees.
The browser executes the JavaScript and renders the page through various steps (tokenizer, parser, render tree, layout, and painting).
Finally, the webpage appears on your screen.
Over to you: Which other step will you add to the overall process?
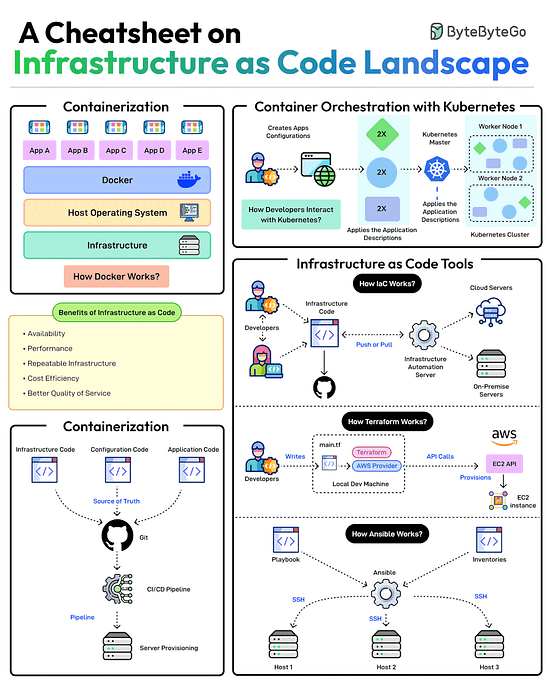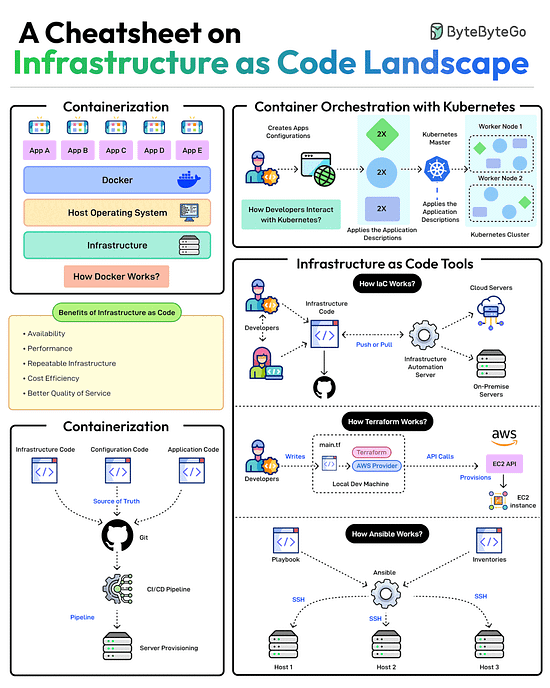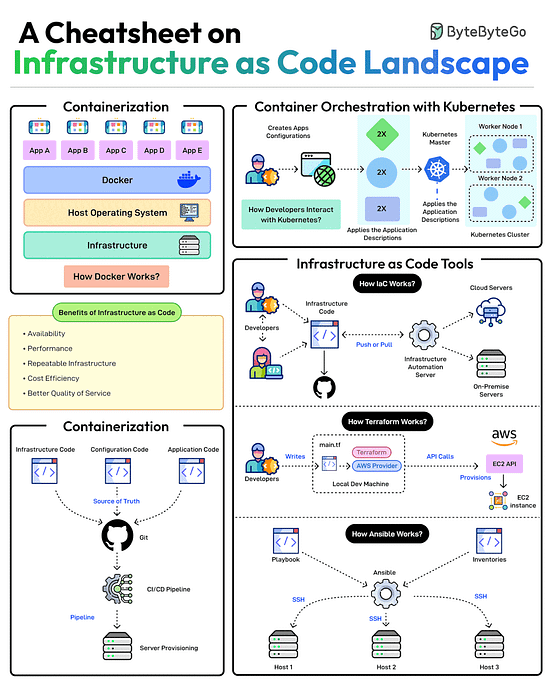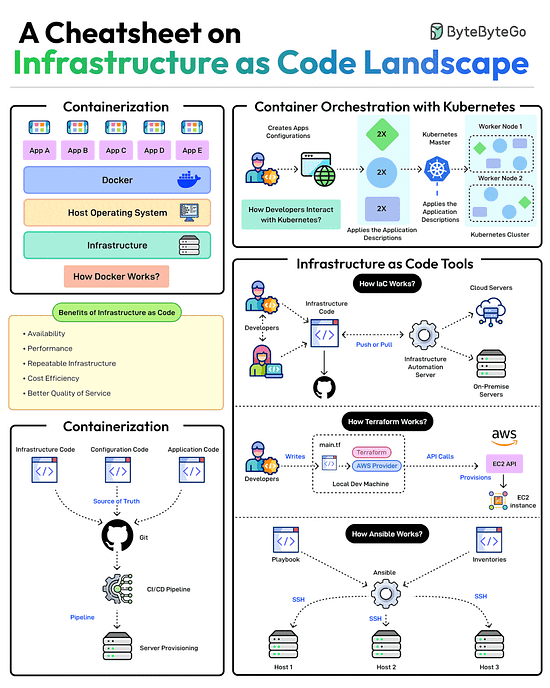
A Cheatsheet on Infrastructure as Code Landscape
Scalable infrastructure provisioning provides several benefits related to availability, scalability, repeatability, and cost-effectiveness.
But how do you achieve this?
Provisioning infrastructure using code is the key to scalable infra management.
There are multiple strategies that can help:Containerization is one of the first strategies to make application deployments based on code. Docker is one of the most popular ways to containerize the application.
Next, container orchestration becomes a necessity when dealing with multiple containers in an application. This is where container orchestration tools like Kubernetes become important.
IaC treats infrastructure provisioning and configuration as code, allowing developers to define the application infrastructure in files that can be versioned, tested, and reused. Popular tools such as Terraform, AWS CloudFormation, and Ansible can be used. Ansible is more of a configuration tool.
GitOps leverages a Git workflow combined with CI/CD to automate infrastructure and configuration updates.
Over to you: Have you used Infrastructure as Code for your projects?
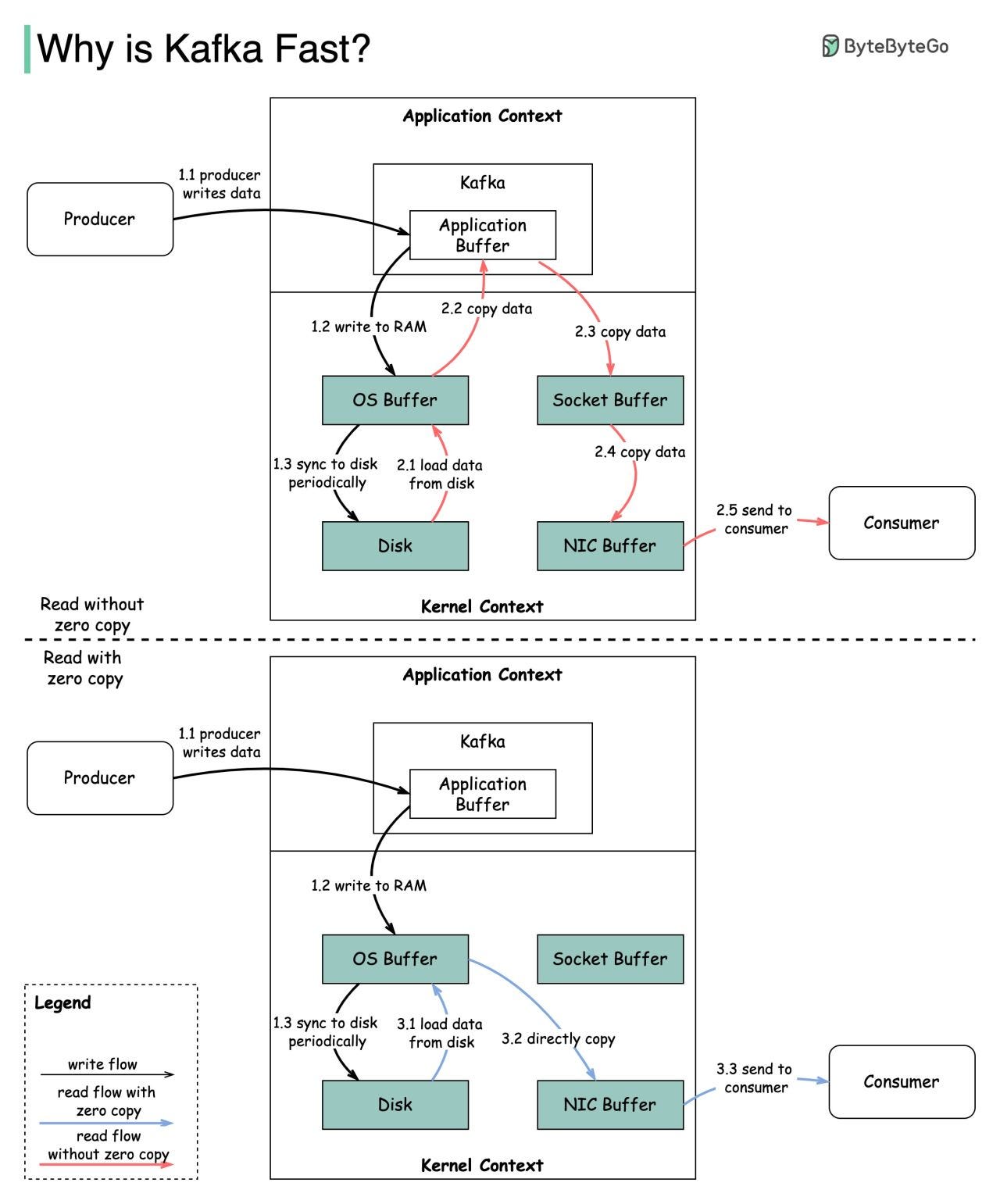
Why is Kafka fast?
There are many design decisions that contributed to Kafka’s performance. In this post, we’ll focus on two. We think these two carried the most weight.
The first one is Kafka’s reliance on Sequential I/O.
The second design choice that gives Kafka its performance advantage is its focus on efficiency: zero copy principle.
The diagram below illustrates how the data is transmitted between producer and consumer, and what zero-copy means.
Step 1.1 - 1.3: Producer writes data to the disk
Step 2: Consumer reads data without zero-copy
2.1: The data is loaded from disk to OS cache
2.2 The data is copied from OS cache to Kafka application
2.3 Kafka application copies the data into the socket buffer
2.4 The data is copied from socket buffer to network card
2.5 The network card sends data out to the consumerStep 3: Consumer reads data with zero-copy
3.1: The data is loaded from disk to OS cache
3.2 OS cache directly copies the data to the network card via sendfile() command
3.3 The network card sends data out to the consumer
Zero copy is a shortcut to save multiple data copies between the application context and kernel context.
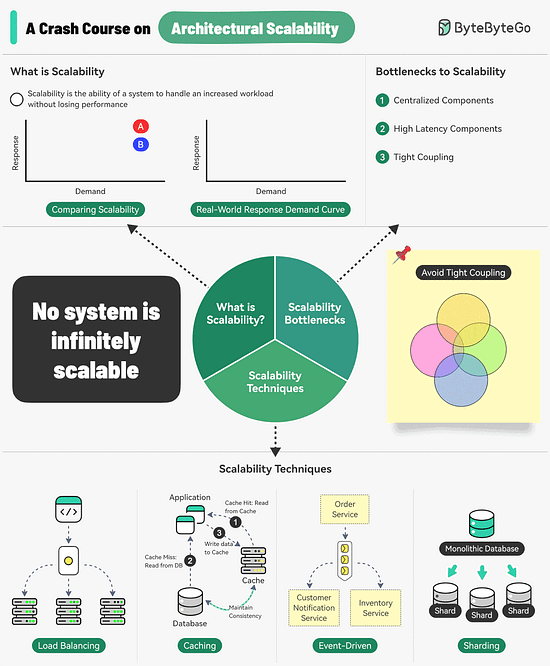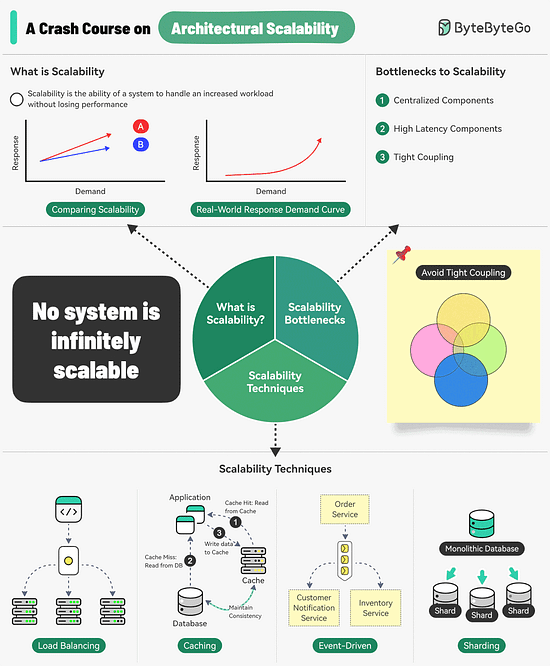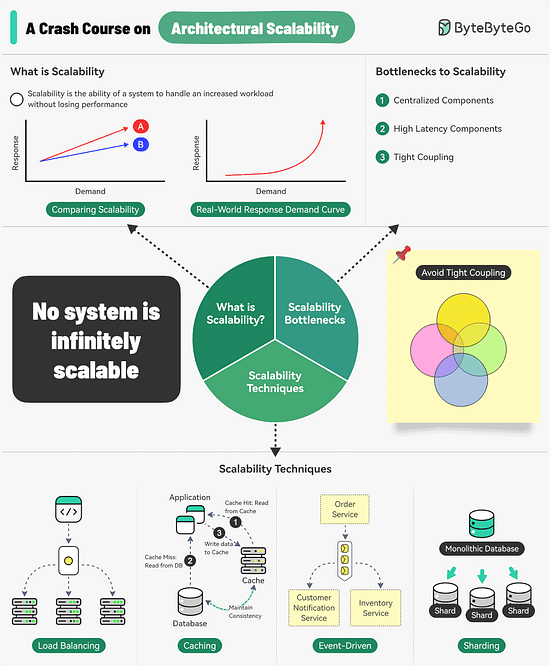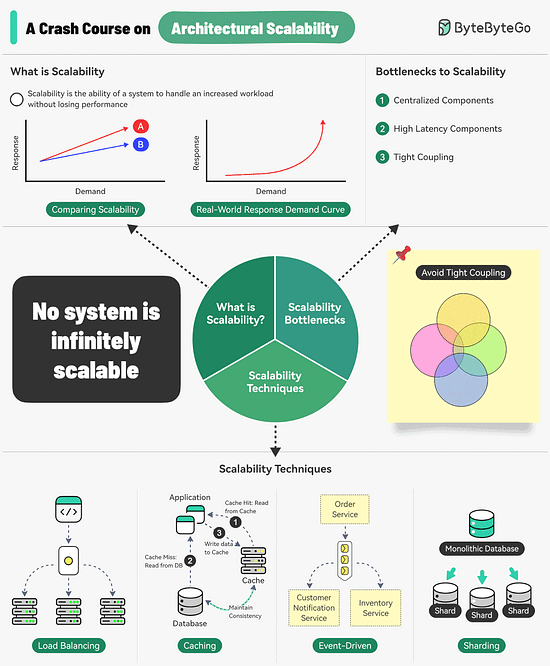
A Crash Course on Architectural Scalability
Scalability is the ability of a system to handle an increased workload without losing performance.
However, we can also look at scalability in terms of the scaling strategy.
Scalability is the system’s ability to handle an increased workload by repeatedly applying a cost-effective strategy. This means it can be difficult to scale a system beyond a certain point if the scaling strategy is not financially viable.
Three main bottlenecks to scalability are:Centralized components: This can become a single point of failure
High Latency Components: These are components that perform time-consuming operations.
Tight Coupling: Makes the components difficult to scale
Therefore, to build a scalable system, we should follow the principles of statelessness, loose coupling, and asynchronous processing.
Some common techniques for improving scalability are as follows:Load Balancing: Spread requests across multiple servers to prevent a single server from becoming a bottleneck.
Caching: Store the most commonly request information in memory.
Event-Driven Processing: Use an async processing approach to process long-running tasks.
Sharding: Split a large dataset into smaller subsets called shards for horizontal scalability.
Over to you: How do you improve a system’s scalability?
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com.
Like
Comment
Restack
© 2025 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe
by "ByteByteGo" <bytebytego@substack.com> - 11:35 - 11 Jan 2025 -
High-Quality Outdoor Gear Your Customers Will Love
Dear [Recipient’s Name],
At Miki Travel Essentials, we know that your customers demand the best when it comes to outdoor gear. That’s why we’ve developed a range of premium camping equipment, e-bikes, and e-scooters that combine durability, functionality, and style.
Our products are perfect for the adventurous spirit, offering everything from UV-protection tents to foldable electric scooters designed for easy transport. We’re confident that our gear will resonate with your customer base and help you stand out in a competitive market.
Could we arrange a brief call to explore how our products can fit into your inventory?
Deal or no deal, we are always here 24/7.
Best regards,
Fathima Ahmed
Manufacturing Director
Miki Travel Essentials Co., Ltd.
by "Silvana Anelli" <silvanaanelli366@gmail.com> - 11:21 - 11 Jan 2025 -
Desarrollar una fuerza de trabajo resiliente y adaptable
Además, IA para la modernización de TI En el incierto y volátil entorno empresarial actual, los líderes del siglo XXI necesitan una fuerza laboral comprometida e innovadora que pueda cambiar de rumbo con rapidez, eficacia y fluidez, escriben Jacqueline Brassey, Aaron De Smet, Dana Maor y Sheida Rabipour. En nuestro artículo principal, describen cómo los líderes pueden crear resiliencia y adaptabilidad a gran escala. Otros temas destacados son:
•
Cómo las asociaciones no convencionales pueden ayudar a los promotores inmobiliarios
•
Qué pueden hacer las empresas para aplicar eficazmente la IA generativa para modernizar la tecnología heredada y reducir la deuda técnica
•
Construir un sistema de equipos sanos para impulsar un cambio duradero
•
El potencial de la electrificación térmica para descarbonizar la industria y apoyar el objetivo de cero emisiones netas
La selección de nuestros editores
LOS DESTACADOS DE ESTE MES

Asociaciones no convencionales: La ventaja innovadora del promotor inmobiliario
Los promotores inmobiliarios globales pueden alcanzar un éxito duradero mediante colaboraciones estrechas con socios no tradicionales. Aquí explicamos cómo.
Explore nuevos caminos
IA para la modernización de TI: Más rápida, más barata, mejor
Los agentes de IA generativa están comenzando a ofrecer un valor revolucionario, pero solo cuando las empresas descubren cómo construir y orquestar cientos de ellos.
Mejore los resultados
Abordar la electrificación térmica para descarbonizar la industria
La mayor parte de la producción de calor industrial (más del 20 por ciento del consumo mundial de energía) se genera con combustibles fósiles. Las tecnologías de electrificación térmica pueden ayudar a descarbonizar la industria y apoyar el objetivo de cero emisiones netas.
Dé el paso correcto
El contexto es clave: Tanguy Catlin sobre el futuro de los seguros
Para aprovechar todo el valor de la inteligencia artificial generativa, los líderes de seguros deben saber cómo funciona y qué problemas puede –y no puede– resolver. Asimismo, los datos y el contexto son vitales para innovar soluciones a las demandas cambiantes.
Prepárese para el mañana
Invertir en el futuro de la tecnología: Lecciones de empresas ganadoras
Los resultados de la encuesta sugieren que, si bien las perspectivas generales para las inversiones en tecnología son sólidas, solo unas pocas empresas están invirtiendo en las bases y las personas que pueden respaldar el éxito futuro.
Apueste por el futuro
Es todo sobre los equipos: Un nuevo enfoque de la transformación organizacional
Los equipos son los catalizadores que impulsan el valor y los nuevos comportamientos, pero no todos son iguales. Cuatro acciones ayudan a construir un sistema de equipos sanos para promover un cambio duradero.
Aproveche el potencialEsperamos que disfrute de los artículos en español que seleccionamos este mes y lo invitamos a explorar también los siguientes artículos en inglés.

McKinsey Explainers
Find direct answers to complex questions, backed by McKinsey’s expert insights.
Learn more
McKinsey Themes
Browse our essential reading on the topics that matter.
Get up to speed
McKinsey on Lives & Legacies
Monthly obituaries from business and society, highlighting the lasting legacies of executives and leaders from around the globe.
Explore the latest obituaries
Leading Off
Each Monday, let McKinsey’s editors help you get ready to take on the leadership challenges of the coming week, through revealing research, inspiring interviews, and insightful quotations to empower you and those you lead.
Get it in your inbox weekly
McKinsey Classics
Engaging customers today requires commitment from the entire company—and a redefined marketing organization. Read our 2011 classic “We’re all marketers now” to learn more.
Rewind
Mind the Gap
Biweekly curated reads on Gen Z in the workplace.
Subscribe now— Edited by Joyce Yoo, editor, New York
COMPARTA ESTAS IDEAS
¿Disfrutó este boletín? Reenvíelo a colegas y amigos para que ellos también puedan suscribirse. ¿Se le remitió este articulo? Regístrese y pruebe nuestras más de 40 suscripciones gratuitas por correo electrónico aquí.
Este correo electrónico contiene información sobre la investigación , los conocimientos, los servicios o los eventos de McKinsey. Al abrir nuestros correos electrónicos o hacer clic en los enlaces, acepta nuestro uso de cookies y tecnología de seguimiento web. Para obtener más información sobre cómo usamos y protegemos su información, consulte nuestra política de privacidad.
Recibió este correo electrónico porque es un miembro registrado de nuestro boletín informativo Destacados.
Copyright © 2025 | McKinsey & Company, 3 World Trade Center, 175 Greenwich Street, New York, NY 10007
by "Destacados de McKinsey" <publishing@email.mckinsey.com> - 08:13 - 11 Jan 2025 -
NEW FHL speaker just announced (+ FREE bonus)
From vacuum salesman to running a MULTI-MILLION DOLLAR internet marketing empire…I really hope you didn’t miss my live interview today with our newly-announced, PHENOMENAL Funnel Hacking Live 10 speaker, Armand Morin!!
WATCH THE INTERVIEW REPLAY W/ ARMAND MORIN HERE →
You may not immediately recognize his name, but I guarantee this man has influenced the way you do business FAR more than you realize!!
Almost 30 years ago he started out with $1.83 to his name and zero experience…
Today Armand’s internet marketing business has grown into an international, MULTI-MILLION DOLLAR empire.
This is the genius that not only taught me how to drastically increase my sales using the game-changing “stack and close” technique…
He IS THE ORIGINATOR of the “stack and close”!!
As my original mentor, Armand has helped me and literally thousands of other entrepreneurs take their businesses from humble beginnings to wild successes… after simply incorporating his incredibly easy-to-understand methods!
And now, when you secure your FHL tickets ASAP, you’ll not only get to learn from one of the OG pioneers of internet marketing, you also get access to his extremely valuable bonus (which you can find out here in the interview)
I’ll let you find out directly from Armand what his bonus is in the replay, but I’ll just say that I am SHOCKED he’s willing to give this kind of information away FOR FREE.
With this added knowledge in your toolkit, the effectiveness of your stack and close will be absolutely MULTIPLIED.
REMEMBER: When you secure your FHL 10 ticket ASAP you get access to ALL of the following speaker bonuses –-
Ashley Kirkwood’s Bonus! The “cheat sheet” that will not only help INCREASE your engagement and sales… but can change your entire business model into the one you’ve always wanted!! (Watch Ashley’s bonus reveal HERE→)
- Eileen Wilder’s Bonus! Hours of coaching content teaching you her framework of persuasion and influence you can use absolutely ANYWHERE to maximize influence and quickly increase sales!! (Watch Eileen’s bonus reveal HERE→)
-
Tim Shields’ Bonus! THE essential webinar-building companion that will help you create your expert level, game-changing webinar faster than you ever thought possible! (Watch Tim’s bonus reveal HERE→)
-
Trent Shelton’s Bonus! Become a more confident and successful speaker and overall expert communicator with Trent’s extremely beneficial training that will help you improve in ALL areas of selling! (Watch Trent’s bonus reveal HERE→)
- Armand Morin’s Bonus! Discover the exact formula Armand uses to compound the effectiveness of the “stack and close” system! (Watch Armand’s bonus reveal HERE→)
- The FREE bonuses of ALL the remaining FHL 10 speakers I have yet to reveal!!
I’ll be going live again NEXT WEEK to reveal another FHL 10 speaker as well as their FREE bonus…
This speaker is an absolute POWERHOUSE. If you’ve ever struggled in your journey of becoming the parent, entrepreneur, spouse, partner or LEADER you know you were meant to be… then this person will help you rise up and become that person. Period.
Keep your eyes peeled on Monday for an email with the link to watch the LIVE reveal!!
See you there!
Russell Brunson
P.S. Don’t forget, you’re just one funnel away…
© Etison LLC
By reading this, you agree to all of the following: You understand this to be an expression of opinions and not professional advice. You are solely responsible for the use of any content and hold Etison LLC and all members and affiliates harmless in any event or claim.
If you purchase anything through a link in this email, you should assume that we have an affiliate relationship with the company providing the product or service that you purchase, and that we will be paid in some way. We recommend that you do your own independent research before purchasing anything.
Copyright © 2018+ Etison LLC. All Rights Reserved.
To make sure you keep getting these emails, please add us to your address book or whitelist us. If you don't want to receive any other emails, click on the unsubscribe link below.
Etison LLC
3443 W Bavaria St
Eagle, ID 83616
United States
by "Russell Brunson" <noreply@clickfunnelsnotifications.com> - 10:41 - 10 Jan 2025 -
Ashley Kirkwood’s Bonus! The “cheat sheet” that will not only help INCREASE your engagement and sales… but can change your entire business model into the one you’ve always wanted!! (Watch Ashley’s bonus reveal HERE→)
-
Cost-Effective Solutions for Plastic, Die-Casting, and Metal Parts
Hello,
Our company is specialized in designing and manufacturing plastic parts, die-casting parts, metal stamping parts, and metal parts for over 18 years.
Our strengths:
1) Complete industrial support facilities, located in a renowned manufacturing base in China.
2) Over 18 years of experience in engineering, design, and manufacturing custom parts.
3) Competitive prices backed by a strong material supply chain and efficient management.
If you have any new projects, you could consider if we would be a good fit.
Best Regards
Tina
 Gain Power Industries Limited
Gain Power Industries LimitedWork Mobile / WA: +86 133 3265 4817
Website:www.majortooling.com
HengCheng Road No6, XinAn Community,ChangAn town
DongGuan, GuangDong,China 523882
by "Favyola Dzip" <favyoladzip968@gmail.com> - 04:37 - 10 Jan 2025 -
Cost-Effective Solutions for Plastic, Die-Casting, and Metal Parts
Hello,
Our company is specialized in designing and manufacturing plastic parts, die-casting parts, metal stamping parts, and metal parts for over 18 years.
Our strengths:
1) Complete industrial support facilities, located in a renowned manufacturing base in China.
2) Over 18 years of experience in engineering, design, and manufacturing custom parts.
3) Competitive prices backed by a strong material supply chain and efficient management.
If you have any new projects, you could consider if we would be a good fit.
Best Regards
Tina
 Gain Power Industries Limited
Gain Power Industries LimitedWork Mobile / WA: +86 133 3265 4817
Website:www.majortooling.com
HengCheng Road No6, XinAn Community,ChangAn town
DongGuan, GuangDong,China 523882
by "Meshach Bodey" <meshachbodey@gmail.com> - 03:50 - 10 Jan 2025