Archives
- By thread 5362
-
By date
- June 2021 10
- July 2021 6
- August 2021 20
- September 2021 21
- October 2021 48
- November 2021 40
- December 2021 23
- January 2022 46
- February 2022 80
- March 2022 109
- April 2022 100
- May 2022 97
- June 2022 105
- July 2022 82
- August 2022 95
- September 2022 103
- October 2022 117
- November 2022 115
- December 2022 102
- January 2023 88
- February 2023 90
- March 2023 116
- April 2023 97
- May 2023 159
- June 2023 145
- July 2023 120
- August 2023 90
- September 2023 102
- October 2023 106
- November 2023 100
- December 2023 74
- January 2024 75
- February 2024 75
- March 2024 78
- April 2024 74
- May 2024 108
- June 2024 98
- July 2024 116
- August 2024 134
- September 2024 130
- October 2024 141
- November 2024 171
- December 2024 115
- January 2025 216
- February 2025 140
- March 2025 220
- April 2025 233
- May 2025 239
- June 2025 303
- July 2025 175
-
How Airbnb Built a Key-Value Store for Petabytes of Data
How Airbnb Built a Key-Value Store for Petabytes of Data
Disclaimer: The details in this post have been derived from the Airbnb Technical Blog.͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ Forwarded this email? Subscribe here for moreHow to Diagram Your Cloud Architecture (Sponsored)
Get best practices from AWS solutions architects for diagramming your cloud architecture.
Cloud architecture diagrams provide critical visibility into the resources in your environment and how they’re connected. In our latest eBook, AWS Solution Architects Jason Mimick and James Wenzel walk through best practices on how to build effective and professional diagrams.Disclaimer: The details in this post have been derived from the Airbnb Technical Blog. All credit for the technical details goes to the Airbnb engineering team. The links to the original articles are present in the references section at the end of the post. We’ve attempted to analyze the details and provide our input about them. If you find any inaccuracies or omissions, please leave a comment, and we will do our best to fix them.
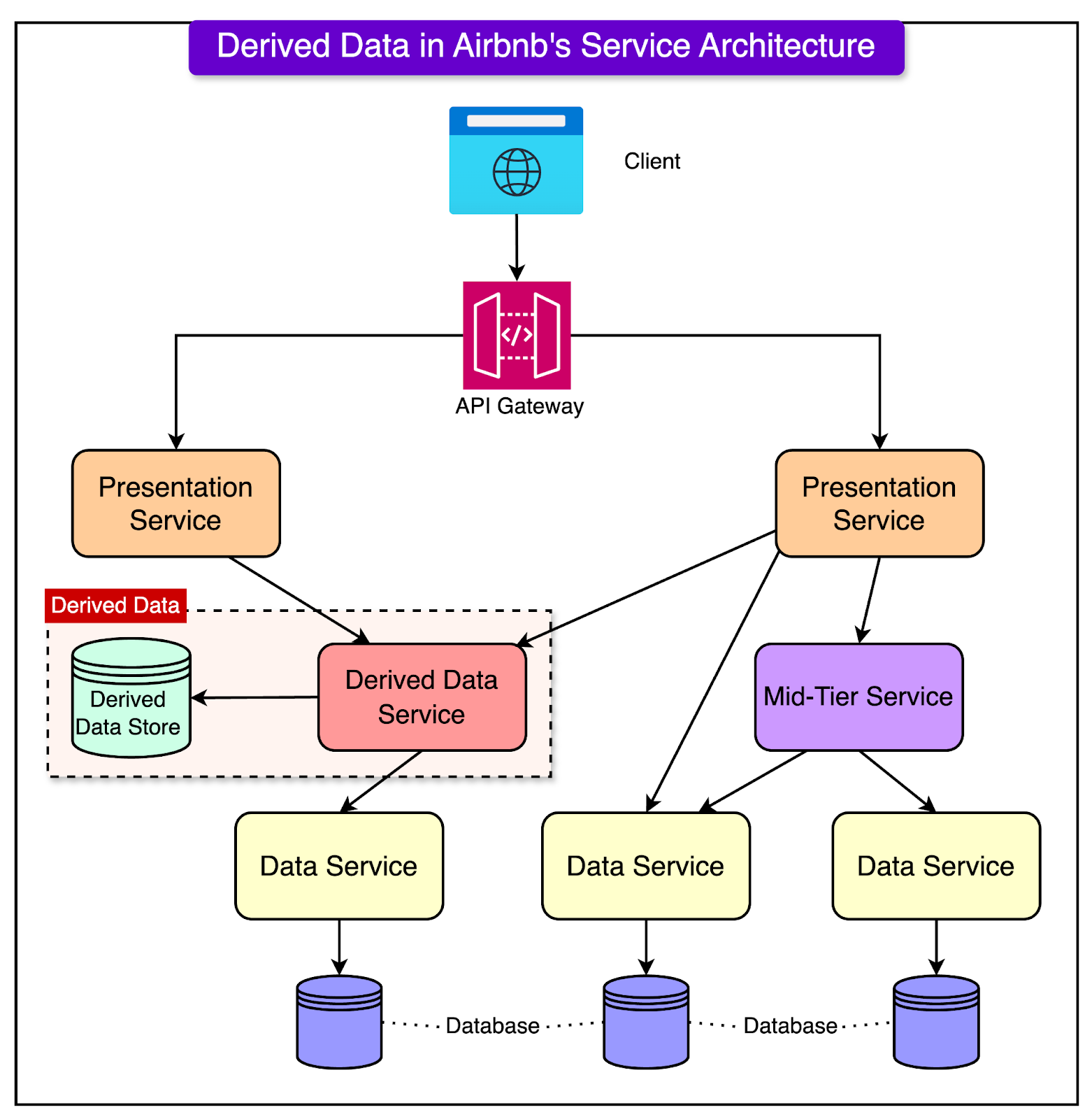
Airbnb's services rely on more than just raw data. They also depend on derived data.
But what is derived data?
It is information computed from massive offline datasets processed by tools like Spark or real-time event streams from systems like Kafka. This derived data is crucial for enabling personalized features, such as tailoring a user’s experience based on activity history and other similar features.
See the diagram below that shows the role of derived data in Airbnb’s overall service architecture.
However, accessing this data efficiently poses unique challenges.
The system supporting these services must be exceptionally reliable to ensure uninterrupted functionality.
It must offer high availability so data can be accessed anytime without delays, and it needs to handle scalability, supporting the ever-growing data demands of a platform as large as Airbnb.
Finally, low latency is critical since no one wants to wait while a system lags in fetching information.
This is where Mussel comes in.
Built to meet these stringent requirements, it’s a key-value store designed to ensure Airbnb’s services can retrieve the right data at the right time.
In this article, we’ll understand the architecture of Mussel and learn how Airbnb built this key-value store to manage petabytes of data.
Evolution of Derived Data Storage at Airbnb
Mussel wasn’t the first solution that Airbnb used to store derived data. Before the brand-new key-value store became a reality, there were other solutions implemented by the Airbnb engineering team.
Let’s go through the main stages of this evolution:
Stage 1: Unified Read-Only Key-Value Store
During the early stages of Airbnb's journey to handle derived data effectively, they faced several technical challenges. Existing tools like MySQL, HBase, and RocksDB couldn't meet the demanding requirements such as:
Managing petabytes of data
Allowing fast bulk uploads
Providing low-latency access for quick responses
Supporting multi-tenancy so multiple teams could use the system simultaneously
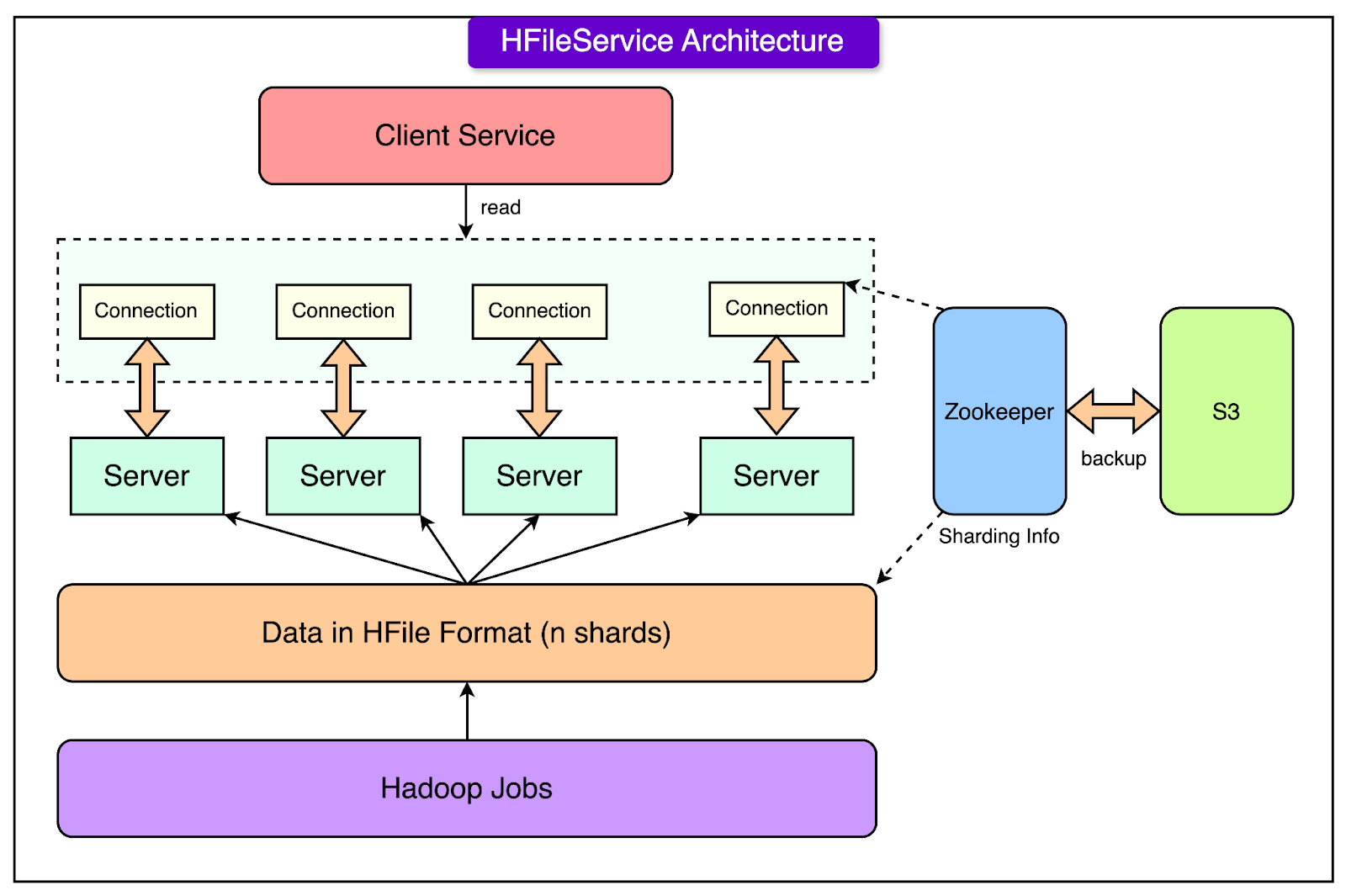
To address these needs, Airbnb created HFileService in 2015. It was a custom solution built using HFile, which is a building block for HBase and based on Google’s SSTable.
See the diagram below for the architecture of HFileService:
Here's how it worked:
Scalability Through Sharding and Replication:
Data was divided into smaller pieces, or "shards," based on primary keys. This approach spread the data across multiple servers, making the system scalable as data grew.
The number of shards was fixed. Each shard was replicated across multiple servers, ensuring high reliability. If one server failed, others could still serve the data.
Manual Partition Management with Zookeeper:
Zookeeper, a tool for managing distributed systems, was used to keep track of which shards were stored on which servers.
However, this mapping had to be updated manually, making it difficult to scale as data and usage increased.
Daily Batch Updates Using Hadoop:
Data updates were processed offline using Hadoop jobs that ran once daily. These jobs converted raw data into the HFile format, which was then uploaded to cloud storage (S3).
Servers downloaded their assigned shards from S3 and replaced outdated data locally.
While HFileService solved many problems, it had significant limitations:
It only supported read operations, meaning data couldn't be updated in real-time. If new data was added, users had to wait for the next day's batch process to access it.
The reliance on a daily processing cycle made the system less flexible and unsuitable for real-time or rapidly changing data needs.
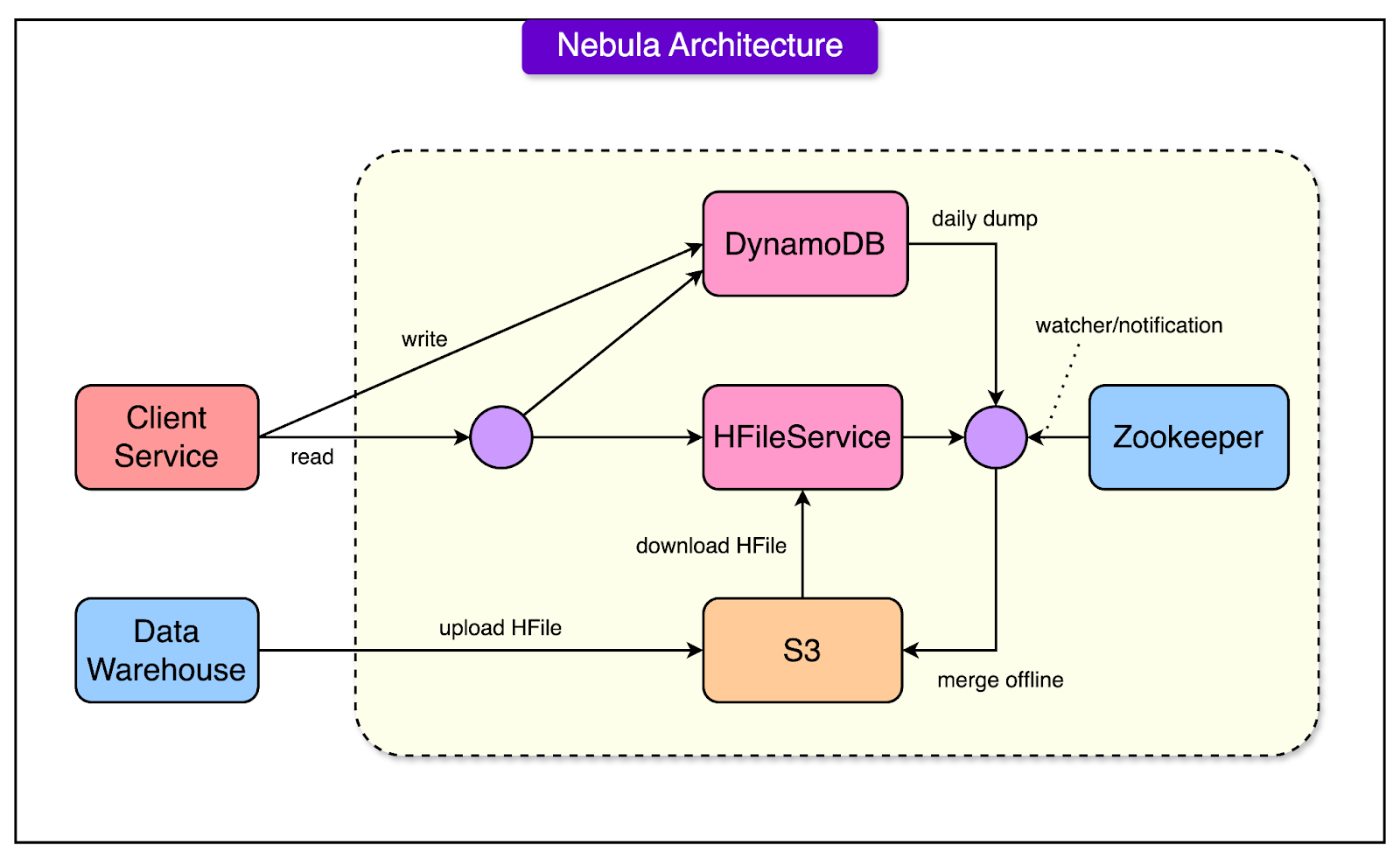
Stage 2: Real-Time and Derived Data Store (Nebula)
In the second stage of evolution, Airbnb introduced Nebula, a system designed to bridge the gap between batch-processed data and the growing need for real-time data access.
See the diagram below to understand the architecture of Nebula.
Nebula brought several important enhancements to improve upon the limitations of its predecessor, HFileService.
Combining Batch and Real-Time Data: Nebula used HFileService to handle batch-updated, offline data. For real-time data (like live updates from users or systems), Nebula integrated DynamoDB, a fast, scalable NoSQL database. This dual approach ensured that Nebula could serve static historical data and dynamic, up-to-the-minute information.
Timestamp-Based Versioning: To maintain data consistency, Nebula assigned timestamps to each piece of data. When a query was made, the system merged real-time and offline data based on these timestamps. This ensured that users always received the most recent and accurate data.
Minimize Online Merge Operations: Nebula dynamically merged data from DynamoDB and HFileService for every query to provide latest information. However, merging data from two storage systems during a query added latency, especially for large datasets or high query volumes. To reduce the burden of online merge operations, Nebula introduced daily spark jobs. These jobs pre-merged real-time updates from DynamoDB with the batch snapshot from HFileService, producing a unified dataset.
Despite the advantages, Nebula also had some limitations such as:
High Maintenance Overhead: Nebula required managing two separate systems: DynamoDB for real-time data and HFileService for batch data. This dual-system approach added complexity, as both systems needed to be kept in sync and operated efficiently.
Inefficient Merging Process: The daily merging job using Spark became slow and resource-intensive as the data grew. For example, even if only 1–2% of the data had changed in DynamoDB, Nebula reprocessed and published the entire dataset from HFileService daily.
Scalability Challenges: As Airbnb's data grew, scaling Nebula to handle increasing traffic and larger datasets became cumbersome, particularly with the manual maintenance and heavy processing requirements.
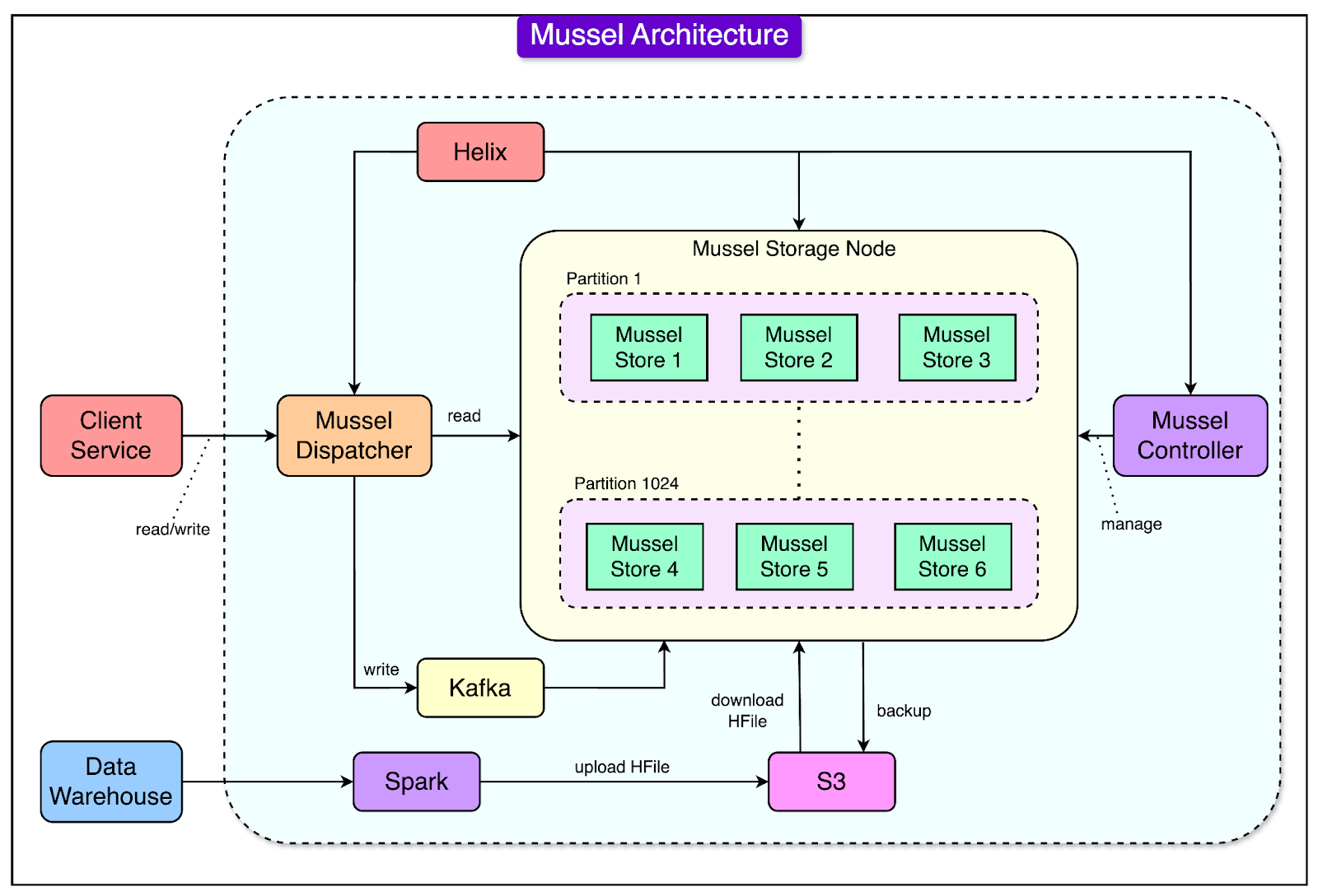
Mussel Architecture
In 2018 the Airbnb engineering team built a new key-value store called Mussel.
The architecture of Mussel was designed to address the scalability and performance limitations of previous solutions.
See the diagram below that shows the architecture of Mussel:
Let’s look at each feature of Mussel’s architecture in more detail:
Partition Management with Apache Helix
Mussel increased the number of shards (data partitions) from 8 to 1024 to support Airbnb’s expanding data needs. These shards are smaller subsets of data distributed across multiple servers, ensuring that no single server is overwhelmed by too much data.
The data was partitioned into those shards by the hash of the primary keys. They used Apache Helix to automate the management of these shards. It determined which physical servers stored each shard and balanced the load dynamically.
This removed the need for manual intervention, making the system more efficient and scalable.
Leaderless Replication with Kafka
Mussel used Kafka as a write-ahead log for every write operation.
Kafka divided the log into 1024 partitions, aligning with the shard structure in Mussel so that each shard’s data was processed in order. This ensured that all updates were recorded and replicated consistently.
Mussel also followed a leaderless replication approach.
Unlike systems with a designated “leader” node for each shard, Mussel allowed any node holding a shard replica to handle read requests. Write operations, however, synchronized across nodes using Kafka logs to maintain consistency.
This design smoothed out spikes in write traffic and prioritized high availability for read-heavy workloads common at Airbnb. The data was eventually consistent, but it was acceptable for the derived data use cases.
Unified Storage Engine with HRegion
Mussel replaced DynamoDB, simplifying the architecture by extending HFileService to handle real-time and batch data in a unified system.
Instead of HFile, Mussel used HRegion, a component of HBase, as its key-value storage engine. This was because HRegion offered:
LSM Tree (Log-Structured Merge Tree) to organize data efficiently.
MemStore for temporary in-memory storage of writes.
BlockCache to speed up reads by caching frequently accessed data.
In HRegion, each client table was mapped to a column family. This grouped related data logically and helped Mussel support advanced queries such as:
Point queries to fetch specific records by primary key.
Range queries to retrieve data over a range of keys.
Time-range queries to access data within a timeframe.
Over time, HRegion created multiple small files from writes and deleted or expired data. To optimize performance, these files needed to be merged using a process called compaction.
Mussel divided its nodes into:
Online nodes: Handled read requests and limited compaction activity to ensure good performance.
Batch nodes: Focused on full-speed compaction.
Helix managed scheduled rotations between these node types, ensuring the system maintained high read availability and efficient compaction.
Bulk Load Support
They supported two types of bulk load pipelines from the data warehouse to Mussel via Airflow jobs:
Merge Type: Involves merging the data from the data warehouse and the data from the previous write with older timestamps in Mussel.
Replace Type: Involves importing the data from the data warehouse and deleting all data with previous timestamps.
Mussel used Spark to process data from Airbnb’s data warehouse, converting it into HFile format. These files were uploaded to S3 (cloud storage), where each Mussel storage node downloaded and loaded them into HRegion using the bulk loading API.
Instead of reloading the entire dataset daily, Mussel loaded only the incremental changes (delta data). This reduced the daily data load from 4TB to just 40–80GB, significantly improving efficiency and reducing operational costs.
Adoption and Performance of Mussel
Mussel has become a core component of Airbnb’s data infrastructure, supporting a wide range of services that rely on key-value storage. It serves as the backbone for applications requiring reliable, low-latency access to derived data.
Some performance metrics regarding Mussel are as follows:
Mussel manages approximately 130TB of data across 4,000 tables in its production environment.
With a >99.9% availability rate, Mussel ensures that its services experience minimal downtime, providing a consistent and reliable user experience.
Mussel handles an impressive read query rate of over 800,000 QPS, making it highly suitable for read-heavy workloads.
It also supports 35,000 write QPS, showcasing its capacity to process real-time updates alongside bulk data loads.
The system achieves an average P95 read latency of less than 8 milliseconds, meaning 95% of read operations are complete in under 8ms.
Conclusion
Mussel demonstrates the evolution of a robust key-value store, addressing critical challenges like scalability, low latency, and operational complexity.
Its impressive metrics and widespread adoption within Airbnb demonstrate how it has become a critical enabler for high-performance data-driven services.
Mussel serves Airbnb’s current use case quite well. However, the Airbnb engineering team is also committed to enhancing Mussel to support use cases such as read-after-write consistency, auto-scaling, and traffic-based repartitioning.
References:
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com.
Like
Comment
Restack
© 2025 ByteByteGo
548 Market Street PMB 72296, San Francisco, CA 94104
Unsubscribe
by "ByteByteGo" <bytebytego@substack.com> - 11:36 - 7 Jan 2025 -
Your Jaspersoft Trial
Hi MD Abul,
Thank you for downloading a 30-day trial of Jaspersoft commercial edition which contains everything you need to design and deliver any report, any way you want.
Jaspersoft can be installed and deployed in any environment because it is built on an open architecture. To get started, please see our Quick Start Guide and Installation Guide. If you run into any roadblocks or need assistance, let me know, and I can connect you with one of our Solution Engineers to get your trial up and running.To help you get the most from your trial, I would love to learn more about your particular use case. Is there a convenient time for us to meet this week or next week? Feel free to book a meeting with me via the link in my signature.Thank you,BrianBrian Farrell,Business Development Representative,Dublin, Ireland.JaspersoftClick here to unsubscribe

by "Brian Farrell" <brian.farrell1@cloud.com> - 10:19 - 7 Jan 2025 -
Key
Hello,
Hope you are doing pretty well! It is my pleasure to discuss with you an SEO report.
I can assist your website in performing well on the first page of Google, Bing, and Yahoo and generating more leads with traffic.
As a result, your sales target and leads will increase, and you will be earning a large amount of revenue.
To get more information, share your interest with me, and then I could equip you with a full proposal.
Best regards,
Hani Singh
by hani28390@gmail.com - 09:33 - 7 Jan 2025 -
GRAB 3 FREE 1 !!! EQ AND COMMUNICATION SKILL USING NLP FOR MANAGERS & LEADERS (24 - 25 Feb 2025)
GRAB 3 FREE 1 !!!
Please call 012-588 2728
email to pearl-otc@outlook.com
FACE TO FACE PUBLIC PROGRAM
EQ AND COMMUNICATION SKILL USING NLP
FOR MANAGERS & LEADERS
5 CPD Points Awarded by MBOT
Venue : Wyndham Grand Bangsar Kuala Lumpur Hotel (SBL Khas / HRD Corp Claimable Course)
Date : 24 Feb 2025 (Mon) | 9am – 5pm By Daniel
25 Feb 2026 (Tue) | 9am – 5pm . .
INTRODUCTION:
This program is designed to offer awareness and skills to the participants on the importance of using EQ in communications. The benefits of having the knowledge of how to implement EQ will give the participants a required skill set in this Experience Economy.
Being able to communicate effectively is an important asset. It can create superb rapport with colleagues and customers alike, increase sales, improve teamwork productivity and help you achieve and contribute towards your success and progression as well as theirs. And learning how to improve our Emotional Intelligence (EI) enhances our understanding of ourselves and our abilities to manage relationships and deal with people better So, why would not you want to be a better communicator?
This highly interesting workshop incorporates tools and ideas used in Neuro-Linguistic Programming (NLP) that makes a real difference by enhancing and developing your EQ & communication skills to achieve significant results. By understanding how to use all your senses, using different styles and levels of language patterns and re-writing your thinking process you can achieve the things you want to at the workplace.
WHY EXCELLENT COMMUNICTION WITH NLP? :
If you need to communicate successfully and influence others then this is the programme for you.
- Inculcate Better understanding-of NLP communication model and process
- Develop Empathy-heighten your listening skills
- Be more persuasive-learn the essential skills to influence and inspire.
- Improve confidence-with the skills to communicate effectively, your self esteem and self worth will be elevated to new levels
- Work better with others-develop the flair to interact well with others
- Know yourself and others better-having a greater understanding of yourself and those around you will make you a more flexible communicator
- Learn to manage-selfs and interpret others non-verbal communication
- Motivate yourself and others-enhance yours and others performance
- Enhance relationships-managing our own emotions and that of others
- Able to manage and overcome-interpersonal communication conflict
- Become an excellent communicator-communicate with integrity and clarity
WHO SHOULD ATTEND:
Anyone who needs to communicate effectively in order to improve work performance and productivity, including:
- Sales & Marketing personnel
- Customer services
- Engineering Designers
- Technical personnel
- Project managers
- Managers/Team Leaders
WHAT WILL YOU LEARN:
Not only will you learn a new skill but you will experience actual mind programming to assist YOU in immediately applying and adopting a dynamic scientific approach to communicate effectively.
LEARNING METHODS USED:
In this fun-filled highly engaging experiential training, the training facilitator adopts a coaching and facilitative approach. It is very important to engage the participants in reviewing their own outcomes.
The fun-filled activities are designed to illustrate key issues that the participants are facing in communicating by using EQ & NLP tools to create illustrations, demonstrations and activities such as role plays, Mind development exercises, group discussions
OUTLINE OF WORKSHOP
Module 1: Introduction
- Understand how different methods of communication affect your work
- Recognise good and bad communication
- Understanding Individual Emotional Orientations and Needs
Module 2: The brain
- How to use the left and right side of your brain to achieve its full potential
- Self Assessment of our preferred thinking approaches in communication
- Change the way you think by re-wiring your brain, breaking habits and thinking more positively
- Learn how the unconscious mind affects our thinking, actions and habits
Module 3: Emotional Intelligence
- What is EQ & EI?
- The Difference between EQ and IQ
- Understanding \Why EQ is important
- EQ Self Assessment of Personality Types
- How to deal effectively with each Personality Type
Module 4: Influential Factors on EQ
- Personality Traits & EQ
- Recognition of your Behaviours and Impulses
- Understanding Situational Non-Verbal Behaviours
- Perception – Interpreting Body Language
- Fear Factors
Module 5: Excellent Communication
- Learn all about human interaction and how to communicate well
- Discover how to make messages clearer, more effective and persuasive
- Answer questions like: What does communication help to do? How do beliefs and values effect communication?
- Backtracking to understand others 3-levels deeper
- Emphatic listening & deep communication
- Emotional Excellence for relationship building
Module 6: Advance Language Patterns
- What words to use to encourage better communication, how to use body language to build rapport
- Advance language patterns that access the sub-consciousness to influence others easily.
- Pacing and priority conflicts in teams
- Meta Modeling-the ultimate persuasive tool
Module 7: Action planning
- Develop an action plan to take your new skills forward
- Action plan to implement Emotional Excellence for relationship development
** Certificate of attendance will be awarded for those who completed the course
ABOUT THE FACILITATOR
Daniel
- Certified Professional Trainer, MIM
- MBA (General) University of Hull, UK
- Council of Engineering Institutions (UK) Part I & II
- Associate Member of Institute of Electrical Engineers, UK
- ISO Standardization Internal Auditor
- NLP Master Trainer Certification, NFNLP US
- Certified Master Conversational Hypnotherapist, IAPCH US
- Certified Specialist in Neuro-Hypnotic Repatterning, SNLP US
- Diploma in International Sound Therapy, IAST Alicante, Spain
Daniel has more than 30 years experience in the corporate world, out of which 20 years has been spent on coaching and training: teaching Sales & Negotiation Skills, Management & Leadership skills - training Companies and individuals on Coaching & Mentoring Skills, Communication Skills, Neuro-Linguistic Programming (NLP) and Project Management skills. And in the process, continually coaching and motivating all his students, staffs and associates to learn, grow and expand their personal paradigms and horizons.
He also has extensive sales management, marketing and sales experience; from selling single course programs to education franchise businesses; as well as single pieces of equipment right-up to multi-million US dollar projects for more than 15 years. In his last major corporate appointment as Assistant General Manager of GEC (UK), Mahkota Technologies, where he was fully in-charge of both local and regional sales for his Division, he successfully managed over 15 different products and systems, with an annual turnover of RM60 million, for both the domestic and regional markets.
He is an engineer by profession and has completed his professional engineering degree, the Council of Engineering Institutions, UK., Part I & II within 2 years, one year short of the normal period of 3 years. As such he was awarded: Excellent Performance Award in the Professional degree. Positions held in the various multi-national corporate companies include from a young installation/service engineer to department manager & general manager of a leading MNC. Currently, he is a Certified Professional Trainer with the Malaysian Institute of Management (MIM) and Cambridge ICT. He is also a Certified Master NLP Trainer of the National Federation of Neuro-Linguistic Psychology, USA.
He also specializes in Effective Communication & Project Management skills, Management & Leadership Skills, Sales training applying Neuro-linguistic Programming and Subconscious Learning in order to accelerate adult learning. His other specialties include Functional & Instructional English for the Workplace, Effective English for Front-liners, Writing Skills, Presentation skills and Engaging Dialogue.
Daniel recognizes the great potential within each individual participant and he believes in making a difference in their learning through his personalised, demonstrative, practical and dynamic approach to make training an enjoyable and valuable experience. His passion for training stems from his innate desire to empower all those individuals who are keen to seek knowledge, wisdom and self improvement; so that they can be the person they need to be to have what they want.
(SBL Khas / HRD Corp Claimable Course)
TRAINING FEE
2 days Face-to-Face Public Program
RM 2,407.00/pax
(excluded 8% SST)
Group Registration: Register 3 participants from the same organization, the 4th participant is FREE.
(Buy 3 Get 1 Free) if Register before 14 Feb 2025. Please act fast to grab your favourite training program!We hope you find it informative and interesting and we look forward to seeing you soon.
Please act fast to grab your favorite training program! Please call 012-588 2728
or email to pearl-otc@outlook.com
Do forward this email to all your friends and colleagues who might be interested to attend these programs
If you would like to unsubscribe from our email list at any time, please simply reply to the e-mail and type Unsubscribe in the subject area.
We will remove your name from the list and you will not receive any additional e-mail
Thanks
Regards
Pearl
by "pearl@otcsb.com.my" <pearl@otcsb.com.my> - 04:22 - 7 Jan 2025 -
IVD REAGENT SUPPLIER
Dear Manager,
Greetings!
This is Zhejiang Xinke Medical Technology Co., Ltd.
We are a professional factory of producing immunoassay analyzer reagent, hematology analyzer reagent, biochemistry analyzer reagent etc. for many famous brands machines.
Such as Mindray, Sysmex, Roche, Beckman Coulter, Abbott, ABX, Nihon Kohden, Urit, Siemens,Dirui, Snibe, Rayto, Genrui etc.Meanwhile, we can accept OEM.
Do you need these reagents ? Waiting for your kindly reply.
by "Emmaya Kessy" <emmayakessy@gmail.com> - 07:00 - 6 Jan 2025 -
🎁 Hurry – we’ve unlocked this GIFT for you! 🎁
We noticed you haven’t completed your 14-day FREE ClickFunnels trial yet.Hey – it’s the ClickFunnel team!
We noticed you haven’t completed your 14-day FREE ClickFunnels trial yet.
And we just wanted to make sure you saw the INSANE gift Russell decided to throw in when you finish your registration here. 🎁🎁🎁
FREE access to the brand new One Funnel Away Challenge!The One Funnel Away Challenge is THE 10-day blueprint to show you step-by-step how to build, launch, and begin to bring in customers (that turn into sales)...
With nothing but ClickFunnels and a FUNNEL!
Know what that means?
With your 14-day ClickFunnels trial… AND the One Funnel Away Challenge…
You can dive in and start building a winning funnel without risking a single penny.
You’ll discover…
✔ The exact buttons to click to set up a beautiful, high-converting funnel.
✔ How to write the words that whip your prospects up into a buying frenzy.
✔ How to fill your funnel with high-quality buyers – without paying a cent on ads.
✔ And so much more!
And even though we’ve always sold this for $100…
We’re gifting it to you today, for FREE, when you start your 14-day ClickFunnels trial!
So click the link below, pick up right where you left off…
And unlock the brand-spankin’-new One Funnel Away Challenge as our gift to you:
Finish Setting Up Your FREE TRIAL Here (Less than 3 mins)
And have your funnel launched in 10 days with the One Funnel Away Challenge!
Thanks,
-ClickFunnels Team
P.S. - So many 2CC Award winners (people who have made $1mil with a single funnel!!) have credited their success to this challenge.
Look at some of the testimonials real OFA Challengers have sent us:
⭐⭐⭐⭐⭐
"The One Funnel Away Challenge blew away ALL of the other courses and trainings I invested in... it was full of brilliant value. It's a whole different mindset... I followed the training advice and it gave my business a MASSIVE push.”
~Mark Felstead
⭐⭐⭐⭐⭐
"My favorite part... The encouragement from the OFA team. I really appreciated the way they showcased that virtually ANYONE can find a way to use funnels and generate revenue."
~Ren B
⭐⭐⭐⭐⭐
"OFA challenge, in a nutshell, is ALL, I mean ALL what you need to understand Online Marketing (and Offline too). And the Coaching Calls?...well. This is the best program I’ve ever been a part of."
~Pablo P
Are YOU the next OFA success story?
Complete Your ClickFunnels Trial & Start Your ONE FUNNEL AWAY Journey Today!
© Etison LLC
By reading this, you agree to all of the following: You understand this to be an expression of opinions and not professional advice. You are solely responsible for the use of any content and hold Etison LLC and all members and affiliates harmless in any event or claim.
If you purchase anything through a link in this email, you should assume that we have an affiliate relationship with the company providing the product or service that you purchase, and that we will be paid in some way. We recommend that you do your own independent research before purchasing anything.
Copyright © 2018+ Etison LLC. All Rights Reserved.
To make sure you keep getting these emails, please add us to your address book or whitelist us. If you don't want to receive any other emails, click on the unsubscribe link below.
Etison LLC
3443 W Bavaria St
Eagle, ID 83616
United States
by "ClickFunnels" <noreply@clickfunnelsnotifications.com> - 02:17 - 6 Jan 2025 -
Provide power solutions and tender for various power projects
Hi info,
This is Mulang Electric,a company focus on Low voltage-ATS,MCCB,MCB,ACB,SPD. We work with organizations like Schneider,Siemens,ABB to Joint development of low-voltage electrical products.
Provide power solutions and tender for various power projects.
Our products are of top quality and help my clients increase sales by offering new and unique designs to capture the market and win projects. The benefit for our clients is that they can get more and more clients and projects.
Could you direct me to the right person to talk to about this so we can explore if this would be something valuable to incorporate into your projects?
Kind regards,
Mulang Electric
by "sales2" <sales2@ml-ele.com> - 12:12 - 6 Jan 2025 -
HRDC !!! HEATING, VENTILATION & AIR-CONDITIONING (HVAC) (26 - 27 Feb 2025)
HRDC CLAIMABLE COURSE!!!
Please call 012-588 2728
email to pearl-otc@outlook.com
PUBLIC PROGRAM
HEATING, VENTILATION &
AIR-CONDITIONING (HVAC)
8 CDP Points Awarded by Suruhanjaya Tenaga.
Venue : Dorsett Grand Subang Hotel, Selangor (SBL KHAS / HRD Corp Claimable Course)
Date : 26 Feb 2025 (Wed) | 9am – 5pm By Ir.Dr.Jaya
27 Feb 2025 (Thu) | 9am – 5pm .
.
ABSTRACT:
HVAC (heating, ventilation, and air conditioning) is the technology of indoor environmental comfort. HVAC system design is a sub-discipline of mechanical engineering, based on the principles of thermodynamics, fluid mechanics, and heat transfer. HVAC is important in the design of medium to large industrial and office buildings such as skyscrapers and in marine environments such as aquariums, where safe and healthy building conditions are regulated with respect to temperature and humidity, using fresh air from outdoors. New methods of modernization, higher efficiency, and system control are constantly introduced by companies and inventors worldwide. The three central functions of heating, ventilating, and air-conditioning are interrelated, especially with the need to provide thermal comfort and acceptable indoor air quality within reasonable installation, operation, and maintenance costs. HVAC systems can provide ventilation, reduce air infiltration, and maintain pressure relationships between spaces. The means of air delivery and removal from spaces is known as room air distribution. The starting point in carrying out an estimate both for cooling and heating depends on the exterior climate and interior specified conditions. However before taking up the heat load calculation, it is necessary to find fresh air requirements for each area in detail, as pressurization is an important consideration.
In modern buildings the design, installation, and control systems of these functions are integrated into one or more HVAC systems. Building services designers and engineers, such as mechanical, architectural, or building services engineers analyze, design, and specify the HVAC systems, and specialty mechanical contractors fabricate and commission them. Building permits and code-compliance inspections of the installations are normally required for all sizes of buildings.
COURSE OVERVIEW:
This course is industry designed, to provide a broad understanding of the improvement methodology, concepts, and process. The methodology is presented with case studies and examples drawn from service, business process and industrial applications. With a heavy practice orientation, as much as a third of your time will be spent working through interactive practical exercises and assessments.
COURSE OBJECTIVES:
This training program is designed to provide an understanding of engineering related problems related to industry globally and a clear sense of what is required to effectively structure, establish measurements and solve problems. Participants will learn the goals and deliverables behind the solutions. Methodology as well as the most commonly used tools within each phase will be discussed. Participants will also learn how to support a problem solving initiative within their organization.
LEARNING OUTCOMES:
On successful completion of this course, the participant should be able to:-
- Understand the benefits and implications of HVAC design and relate the concepts to the overall business mission and objectives.
- Think about his/her organization as a collection of processes, with inputs that determine the output.
- Use the concepts of HVAC design to evaluate the capability of a process or organization.
- Recognize the engineering problem solving model used to improve processes.
- Recognize the organizational factors that are necessary groundwork for a successful engineering problem solving program.
- Integrate HVAC design effort with other process improvement initiatives.
TRAINING METHODOLOGY:
a) The latest educational methods and strategies will be utilized.
b) The course is designed to maximize delegate participation.
c) Questions and answers are encouraged throughout and at the daily wrap-up sessions. This gives participants the opportunity to discuss with others and the presenter their specific problems and appropriate solutions.
d) The course shall be conducted through lectures, case studies, group discussions and exercises to reinforce participant’s learning.
TARGET AUDIENCE:
Design engineers, design technical assistants, draughting personnel, maintenance personnel, operational managers etc.
COURSE FORMAT:
The course consists of formal content presentation interspersed with content quiz sessions. The presenter’s style involves intensive participant participation.
OUTLINE OF WORKSHOP
DAY 1
Introduction to HVAC System Design
- Air system design overview
- Airflow with constant volume systems
- Airflow with variable volume systems
- How Do You Balance Airflow?
- Best air delivery practices
- Air-side economizer
- Lower humidity limit
- A case study of two designs
Refrigeration & Air Conditioning
- Introduction
- Type of refrigeration
- Assessment of refrigeration and air-conditioning
- Energy efficiency opportunities
HVAC Equipment Overview
- Condenser
- Evaporator
- Expansion valve
- Compressor
- Air Handler
- Duct System
- Duct Design Problems
Function of an Air conditioner
- Principle
- Arrangement
- Types of Air-Conditioning Units
a) Room Units
b) Central Units
c) Types of Centralised Units
d) Large Units
e) Sizing Air-Conditioning Units
DAY 2
Design of Indoor Air Quality Systems
- Recommended temperatures for acceptable relative humidity (RH)
- Outside air pollutants
- Damper operation
- Filters
a) Mechanical filters
b) Carbon filters
- Cooling coils
- Humidifiers
- Drain pans
- Air-Handling Units (AHU)
a) Single zone AHU
b) Multi-zone AHU
c) Dual duct AHU
d) Terminal reheat AHU
e) Variable air volume AHU
Complex HVAC Requirements
- Multiple Zone Air-side Systems
- Air-Side Economizers
- Controls (Air-Side, Complex Systems)
- Chillers
- Heat Rejection Equipment
- Hydronic Systems & Controls
Pump Design
- Condenser water pumps
- Chilled water pumps
Energy Savings in HVAC Systems
- A Case Study
Heat Pump Design
- What Is a Heat Pump?
- Basic types of heat pump cycles:
- Heat sources and sinks
Underfloor Air Distribution
- Introduction
- Goals and applications
- Revised load calculations
- Ventilation modifications
- Supply air quantities and temperatures
- System equipment
- Initial cost impacts
- Annual energy consumption and cost
Question &Answer Session
End of Workshop
** Certificate of attendance will be awarded for those who completed the course
ABOUT THE FACILITATOR
Ir. Dr. JAYA has about 32 years of experience in various industries.
Ir. Dr. JAYA is a Professional Engineer registered with the Board of Engineers (BEM), Malaysia, a Fellow of The Institution of Engineers, Malaysia (IEM), member of the Institution of Engineering and Technology (IET), UK and a Member of Engineers Australia and a Chartered Professional Engineer of Australia. Jayaseelan was the past Chairman of the Engineering Education Technical Division of The Institution of Engineers, Malaysia; Member of the Education Committee of the Association of Consulting Engineers (ACEM); Member of the Accreditation Board, Institution of Engineers, Malaysia, Member of the Standing Committee on Admission and Practical Training, Institution of Engineers, Malaysia, a member of the Standing Committee on Examinations and Qualifications, Institution of Engineers, Malaysia and also an EAC accreditation panel member. He is also a Certified Energy Manager, registered with the Energy Commission of Malaysia.
He graduated from the University of Malaya, Leeds Polytechnic, UK and Universiti Putra Malaysia and holds a Degree in Mechanical Engineering, Masters in Engineering and a doctoral degree in engineering.
His wide hands-on industrial experience has enabled him to design and facilitate training courses.
He was a recipient of the Association of Overseas Technical Scholarships (AOTS) award on two occasions, awarded by the Ministry of Economy, Trade and Industry of Japan. Jayaseelan was also a member of the working group to draw up the energy efficiency and energy conservation guidelines for pumps and compressors for Malaysian industries organized by the Institution of Engineers, Malaysia, Pusat Tenaga Malaysia, and the Ministry of Energy, Water and Communications (KTAK). He also actively writes technical articles for various international journals.
He has working experience in various industries, which includes being a General Manager for Facilities Management for a Facility Management Company involved in the management of a portfolio of facilities, including manufacturing plants, high-rise commercial buildings, chemical plants etc. a design engineer with a leading consulting engineering company etc.
Some of the companies he has trained includes, Tenaga Nasional Bhd, Bank Pembangunan, Ranhill, Ebara Pumps, Usaha TegasSdn.Bhd (Maxis), Infineon (M) Sdn.Bhd, UniversitiMalaya, UniversitiTeknologi Malaysia, Penang Port Sdn.Bhd. Cement Industries of Malaysia Berhad, Politeknik Mukah (Sarawak), Petlin Malaysia Sdn Bhd, Bintulu Port, Sime Austral, Perbadanan Putrajaya Holdings, Syarikat Air Johor, ORYX, Carsem, Unisem etc.
Professionally trained in mechanical engineering, he is positive and lively in his approach. He livens his audience by always providing interactive and energetic presentation of his material in a comprehensive and easy to use format of ideas that work. His participants describe him as a very creative, fun and lively trainer who sets high standards.
(SBL KHAS / HRD Corp Claimable Course)
TRAINING FEE
2 days Face-to-Face Public Program
RM 2,407.00/pax
(excluded 8% SST)
Group Registration: Register 3 participants from the same organization, the 4th participant is FREE.
(Buy 3 Get 1 Free) if Register before 12 Feb 2025. Please act fast to grab your favourite training program!We hope you find it informative and interesting and we look forward to seeing you soon.
Please act fast to grab your favorite training program! Please call 012-588 2728
or email to pearl-otc@outlook.com
Do forward this email to all your friends and colleagues who might be interested to attend these programs
If you would like to unsubscribe from our email list at any time, please simply reply to the e-mail and type Unsubscribe in the subject area.
We will remove your name from the list and you will not receive any additional e-mail
Thanks
Regards
Pearl
by "pearl@otcmsb.com.my" <pearl@otcmsb.com.my> - 07:22 - 6 Jan 2025 -
Problem with your trial…
Plus your MASSIVE gift for starting your trial today!Hey!
It looks like you started the process for your 14-day ClickFunnels free trial…
But didn’t quite finish your registration.
Maybe you got an important call, there was a problem checking out, or you had a last minute question?
We know life can get busy so we put your ClickFunnels trial on hold for you at no charge. No need to re-enter your email or anything…
We’ve saved your spot right here >>
Meaning, you’re minutes away from unlocking the most powerful business-building tool on the planet — with everything you need to launch a successful online or offline business.
Now including:
The BRAND NEW One Funnel Away Challenge!
This shows you every step you need to take to launch a winning funnel in just 10 days from now. Including…
✔ The exact buttons to click to set up a beautiful, high-converting funnel.
✔ How to write the words that whip your prospects up into a buying frenzy.
✔ How to fill your funnel with high-quality buyers – without paying a cent on ads.
✔ And so much more!
Now, even though we’ve always sold OFA for $100… we’re gifting it to you today, for FREE, when you start your 14-day ClickFunnels trial!
So click the link below, pick up right where you left off…
And unlock the brand-spankin’-new One Funnel Away Challenge as our gift to you:
And have your funnel launched in 10 days with the One Funnel Away Challenge!Thanks,
-ClickFunnels Team
P.S. - If you have any questions, hit us up at support@clickfunnels.com, and we’ll be happy to help you out ASAP.
© Etison LLC
By reading this, you agree to all of the following: You understand this to be an expression of opinions and not professional advice. You are solely responsible for the use of any content and hold Etison LLC and all members and affiliates harmless in any event or claim.
If you purchase anything through a link in this email, you should assume that we have an affiliate relationship with the company providing the product or service that you purchase, and that we will be paid in some way. We recommend that you do your own independent research before purchasing anything.
Copyright © 2018+ Etison LLC. All Rights Reserved.
To make sure you keep getting these emails, please add us to your address book or whitelist us. If you don't want to receive any other emails, click on the unsubscribe link below.
Etison LLC
3443 W Bavaria St
Eagle, ID 83616
United States
by "ClickFunnels" <noreply@clickfunnelsnotifications.com> - 04:14 - 6 Jan 2025 -
Congratulations on registering for our free training: Master Odoo ERP Accounting Free Training
Hi there,
Congratulations on registering for my free training:
Master Odoo ERP Accounting Free Training
Here is the link to attend the training on Wednesday 15 January 2025 at 12.30pm-2pm ADST:
>> Access Your Free Training HereIn this training, you’ll discover how to confidently set up Odoo for accounting success while avoiding the common traps that trip up most accountants.
I’ll guide you step-by-step through the tools and strategies to streamline your processes, save time, and deliver exceptional results for your clients.
Odoo doesn’t have to be overwhelming—and I’m here to show you how to master it with ease.
I can’t wait to see you inside!
WAO Group
96 Currawong Drive
Port Macquarie, NSW 2444
Australia
by "Jeri Wambeek (WAO Group)" <myworkspaceaa98c96e02-JmNnPW@clickfunnelsmail.com> - 03:43 - 6 Jan 2025 -
High-Quality Decorative Materials for Your Needs
Dear info,
I hope this message finds you well. We are Changsha Lanfeng Decoration Materials Co., Ltd., a professional manufacturer with over 15 years of experience specializing in decorative materials such as PVC self-adhesive wallpaper, blister film, and self-adhesive furniture films.
Our products are widely used in interior and exterior decoration, furniture, advertising, and more. With certifications like CE and SGS, we ensure premium quality for all our customers.
As a direct factory, we offer competitive pricing, customization options, and fast delivery (3–7 days for stock orders). Let us know if you’d like a sample or a price quote.
Looking forward to working with you.
Best regards,
changshalanfeng
by "Olivia" <Olivia@factoryfob.com> - 03:29 - 6 Jan 2025 -
Seeking an opportunity to connect regarding EDB PostgreSQL
Hi Md Abul,
Thanks for registering on the EDB website and for taking the trial EDB PostgreSQL distributed. Let me know if you need any specific information about the EDB PostgreSQL.
Also, Let's have a brief call on Thursday, we will give you a quick overview of our solutions and answer any questions.
Looking forward to connecting!
Best regards,

by "Ganesh Kale" <ganesh.kale@enterprisedb.com> - 01:12 - 6 Jan 2025-
Re: Seeking an opportunity to connect regarding EDB PostgreSQL
Hi Md Abul
Companies that have invested in Postgres as an open-source database alternative have realized huge gains in innovation and even bigger cost savings.
But wider adoption has been held back by concerns about applications that require high-availability and near-zero downtime, and latency issues that would significantly degrade the customer experience and tarnish the brand’s reputation.
For Postgres to be trusted with top-tier applications, it needs to scale to support geographically distributed users with near-zero downtime, near-zero data loss, and near-zero latency for very high read workloads.
If you’re still reading, this must sound familiar. Can we schedule a call to talk about bringing Postgres up to enterprise-grade?
If you’re dying of curiosity and want to know more, check out this whitepaper on the next generation of high availability for PostgreSQL.
Thanks!
On Jan 6, 2025 11:12 AM, "Ganesh Kale" <ganesh.kale@enterprisedb.com> wrote:
Hi Md Abul,
Thanks for registering on the EDB website and for taking the trial EDB PostgreSQL distributed. Let me know if you need any specific information about the EDB PostgreSQL.
Also, Let's have a brief call on Thursday, we will give you a quick overview of our solutions and answer any questions.
Looking forward to connecting!
Best regards,

by "Ganesh Kale" <ganesh.kale@enterprisedb.com> - 02:24 - 6 Jan 2025
-
-
Seamless Shipping Solutions for Your Business
Dear info,
I hope you're doing well. I’d like to introduce our logistics services that have been trusted by companies for over 10 years. We specialize in air and sea freight solutions, to ensure smooth, cost-effective deliveries.
Our team is experienced in handling all types of cargo, and we provide personalized support to make sure your shipments are efficiently managed. If you are looking for a reliable logistics partner to handle your international shipments, I’d love to discuss how we can assist you.
Looking forward to hearing from you!
Best Regards,
Mandy Liu
----------------------------------------------------
Paramount Logistics (Shenzhen) Co.,Ltd
Add: 1002#A Block,HuaYi building ,No.9 Pingji Road ,Nanwan Street,Longgang District , Shenzhen, Guangdong, China (Mainland)
TEL:0755-84594989 Fax :0755-89208448
Mobile :+8615360166019 (Whatsapp&Wechat) +86199(Wechat)
E-mail: zswl@paramtlogistics.com
Website: https://www.paramtlogistics.com/www.sz-zs56.com
by "sale10" <sale10@zswlship.com> - 12:11 - 6 Jan 2025 -
Re: Beauty Industry Professionals list
Hope you are doing well!
We have a Newly Updated OPT-IN database which will help you in reaching Beauty Industry Professionals across North America, UK, Europe and Global.
Job Titles:
· Beauty Industry Consultants
· Beauty Procurement/Purchasing
· Chain Salon Buyer
· Department Store Buyer
· Distributors / Drug Store Buyer
· Estheticians / Importers/Exporters
· International Buyer
· Investment Companies
· Licensed Makeup Artists
· Manufacturer- Representatives
· Manufacturers / Nail Technicians
· OTC/Beauty Retailers
· Packaging Vendors or Suppliers
· Pharmaceutical Companies
· Raw Material Suppliers
· Retail Buyers / Salon/Spa Managers
· Salon/Spa Owners / School Owners
· Specialty Store Buyer / Stylist/Cosmetologists
· Transportation/Shipping Logistics
· Venture Capitalists
The list includes Name, Company, Title, Employee & Revenue Size, Industry, SIC Code, Fax, Website, Physical Address, Phone Number and Verified Email Address.
Please fill in the below details and revert back on the same email, If you would like to add any other criteria (Which mean business to you).
Target Criteria:
· Industry you would like to reach: _______?
· Job title: _______?
· Geography: _______?
We can also help you in E mail and data appending solutions which can help in holding back your lost customers.
Look forward to hearing from you. Thanks!!
Warm Regards,
Nora Davis
Marketing Executive
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
We respect your privacy, if you want to remove it from this list. Please reply back with the subject line as “Leave Out”.
by "Nora Davis" <nora@medicaldataclub.com> - 10:59 - 5 Jan 2025 -
Explore our stainless steel pipe products and enhance your business competitiveness
Dear Sir/Madam:
We learned about your company name on the Internet. We are glad to know that your company is engaged in stainless steel material business. Our company exports stainless steel seamless and welded pipes from Wenzhou, China. We are professional in this field for many years, with excellent quality, very competitive prices and fastest delivery.
Grades:
TP304, TP304L, TP316L, TP310S, TP309S, TP321, 904L, Duplex 2205, 2507, 254SMO, etc.We also provide fittings, flanges, valves, etc., providing a one-stop solution for piping systems.
If you are interested, can you give me your whatsapp number so that I can send you more detailed information? If you have any other questions, please feel free to contact me.
Best regards
Mrs.Fun
by "sales09" <sales09@304316pipestock.com> - 09:51 - 5 Jan 2025 -
Heating Solution supplier
Hi info,
Nice to know excent you. If you'd like to find better electric heating solution, I am willing to share 20 years of industry design experience with you without reservation. We also have a strong design team to help you to develop new heating element design if you need it. Hi
Nice to know excent you. If you'd like to find better electric heating solution, I am willing to share 20 years of industry design experience with you without reservation. We also have a strong design team to help you to develop new heating element design if you need it.
by "Kalvin Laudon" <panibubbel237@gmail.com> - 07:41 - 5 Jan 2025 -
Ergonomic chair S1
Dear info,I would like to recommend you our new task chair .This is the outstanding feature:1) BIFMA standard2 ) Big size neckrest with height and angle adjustble function3) Supportive lumbar support with height and depth adjustment4) 3D adj armrest, arm pad made of soft PU, good touch5) Self-balanced mechanism, no need to adjust tension6) 4 locking positions for backrest to meet any tilting positionMore importantly, this chair is moving fast. customers feed back positively.Are you interested in this chair?


Chris Lu

Guangzhou Huashi Furniture Manufacturing Co., Ltd
Add:No.5 Area B,Yuanxia Industrial zone,Baiyun District,Guangzhou city,Guangdong Province,China.
T: 0086 20 87413588
Whatsapp: +86 18074603378
E: info@huashifurniture.com.cn
E: info@huashichair.com
E: admin@vaseat.com
www.facebook.com/VaseatFurniture
www.vaseat.com

by "Villiard Daymude" <villiarddaymude956@gmail.com> - 02:51 - 5 Jan 2025 -
Button certification, quality-assured ceramic product supplier
Hello info,
Good day!
The purpose of sending you an email is to draw your attention to our company. We are a ceramic manufacturer from China, Linyi Guangfa Porcelain Co., Ltd. Our company has been supplying domestic and foreign trade companies since its establishment.Now we think that the advantages of taking foreign orders independently are:
1. The delivery time is guaranteed, and we will give priority to producing our own orders.
2. Our factory has obtained Walmart, BSCI, SEDEX certification.
3. Quality assurance: We can provide you with the best quality to optimize your company's reputation and increase your company's sales.
Your response is very important to us, so please don't ignore us. I browsed your website and found that we can offer you an 18 piece dinner set at the best price and quality. Attached is our quotation, which is very competitive.We look forward to your valuable suggestions and feedback.
Thanks and beste regardsLinyi Guangfa Porcelain Co., Ltd
by "sales" <sales@gfporcelain.com> - 10:44 - 4 Jan 2025 -
High-quality health ingredients and plant extracts are now on the market
Dear info,
Have a nice day!This is Harris from Shaanxi top purity biotech ltd&sino ingredients Inc. Our company is dedicated to the field of Raw materials of health care products and plant extracts etc. Whether you are in the food and beverage industry looking for natural flavorings and colorants, or in the cosmetics and skincare sector seeking effective ingredients for anti-aging and moisturizing products, we have the perfect solution for you.
Some of our key products include: Berberine HCL Extract, NAD, Coenzyme Q10, PQQ, Sodium copper chlorophyllin etc...
Here's our advantage:
· we are familiar enough with the Chinese market to share with you the latest news on the market.
· We have a warehouse in California, USA, which greatly improves the delivery time.
· Our highly competitive prices.
· Our professional service.
By the way, Please check the attached inventory of our American warehouse. Please feel free to contact me if there are any products you are interested in.
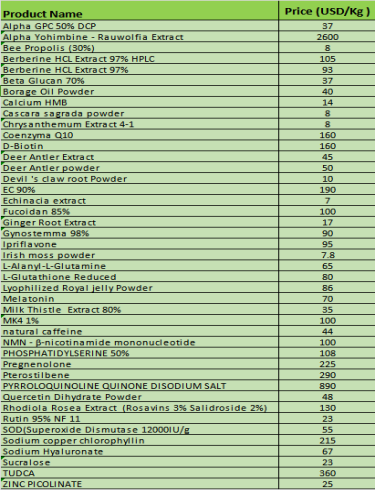
We'd like to rely on our competitive price, professional service, good quality to reduce customers' production costs.
Looking forward to your feedback.
Best Regards,Harris Li
Mob: +86-17765028657 What's App: +86-18779653945QQ: 3109963732
Wechat: +8617765028657 TEL: +86-29-8441122
e-mail: sales08@toppuritybio.net, harrishsfbiotech@gmail.com
by "Tyson Nensthiel" <tysonnensthiel@gmail.com> - 06:49 - 4 Jan 2025 -
Предоставление оборудования для подготовки спиральных ножей и барабанного концентратора.
Добрый день!
Меня зовут Джек из Шанхая,
наша компания главна производим шнековый обезвоживатель,барабанный сгуститель, ленточный фильтр-пресс, флотатор и установка приготовления флокулянта и.т.д.
Если вам заинтересванны, пожалуйста сообщите мне.
Наш русский сайт: http://ru.hibarmachinery.com/
Спасибо.
С уважением
Джек
Shanghai Haibar Mechanical Engineering Co.,Ltd & Shanghai Haibar International Trading Co.,Ltd
Add: 7th fl., Building NO. 7,Baolong City Square, 2449 Jinhai Rd, Pudong Dist, Shanghai 201209
T: 0086-21-50192688
F: 0086-21-31779776
M: 0086-150 0008 0596 (WeChat,whatsapp)
WhatsApp:+19567622690
E-mail: jack@hibar.com.cn
Web: https://www.hibarmachinery.com/
Skype: cheerfuly1
Shanghai Haibar is a leading designer and manufacturer of sludge treatment process equipment for thickening and dewatering in Shanghai.
Please consider the environment before printing this email !
by "sales09" <sales09@hibarmachine.com> - 05:12 - 4 Jan 2025